Abstract
Contents
- Introduction
- 1. Actuality of the theme
- 2. Goal and tasks of the research
- 3. DDoS–attack
- 4. Ways protecting against DDoS–attacks
- Conclusion
- References
Introduction
Until a few decades ago, computer systems were mostly single–user and shared information across multiple channels rather limited.
Development of a new principle of building a network based on packet switching have substantially improved the flexibility and vitality of the system. At present, any activity connected with the exchange of information is not complete without the use of computer networks. The capacity and coverage of the largest networks – the Internet is increasing. This allows multi strongly for distributed applications worldwide. Such systems are widely used in the fields of credit, insurance, health care, law, military applications, communications, and many others.
The functioning of all these applications depends significantly on the security of information flow, since the effective sharing of information resources can significantly improve the quality of customer service, productivity of businesses, public services. Thus, for organizations and individual users a high degree of connectedness through open networks and the dependence of the functioning of their smooth operation.
However, the widespread introduction of networks has increased the number of potential attackers with access to open systems. One of the most dangerous types of criminal activities on the Internet are the so–called network cyberattacks.
1. Actuality of the theme
Prevention of network attacks – one of the most difficult tasks in the field of information systems. Most modern systems is a distributed structure, the core architecture is the use of network technology. And ensuring operability of these systems depends on the ability to withstand malicious actions that aim to disrupt both the network and information system operating within it. One of the most dangerous types of criminal activities on the Internet are the so–called network attacks. According to the statistics given in the online sources, the number of network attacks continues to grow, the methods used by criminals are constantly evolving and improving, from individual efforts they go to corporate developments. At the same time, the existing intrusion detection systems and attacks are not perfect and are not efficient enough in terms of security solutions. Therefore, the methods of work in this direction are necessary and relevant.
2. Goal and tasks of the research
The aim is to study the various methodologies for the protection of information systems and identify areas for development, which will provide a cost–effective system that works in real time, having sufficiently high stability, low computational complexity, flexibility and adaptability to new types of attacks.
3. DDoS–attack
One of the most challenging tasks in the area of computer systems is to prevent DDoS–attack.
DDoS–attack (Distributed Denial of Service, distributed attack of the denial of service
) – an
attack on a computer system to run on a large number of computers, in order to bring it to the full. That
is to create the conditions under which legitimate (lawful) system users can not get access to the
provided system resources (servers), or that the access is difficult [1].
Initially, DDoS–attacks were used to test the capacity of the channel, however, over time, all
malicious cyber criminals have realized the possibilities of this technology, and accepted it on their
weapons
. Now DDOS–attacks used by cyber criminals for various purposes: the pressure on people,
blocking key parts of the Internet, any malfunction of the Internet – services companies, whose
business is based on web–services, in competition, political competition, etc. Accordingly, the
profitability of this business is high. The consequences of DDoS–attacks can result in the loss
of key network resources, applications, and systems of business, loss of reputation, financial loss, etc.
Just DDoS–attacks can be used as a distraction when you run other malicious programs, for example,
to steal confidential data.
The objectives of such attacks is – the creation of conditions under which legitimate users are denied access to resources provided by the system (either this access is difficult). By itself, the DDoS–attack looks like a rapidly increasing amount of traffic on the victim host.
There are several classifications of DDoS–attacks by type. Conditionally released several techniques are most commonly used by cyber criminals:
- destructive – attacks produced in this way, lead to the fact that the network node becomes completely inaccessible: freezes destroyed the operating system, the configuration of the device and the like, such attacks are made by the vulnerabilities that are in the software;
- attack on system resources – if such an attack is formed by a large number of meaningless or formed in a different format requests to the nodes of the network or applications, resulting in a significant performance computer system or network equipment.
The purpose of this attack is the rejection of the system due to the exhaustion of its resources. They are divided into several types:
- HTTP GET – purposeful, coordinated dispatch on the web–server is the victim a large number of requests from
zombie – network
; - UDP – Flood – this type of attack is directed at the communication channel to the address of the targeted system are sent to UDP queries of large size, with a rapid depletion of the communication channel bandwidth, leading to the target system, and drive using the protocols TCP, stops responding;
- TCP SYN – Flood – in this type of attack to the target node sends a large number of requests to open a connection with the attacked object had to spend all their resources to track all of these half–open connections, which leads to the depletion of the number of sockets and the device stops responding;
- ICMP – Flood – focused, specialized sending a large number of DNS queries to DNS – server with DNS – server is not available for a large range of users, as its resources are busy processing these requests.
More often than not, during the DDoS–attack uses several types of attacks, which largely complicates counter DDoS–attacks.
