
 Masters' portal
DonNTU
Masters' portal
DonNTU
To date, data networks are rapidly evolving. New technologies and methods of information delivery are explored. Wired data networks have gone far ahead, in comparison with wireless ones, and reached transmission speeds of 100 gigabits per second using Ethernet technology and 43 terabits per second over Optical Fiber. Wireless networks are far behind at a speed of 6.9 gigabits per second (theoretically). In the open space with the transfer of information over wireless networks, there are practically no problems, but in closed rooms communication can be cut off.
2.Description of wireless technologies
There are many standardized technologies and wireless communication protocols used in data networks such as Zig-bee, Bluetooth, Wi-fi.
Technologies ZigBee and Thread were originally developed to create reliable distributed networks of sensors and control devices with low data rates. These technologies support the network topology "mesh", sleeping and mobile nodes, as well as nodes that support the operation of retransmission and self-healing algorithms. These technologies have a speed of 250 kbit / s - this is the maximum network bandwidth. The useful speed will be of the order of 30-40 kbit / s within adjacent nodes and 5-25 kbit / s when using retransmission. The main difference between Thread technology and ZigBee is that it adds IP protocol support, which simplifies the integration of Thread networks with network applications. [1]
The technology uses small short-range transceivers, either directly embedded in the device, or connected via a free port or PC card. Adapters operate within a radius of 10 meters and, unlike IrDA, are not necessarily in line of sight, that is, there can be various obstacles or walls between connected devices.
Devices that use the Bluetooth standard operate in the 2.45 GHz ISM range (Industrial, Scientific, Medical - industrial, scientific and medical) and are capable of transmitting data at speeds up to 720 kbps at distances of up to 10 meters and transmitting 3 voice channels. Such indicators are achieved by using a transmission power of 1 mW and an intervening frequency switching mechanism that prevents interference. If the receiving device determines that the distance to the transmitting device is less than 10 m, it automatically changes the transmit power to the level required for this device location. The device switches to energy saving mode when the amount of data transferred becomes small or the transmission stops.
The technology uses FHSS - frequency hopping (1600 jumps / s) with spread spectrum. In operation, the transmitter switches from one operating frequency to another by a pseudo-random algorithm. For full-duplex transmission, a time division duplex (TDD) is used. It supports isochronous and asynchronous data transfer and provides easy integration with TCP / IP. Time Slots are deployed for synchronous packets, each of which is transmitted on its radio frequency.
The power consumption of Bluetooth devices should be within 0.1 watts. Each device has a unique 48-bit network address that is compatible with the IEEE 802 standard.
The 2.45 GHz band is not licensed and can be used freely by all comers. It is managed only by the Federal Communications Commission (FCC), limiting the part of the range that each device can use. The trouble is that these devices have become very many - ranging from wireless networks that support 802.11 and 802.11b standards and Bluetooth devices and up to microwave ovens! Now the commission is considering a request to increase the used range for Home RF (specification used in audio and video equipment). This increase can affect other devices operating in this range, the number of which increases. At the same time, the FCC stated that the use of an unlicensed frequency carries an undoubted risk and the possibility of interference and conflicts between devices is not excluded. Firms supporting wireless network technologies, including Bluetooth, are actively protesting against the increase in the Home RF range.
Bluetooth devices are able to connect with each other, forming a piconet, each of which can include up to 256 devices. In this case, one of the devices is master (Master), another seven - slave (Slave), the rest are in standby mode. Piconets can overlap, and access to resources of slave devices can be organized. Overlapping piconets can form a distributed network over which data can migrate. [2]
Wi-Fi (Wireless Fidelity) is a trademark of the Wi-Fi Alliance for wireless networks based on the IEEE 802.11 standard.
