General characteristic (of dissertation)
Topicality of the research subject:
Nowadays the cybercrime faster increases. Writing malicious code is a way of stealing information and using it in owns aims. There is an opposite arises. It makes the new methods, approaches for struggle with illegal operations of malicious code. This dissertation examines the types of malicious code and methods to struggle with them.
Scientific character:
Development methods to detect (to lurking) malicious code is integral part of dissertation, which demands incessant improvement, because in virtual world of crime new types of viruses always appears. They are need to be examined and new methods for their disclosure and destroys are made.
Aims and tasks of dissertation:
- Analyzing influence of computer viruses on programming complexes with different scales (or types).
- Development the research algorithm of computer virus and the process of executing experimental research of computer viruses.
- Systems analyzing on executing experimental research base, detection subsystem of viruses and methods of their work with programming environment.
- Analyzing computer viruses detection methods.
- It is building computer virus structure system model and functional classification of computer viruses. Development of requirements to virus behavioral model and analyzes of current behavioral models which correspond with current requirements.
- Development of model of programming environment and mathematical mechanism, which helps to describe the programming objects and their behavior.
- Development of behavioral models by abstract computer virus, general classes of computer viruses and their subsystems.
- Development of architecture, working algorithms and programming realization of individual (private) detection system of viruses and it’s testing.
- Development of system analyzing methods of destabilize programming influence.
Objects of research:
Anti-virus components: the interaction between modules, an anti-virus signature database, the "engine" antivirus, driver for quick real-time access to the file system, blocking assignments, drawing up a list of quarantine, code generation for infection, the interception system events, monitoring activity of work.
Subject of the research:
There is realization of the antivirus engine for the embedment it in corporate software.
Area of the research is types of malicious code and methods to struggling against them.
The theoretical and methodological foundations of the research
There are the structures of executable files, conditions of work processes in the operating system, virus detection methods and ways to treating the contaminated objects.
Scientific novelty:
Scientific novelty is development of new algorithms, implementation modules of protecting system, designs the necessary structure of antivirus protection.
The main provisions, the results of dissertation and conclusion
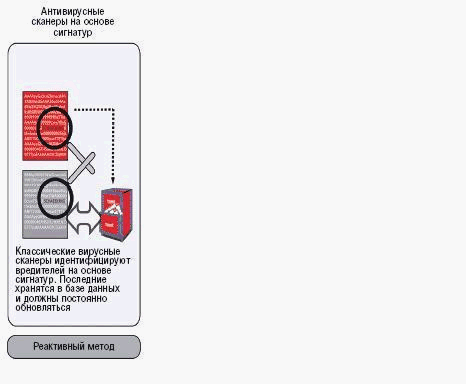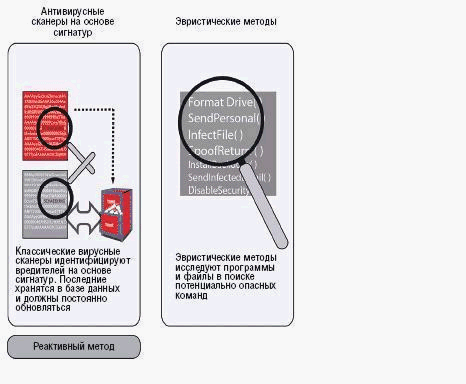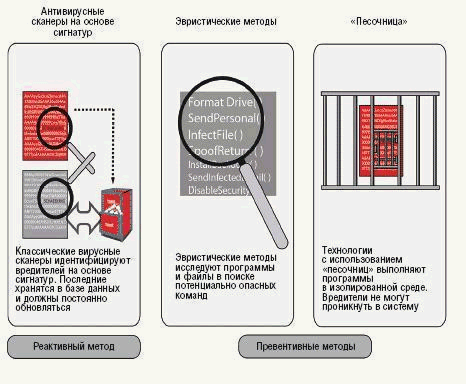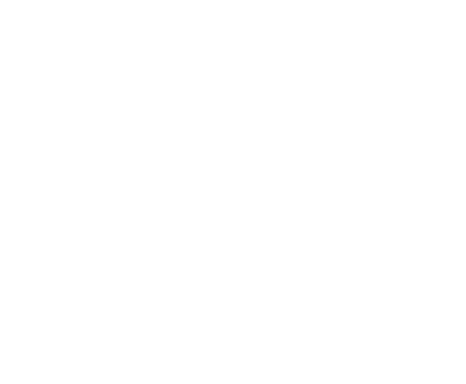
The criminal expectancies are hiding behind attacks which use malicious software and updating of antivirus signatures immediately doesn’t solve security problems. The technology of early disclosure - «sander» (or jail), heuristic methods and blocking behavior can reveal and remove malicious code before it infects system. The classic antivirus software identifies computer viruses by chains of symbols (signatures). They consist of typical for each virus sequence of bytes and show the place of malicious code within infected object. All known signatures are added to database. If a file locks through an antivirus program compares code of file with databases signatures in automatic state. If sequences of symbols are equal than there is a malicious code. The technology is reliable but new viruses will be revealed only after system database updates. This system update will be execute only passing several hour and sometimes passing one day - so much time passed before all manufacture make new signature and take it to clients. During this time user is defenseless against new viruses.
In dissertation it is develop embedded freeware antivirus engine, which can be use to development private security product for commercial aims.
References
1. Appearance on International Conference (subject was «Methods of detecting complex computer viruses»), 2007, DonNTU.
2. Publishing in a collection of conference’s works in 2007, DonNTU. |