According to Kaspersky the most popular type of attack was HTTP–Flood (80%), when the attacked site at the same time sent a lot of HTTP–requests. Attackers use different technologies to carry out this type of attack. In 55% of cases of attacks such as HTTP–Flood bots trying to appeal to a single page of the site, on the second place with 22% of attacks are on the various forms of authorization, and the third place (12%) took the attack using numerous attempts to download any file from the site. In only one case out of 10 held by more complex attacks where the attacker tries to mask the actions of bots with the behavior of real users [3].
In second place c indicator of 10% ranged attacks such as UDP Flood. Bots performing such attacks rely
on brute force
that is generating a lot of fairly small in size (eg, 64 bytes) of garbage bags.
In the third and fourth places in the ranking of popularity among malicious attacks are the type SYN Flood (8%) and ICMP Flood (2%), respectively. Described diagram is shown in figure 1.
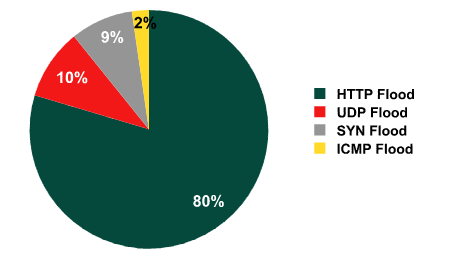
Figure 1 – Types of DDos–attack
In most cases, the network from which you are DDoS–attack, with three tier organization. Such a network is called a cluster DDoS
. At the top of the cluster are one or more computers, which begins and coordinated attack. At the second level – the main (processing) computers that are directly betraying the signal to start the attack to the next level. The third level – pre–organized botnet network.
A botnet network – a network computers – zombies
who fell under the control of cybercriminals after infection. Most often, the bot in the botnet is a program that secretly installed on the victim's device and allows attackers to perform certain actions using the resources of the infected computer. Usually frowned upon or used for illegal activities – sending spam messages, the selection of passwords on remote computers and services, the use during the DDoS–attacks [2].
Control is generally obtained by setting the computer invisible not detectable by the user in the daily work of the software without the user's knowledge. Usually after:
- a virus infecting your computer through a vulnerability in the software (bugs in browsers, email clients, document viewers, images, video);
- the use of inexperienced or careless user – masked by
useful content
; - the use of unauthorized access to a computer (rare);
- exhaustive search the admin password to the network shared resources (in particular, to the ADMIN $, which allows to remotely execute a program) – mainly in local area networks.
At a sufficiently high degree of study of the formation of a botnet networks, opposition cybercriminals is quite a challenge.
The fact that the reverse path from the victim to cyber criminals is difficult to trace, so often they are not disclosed. Because of this fact, and there was kind of criminal activities in internet network – creating a botnet networks and the subsequent transfer or lease them out to the customer to carry out DDoS–attacks and send spam – mails.
In almost all countries of the world DDoS–attacks constitute a criminal offense, but the organizers behind bars them are extremely rare. Today, the organization of DDoS–attacks involved not loners, and organized crime groups. Their branching, organizational and geographic, to successfully counter the actions of law enforcement.
Modern intrusion detection systems and attacks are software or hardware and software solutions that automate the process of monitoring the events occurring in a computer system or network, and to independently analyze these events for signs of security problems, these systems have become an essential component of most organizations security infrastructure.
4. Ways protecting against DDoS–attacks
It is believed that there is no need for special means of detecting DDoS–attacks since the fact of attack impossible not to notice, however, is often observed attack, the result of which can be seen only after a while.
Methods for detection of DDoS–attacks are divided into several groups:
- signature – based on a qualitative analysis of the traffic;
- statistical – based on the quantitative analysis of traffic;
- hybrid – combines the advantages of the two previous methods.
Traditional technical protection measures (such as firewalls and intrusion detection systems (IDS)) does not oppose DDoS–attacks since they only allow either deny or allow network traffic based on the analysis of the various fields of network packets. However, the attack can be implemented successfully and within the permitted field of network packets. Also, almost impossible to distinguish correctly–formed from malicious traffic, since it is the same requests as from ordinary users, only generated a disproportionately greater amount. Cyber criminals use another technology called IP–spoofing.
This method is to affix a return address in the IP–packet wrong address and is used to hide the true address of the attacker, with the purpose to provoke a response packet to the correct address, and for other purposes. Some providers use a technology called «Black–hole routing». This technology allows you to detect attacks on the client, or a range of IP addresses and prohibits entry into a network with a single IP address. Attack stopped, but for the customer it looks like a complete disconnection from the network. Obviously, with major customers or important data so do not, moreover, an attacker may substitute some important addresses (e.g., addresses of the root DNS).