Typically, a Wi-Fi network configuration contains at least one access point and at least one client. It is also possible to connect two clients in the point-to-point mode (Ad-hoc), when the access point is not used, and clients connect directly via network adapters. The access point transmits its SSID network identifier using special signal packets at a rate of 0.1 Mbps every 100 ms. Therefore, 0.1 Mbps is the lowest data rate for Wi-Fi. Knowing the network SSID, the client can determine whether a connection to this access point is possible. If two access points with identical SSIDs fall within the coverage zone, the receiver can choose between them based on the signal level data. The standard Wi-Fi gives the client complete freedom in choosing the criteria for the connection. In more detail, the principle of operation is described in the official text of the standard.
However, the standard does not describe all aspects of building wireless Wi-Fi networks. Therefore, each equipment manufacturer solves this problem in its own way, applying the approaches that he considers best from one or another point of view. Therefore, there is a need to classify ways to build wireless LANs.
The way to combine access points into a single system can be distinguished:
With a "layered" or multi-layered radio channel structure [3]
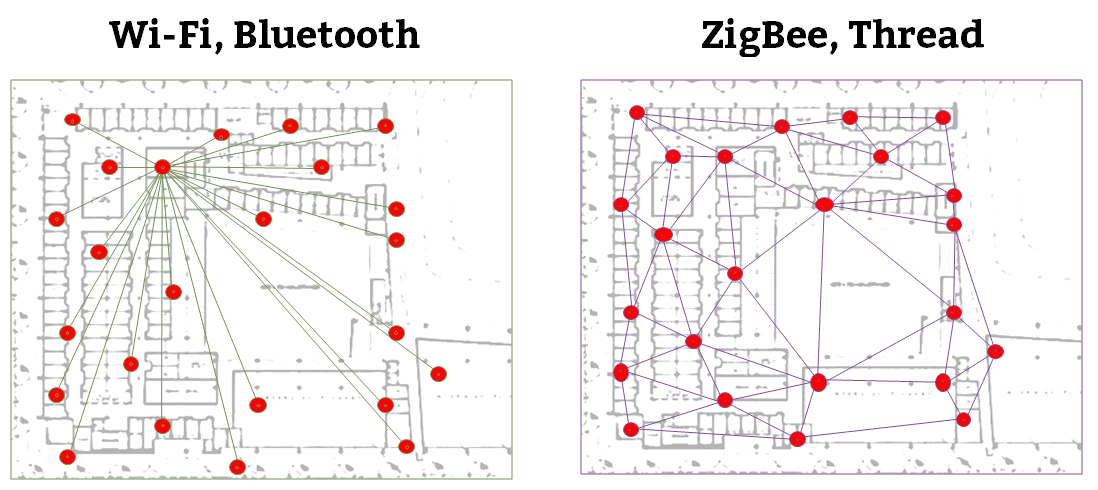
The differences in the topology of Zig-bee and Thread from Wifi and Bluetooth are shown in the figures.
WIMAX (Worldwide Interoperability for Microwave Access) is a telecommunication technology designed to provide universal wireless communications over a wide range of devices (from workstations and laptops to mobile phones). It is based on the IEEE 802.16 standard, also called Wireless MAN (WiMAX should be considered a slang term, since it is not a technology, but the name of the forum on which Wireless MAN was agreed). The name WiMAX was created by the WiMAX Forum, an organization that was founded in June 2001 with the aim of promoting and developing WiMAX technology. The forum describes WiMAX as "standard-based technology that provides high-speed wireless access to the network, an alternative to dedicated telephone lines and DSL." The maximum speed is up to 1 Gbit / s per cell. [4]
Now networks with a variable topology and correct construction of a route of transfer of the information are actively investigated. Networks with variable topology are called self-organizing. In most cases, the terms "mesh" "ad-hoc" "mobile ad-hoc", etc., are used to denote self-organizing networks
Mesh networks are mesh radio networks consisting of wireless fixed routers that create a wireless backbone and a coverage area for mobile and fixed subscribers that have access (within the radio coverage zone) to one of the routers. Topology is a star, with a random connection of support nodes. [5]
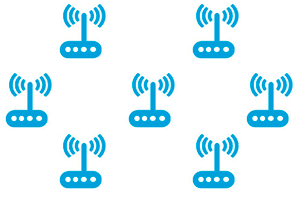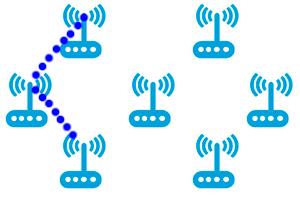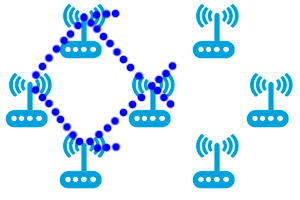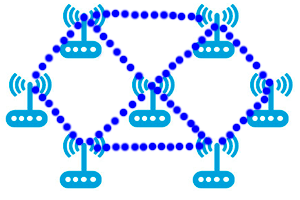
