Ch.Ye Larionova, N.Ye. Gubenko
One of the most popular methods of protection of multimedia information is the embedding of invisible tags - digital watermark (DWM). Now there is the issue of protection of copyright on the information presented in the digital form. Digital watermark is a special tag, invisibly built into the image, or other signal with the purpose in one way or another to control its use [1].
DWM is used for protection against copying and unauthorized use. Examples could be a photo, audio and video recordings.
Unlike conventional watermarks, DWM may be not only visible but also invisible. Invisible DWMs are analyzed by a special decoder, which makes a decision about their validity. They may contain a certain code of authentic information about the owner, etc. Installation and selection of messages from other information is performed by stegosystem, which has the following architecture (Figure 1).
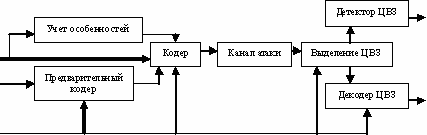
Figure 1 - Block diagram of stegosystem
Here, the preview encoder is a device designed to transform the hidden message into a form, suitable for embedding in the signal-to-container;
stegocoder - a device designed for the insertion of hidden messages in the other data in accordance with their models;
stegodetector is a device designed to determine stegomessages;
decoder is a device that converts a hidden message in an open one. This site may not be available.
At present, there are a large number of algorithms for the implementation of DWM in graphic files. This system was taken as the basis for Cutter’s algorithm [2].
Embedding information is in the spatial domain image. The advantage of this algorithm is that the introduction of DWM is not necessary to calculate the massive transformation of the linear image.
24-bit image format of JPEG or BMP format is RGB-encoding. Embedding is performed in the blue color channel, as human eyes are less sensitive to blue colours.
DWM is built by manipulation of brightness:
I (x,y) є {1,..,L}
or color:
(r (x,y), b(x,y), g(x,y))
Embedding is performed in the blue channel. Image has RGB-encoding. Consider the algorithm for the transfer of one bit of secret information:
si - built-bit
I = {R, G, B} – контейнер,
Р = (х, у) – псевдослучайная позиция, в которой выполняется встраивание.
Secret bit is embedded by modifying the brightness
I (p) = 0.299r(p)+0.587g(p)+0.114b(p):
b' (p)= b(p)+ql(p), если s1=0 и b' (p)= b(p)-ql(p), если s1=1,
where q - constant, which determines the energy of the signal.
Definition of bits by the recipient occurs without the presence of the output image, i.e. blindly. To perform this predicting of the output value, unmodified pixel value based on its neighbors is carried out.
For evaluation of the pixel the values of several pixels located in the same column and in the same row are used [3].
Rating δ'' is presented:
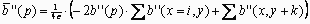
where, c is the number of pixels from top (bottom, left, right) of the estimated pixel (c = 3).
Since DWM in the process of embedding each bit is repeated cr times, we can get cr number of DWM ratings. Secret bits is after averaging variance of pixels ratings and its true value
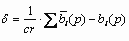
The sign of this difference determines the value of embedded bits.
The developed system, built on the basis of the algorithm described above, has the following algorithm: the opening of the main form of the program, file container, transferring the contents of the file container into a form-dialogue, opening of a dialogue format, receiving of graphic data about the file container, filling in the bit map; job logo in the form of a word, transfering of the logo in the form of the bit sequence (generation of DWM), setting of a key in the form of the word, generation of masking maps (using a CAP generator), preliminary determination of the noise level of container file, filling of the masking card (using a CAP generator), the introduction of DWM in the file container, identifying the level of stego-file noise; evaluation of difference of noise, if necessary, returning to step 7, display of the estimates results, saving the stego-file onto the drive; access to the main form to select a different container file.
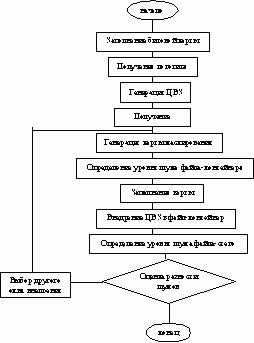
Figure 2. Block diagram of the author's algorithm
Steganografic resistance
During the introduction of the information container-file will be definitely spoilt. But if the used container is only carrying the hidden message, the degree of allowable error of the container should be limited, because the attacker will easily identify the use of stegosystem. Resistance of different stegosystems can be divided into resistant to the detection of transmission of hidden information, and for resistance to the extraction of hidden information. Obviously, such stegosystem is resistant to the identification of transmission of hidden information and it is logical to assume that it is resistant to the reading of the hidden information as well. The converse, in a general case, is incorrect. Stegosystem may be resistant to reading of the hidden information, but the fact of any information under the cover of the container is able to detect an intruder.
In assessing of stegoresistance of the developed system it is taken as a rule that a system is resistant if:
1. an attacker watching the stegocontainer can not visually find that under the cover of the container hidden messages are transferred, and so can not read these messages.
2. a cracker can not identify the embedded logo with software tools.
Literature
1. Оков И.Н., Ковалев Р.М. Электронные водяные знаки как средство аутентификации передаваемых сообщений, 2001.
© Ларионова К.Е. 2009