The most effective way to detect DDoS–attack is the use of specially designed to suppress DDoS–attacks solutions. The principle of operation is based on the training device that can be recognized as well–formed traffic and subsequent detection of anomalies. In identifying anomalies include security mechanisms at various levels.
One of the ways to combat DDoS–attacks is a complete solution Cisco Clean Pipes.
The features of this complex is the quick response to conduct DDoS–attacks, easy scalability, reliability and performance. The complex uses the Cisco Clean Pipes Modules Cisco Anomaly Detector and Cisco Guard, and the Statistical Analysis System network traffic received from the router via Cisco Netflow.
In this solution, implemented three levels of checks:
- filtering spoofing;
- identification of
zombie computers
; - blocking traffic from the attacker's address.
Anomaly Detector, as the name implies, is designed to detect anomalies. Its mission – teaching, and then anomaly detection. It is a passive element and through the traffic does not pass.
Cisco Guard (filter) – parses the traffic to a malicious and legitimate constituents. If the detector detects anomalies, it is necessary to link the fact anomalies with DDoS–attack. For this it is necessary to intervene in traffic and begin to analyze it. In this case, the detector transmits a filter to control a certain area in the network and the traffic zone goes through it, so to filter traffic gets only contains the attack. Everything else passes by.
This scheme can reduce the false positive rate, the cost savings and increased productivity of the filter.
Conclusions
Within the framework of the given job was investigated kinds network attacks, methods of struggle with them. The given area is most developing, as there is a constant rivalry between the malefactors and organizations ensuring safety of the data. The urgency of a problem of protection and detection network attacks was confirmed.
References
- Безопастность сетей // [Электронный ресурс]. – Режим доступа: http://ru.wikipedia.org/wiki/DoS
- Безопастность сетей // [Электронный ресурс]. – Режим доступа: http://www.intuit.ru/department/security/netsec/3/4.html
- Компьютерная сеть и ботнеты // [Электронный ресурс]. – Режим доступа: http://alsiti.net/index.php?topic=396.0
- DDoS-атаки второго полугодия 2011 года // Лаборатория Касперского [Электронный ресурс]. – Режим доступа: http://www.securelist.com/ru/analysis/208050745/
- Михайлюта С. Л., Степанушко И. В., Бабич Б. А., Ткаченко В. Ю., Лавринович В. С., Исследование сетевых DOS-атак, основанных на использовании протокола ICMP // Вісник Інженерної академії України. – К.: 2009. – № 2. – С. 146 – 149
- Denial of Service Attacks // [Электронный ресурс]. – Режим доступа: http://www.cert.org/tech_tips/denial_of_service.html
- Олифер В.Г., Олифер Н.А. Компьютерные сети. Принципы, технологии, протоколы. 4 издание, 2010, 943с
- Ефимов В.И. Система мультиплексирования разнесенного TCP/IP трафика / В.И. Ефимов, Р.Т. Файзуллин // Вестник Том. гос. ун-та. – 2005. – № 14. – С. 115 – 118.
- Лукацкий А. В. Предотвращение сетевых атак: технологии и решения / А. В. Лукацкий. – СПб. : Экспресс Электроника, 2006. – 268 с.
- Обзор механизмов реализации и обнаружения атак [Электронный ресурс]. – Режим доступа : http://comp-bez.ru/?p=778
- Лукацкий А. В. Обнаружение атак / А. В. Лукацкий. – СПб. : БХВ-Петербург, 2003. – 256 с
- Шаньгин В. Ф. Защита компьютерной информации. Эффективные методы и средства / В. Ф. Шаньгин. – М. : ДМК Пресс, 2010. – 544 с
- Котенко И. В., Степашкин М. В., Богданов В. С. Архитектуры и модели компонентов активного анализа защищенности на основе имитации действий злоумышленников // Проблемы информационной безопасности. Компьютерные системы. № 4. – СПб., 2005
- Душкин А.В. Распознавание и оценка угроз несанкционированного воздействия на защищенные информационно-телекоммуникационные системы / А.В. Душкин // Информационные технологии. – 2008. – № 3. – С. 71 – 75.
- Терновой О.С. Раннее обнаружение DDOS-атак методами статистического анализа /О.С. Терновой/ Перспективы развития информационных технологий. – Новосибирск, изд. «Сибпринт», С. 2012 – 212.
Notice
At the time of writing this essay master work still is not complete. Estimated date of completion: December 2013, which is why the full text of the paper, as well as materials on the subject may be obtained from the author or his head only after the specified date.