The architecture of a mesh network consists of a number of nodes (nodes) that form the backbone of the network, and client devices. Nodes can communicate with each and independently create data transmission routes. The nodes detect disconnections of neighboring nodes and the appearance of new ones, and automatically rebuild routes. The technology of mesh networks is not specific for wireless networks, but in wireless networks it acquires new properties. When using wireless nodes, the network topology can easily be rearranged by simply moving, deleting, or adding nodes. Cabling between nodes is not needed. Theoretically, you can cover any necessary territory with a mesh-network. The main problem in this case is the achievement of the necessary number of nodes and the possibility of providing them with power supply. Wireless clients can move within the coverage area, the nodes will build the right routes and provide transparent roaming. From the point of view of subscriber service, such networks already provide a full range of IP-applications - Ethernet, VoIP, real time video. Nodes (nodes) that form the backbone of the network, and client devices. Nodes can communicate with each and independently create data transmission routes. The nodes detect disconnections of neighboring nodes and the appearance of new ones, and automatically rebuild routes. The technology of mesh networks is not specific for wireless networks, but in wireless networks it acquires new properties. When using wireless nodes, the network topology can easily be rearranged by simply moving, deleting, or adding nodes. Cabling between nodes is not needed. Theoretically, you can cover any necessary territory with a mesh-network.
The main problem in this case is the achievement of the necessary number of nodes and the possibility of providing them with power supply. Wireless clients can move within the coverage area, the nodes will build the right routes and provide transparent roaming. From the point of view of subscriber service, such networks already provide a full range of IP-based applications - Ethernet, VoIP, real time video.
The wireless mesh architecture has much in common with the router's algorithm of working on the Internet, where routers independently decide on the direction of the packets, based on dynamic routing protocols. In both cases, the specific path by which packets pass through intermediate nodes is transparent to clients. The mesh networks are self-healing: the network will work even when there is a faulty node on the network or a connection is lost. As a result of such an organization, a very reliable network infrastructure is obtained.
In a wireless mesh network, traffic is dynamically redirected between nodes to select the optimal signal flow to the edge router. For this purpose, special algorithms for intelligent routing are used. The direction of traffic can be influenced by factors of the least number of hop (hop) between nodes, their congestion, traffic priority, etc. That is, the mesh network adapts itself to specific situations and optimizes the signal path. [6]
4. Routing protocols working with Mesh networks
The routing protocols working in such networks can be divided into:
OLSR is based on a broadcast mechanism to update information about the network topology.
