|
Special Publication 800-98
|
||||||||||
|
National Institute of Standards and Technology
Technology Administration U.S. Department of Commerce
|
||||||||||
|
Guidelines for Securing Radio Frequency Identification (RFID) Systems
|
||||||||||
|
Recommendations of the National Institute of Standards and Technology
|
||||||||||
|
To m Karygiannis Bernard Eydt Greg Barber Lynn Bunn Te d Phillips
|
||||||||||
|
nist Special Publication 800-98 Guidelines for Securing Radio Frequency
Identification (RFID) Systems
Recommendations of the National Institute of Standards and Technology
Tom Karygiannis Bernard Eydt Greg Barber Lynn Bunn Ted Phillips
|
|||||||||||
|
C O M P U T E R S E C U R I T Y
|
|||||||||||
|
Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930
April 2007
|
|||||||||||
 |
|||||||||||
|
US Department of Commerce
Carlos M. Gutierrez, Secretary
Technology Administration
Robert C. Cresanti, Under Secretary of Commerce for Technology
National Institute of Standards and Technology
William Jeffrey, Director
|
|||||||||||
|
Guidelines for Securing RFID Systems
|
|||||||||
|
Reports on Computer Systems Technology
The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the US economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. Special Publication 800-series documents report on ITL’s research, guidelines, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations.
|
|||||||||
|
National Institute of Standards and Technology Special Publication 800-98 Natl. Inst. Stand. Technol. Spec. Publ. 800-98, 154 pages (April 2007)
|
|||||||||
|
Certain commercial entities, equipment, or materials may be identified in this
document to describe an experimental procedure or concept adequately. Such
identification is not intended to imply recommendation or endorsement by the
National Institute of Standards and Technology, nor is it intended to imply that the
entities, materials, or equipment are necessarily the best available for the purpose.
|
|||||||||
|
ii
|
|||||||||
|
Guidelines for Securing RFID Systems
|
||||||
|
Acknowledgments
The authors, Tom Karygiannis of NIST, and Bernard Eydt, Greg Barber, Lynn Bunn, and Ted Phillips of Booz Allen Hamilton, wish to thank Steven Fick, Rick Korchak, Kate Remley, Jeff Guerrieri, Dylan Williams, Karen Scarfone, and Tim Grance of NIST, and Kenneth Waldrop and Beth Mallory of Booz Allen Hamilton. These individuals reviewed drafts of this document and contributed to its technical content.
The authors would also like to express their thanks to several experts for their critical review and feedback on drafts of the publication. These experts include V.C. Kumar of Texas Instruments; Simson Garfinkel of the Naval Postgraduate School; Peter Sand of the Department of Homeland Security; Erika McCallister of MITRE; and several professionals supporting Automatic Identification Technology (AIT) program offices within the Department of Defense (DoD), especially Nicholas Tsougas, Fred Naigle, Vince Pontani, Jere Engelman, and Kathleen Smith.
During the public comment period we received helpful comments from the following Federal Government agencies: the US Departments of Defense, Health and Human Services, Homeland Security, Labor, and State; the Office of the Director of National Intelligence; the Office of Management and Budget; and the General Services Administration. We also received several helpful contributions from commercial industry, including comments from EPCglobal, VeriSign, and Priway.
Finally, the authors wish to thank the following individuals for their comments and assistance: Brian Tiplady, Daniel Bailey, Paul Dodd, Craig K. Harmon, William MacGregor, Ted Winograd, Russell Lange, Perry F. Wilson, John Pescatore, Ronald Dugger, Stephan Engberg, Morten Borup Harning, Matt Sexton, Brian Cute, Asterios Tsibertzopoulos, Mike Francis, Joshua Slobin, Jack Harris, and Judith Myerson.
|
||||||
|
iii
|
||||||
|
Executive Summary
|
|||||||
|
Executive Summary
|
|||||||
|
Like any information technology (IT), radio frequency identification (RFID) presents security and privacy risks that must be carefully mitigated through management, operational, and technical controls in order to realize the numerous benefits the technology has to offer. When practitioners adhere to sound security engineering principles, RFID technology can help a wide range of organizations and individuals realize substantial productivity gains and efficiencies. These organizations and individuals include hospitals and patients, retailers and customers, and manufacturers and distributors throughout the supply chain. This document provides an overview of RFID technology, the associated security and privacy risks, and recommended practices that will enable organizations to realize productivity improvements while safeguarding sensitive information and protecting the privacy of individuals. While RFID security is a rapidly evolving field with a number of promising innovations expected in the coming years, these guidelines focus on controls that are commercially available today.
RFID is a form of automatic identification and data capture (AIDC) technology that uses electric or magnetic fields at radio frequencies to transmit information. An RFID system can be used to identify many types of objects, such as manufactured goods, animals, and people. Each object that needs to be identified has a small object known as an RFID tag affixed to it or embedded within it. The tag has a unique identifier and may optionally hold additional information about the object. Devices known as RFID readers wirelessly communicate with the tags to identify the item connected to each tag and possibly read or update additional information stored on the tag. This communication can occur without optical line of sight and over greater distances than other AIDC technologies. RFID technologies support a wide range of applications—everything from asset management and tracking to access control and automated payment.
Every RFID system includes a radio frequency (RF) subsystem, which is composed of tags and readers. In many RFID systems, the RF subsystem is supported by an enterprise subsystem that is composed of middleware, analytic systems, and networking services. RFID systems that share information across organizational boundaries, such as supply chain applications, also have an inter-enterprise subsystem. Each RFID system has different components and customizations so that it can support a particular business process for an organization; as a result, the security risks for RFID systems and the controls available to address them are highly varied. The enterprise and inter-enterprise subsystems involve common IT components such as servers, databases, and networks and therefore can benefit from typical IT security controls for those components.
Implementing the recommendations presented in this publication should help organizations improve the security of their RFID systems.
Personnel responsible for designing RFID systems should understand what type of application an RFID system will support so that they can select the appropriate security controls.
Each type of application uses a different combination of components and has a different set of risks. For example, protecting the information used to conduct financial transactions in an automated payment system requires different security controls than those used for protecting the information needed to track livestock. Factors to consider include:
■ The general functional objective of the RFID technology. For example, does the system need to determine the location of an object or the presence of an object, authenticate a person, perform a financial transaction, or ensure that certain items are not separated?
|
|||||||
|
ES-1
|
|||||||
|
Guidelines for Securing RFID Systems
|
|||||
|
■ The nature of the information that the RFID system processes or generates. One application may only need to have a unique, static identifier value for each tagged object, while another application may need to store additional information about each tagged object over time. The sensitivity of the information is also an important consideration.
■ The physical and technical environment at the time RFID transactions occur. This includes the distance between the readers and the tags, and the amount of time in which each transaction must be performed.
■ The physical and technical environment before and after RFID transactions take place. For example, human and environmental threats may pose risks to tags’ integrity while the tagged objects are in storage or in transit. Some applications require the use of tags with sensors that can track environmental conditions over time, such as temperature and humidity.
■ The economics of the business process and RFID system. The economic factors for RFID systems are different than those for traditional IT systems. For example, many RFID tags offer few or no security features; selecting tags that incorporate basic security functionality significantly increases the cost of tags, especially if encryption features are needed. Also, the operational cost of some basic IT security controls, such as setting unique passwords and changing them regularly, may be higher for RFID systems because of the logistical challenges in managing security for thousands or millions of tags.
For RFID implementations to be successful, organizations should effectively manage their risk.
Like other technologies, RFID technology enables organizations to significantly change their business processes to increase efficiency and effectiveness. This technology is complex and combines a number of different computing and communications technologies. Both the changes to business process and the complexity of the technology generate risk. The major risks associated with RFID systems are as follows:
■ Business process risk. Direct attacks on RFID system components potentially could undermine the business processes the RFID system was designed to enable. For example, a warehouse that relies solely on RFID to track items in its inventory may not be able to process orders in a timely fashion if the RFID system fails.
■ Business intelligence risk. An adversary or competitor potentially could gain unauthorized access to RFID-generated information and use it to harm the interests of the organization implementing the RFID system. For example, an adversary might use an RFID reader to determine whether a shipping container holds expensive electronic equipment, and then target the container for theft when it gets a positive reading.
■ Privacy risk. Personal privacy rights or expectations may be compromised if an RFID system uses what is considered personally identifiable information for a purpose other than originally intended or understood. As people possess more tagged items and networked RFID readers become ever more prevalent, organizations may have the ability to combine and correlate data across applications to infer personal identity and location and build personal profiles in ways that increase the privacy risk.
■ Externality risk. RFID technology potentially could represent a threat to non-RFID networked or collocated systems, assets, and people. For example, an adversary could gain unauthorized access to computers on an enterprise network through Internet Protocol (IP) enabled RFID readers if the readers are not designed and configured properly.
|
|||||
|
ES-2
|
|||||
|
Executive Summary
|
||||||
|
Organizations need to assess the risks they face and choose an appropriate mix of management, operational, and technical security controls for their environments. These organizational assessments should take into account many factors, such as regulatory requirements, the magnitude of each threat, and cost and performance implications of the technology or operational practice.
Privacy regulations and guidance are often complex and change over time. Organizations planning, implementing, or managing an RFID system should always consult with the organization’s privacy officer, legal counsel, and chief information officer.
