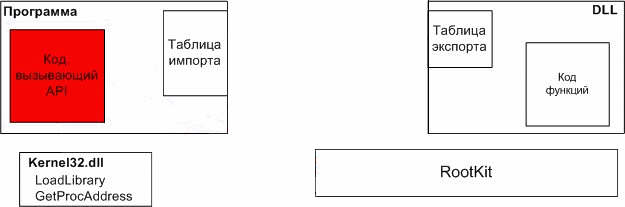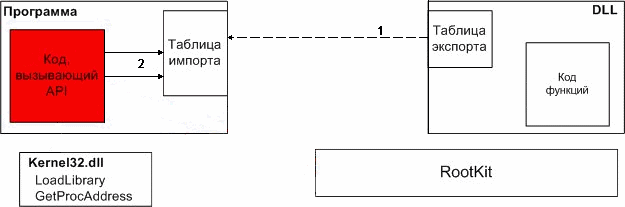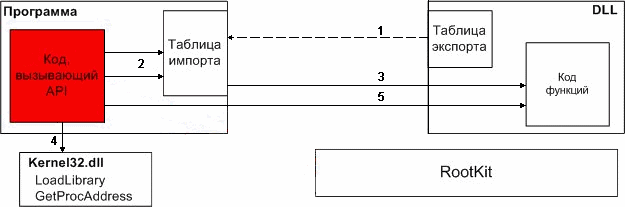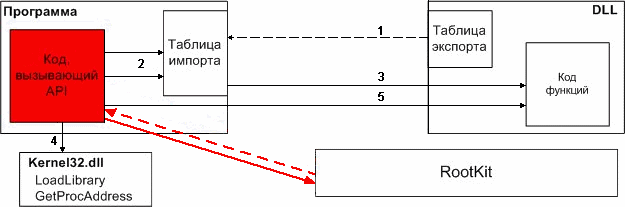
Animation.
scheme splicing functions
(refresh page to re-view)

In modern times, when information technology is widespread, and most staff members are experts in the Internet, at least at the user level, and tend to evade their responsibilities, control of the user is extremely important. Loss of time among the workers during working hours are not engaged in its direct responsibilities e are extremely high, particularly in the area of the Internet. Also important component is the control of access to information, as well as industrial espionage goes to an extremely high level. To control all flows of information that enters or leave the company virtually impossible, because nowadays almost every employee has a workplace in which there is a computer with an Internet or LAN. For all these reasons, the employer is obliged to establish control over every employee of his company, to oversee the activities of information workers. Therefore spyware programs are essential in any enterprise, and their use gives a very large economic effect.
RelevanceThe most convenient solution to this problem is to implement the software, designed to monitor the activities of the user is working with the computer (meaning screenshots, keystrokes). Given the high level of knowledge of today's users, it should be noted that with the help of funds provided by the Internet, often it is easy to bypass the usual means of observation. Thus, currently one of the requirements for the application of this kind is a stealth action program from the user. Ideally, the user does not need to know that his activities being monitored.
AimsThus the purpose of master's work is research on the most modern techniques in the most ubiquitous in businesses and operating systems, the implementation of a software product that uses the most effective methods of concealment, to monitor user activity. And also to build the most effective program that would have been not only hidden, but also provides the most complete information about the activities of the user PCs. To obtain the required result neobhodoimo investigate and find the optimal solution of the following issues::
Similar tasks have been solved for many years, virtually every "respecting" a company has all kinds of analogues, the crucial tasks, as a result there are a few of the most popular solutions. Consider these decisions, incidentally pointing out their advantages and disadvantages.
Actual Spy - the program has expanded opportunities to conduct surveillance over the activities of the user and the core functionality of hiding. Can easily be detected by special software (for example ProcessHunter from Ms-Rem'a) even at the user level. With the help of certain software, can be neutralized and deactivated, or there is the possibility of sending false information about the activities.
StaffCop - a program for monitoring the activities of the user. As with the previous program, has many different options for observation, as well as basic functionality to hide from the user. It is also quite easily detected and removed. Thus it is clear that such products of commercial companies is very poorly protected and is almost always visible to the user, allowing that same exercise control over the activities of the program, and if necessary to eliminate the negative consequences for themselves of its activities.
findingsReturning to the application development to be undertaken, it is necessary to clearly indicate the number of requirements to be met by the program:
Separation of duties depending on the level of activity as follows:
Information gathering should be carried out at the user level, as neobchayno difficult to implement a similar scheme at the kernel level. The same kasachetsya network activity.
As for hiding the program, it is better to implement at the kernel level, to achieve maximum efficiency

Animation.
scheme splicing functions
(refresh page to re-view)
Conclusions
At the current stage of development is created dynamically shared library to hide the activities of applications using the methods of user-level. Hiding produced by splicing function NtQuerySystemInformation and modification of its work and function NtQueryDirectoryInformation with the same pattern of behavior. Also at this stage, it became clear that the methods of the 3rd ring of protection is not effective, and poorly organized by hiding activities (this conclusion is based on the fact that specialized soft reveals the hidden activities). Therefore, at present studied methods of 0-ring. As some intermediate result of research, was created by the driver, who acted on the methodology DKOM, modifying the doubly linked list of kernel structures EPROCESS, describing individual processes in the system. Thus, some hidden process at the kernel level. Also, a special filter driver to intercept all the packets I / O request to all the logical non-removable disks in the system in order to hide files and / or folders. Currently under way to study the function SwapContext to prevent its splicing and to detect hidden processes.
As a result of this master's thesis will explore a variety of techniques to hide in the OS class Windows NT, determine the most effective, and created an application for monitoring the use of these techniques.
online articles