The peculiarity of the protocol is that this information is known to each node of the network. In the OLSR, the network node sends the so-called HELLO message. Changes in the network topology are detected by the nodes using the received HELLO-messages from the neighbors. These messages contain the own address of the node that sent this notification, as well as a list of all its available neighbors, their addresses indicating the type of connection (symmetric or asymmetric). Thus, the node informs its neighbors about the connections available to it. Each subscriber keeps information about his one-neighbors and two-hop neighbors. Sending of HELLO-messages is carried out with the set interval. In case the node does not receive the HELLO-message from the neighbor within a certain time, then the connection with it is considered broken. An appropriate change is made to the subscriber network topology table. In addition to everything on the network, the nodes periodically transmit a broadcast topology control (TC) message. This message contains information about subscriber connection with one-step neighbors. Based on the received information from the TC- and HELLO-messages, the node builds a graph that describes the idea of building a network for this node. With the help of this graph, a table of the shortest paths of information transmission to each node is constructed. It is obvious that in such a way of organization of communication between nodes there is a significant drawback. A natural situation is that a two-step neighbor can be one-step neighbor for two or more one-step neighbors of the transmitting node. Then there will be a situation in which a two-step neighbor will receive the same HELLO-message several times. To address these situations, the OLSR provides a method for optimizing the distribution of network information about Multipoint Relay (MPR) states. According to the network topology table, the node selects one-step neighbors (MPR_Relay) with symmetric coupling, which are one-step neighbors to at least one two-step neighbor of this node. This method allows you to reduce broadcast traffic. [7]
TBRPF (Topology Dissemination Based on Reverse-Path Forwarding) also refers to proactive channel state protocols, designed for mobile ad-hoc networks, which provides routing along the shortest paths to the destination. Each node on which TBRPF is running calculates the source tree (providing paths to all available nodes) based on the partial topology, the information stored in its topology, using the Dijkstra Algorithm modification. To minimize overhead costs, each node reports only a portion of the source tree for neighbors, the TBRPF uses a combination of periodic updates to inform all neighbors of a portion of the source tree. Each node also has the option of reporting the complete network topology, to provide verification, and increasing reliability in mobile networks. TBRPF searches for neighbors using "differential" HELLO messages that only report changes in the status of neighbors. [8]
The DSDV protocol is based on the idea of the classic Bellman-Ford routing algorithm with some improvements. DSDV is a proactive, remotely vector-based algorithm. Each node supports a table routing, which lists all available destinations, the number of routers ("jumps") to the final destination and version number. The nodes periodically transmit their routing tables to the nearest neighbors. The node also sends its routing table if it has changed since the last update was sent. The main task of the algorithm is to exclude the possibility of creating cyclic routes. To minimize the amount of traffic, the protocol provides for the exchange of complete routing tables only with serious changes in the network topology. In most cases, more minor updates are sent. DSDV was one of the first developed algorithms. It is quite suitable for creating peer-to-peer networks with a small number of nodes. Many improved versions of this algorithm have been proposed. The main drawback of DSDV-based protocols is the need for regular transmission of service information between nodes to update their routing tables, which in a wireless network leads to an increase in the battery consumption of the mobile device and occupies part of the radio channel bandwidth, even when the network is not in use. In addition, whenever a network topology changes, a new sequence number for the routing information version is created. With very dynamic networks, it is possible to overflow this parameter, i.e. DSDV is not suitable for networks with a rapidly changing topology. [9]
The reactive protocols include:
AODV (English Ad Hoc On-Demand Distance Vector) is a dynamic routing protocol for mobile ad-hoc networks (MANET) and other wireless networks. Developed jointly by the Nokia Research Center of the University of California, Santa Barbara and the University of Cincinnati by K. Perkins and S. Das. AODV is suitable for routing both unicast and multicast packets.
It is a reactive routing protocol, that is, it establishes a route to the addressee on demand. Unlike classic Internet routing protocols that are proactive, that is finding routing paths regardless of the use of routes. As the name implies, a distance-vector routing algorithm is used to calculate routes. In AODV, the use of sequence numbers for route updates eliminates the possibility of the problem of "counting to infinity" inherent in other protocols using this routing algorithm. This technique was previously implemented in the DSDV protocol. [10]
DSR (Dynamic Source Routing) is the routing protocol for MANET with the mesh topology. Similar to AODV in that it also forms a route on demand, by transmitting a broadcast-request. However, it uses explicit routing, without relying on routing tables on each staging device. In addition, DSR has introduced a number of sequential instantiations, including DSR-Flow (a hybrid of explicit routing and table routing). Explicit route assignment requires the accumulation of the addresses of each device between the source and the receiver during its search. Information about the accumulated path is replenished by the nodes that process broadcast-requests from the source. The paths studied in this way are used for packet routing. As a result, the routed packets contain the address of each device through which they passed. Due to the increase in packet headers, this can lead to redundancy of the service data flow for long paths or large addresses, as in IPv6. For such situations, the "flow id" option is defined in DSR-Flow, which allows packets to be sent in accordance with routing tables (it can be activated for far routes).