When securing an RFID system, organizations should select security controls that are compatible with the RFID technologies they currently deploy or purchase new RFID technologies that support the necessary controls.
To be most effective, RFID security controls should be incorporated throughout the entire life cycle of RFID systems—from policy development and design to operations and retirement. However, many RFID products support only a fraction of the possible protection mechanisms. Tags, in particular, have very limited computing capabilities. Most tags supporting asset management applications do not support authentication, access control, or encryption techniques commonly found in other business IT systems. RFID standards specify security features including passwords to protect access to certain tag commands and memory, but the level of security offered differs across these standards. Vendors also offer proprietary security features, including proprietary extensions to standards-based technologies, but they are not always compatible with other components of the system. Careful planning and procurement is necessary to ensure an organization’s RFID system meets its security objectives.
|
||||||
|
ES-3
|
||||||
|
Section 2: RFID Technology
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Table 2-2. Common Sources of RF Interference
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
9 10
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
S. Lahiri, RFID Sourcebook. Pearson Education, 2005.
In the table, transparent is used to indicate that the material allows radio waves to propagate through it without a significant
loss of energy. Absorbent specifies that radio waves propagating through the material will have a significant loss of energy.
Opaque indicates that radio waves will be blocked, reflected, or scattered.
This is the designated center frequency for the frequency band of 13.553-13.567 MHz, which is an Industrial, Scientific, and
Medical (ISM) band that is available worldwide. ISM bands are also used for consumer applications.
The designation 915 MHz represents the frequency band of 902-928 MHz, which is an ISM band in North and South
America. Contrarily, 433.5-434.5 MHz is not an ISM band in North and South America, but RFID systems in the United
States can use this band subject to restrictions in the US Federal Communications Commission (FCC) Part 15 rules.
The designation of 2.45 GHz represents the center frequency of the 2.400-2.500 GHz frequency band, which is an ISM
band.
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
11 12
13
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
2-7
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Section 4: RFID Risks
|
||||||||||
|
4.
|
RFID Risks
|
|||||||||
|
RFID technology enables an organization to significantly change its business processes to:
■ Increase its efficiency, which results in lower costs,
■ Increase its effectiveness, which improves mission performance and makes the implementing organization more resilient and better able to assign accountability, and
■ Respond to customer requirements to use RFID technology to support supply chains and other applications.
The RFID technology itself is complex, combining a number of different computing and communications technologies to achieve the desired objectives. Unfortunately, both change and complexity generate risk. For RFID implementations to be successful, organizations need to effectively manage that risk, which requires an understanding of its sources and its potential characteristics.
This section reviews the major high-level business risks associated with RFID systems so that organizations planning or operating these systems can better identify, characterize, and manage the risk in their environments. The risks are as follows:
■ Business Process Risk. Direct attacks on RFID system components potentially could undermine the business processes the RFID system was designed to enable.
■ Business Intelligence Risk. An adversary or competitor potentially could gain unauthorized access to RFID-generated information and use it to harm the interests of the organization implementing the RFID system.
■ Privacy Risk. Personal privacy rights or expectations may be compromised if an RFID system uses what is considered personally identifiable information for a purpose other than originally intended or understood. The personal possession of functioning tags also is a privacy risk because it could enable tracking of those holding tagged items.
■ Externality Risk. RFID technology potentially could represent a threat to non-RFID networked or collocated systems, assets, and people.
An important characteristic of RFID that impacts all of these risks is that RF communication is invisible to operators and users. In other AIDC and IT systems, it often is easier to identify when unauthorized behavior is occurring. This section characterizes the risks listed above in more detail. The security controls that mitigate these risks are discussed in Section 5.
4.1 Business Process Risk
RFID systems typically are implemented to replace or enhance a paper or partially automated process. Organizations implementing RFID systems could become reliant on those systems, which if not implemented properly with business continuity planning might be less resilient to disruptions than the systems they replace. For example, suppose that a warehouse replaces its paper-based inventory management system with an RFID-enabled system. The paper system involves storing completed forms at the warehouse and sending form duplicates to a central office, while the new RFID system locates its backend database servers at a single computing center. In this environment, the paper system might be more resilient to a local disaster than the RFID system, despite the increased efficiency, accuracy, or effectiveness of the RFID-enabled business process.
|
||||||||||
|
4-1
|
||||||||||
|
Guidelines for Securing RFID Systems
|
||||||||||||||||||||||||||||||||||||||||
|
Failure in any component or subsystem of the RFID system could result in system wide failure. In the warehouse example, system wide failure might result from many causes, such as loss of the network connection between the warehouse and the computing facility, a software virus that disables critical middleware functionality, or a new source of radio interference that prevents readers from accurately reading tags. If an RFID system is rendered unavailable for any reason, then potential impacts can range from a deceleration of the business process to the loss of critical business or operational records. If the system is mission critical, then the consequences could be devastating to the organization’s performance.
Table 4-1 reviews some of the factors that determine the level of business process risk.
Table 4-1. Factors Influencing Business Process Risk
|
||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||
|
Unlike most of the other risks, business process risk can occur as a result of both human action and natural causes. Moreover, human causes may be intentional or unintentional. For example, a tag might
|
||||||||||||||||||||||||||||||||||||||||
|
4-2
|
||||||||||||||||||||||||||||||||||||||||
|
Section 4: RFID Risks
|
||||||||
|
fail to perform its intended function because someone removed it from its packaging, an employee accidentally damaged it with a box cutter, or a severe storm covered it in ice.
An example of an intentional attack on an RFID business process is cloning, which occurs when an adversary reads information from a legitimate RFID tag and then programs another tag or device to emulate the behavior of the legitimate tag. Documented examples of cloning have occurred in tags used for financial payment32 and access control.33 Another attack on an RFID business process would be removing a tag from the item it is intended to identify and attaching it to another unrelated item. Someone might, for example, perform such an attack to get a better price on an expensive item in a store.
Potential problems are not just limited to the RF subsystem. If the network supporting the RFID system is down, then the RFID system is likely down as well. In supply chain applications, network failures at any point in the chain have the potential to impact the business processes of any subsequent link in the chain. For example, if a supplier is unable to write manifest data to a tag, then the recipient cannot use that data in its operations even if its RFID readers and network infrastructure are fully functional. Servers hosting RFID middleware, databases, analytic systems, and authentication services are all points of failure. Any efforts to assess business process risk need to be comprehensive, because such a wide variety of potential threats exist. All of these threats have the potential to undermine the supported business process and therefore the mission of the implementing organization.
4.2 Business Intelligence Risk
RFID is a powerful technology, in part, because it supports wireless remote access to information about assets and people that either previously did not exist or was difficult to create or dynamically maintain. While this wireless remote access is a significant benefit, it also creates a risk that unauthorized parties could also have similar access to that information if proper controls are not in place. This risk is distinct from the business process risk because it can be realized even when business processes are functioning as intended.
A competitor or adversary can gain information from the RFID system in a number of ways, including eavesdropping on RF links between readers and tags, performing independent queries on tags to obtain relevant data, and obtaining unauthorized access to a back-end database storing information about tagged items. Supply chain applications may be particularly vulnerable to this risk because a variety of external entities may have read access to the tags or related databases. The risk of unauthorized access is realized when the entity engaging in the unauthorized behavior does something harmful with that information.
In some cases, the information may trigger an immediate response. For example, someone might use a reader to determine whether a shipping container holds expensive electronic equipment, and then break into the container when it gets a positive reading. This scenario is an example of targeting.
In other cases, data might also be aggregated over time to provide intelligence regarding an organization’s operations, business strategy, or proprietary methods. For instance, an organization could monitor the number of tags entering a facility to provide a reasonable indication of its business growth or operating practices. In this case, if someone determined that a warehouse recently received a number of very large
|
||||||||
|
Researchers from the Johns Hopkins University and RSA Laboratories cloned tags used as vehicle immobilizers and electronic payment tokens. Source: S. Bono, M. Green, A. Stubblefield, A. Juels, A. Rubin, and M. Szydlo, "Security analysis of a cryptographically-enabled RFID device," in the Fourteenth USENIX Security Symposium, 2005, pp. 1-16. A University of Waterloo student cloned a proximity card used for access control. Source: S. Garfinkel, Ed., and B. Rosenberg, Ed., RFID Applications, Security, and Privacy. Upper Saddle River, New Jersey: Pearson Education, Inc., 2006, pp. 291-301.
|
||||||||
|
4-3
|
||||||||
|
Guidelines for Securing RFID Systems
orders, then that might trigger an action in financial markets or prompt a competitor to change its prices or production schedule.
Table 4-2 reviews some of the factors that determine the level of business intelligence risk.
Table 4-2. Factors Influencing Business Intelligence Risk
|
||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||
|
4.3 Privacy Risk
RFID technology raises several important privacy concerns. One concern is that organizations may collect personal information for a particular purpose, such as to complete a financial transaction or grant an individual access to a facility, and then later use that information for a different purpose that the individual finds undesirable, such as to conduct a direct marketing campaign. Another concern is that organizations that are implementing RFID systems to serve a particular business process might not be aware of how the RFID information could be used for unintended purposes, such as the targeting or tracking of individuals, or the potential disclosure of personal practices or preferences to unauthorized third parties.
|
||||||||||||||||||||||||||||||||||||
|
4-4
|
||||||||||||||||||||||||||||||||||||
|
Section 4: RFID Risks
|
|||||
|
There are privacy risks from the perspective of the individual and from the perspective of the organization implementing RFID technology. The privacy risk from the perspective of the individual is the unauthorized revelation of personal information and the personal consequences of that breach. The privacy risk from the perspective of the implementing organization might include:
■ Penalties if the organization does not comply with privacy laws and regulations,
■ Customer avoidance or boycott of the organization because of real or perceived privacy concerns about RFID technology,
■ Being held legally liable for any consequences of the weak privacy protections, and
■ Employees, shareholders and other stakeholders might disassociate with the organization due to concerns about corporate social responsibility.
Business objectives often conflict with privacy objectives. Organizations can benefit from the analysis and sharing of personal information obtained with RFID technology. At the same time, these activities may potentially violate the privacy rights or expectations of citizens and consumers. Similarly, methods to protect personal privacy may pose a business process risk. For example, consumers may want tags to be disabled at point-of-sale so that they cannot be used for tracking purposes afterwards. However, if it is easy to disable a tag at point-of-sale, then it may also be easier for adversaries to disable tags prior to point-of-sale, thereby disrupting the business process. Moreover, organizations may want to use tags after point-of-sale for post-sale support, recalls, and other purposes.
Privacy risk may increase when an individual possesses tags from multiple organizations because someone reading the tags can now combine and correlate information to profile individuals in ways that none of the organizations alone might have anticipated. For example, if a consumer purchases a tagged item and the tag is not disabled or removed, then the seller or someone else could subsequently use the tag to reveal the presence of that person at a another location and time. The consumer may have purchased the item with cash, presuming to remain anonymous in the transaction. However, if she also carries another tag that reveals her identity, such as an RFID-enabled identification card, then someone may be able to surreptitiously read both tags to establish an association between the purchased item and her identity that had not previously existed. As people possess more tagged items and readers become more prevalent in everyday life, the potential for more complex associations and inferences increases.
Other factors that impact the level of privacy risk include:
■ Whether personal information is stored on tags,
■ Whether the tagged items are considered personal (e.g., pharmaceuticals or devices that would reveal a medical condition, or a book that might reveal a political or religious affiliation),
■ The likelihood that the tag will be in the proximity of compatible readers,
■ The length of time records are retained in analytic or archival systems, and
■ The effectiveness of RFID security controls, in particular:
- The efficacy of tag memory access control and authentication mechanisms,
- The ability of tags to be disabled after their use in a business process has been completed, and
- The ability of users to effectively shield tags to prevent unauthorized read transactions.
4-5
|
|||||
|
Guidelines for Securing RFID Systems
|
||||||||
|
For additional information on privacy considerations, see Section 6.
4.4 Externality Risk
RFID systems typically are not isolated from other systems and assets in the enterprise. Every connection point between the RFID system and something outside the RFID system represents a potential vulnerability for the entity on the other side of the connection, whether that is an application process, a valued asset, or a person. Externality risks are present for both the RF and enterprise subsystems of an RFID system. The main externality risk for the RF subsystem is hazards resulting from electromagnetic radiation, which could possibly range from adverse human health effects to ignition of combustible material, such as fuel or ordnance. The main externality risk for the enterprise subsystem is successful computer network attacks on networked devices and applications. Computer network attacks can involve malware (e.g., worms and viruses) or attack tools that exploit software vulnerabilities and configuration weaknesses to gain access to systems, perform a denial of service, or cause other damage. The impact of computer network attacks can range from performance degradation to complete compromise of a mission-critical application.
Because the externality risk by definition involves risks outside of the RFID system, it is distinct from both the business process and business intelligence risks; externality risks can be realized without having any effect on RFID-supported business processes or without revealing any information to adversaries.
4.4.1 Hazards of Electromagnetic Radiation
RFID technology, like any other radio technology, relies on the use of electromagnetic radiation to communicate information. The potential risk of electromagnetic radiation includes:
■ Hazards of electromagnetic radiation to people (HERP),
■ Hazards of electromagnetic radiation to ordnance (HERO),
■ Hazards of electromagnetic radiation to fuel (HERF), and
■ Hazards of electromagnetic radiation to other materials, including medical supplies such as blood products, vaccines, and pharmaceuticals.
As of the publication of this document, no documented examples have been identified that any of these hazards have been realized with respect to RFID technology, which typically operates at power levels below those that would cause a concern. Moreover, no research has suggested the realization of these risks with respect to RFID technology is likely, although interaction with some medical devices has been the subject of research studies.34 The US Federal Communications Commission (FCC) promulgates regulations to protect citizens against unsafe radio transmissions by requiring equipment testing and certification. The FCC limits for general population/uncontrolled exposure are tabulated in Appendix E.
|
||||||||
|
US Food and Drug Administration has identified the potential for human implanted RFID chips to be incompatible with magnetic resonance imaging (MRI). Source: D. Tillman, "Re: K033440; evaluation of automatic class III designation; VeriChip™ health information microtransponder system; regulation number: 21 Code of Federal Regulations (CFR) § 880.6300; classification: class II; product code: NRV," October 12, 2004,
http://www.sec.gov/Archives/edgar/data/924642/000106880004000587/ex99p2.txt. While RF interference with pacemakers is a concern, it does not appear to pose a serious problem in practice. Source: R. Cleveland Jr. and J. Ulcek, "Questions and answers about biological effects and potential hazards of radiofrequency electromagnetic fields," Federal Communications Commission Office of Engineering and Technology (OET), Washington, D.C., OET Bulletin 56, Fourth Edition, August 1999, pp. 26.
|
||||||||
|
4-6
|
||||||||
|
Section 4: RFID Risks
|
|||||||
|
In addition, DoD regulations require HERO and HERF evaluation of RF systems.35 It is important to note that RFID systems may be within exposure limits when initially installed, but later exceed limits if operators increase the emitted power of readers, perhaps to improve the performance and reliability of the system.
Nevertheless, the critical consequences that would result from any realization of the risk suggest that organizations exercise prudence when fielding RFID technology, especially in complex electromagnetic environments. Electromagnetic signals and waves can reflect, interfere, and resonate in unintended ways in complex electromagnetic environments that include metal objects such as metal doors, window frames, and metal enclosures. This can result in unexpected or unintended signal and field cancellation, interference, summation, or resonance. This makes it difficult to accurately predict specific localized field levels from radiated power alone. Some factors that may warrant additional examination of electromagnetic radiation hazards include:
■ The use of RFID equipment that has not been certified by the FCC or that has been modified to operate outside of FCC mandated limits36 (both of which are illegal in the US but may be legal in other countries), and
■ Operating RFID equipment in environments in which signal reflections and other electromagnetic effects can focus radiation in unintended ways.37
4.4.2 Computer Network Attacks
RFID technology represents a new attack vector on an enterprise network. Once RFID systems are implemented, a possibility exists that attackers could reach non-RFID and enterprise subsystem computers through a reader, although no such attack is known to have successfully occurred to date. If the system involves wireless handheld readers, then the wireless link between the reader and the networked middleware servers is another point of entry. Once RFID servers are compromised, they can be used to launch attacks on other networked systems. Attack possibilities include the introduction of malware (e.g., a worm or virus) or the exploits of a single adversary compromising one computer at a time. Once additional systems are compromised, all types of adverse consequences to the IT infrastructure are possible, including loss of confidentiality, integrity, and availability.
While the risk of network compromise through an RFID interface is considered low, it is possible, especially as the number of RFID reader, middleware, and enterprise applications increases. RFID air-interface protocols do not support the execution of remote commands on the RFID interface, but if the reader accepts data formats outside those expected by the protocol, then conceivably an adversary could exploit a buffer overflow vulnerability on a reader by sending it non-compliant data. If the system is poorly designed, the adversary may be able to insert code or commands in memory buffers read by processes that can execute administrative functions such as disabling security controls. The potential consequence is that the adversary could gain full control of the device and use that control to attack other systems.
Although no known instance of this type of attack has occurred in a real-world application, RFID security specialists have demonstrated RFID viruses in a controlled laboratory environment.38 An RFID virus is a
|
|||||||
|
Department of Defense, "Directive 3222.3: DoD electromagnetic environmental effects (E3) program," September 8, 2004,
Under US FCC regulation, the antennas of RFID readers operating in the 902–928 MHz band may output radiated power up
to 4 watts. Source: 47 CFR § 15.247.
An example might be the hull of a steel ship, in which there are numerous reflective metal surfaces with a variety of
curvatures. While everyday objects such as metal furniture or vehicle bodies can reflect and focus RF signals in ways
difficult to predict, they are unlikely to cause electromagnetic hazards.
|
|||||||
|
4-7
|
|||||||
|
Guidelines for Securing RFID Systems
|
||||||||||||||||||||||||||||||||||||||
|
small program encoded on a tag that becomes active once it has been read and is then passed to the middleware or database of an IT system. If the system is poorly designed, the virus could possibly take advantage of internal software weaknesses in middleware or database products to replicate itself to other tags. This distinguishes the risk from AIDC technologies such as bar codes that cannot be changed after manufacture because they do not contain modifiable memory.
Some factors influencing the magnitude of the risk to the IT infrastructure and the applications they support are presented in Table 4-3.