Thanks to the explicit assignment of routes, all information about them is continuously updated by mobile nodes (while the data stream passes through them). This avoids the need for periodic route verification (as opposed to AODV). As a result, only the phases of search and support remain. In any case, the route is generated only if the request message has reached the intended destination node (in response, the chain of nodes accumulated in the request is added).
To send a response to a request, the destination node must have a route to the source node. If the route were in the cache, a cached entry would be used. Otherwise, the route to the source node will be determined based on the stored in the chain path of the request packet (this requires that all channels in the network are symmetric). In the case of a successful transmission of a response, support is initialized, through which the transmission of error messages will be considered by the node. As a result, the corrupted link will be deleted from the node's cache path, as well as all routes containing this channel. Then, the phase of searching for a new viable path will be re-initiated.
Dynamic Source Routing Protocol (DSR) on demand was created in order to reduce the traffic consumed by control packets in wireless networks, eliminating the table update messages required in the route-based approach using tables. The main difference between this and other reactive routing protocols is that it does not have "beacons" and therefore does not require periodic transmission of the greeting packet that the node uses to inform neighbors of its presence. The main approach of this protocol (as well as other reactive routing protocols) is that during the phase of the route design the node sets the route by sending Broadcast RouteRequest packets over the network. The destination node, when receiving a RouteRequest, responds by sending the RouteReply packet back to the source that carries the route traversed by the received RouteRequest.
Consider the source node that does not have a route to the destination. When it has data packets that will be sent to the recipient, it initializes the RouteRequest package that is distributed over the network. Each node, after receiving the RouteRequest package, re-transmits the packet to its neighbors (if it has not yet been transmitted, since a copy of the packet can come to it from another node), provided that the node is not the destination and that the packet's lifetime (TTL ) has not been exceeded. Each RouteRequest has a sequence number generated by the source node and the nodes through which it passed. The node, after receiving the RouteRequest package, checks the sequence number on the packet before sending it. The packet is sent only if it is not a duplicate RouteRequest. The sequence number on the packet is used to prevent looping and avoid multiple transmissions of the same RouteRequest by the intermediate node, which receives it through several channels. Thus, all nodes except the addressee send the RouteRequest packet during the route formation phase. The destination node, after receiving the first RouteRequest packet, responds to the source through the return path that crossed the RouteRequest packet. Nodes can also learn about neighboring routes crossed by data packets if a mode of promiscuity is set (the mode of operation in which a node can receive packets that are not transmitted and are not addressed to it). This route cache is also used during the route formation phase. If the intermediate node receiving the RouteRequest has a route to the destination node in its route cache, it responds to the source node by sending RouteReply with all the route information from the source node to the destination node. [11]
Hybrid protocols include the HWMP protocol HWMP - The wireless network hybrid protocol defined in IEEE 802.11s is the basic routing protocol for a wireless mesh network. [12] Based on AODV, tree-based routing, management protocol peer-to-peer communication, whereby each Mesh point detects and tracks neighboring nodes. This protocol is hybrid because it supports two types of path selection protocols.
Today, networks are a multilevel structure. It is almost impossible to calculate the exact number of connections. Nevertheless, with all this, there must be standards and technologies that provide the highest possible quality of service, the maximum transmission speed, and should be easily scalable. Although there are a number of problems associated with wireless networks such as indoor attenuation, this problem is solved by mesh networks that allow you to create a cellular structure with a control device that, depending on the type of protocol, monitors all devices and builds optimal routes thanks to built-in routing algorithms (Dijkstra's Algorithm, etc.). In the future, modeling will be carried out in order to establish the optimal properties that must be considered in order to build an optimal route from the sender to the receiver in wireless networks.