Table 4-3. Factors Influencing Cyber Attack Risk
|
||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||
|
4.5 Summary
For RFID implementations to be successful, organizations should effectively manage their risk. The major categories of risk are as follows:
■ Business Process Risk. This encompasses threats and vulnerabilities that could cause part or all of the RFID system to fail. Potential impacts range from a deceleration of the business process to the loss of critical business or operational records. Business process risk can occur for many reasons, including human action (either benign or malicious) and natural causes. Factors influencing business process risk include the importance of the RFID-supported business processes to the mission of the organization, the robustness of business continuity planning, and the environment in which the RFID technology is located. The cloning of tags and attacks on enterprise subsystem networks are examples of threats to business processes.
■ Business Intelligence Risk. This involves threats and vulnerabilities that could permit unauthorized parties to gain access to sensitive or proprietary information. A competitor or adversary can gain
|
||||||||||||||||||||||||||||||||||||||
|
M. Rieback, B. Crispo, and A. Tanenbaum, "Is your cat infected with a computer virus?" in the Fourth IEEE International Conference on Pervasive Computing and Communications, 2006, pp. 169-179.
|
||||||||||||||||||||||||||||||||||||||
|
4-8
|
||||||||||||||||||||||||||||||||||||||
|
Section 4: RFID Risks
|
||||||
|
information from the RFID system in a number of ways, including eavesdropping on RFID transactions, reading tags, and gaining access to RFID-related databases. The risk of unauthorized access is realized when the entity engaging in the unauthorized behavior does something harmful with that information. In some cases, the information may trigger an immediate response, such as breaking into a container holding valuable goods. In other cases, data may also be aggregated over time to provide intelligence related to an organization’s customers, operations, business strategy, or proprietary methods.
■ Privacy Risk. Privacy rights or expectations may be compromised if an RFID system uses what is considered personal information for a purpose other than originally intended or if a third party uses the presence of tagged items to profile individuals. In the case of the latter, the primary privacy risk is likely borne by the consumer, not the organization that implemented the RFID system. Nevertheless, the RFID implementing organization still has privacy-related risks, including penalties from non-compliance with existing privacy regulations, legal liability, and the reaction of consumers, employees, public interest groups, and other stakeholders.
■ Externality Risk. Every connection point between an RFID system and other systems represents a potential vulnerability. One externality risk for an RF subsystem is hazards resulting from electromagnetic radiation, which could possible range from adverse human health effects to ignition of combustible material, such as fuel or ordnance. The main externality risk for an enterprise subsystem is successful attacks on networked hosts and applications. Computer network attacks can involve malware or attack tools that exploit software vulnerabilities and configuration weaknesses to gain access to systems, perform a denial of service, or cause other damage. The impact of computer network attacks can range from performance degradation to complete compromise of a mission-critical application.
|
||||||
|
4-9
|
||||||
|
Section 5: RFID Security Controls
|
|||||||||||
|
5.
|
RFID Security Controls
|
||||||||||
|
This section discusses security controls that can potentially mitigate the business risks associated with RFID systems. As previously discussed, RFID implementations are highly customized. As a result, the security controls listed are not all applicable or effective for all RFID applications. Organizations need to assess the risks they face and choose an appropriate mix of controls for their environments, taking into account factors such as regulatory requirements, the magnitude of the threat, cost and performance.
Federal agencies should refer to Federal Information Processing Standards (FIPS) Publication 200, Minimum Security Requirements for Federal Information and Information Systems and NIST Special Publication 800-53 (as amended), Recommended Security Controls for Federal Information Systems, when developing or revising policies related to an RFID system. NIST Special Publication 800-100, Information Security Handbook: A Guide for Managers may also be helpful as it provides a broad overview of information security program elements to assist managers in understanding how to establish and implement an information security program.
This section covers security controls applicable to most RFID implementations. It does not address the security of RFID-enabled smart cards and payment systems. This section also does not discuss security controls related to general IT systems, such as network infrastructure, databases, and Web servers because these are already covered by other security requirements and guidelines. For example, EPCIS servers, which can be accessed by trading partners through the Internet, should be protected by the same types of controls that would be used for any other Internet-facing system (e.g., encryption of sensitive communications, access control to prevent unauthorized access to data and systems) to ensure the security of the data collected by the RFID system. Guidelines on topics such as IT server, application, database, and network security are available from many sources, including NIST’s Computer Security Resource Center (CSRC).39
RFID security is a rapidly evolving discipline. Although promising research is noted when applicable, this section focuses on controls that are presently commercially available.
The RFID security controls discussed in this section are divided into three groups:40
■ Management. A management control involves oversight of the security of the RFID system. For example, the management of an organization might need to update existing policies to address RFID implementations, such as security controls needed for an RF subsystem.
■ Operational. An operational control involves the actions performed on a daily basis by the system’s administrators and users. For example, RFID systems need operational controls that ensure the physical security of the systems and their correct use.
■ Technical. A technical control uses technology to monitor or restrict the actions that can be performed within the system. RFID systems need technical controls for several reasons such as protecting data on tags, causing tags to self-destruct, and protecting wireless communications.
The information provided for each control includes:
|
|||||||||||
|
39 The CSRC is located at http://csrc.nist.gov/publications/nistpubs/index.html. Appendix D contains a list of NIST publications that address general security issues and provide guidelines for the configuration of specific technologies that might be of use when securing an RFID system, including the computing devices in the enterprise subsystem.
40 For more information on security controls see R. Ross, S. Katzke, A. Johnson, M. Swanson, G. Stoneburner, and G. Rogers, Recommended Security Controls for Federal Information Systems. NIST Special Publication 800-53 (as amended), December 2006.
|
|||||||||||
|
5-1
|
|||||||||||
|
Guidelines for Securing RFID Systems
|
||||||
|
■ A description of the control and how it works,
■ The types of implementations or applications where the control might be helpful,
■ The benefits that the control provides, such as which risks it mitigates, and
■ The weaknesses of the control, including why it might not be effective in some environments, and what residual risks and other concerns remain even if the control is implemented.
The summary at the end of Section 5 summarizes the controls and maps them to the risk categories discussed in Section 4.
5.1 Management Controls
Management controls are typically involved in risk assessment, system planning, and system acquisition, as well as security certifications, accreditations, and assessments. The sub-sections below discuss management controls for RFID systems in more detail.
5.1.1 RFID Usage Policy
Control: An RFID usage policy describes the authorized and unauthorized uses of RFID technology in an organization and the personnel roles assigned to particular RFID system tasks. Federal agencies should follow FIPS Publication 199, Standards for Security Categorization of Federal Information and Information Systems, when developing the RFID usage policy.
The usage policy also should be consistent or integrated with the organization’s privacy policy, which addresses topics such as how personal information is stored and shared. The RFID usage policy should also address privacy issues associated with the tag identifier formats and the potential disclosure of information based on solely on the tag identifier format selected. Additional information resources are found in the privacy guidelines in Section 6.
Applicability: All organizations that use RFID technologies or are considering using them.
Benefits: The policy establishes the framework for many other security controls. It provides a vehicle for management to communicate its expectations regarding the RFID system and its security. It enables management to take legal or disciplinary action against individuals or entities that do not comply with the policy.
Weaknesses: The existence of a policy does not ensure compliance with the policy. A policy needs to be coupled with the implementation and enforcement of appropriate operational and technical controls to be effective.
5.1.2 IT Security Policies
Control: IT security policies describe the approach to achieve high-level security objectives of the usage policy. The IT security policies related to RFID should cover each RFID subsystem, including network, database and application security in the enterprise and inter-enterprise subsystems; they should not just be limited to security of tags and readers in the RF subsystem.
IT security policies for RFID systems should address:
■ Access control to RFID information, especially records contained in RFID analytic system databases,
|
||||||
|
5-2
|
||||||
|
Section 5: RFID Security Controls
|
||||||||
|
■ Perimeter protection, including port and protocol restrictions for network traffic between the RF and enterprise subsystems and between the enterprise subsystem and a public network or extranet,
■ Password management, particularly with respect to the generation, distribution, and storage of tags’ access, lock, and kill passwords,
■ Management system security for readers and middleware, including the use and protection of SNMP read and write community strings,41
■ RFID security training for system administrators and operators, and
■ Management of associated cryptographic systems, including certification authorities and key management.
Applicability: All RFID implementations, particularly those with enterprise subsystems or inter-enterprise subsystems.
Benefits: We ll-crafted security policies govern the mitigation of business risks associated with the use of RFID technologies. The policies provide requirements and guidelines for the individuals designing, implementing, using, and maintaining RFID systems. For example, IT policies help the personnel designing RFID systems or procuring system components to make appropriate decisions. Similarly, they help system administrators correctly implement and configure software and related network components.
Weaknesses: The existence of a policy does not ensure compliance with the policy. A policy needs to be coupled with the implementation and enforcement of appropriate operational and technical controls to be effective.
5.1.3 Agreements with External Organizations
Control: When data associated with an RFID system needs to be shared across organizational boundaries, formal agreements among the participating organizations can codify the roles and responsibilities, and in some cases the legal liability, of each organization. These formal agreements are usually documented as a Memorandum of Agreement (MOA) or Memorandum of Understanding (MOU). The MOU or MOA specifies the network connections and authentication mechanisms to be used, the data to be shared, and the manner in which data should be protected both in transit and at rest. It may also address controls on vendors, subcontractors, and other third parties to the extent they have access to the
system.
If the inter-enterprise application requires tag passwords to be shared across organizations, then the MOU or MOA should specify how these passwords will be generated, stored, and shared. The memorandum may specify IT security controls such as methods of authentication, access control, or encryption that participating organizations shall implement to protect the passwords.
Applicability: Any RFID system involving more than one organization, which is most common in supply chain applications.
|
||||||||
|
SNMP community strings are passwords that provide anyone with an SNMP management client and network access the ability to manage the associated systems. Knowledge of the read community string provides the holder the ability to view the system configuration and track system behavior. Knowledge of the write community string provides the holder the ability to reconfigure system components.
For additional information on agreements with external organizations, see NIST Special Publication 800-47, Security Guide for Interconnecting Information Technology Systems, which can be found at http://csrc.nist.gov/publications/nistpubs/800-47/sp800-47.pdf.
|
||||||||
|
5-3
|
||||||||
|
Guidelines for Securing RFID Systems
|
|||||
|
Benefits: Having an MOA or MOU significantly reduces the potential for subsequent misunderstandings and security breaches. They enable signatories to communicate their respective security requirements while also realizing the benefits of the business partnership that led them to collaborate in the development and use of the RFID system.
Weaknesses: Monitoring an external organization’s enforcement of an agreement is difficult without full access to its systems and personnel, which is unlikely. As a result, violations may occur without detection. This risk can be mitigated with independent audits if signatories agree to hire third-parties to conduct such audits.
5.1.4 Minimizing Sensitive Data Stored on Tags
Control: Instead of placing sensitive data on tags, the data could be stored in a secure enterprise subsystem and retrieved using the tag’s unique identifier.
Applicability: Applications that use tags with on-board memory and process data that is either considered sensitive or that could be combined with other data to infer sensitive information.
Benefits:
■ Adversaries cannot obtain information from the tag through rogue scanning or eavesdropping.
■ Data encryption and access control is often more cost-effectively performed in the enterprise subsystem than in the RF subsystem.
Weaknesses:
■ Adversaries can often obtain valuable information from the identifier alone. For example, knowledge of the EPC manager ID and object class bits in certain EPC formats may reveal the make and model of a tagged object concealed in a container. An adversary might target containers based on the perceived worth of their contents.
■ Placing data in the enterprise subsystem makes the availability of that data contingent on the availability of the network. Retrieving data over a network also introduces a small delay, which could be unacceptable for some applications. Section 3.3.3 discusses why organizations might choose to store data on tags even after taking into consideration the risks of doing so.
5.2 Operational Controls
There are several types of operational controls:
■ Physical access controls restrict access to authorized personnel where the RFID systems are deployed.
■ Proper placement of RF equipment helps avoid interference and reduce hazards from electromagnetic radiation.
■ Organizations can destroy tags after they are no longer useful to prevent adversaries from gaining access to their data.
■ Operator training can help ensure that personnel using the system follow appropriate guidelines and policies.
|
|||||
|
5-4
|
|||||
|
Section 5: RFID Security Controls
|
||||||
|
■ Information labels and notice can inform users of the intended purposes of the RFID system and simple methods users can employ to mitigate risk.
The sub-sections below discuss operational controls for RFID systems in more detail.
5.2.1 Physical Access Control
Control: Physical access controls include fences, gates, walls, locked doors, turnstiles, surveillance cameras, and security guards. When the objective is to limit radio communication over a short distance, room walls or partitioned stalls might provide adequate protection if they are opaque to the relevant radio frequencies that the RF subsystem uses.
Applicability: All RFID implementations except those in which RFID tags or other system components are in public areas.
Benefits: Physical access controls limit the ability of an adversary to get close enough to RFID system components to compromise RFID data security or to modify, damage, or steal RFID system components. Physical security applies to all RFID subsystems. In the RF subsystem, the primary objective of the control is to prevent unauthorized radio communications. In the enterprise and inter-enterprise subsystems, the primary objective is to prevent physical access to system components.
Examples of risks that are mitigated by physical access controls include:
■ Unauthorized reading and writing of tag data,
■ Rogue and cloned tags,
■ Reader spoofing,
■ Denial of service resulting from radio interference or unauthorized commands,
■ Targeting,
■ Physical destruction of RFID equipment, and
■ HERF/HERO/HERP. Weaknesses:
■ Physical access controls are not a countermeasure for radio interference from legitimate radios located within a perimeter designed to block external emissions,
■ The effective range of RF signals may be much longer than stated operating ranges, thereby allowing many attacks to occur using customized directional antennas and other technologies (see Section 2.3.3.3 for additional information on relevant operating ranges),
■ Physical access controls do not protect against attacks by insiders (i.e., those granted access to the area),
■ HERF/HERO/HERP still exists with respect to radiation emitted within the physical perimeter, and
■ Physical controls may fail to contain radio signals as expected if ductwork or other openings allow radio signals to escape.
|
||||||
|
5-5
|
||||||
|
Guidelines for Securing RFID Systems
|
||||||||
|
5.2.2 Appropriate Placement of Tags and Readers
Control: RFID system equipment can be placed to minimize unnecessary electromagnetic radiation. Tags and readers can be kept away from:
■ Fuel, ordnance, and other materials that could cause harm if exposed to electromagnetic radiation,
■ Humans and sensitive products (e.g., blood, medicine) that might be harmed by sustained exposure to RF subsystem radiation,
■ Metal and reflective objects that can modify and amplify signals in unintended and potentially harmful ways, and
■ Legitimate radios with which the RF subsystem communication will cause interference.
Applicability: All environments in which the organization deploying RFID systems determines the location of the RF equipment (which excludes many consumer and supply chain applications).
Benefits:
■ Reduced risk of interference with legitimate radios
■ Reduced risk of eavesdropping and unauthorized RF subsystem transactions
■ Mitigation of HERF/HERO/HERP Weaknesses:
■ Tag location cannot always be controlled, such as when tags are used to track mobile items (e.g., hospital cart) or items in transit (e.g., pallet on a truck).
■ Radio interference may persist even if the tags or readers are placed in a new location that is still sufficiently close to other radios.43
5.2.3 Secure Disposal of Tags
Control: Secure disposal involves physically or electronically destroying tags, as opposed to just discarding them, when they are no longer needed to perform their intended function. Physical destruction may involve manual tearing or shredding using a paper shredder. Electronic destruction can be accomplished by using a tag’s kill feature or using a strong electromagnetic field to render a tag’s circuitry permanently inoperable. When a tag supports an electronic disabling mechanism, it usually is the preferred way to disable a tag before it is disposed because it can be accomplished without touching each tag, thereby reducing the cost of the effort. The kill feature is also discussed in Section 5.3.3.3.
Applicability: RFID applications in which the continued operating presence of a tag after it has performed its intended function poses a business intelligence or privacy risk (e.g., an adversary can subsequently use the presence of the tag to track items or people).
Benefits: Destroying or disabling tags:
■ Eliminates the possibility that they could be used later for tracking or targeting, and
|
||||||||
|
In this situation, a panel or wall of grounded wire fencing between the two RF sources is a possible alternative means to reduce interference.
|
||||||||
|
5-6
|
||||||||
|
Section 5: RFID Security Controls
|
||||||
|
■ Prevents access to sensitive data stored on tags.
These benefits apply to both business intelligence and privacy risks.
Weaknesses:
■ Even if minimal, the effort it takes to destroy a tag increases the tag’s life cycle cost, which is a concern if very low costs are required to justify an RFID-enabled business process.
■ Destruction of a tag precludes the ability to use it for future value-added applications such as post-sale product support, targeted recalls, receipt-free returns, expiration date monitoring, and sorting assistance for recycling.
5.2.4 Operator and Administrator Training
Control: Operator and administrator training provides personnel with the skills and knowledge necessary to comply with RFID usage, IT security, and privacy policies, as well as agreements with external organizations. In most RFID implementations, personnel will perform various roles, which might require different training materials for each role. For example, an administrator of middleware might need different information than an operator of a mobile reader. Appropriate security and privacy training addresses at least three points:
■ What constitutes unauthorized use,
■ How to detect that unauthorized use might be occurring, and
■ To whom to report violations.
If HERF/HERO/HERP risks are present, appropriate security training covers mitigation techniques, such as safe handling distances.
If tags are destroyed or recycled, training should cover how to perform these functions. For example, operators might be trained how to clear tag memory before reuse.
Applicability: All RFID implementations.
Benefits: Operator training helps ensure that the system is used and maintained properly. Training also helps operators identify security violations and take appropriate actions to prevent their reoccurrence.
Weaknesses: Training alone cannot ensure proper operation of the system or compliance with policy.
5.2.5 Information Labels / Notice
Control: A written message is affixed to or distributed with each tag or is posted near readers. The notice may inform users of the purposes of the RFID system or advise users on how to minimize privacy or other risks (e.g., place an RFID-enabled access card or transponder in metal foil or a sleeve that shields RF radiation when the card or transponder is not in use).
Applicability: All applications in which there is a risk that could be mitigated with simple informational messages. The control is particularly relevant to consumer applications in which privacy is a concern.
|
||||||
|
5-7
|
||||||
|
Guidelines for Securing RFID Systems
|
|||||||
|
Benefits: Information labels or notices can communicate basic information about risks that might otherwise be left unknown by users that are able to take simple steps to mitigate the risk (e.g., remove a tag or place it in a shielded sleeve).