1. Хабрахабр[Электронный ресурс]: Беспроводные сети ZigBee. Часть 1 [Вводная] — электронные данные — режим доступа https://habrahabr.ru/company/efo/blog/281048/ — дата доступа: декабрь 2017
2. Бурабай[Электронный ресурс] Технология Bluetooth — электронные данные — режим доступа http://bourabai.kz/einf/bluetooth.htm — дата доступа: декабрь 2017
3. Википедия[Электронный ресурс] Wi-Fi — электронные данные — режим доступа https://ru.wikipedia.org/wiki/Wi-Fi — дата доступа: декабрь 2017
4.Броадбэнд [Электронный ресурс] Что такое WiMAX? Принципы работы WiMAX — электронные данные режим доступа http://www.broadband.org.ua/tekhnologii-bystrogo-interneta/1311-chto-takoe-wimax-printsipy-raboty-wimax - дата доступа: декабрь 2017
5.Хабрахабр[Электронный ресурс] Что такое MANET или почему WiFi не решение всех телекоммуникационных проблем — электронные данные — режим доступа https://habrahabr.ru/post/197860/ дата доступа: декабрь 2017
6.Павлов А. А. Датьев И. О. ПРОТОКОЛЫ МАРШРУТИЗАЦИИ В БЕСПРОВОДНЫХ СЕТЯХ // Киберленинка — [Электронный ресурс] — режим доступа https://cyberleninka.ru/article/v/protokoly-marshrutizatsii-v-besprovodnyh-setyah - дата доступа: декабрь 2017
7. Википедия[Электронный ресурс] OLSR — электронные данные — режим доступа https://ru.wikipedia.org/wiki/OLSR дата доступа: декабрь 2017
8.Датьев И.О. Павлов А.А. МОДЕЛИРОВАНИЕ БЕСПРОВОДНЫХ МНОГОШАГОВЫХ САМООРГАНИЗУЮЩИХСЯ МОБИЛЬНЫХ СЕТЕЙ // Киберленинка [Электронный ресурс] — режим доступа https://cyberleninka.ru/article/v/modelirovanie-besprovodnyh-mnogoshagovyh-samoorganizuyuschihsya-mobilnyh-setey-1 дата доступа: декабрь 2017
9.Павлов А.А. Датьев И.О. ИССЛЕДОВАНИЕ ВЛИЯНИЯ РАЗЛИЧНЫХ ПАРАМЕТРОВ НА ХАРАКТЕРИСТИКИ ПЕРЕДАЧИ ДАННЫХ БЕСПРОВОДНЫХ МНОГОШАГОВЫХ СЕТЕЙ // Киберленинка [Электронный ресурс] - режим доступа https://cyberleninka.ru/article/v/issledovanie-vliyaniya-razlichnyh-parametrov-na-harakteristiki-peredachi-dannyh-besprovodnyh-mnogoshagovyh-setey — дата доступа: декабрь 2017
10. Академик[Электронный ресурс] Список протоколов маршрутизации в ad hoc сетях — электронные данные — режим доступа [Ссылка на источник] дата доступа: декабрь 2017
11. Климов И. А. Исследование динамики в беспроводных сетях с переменной топологией // Портал магистров [Электронный ресурс] — режим доступа http://masters.donntu.ru/2013/fkita/klimov/diss/index.htm — дата доступа: декабрь 2017
12. Дугаев Д.А. АРХИТЕКТУРА И ГИБРИДНЫЙ ПРОТОКОЛ МАРШРУТИЗАЦИИ ДЛЯ БЕСПРОВОДНЫХ ЯЧЕИСТЫХ СЕТЕЙ НА БАЗЕ СТАНДАРТА IEEE 802.11S // Научная электронная библиотека [Электронный ресурс] — режим доступа https://elibrary.ru/item.asp?id=20315991 — дата доступа : декабрь 2017