Weaknesses: Distributing a notice is no guarantee that it will be read or understood. Notice is not an appropriate communications medium for complex concepts or instructions that may require formal training.
5.2.6 Separation of Duties
Control: RFID system duties are distributed among various personnel roles to minimize the damage resulting from an inadvertent or malicious activity of a single person. The general principle of the control is that malicious collusion between two or more authorized users is much less likely than one person engaging alone in inappropriate behavior.
One example of separation of duties is having different personnel (1) attach tags to objects and (2) read the tags. If an individual performed both functions, the individual could intentionally put the wrong tag on an object to circumvent the objectives of the business process. For example, a store clerk could affix tags intended for low-priced items on high-priced items, and then later work the checkout scanner while the clerk’s accomplice purchased the items. The system would not know that the tags had been switched, but if another person performed the checkout, he or she might be suspicious of the checkout total, which could uncover the plot.
Applicability: RFID applications in which an insider might have a motive to perform unauthorized RFID transactions. This scenario is most likely to occur when tags support commercial transactions, especially those related to high-value objects.
Benefits: Separation of duties helps to reduce fraud and malicious damage, because any user attempting to engage in such activities would be forced to collude with at least one other user. Separation of duties also reduces errors, because a second operator will often catch mistakes made or missed by the first.
Weaknesses: Multiple employees still could collude to commit fraud or violate the RFID usage policy. Also, organizations with a limited staff may not be able to perform complete separation of duties.
5.2.7 Non-revealing Identifier Formats
Control: RFID tags are assigned identifiers using identifier formats that do not reveal any information about tagged items or the organization operating the RFID system. Non-revealing identifier format options include serially assigning identifiers and randomly assigning identifiers.44
In contrast, if an adversary reads an identifier that is encoded with a standardized format, such as the EPC format, that adversary may be able to discern the manufacturer or issuer of the item, as well as the type of item. For example, all cans of a soft drink from a certain manufacturer will have the same EPC manager
|
|||||||
|
A related control is rotating identifiers. Auto-rotating tags store a list of identifiers and cycle through the list when queried. To support multiple identifiers, databases in the enterprise subsystem must associate each identifier in the list to the particular item. The benefit of rotating identifiers is that organizations can make it more difficult to identity and track particular items as well as hide the type of item. Random and serialized identifiers, on the other hand, may not reveal information about the type of item, but since these identifiers are fixed, once they are revealed that particular item can be tracked. One weakness to rotating identifiers is that a rogue reader can easily obtain the complete list of identifiers through repeated queries. Therefore, this control is more appropriate when the primary threat is eavesdropping. While research is being conducted on the concept of rotating identifiers, it is not specified in any RFID standard and proprietary designs are not widely commercially available.
|
|||||||
|
5-8
|
|||||||
|
Section 5: RFID Security Controls
|
|||||||||||||
|
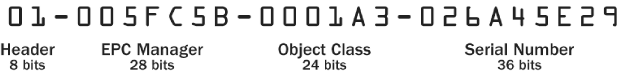
ID and object class bits if their identifiers are encoded in an EPC identifier format. Figure 5-1 shows an example 96-bit EPC and how it can be parsed into the four aforementioned, individual fields.
|
|||||||||||||
 |
|||||||||||||
|
Figure 5-1. Example 96-bit EPC
|
|||||||||||||
|
Tags must have programmable identifiers to support the control. Even tags that are designed to support standard tag formats can still be assigned non-standard identifiers in the field. However, some tags have factory-initialized identifiers that cannot be modified after manufacture.
Applicability: Any applications in which the implementing organization determines that the revelation of a tag’s identifier is a business intelligence risk.
Benefits: Adversaries cannot obtain information about tagged items from the identifier alone.
Weaknesses:
■ The use of non-revealing identifier precludes an organization from realizing benefits that come from standard identifier formats that reveal organization and item type information. For example, standard identifier formats are particularly advantageous when designing and maintaining distributed databases in inter-enterprise systems. Lookup and query functions are much easier in such databases when the identifiers provide information on where item data is located.
■ If identifiers are assigned randomly, then a potential exists that two tags may be assigned the same identifier. The likelihood of such an event is very small, but it could lead to errors in the supported business process.
■ If there is logic in how the identifiers are assigned, an adversary may uncover the method that is used, which would defeat the control. For example, an adversary knows that an identifier was assigned to a certain item and that all items of that type were assigned sequentially, then the adversary may be able to deduce the approximate range of identifiers that correspond to items of that type. Similarly, when identifiers are serialized, the adversary may be able to deduce the approximate time of the assignment based on the identifier.
5.2.8 Fallback Identification System
Control: A fallback identification system provides an alternative means to identify, authenticate, or verify an object when the RFID system is unavailable or an individual tag is inoperable. Options include text labels and AIDC technology such as bar codes.46 The fallback may consist of just an identifier, or it may also include additional data about the tagged object. The fallback system is accompanied by standard operating procedures and operator training to ensure that personnel know when and how to use it.
|
|||||||||||||
|
When two tags are assigned the same identifier, the event is called a collision. If identifiers are randomly assigned, a collision is expected after approximately the square root of the total number of possible identifiers. Therefore, in the case of a 96-bit EPC, a collision is expected after approximately 248 tags, which is an enormous number not likely to be encountered in most RFID applications.
If the RFID application’s objective is to provide security or authentication, then a fallback technology such as holograms or other optical security features may be used.
|
|||||||||||||
|
5-9
|
|||||||||||||
|
Guidelines for Securing RFID Systems
|
||||||
|
Applicability: All RFID applications.
Benefits: Duplicating tag identifiers and data on a label provides a fallback in case of malicious or accidental tag damage, reader malfunction, or enterprise subsystem network outage. The redundant data can also be used to verify that tag data has not been altered improperly.
Weaknesses: This control has several potential weaknesses, including:
■ Damage to the tag could render both the stored data and the printed data unusable. Similarly, many enterprise subsystem outages that would affect the RFID system would also affect its fallback alternative.
■ The data stored on the label is visible, so it may be easier for unauthorized parties to gain access to it than it would be to read the data from the tag.
■ The text label or bar code might not provide the same data capacity as RFID memory, although two-dimensional bar codes can encode at least as many bits as standards-based tag identifiers.
■ Text labels and AIDC technologies are static, so they do not provide a complete fallback solution for applications in which tag data changes over time. However, some identification information is still likely to be better than none in most applications.
5.3 Technical Controls
There are a number of technical controls currently available for RFID systems, and many others are under development in industrial and university research labs. This section focuses on technical controls that are commercially available as of the publication date of this document. Supplementary information on selected emerging security technologies is provided in footnotes. Many of the technical controls listed are specified in standards, while others are available only in proprietary systems.
Many technical controls related to a tag require the tag to perform additional computations and to have additional volatile memory. Accordingly, a tag that uses such technical controls requires a more sophisticated microchip than those that do not use such controls. In the case of passive tags, the tags may also need to be closer to readers to obtain the required power to perform these computations. Alternatively, readers may need to operate at greater power levels, although this may not be feasible or permitted in many cases. These inherent characteristics of passive tags can limit the use of certain technical controls in some environments.
Technical controls exist for all components of RFID systems, including the RF, enterprise, and inter-enterprise subsystems. This section focuses on technical controls for the RF subsystem. Many controls also exist for the enterprise and inter-enterprise subsystems, but these typically apply to IT systems in general rather than to RFID systems in particular. Readers are encouraged to read other NIST IT system and network security guidelines, many of which are listed in Appendix D.
The general types of RF subsystem controls include controls to:
■ Provide authentication and integrity services to RFID components and transactions,
■ Protect RF communication between reader and tag, and
■ Protect the data stored on tags.
|
||||||
|
5-10
|
||||||
|
Section 5: RFID Security Controls
|
||||||||
|
Examples of each of these types of controls are discussed in depth in Sections 5.3.1 through 5.3.3, respectively.
5.3.1 Authentication and Data Integrity
While a wide variety of authentication methods exists for IT systems, the most common techniques for the RF subsystem of RFID systems are passwords, keyed-hash message authentication codes (HMAC), and digital signatures. In some cases, the primary objective of the authentication technology is to prevent unauthorized reading from or writing to tags. In other cases, the objective is to detect cloning of tags. Authentication techniques based on cryptography often provide integrity services for data included in the authentication transaction; in other words, an adversary cannot modify data in the transaction without the reader or tag detecting the change.
5.3.1.1 Password Authentication
Control: A tag does not permit password-protected commands to be executed unless they are accompanied by the correct password. Protected commands may include those that support reading and writing of tag data, memory access control (Section 5.3.3.1), and the kill feature (Section 5.3.3.3).
Organizations properly implementing this control will develop a password management system to support it. The password management system addresses all stages of the password, including generation, conveyance, and storage. From a security perspective, effective password generation involves random selection of each password. 47 Whenever possible, the passwords are assigned to each tag in a physically secure environment to reduce the likelihood of eavesdropping. Tags should not share passwords, although this may not be administratively feasible in some environments, such as those in which the reader is not expected to have access to a networked database of tag passwords. In inter-enterprise applications such as supply chains, multiple organizations may need to access databases that contain tag identifiers and passwords. Authenticating external entities likely will require additional security systems. While in traditional IT systems, passwords are often changed on a periodic basis (e.g., every 90 days); in RFID systems, such changes may be infeasible, especially if the tags are not always accessible to the organization assigning the passwords.
Applicability: Any application where authorized execution of a particular command represents a business process, business intelligence, privacy, or externality risk.
Benefits: The likelihood that tags will be used for unauthorized purposes is greatly reduced.
Weaknesses:
■ Password management for RFID systems is complex, particularly if the application deploys large number of tags or if passwords must be shared across organizational boundaries as might be the case in supply chains.
■ Adversaries can intercept passwords transmitted over the air and then use them at a later time to perform unauthorized transactions.48
|
||||||||
|
For additional information on proper random number generation, see E. Barker and J. Kelsey, Recommendation for Random Number Generation Using Deterministic Random Bit Generators, NIST Special Publication 800-90, June 2006. RFID passwords are often transmitted “in the clear” (i.e., without cryptography to hide them), which makes them particularly vulnerable to eavesdropping. The cover-coding technique described in Section 5.3.2.1 mitigates this risk for tags that support cover coding, but this technique is not without its own limitations.
|
||||||||
|
5-11
|
||||||||
|
Guidelines for Securing RFID Systems
|
|||||||||
|
■ If the application environment precludes access to an on-line tag password database (e.g., mobile readers in remote locations), then the implementing organization may need to take simplifying measures, such as assigning the same password to multiple tags. In cases such as these, the compromise of a single password could compromise the integrity of the entire system.
■ RFID passwords can be obtained through brute force methods (i.e., cycling through all possible passwords) when the tag technology is limited to short passwords.49
■ RFID passwords can be revealed through power analysis attacks on some types of passive tags.50 5.3.1.2 Keyed-Hash Message Authentication Code (HMAC)
Control: Both the reader and the tag share a common secret key that can be used in combination with a hash algorithm to provide one-way or mutual authentication between tag and reader. When HMAC is applied to messages, it also ensures the integrity of data in the messages. HMAC is specified in FIPS Publication 198.51 HMAC supports any cryptographic hash algorithm, but Federal agencies must use one of the secure hash algorithms (SHA) specified in FIPS Publication 180-2.52 HMAC is not specified in any RFID standard, but it is available in proprietary designs.
Applicability: Applications in which passwords are considered to offer an inadequate authentication mechanism, perhaps because the risk of eavesdropping is high. Applications that require evidence of a tag’s authenticity.
Benefits: The advantages of HMAC relative to password authentication include that HMAC:
■ Provides evidence of tag’s authenticity,53
|
|||||||||
|
49
|
|||||||||
|
For example, EPC Class-1 Generation-1 UHF tags support a maximum password length of 8-bits, which enables only 256 possible passwords. An adversary can cycle through 256 passwords in a matter of seconds. EPC Class-1 Generation-2 tags support 32-bit passwords and, therefore, 232 possible passwords, which is sufficient if the passwords are randomly generated. However, if the binary password is based on American Standard Code for Information Interchange (ASCII) characters, then the actual number of possible passwords may be much smaller. For example, the ASCII representation of a 4-digit decimal number (a common length for personal identification numbers) is 32-bits, but results in only 10,000 possible combinations, a number certainly vulnerable to brute force attacks. Tags typically do not lock-out readers after a certain number of incorrect guesses, which means a determined adversary can continue to guess the password as long as the tag remains within the operating range of the adversary’s reader.
The power analysis attack (also called a side channel attack) is based on the fact some passive tags use different levels of power depending on how close the password provided is to the actual password. For instance, if the first bit in a password is incorrect, the tag uses less energy than it would if the eighth bit is incorrect, given how the algorithm is hard-coded into the tag’s circuitry. These power differences are detected in the backscatter to the reader, but it requires that the adversary be reasonably close to the tag to get effective measurements. If such measurements are possible, an adversary can determine the password much more quickly than by using a brute force method. Lab experiments proved that someone could crack the 8-bit password protection found on EPC Class-1 Generation-1 tags in one minute. For more information, see Y. Oren and A. Shamir, "Power Analysis of RFID Tags," discussed at the Cryptographers Panel of the Fifteenth RSA Conference, San Jose, 2006.
The FIPS HMAC is a generalization of HMAC described in H. Krawczyk, M. Bellare, and R. Canetti, "HMAC: keyed-hashing for message authentication," Internet Engineering Task Force, Request for Comments (RFC) 2104, February 1997 and American Bankers Association, "Keyed Hash Message Authentication Code," American National Standards Institute (ANSI) X9.71, Washington, D.C., 2000.
The specified algorithms are SHA-1, SHA-256, SHA-384, and SHA-512. While SHA-1 offers the lowest level of assurance and is not recommended for use in digital signatures beyond 2010, it is likely most applicable to RFID systems due to its greater computational efficiency relative to the other algorithms. See NIST Special Publication 800-57, Recommendation on Key Management, Part 1 for additional information.
The evidence of tag or item authenticity is provided by authenticating a tag to a reader, which can be accomplished when the tag computes and returns an HMAC using a random challenge provided by the reader. Mutual authentication is also possible if both tag and reader provide challenges to each other. Passwords, on the other hand, typically only are used to authenticate readers to tags, thereby protecting the tag against rogue commands. If the tag were to authenticate itself to a
|
|||||||||
|
50
|
|||||||||
|
51
|
|||||||||
|
52
|
|||||||||
|
53
|
|||||||||
|
5-12
|
|||||||||
|
Section 5: RFID Security Controls
|
||||||||
|
■ Does not transmit secrets over-the-air, which eliminates the risk of eavesdropping inherent with clear text passwords.
Weaknesses:
■ The management of HMAC keys provides similar challenges to those of password management and may not be practical if mobile readers do not have reliable access to an HMAC key management system.
■ The authenticity claims associated with HMAC authentication only hold when the HMAC key remains secret. If an adversary has physical access to a tag and can obtain its HMAC key, then the adversary can clone the tag. This attack, however, assumes that that the adversary has some level of expertise, both in reverse engineering the HMAC-capable tag and in producing a reasonable facsimile.
■ When HMAC keys are shared across organizations, authenticity claims rely on an implicit trust between the organizations that may not be present in practice.
■ HMAC requires greater computing power than password comparisons, and therefore requires more complex tag designs to support it.
5.3.1.3 Digital Signatures
Control: Readers digitally sign tag identifiers, time stamps, and related event data to provide for non-repudiation of tag transactions. The resulting signatures are stored on tags for subsequent verification, although recording signatures in enterprise subsystem databases provides additional assurance of the tag’s chain of custody.
Digital signatures are based on asymmetric cryptography, also commonly referred to as public key cryptography. Federal agencies implementing digital signature technology must comply with FIPS Publication 196, Entity Authentication Using Public Key Cryptography. The use of digital signature technology in the context of RFID systems is also referred to as authenticated RFID. It typically works as follows:
1. The tag has a permanent unique identifier than cannot be modified after manufacture.
2. The reader generates a public/private key pair and obtains a corresponding public key certificate.
3. The reader uses a specified hash algorithm to compute a message digest of the tag’s identifier and possibly other transaction-related data, encrypts the message digest with its private key to create a digital signature for the transaction, and stores the resulting signature on the tag.
4. Other readers read the signature, decrypt it with the first reader’s public key, and compute the identical message digest to determine if a match exists. If the message digests match, then verification procedure provides assurance of the authenticity of the earlier transaction. If the message
|
||||||||
|
reader using a password, an adversary could simply use a rogue reader to obtain the password and then re-use with a legitimate reader. HMAC provides an effective countermeasure to this attack because it never reveals the secret key during any of its transactions.
Integrity protection is when either tag or reader computes an HMAC using as input the data for which integrity protection is desired. Any change in the data results in a different value of the HMAC, which would be detected by the receiving entity.
|
||||||||
|
5-13
|
||||||||
|
Guidelines for Securing RFID Systems
|
||||||||
|
digests do not match, then either the transaction data has been altered or an unauthorized device created the digital signature.
5. The other readers can store their own event transactions on the tag or record them in enterprise subsystem databases for later queries regarding the tag’s chain of custody.
Applicability: Applications that require more robust evidence of authenticity than provided by HMAC technology, including authentication of multiple chain of custody events. Applications that require verification of authenticity without network connectivity.
Benefits: Digital signatures offer several advantages relative to HMAC authentication, including:
■ Digital signature systems do not require tags to store cryptographic secrets. Instead, readers maintain private keys. In password and HMAC authentication, both the tag and the reader must share a secret for the system to function, but there are no shared secrets in the public key cryptosystems that support digital signatures. Tags are typically much more vulnerable to compromise than readers, so eliminating the need to store secrets on tags enhances overall system security. One private key and one or more public key certificates are on the reader. Integrity is needed for the certificates, but not confidentiality.
■ In many cases, digital signatures do not require network connectivity to successfully perform the authentication function. In password and HMAC authentication, a reader is unlikely to have the memory to store the passwords or keys for large numbers of tags. With digital signatures, a reader may only need to store the public key certificate of the entity that initialized the tags or perhaps a relatively small number of readers. In inter-enterprise systems, each participating organization only has to share the public keys of its readers rather than provide its partners reliable network access to a password or secret key database.
■ Digital signatures are compatible with existing RFID tag standards. HMAC requires tags to support hash algorithms and to implement a challenge-response protocol, neither of which are included in existing RFID standards. On the other hand, in authenticated RFID systems, tags can receive, store, and transmit digital signatures with existing read and write commands because the complexity resides in readers or middleware.
Weaknesses:
■ A system of digital signatures requires a public key infrastructure (PKI), including registration and certification authorities, revocation functions, and associated policies and practice statements. Successfully implementing and operating a PKI requires careful planning and considerable expertise. In addition, readers or middleware need to support digital signature and other PKI functionality that is not commonly found in current RFID technology.
■ Digital signatures systems require more memory than found on many current tags. For example, NIST recommends that RSA signatures have a length of 1024 bits, and a length of 2048 bits after 2010. 55 Additional memory is required to store identifying information related to the transaction. Providing chain of custody evidence requires storing a digital signature and related identifying information for each transaction.
|
||||||||
|
Elliptic curve cryptography can reduce the size of signatures. Elliptic curve methods provide comparable assurance to 1024bit RSA signatures with 163 bits, and to 2048-bit RSA signatures with 224 bits. This approach combined with greater memory on tags may alleviate storage concerns over time.
|
||||||||
|
5-14
|
||||||||
|
Section 5: RFID Security Controls
|
||||||||
|
■ Digital signatures that are not generated by the tag are subject to replay attacks. An adversary could query a tag to obtain its evidence of authenticity (i.e., the digital signature created by a previous reader) and then replicate that data on a cloned tag.
■ The use of digital signatures to support authentication of readers to tags would require tags to support relatively complex cryptographic functions beyond the capacity of most common tag designs. Consequently, password or symmetric key authentication systems likely will support tag access control, as opposed to tag authenticity verification, for the foreseeable future.
5.3.2 RF Interface Protection
Several types of technical controls focus on the RF interface to tags, including:
■ Cover-coding can be used to obscure the content of messages from readers to tags.
■ Data can be encrypted prior to its transmission.
■ Shielding can be installed to limit eavesdropping and rogue scanning.
■ The selection of an operating radio frequency can be used to avoid interference from other sources or achieve certain operating characteristics such as the ability to propagate through metals, liquids, and other materials that are opaque to many frequencies.
■ Reader and active tag transmission characteristics can be tuned to reduce the likelihood of eavesdropping and help mitigate interference and the hazards from electromagnetic radiation.
■ The RF interface for tags can be temporarily shut off to prevent unauthorized access when the tag is not expected to be used for authorized purposes.
■ The RF interface may be turned off by default until a user takes an action to activate it.
■ Readers may periodically poll tags to determine the presence of the tags, assess system health, and acquire environmental data.
These controls are discussed further in Sections 5.3.2.1 through 5.3.2.8.
5.3.2.1 Cover-Coding
Control: Cover-coding is a method for hiding information on the forward channel from eavesdroppers.
In the EPCglobal Class-1 Generation-2 standard, cover-coding is used to obscure passwords and information written to a tag using the write command. The EPCglobal Class-1 Generation-2 cover-coding protocol works as follows:
1. The reader sends a message to the tag requesting a key.
2. The tag generates a random 16-bit number (i.e., the key) and returns it to the reader.
3. The reader produces ciphertext (i.e., a message unintelligible to an eavesdropper who cannot intercept the key) by applying an exclusive-or (XOR) operation56 to the key and the plain text.
|
||||||||
|
The XOR operation is a binary operation denoted with the symbol “⊕” that works as follows: 1 ⊕ 1 = 0; 1 ⊕ 0 = 1; 0 ⊕ 1 = 1; 0 ⊕ 0 = 0. When the XOR operation is applied to two multi-bit strings, the XOR operation is applied to the first bit of the each string to produce the first bit of the result, the second bit of each string to produce the second bit of the result, and so
|
||||||||
|
5-15
|
||||||||
|
Guidelines for Securing RFID Systems
|
||||||||||
|
4. The reader sends the ciphertext to the tag.
5. The tag applies the XOR operation using the ciphertext and the key it generated to recover the plain
text.57
Cover coding is an example of minimalist cryptography because it operates within the challenging power and memory constraints of passive RFID tags.58 By itself, the XOR operation would be considered a trivial encryption algorithm in traditional cryptography, but it nonetheless mitigates risk to an acceptable level in many RFID environments.
Figure 5-2 illustrates how cover-coding works. As shown in the figure, the passive tag’s back channel signal is weaker than the reader’s forward channel signal. This will always be the case for a passive tag, which must use the forward channel to power both its computations and the backscattered signal. In the figure, the adversary is able to eavesdrop on the forward channel but not the back channel. So long as this condition holds, the adversary will not be able to learn the random number sent from the tag and therefore will be unable to decipher cover coded information.
|
||||||||||
 |
||||||||||
|
Figure 5-2. Cover-Coding
|
||||||||||
|
on. To work properly, the inputs to the XOR operation must be of equivalent length, and the output is also of the same
length.
The XOR operation is symmetric. For instance, given key K, plaintext P, and ciphertext C, if P ⊕ K = C, then C ⊕ K = P.
For more information on minimalist cryptography, see A. Juels, "Minimalist cryptography for low-cost RFID tags," in the
Fourth Conference on Security in Communication Networks, 2004, pp. 149-164.
|
||||||||||
|
5-16
|
||||||||||
|
Section 5: RFID Security Controls
|
||||||
|
Applicability: Cover coding is useful when eavesdropping is a risk that requires mitigation, but adversaries are expected to be at a greater distance from the tags than readers. Intelligible reception of back channel signals from a passive tag requires proximity of less than four meters in most applications. In many applications, an adversary’s reception equipment would be conspicuous if it were located within this range. In contrast, reader signals can be detected at distances of a kilometer or more under ideal conditions.
Cover-coding is designed for RF subsystems in which the forward channel carries stronger signals than the back channel, which essentially limits the control to passive tags. EPCglobal Class-1 Generation-2 technologies support cover-coding. Proprietary technologies support similar features.
Benefits: Cover-coding helps prevent the execution of unauthorized commands that could disable a tag or modify the tag’s data. Consequently, cover-coding mitigates business process, business intelligence, and privacy risks.
Weaknesses:
■ If an adversary can intercept a key distributed on the back channel, the adversary could decrypt any ciphertext message generated with that key.
■ The effectiveness of cover-coding depends on the performance of the tag’s random number generator. If the random number is predictable due to a flaw in the tag’s design or cryptanalysis, then an adversary can learn the key and decrypt subsequent communication.
5.3.2.2 Encryption of Data in Transit
Control: Data collected or processed by the tag is encrypted prior to over-the-air transmission.
Applicability: Applications that require an effective countermeasure to the threat of eavesdropping and for which cover coding offers inadequate protections. Tags typically only require on-board encryption capabilities to protect the confidentiality of data in transit if they collect or process data from sensors or other directly connected sources. In these cases, no alternative exists to hide the content of the data over-the-air because the data originates on the tag.
On-board cryptography for confidentiality is not required for applications in which readers are the only source of data. In these cases, the data can be encrypted in the enterprise subsystem or by a reader before it is written to the tag and then retrieved in its encrypted form from the tag when needed. If the tag never has to perform computations on the data, then it never has to decrypt it, but merely store it. Encryption of data at rest is also discussed in Section 5.3.3.2.
Proprietary tag designs support encryption for over-the-air confidentiality, but EPCglobal and ISO/IEC 18000 standards do not as of the date of this publication.
Benefits: Encryption of data in transit prevents successful eavesdropping of over-the-air RFID transactions.
Weaknesses:
■ Data encryption requires a key management system, which can be complex to manage and operate.
■ Cryptographic functions may introduce an unacceptable delay in RFID systems that require very fast read or write transactions.
|
||||||
|
5-17
|
||||||
|
Guidelines for Securing RFID Systems
|
||||||
|
■ Cryptographic functions require additional power to complete, which could impact applications that use passive tags.
■ Tags that support onboard encryption currently are more costly than those that do not. One reason for the increased cost is that onboard encryption requires additional logic gates to perform the necessary computations. Most low-cost passive tags do not have enough logic gates to perform complex encryption algorithms.59
5.3.2.3 Electromagnetic Shielding
Control: RF shielding encloses an area with a conducting material that limits the propagation of RF signals outside of the shielded area. Shielding can vary in size and form depending on the application.
For example, some RFID-enabled travel documents are protected by a metallic anti-skimming material. This material helps to prevent adversaries from reading the embedded tag when the passport cover is closed. Shipping containers are sometimes shielded to prevent the reading of tags during transit. Shielding is also placed in walls, partitions, or stalls to prevent RF emissions from leaving a confined area. When readers are placed in tunnels on industrial production conveyor belts, the tunnels may be shielded to reduce radio interference. Wrapping a tag in aluminum foil is also an effective means of shielding.
Figure 5-3 shows how shielded partitions can separate collocated readers to prevent interference. The readers near forklift A can operate without inadvertently reading tags on boxes on forklift B due to the shielding in the partition that separates the portals. Shielding may be necessary when middleware is unable to correctly filter duplicate read events from the two portals.
|
||||||
|
59 Low cost tags currently have about 10,000 logic gates. The most efficient implementations of AES require 3,400 gates, which suggests that cryptographic support on low cost tags may be more feasible in the future. Source: M. Feldhofer, J. Wolkerstorfer and V. Rijmen, “AES implementation on a grain of sand,” IEEE Proceedings, Information Security, vol. 152, issue 1, pp. 13-20, October 2005.
|
||||||
|
5-18
|
||||||