Abstract
Содержание
- Introduction
- 1. Theme urgency
- 2. Goal and tasks of the research
- 3. Fiber-optical communication lines
- Conclusion
- References
Introduction
In the information society, the main resource is information. It is on the basis of possession of information about the most diverse processes and phenomena that it is possible to effectively and optimally construct any activity [1].
To prevent the loss of information, various mechanisms for its protection are being developed, which are used at all stages of working with it. Protect from damage and external influences is necessary and the devices that store the secret and important information, and communication channels.
Damage may be caused by damage to the equipment or communication channel, fake or disclosure of secret information. External impacts occur as a result of natural disasters, as well as as a result of equipment failures or theft. To avoid this, the communication line must be protected from unauthorized access (unauthorized access).
Fiber-optical communication lines (FOCL) are used to transfer data more and more often. Recently, optical fiber can be found not only in large trunk transmission lines, but also in a local computer network located within one building [2].
1. Theme urgency
In the modern world, effective work with information is one of the success factors. Protection of information received its relevance due to the large number of attacks, both on the communication line and on the means of storing information.
Due to the extremely widespread use of fiber as a transmission medium, the problem of its protection from unauthorized access to information is quite relevant.
2. Goal and tasks of the research
The purpose of this work is to study the methods of protecting information transmitted via fiber optic links from unauthorized access and to develop a model for detecting unauthorized access to fiber optic links.
Main tasks of the research:
- General analysis of fiber optic lines.
- Research methods for the removal of information from fiber optic links.
- Research methods of protecting information in fiber optic links.
- Develop a model for the detection of unauthorized access to fiber optic networks.
- Assess the cost-effectiveness of the proposed solutions.
- Select labor protection measures.
3. Fiber-optical communication lines
Fiber-optical communication lines are a type of communication with the highest throughput among all existing means of communication, in which information is transmitted via optical dielectric waveguides. This type of communication is considered the most perfect physical medium for transporting information, with the possibility of transmitting large flows of information over considerable distances [2, 3].
Optical fiber, as a rule, has a circular cross section and consists of two parts – the core and the shell. Quartz glass, which is the carrier medium of fiber optic links, in addition to the unique transmission characteristics, has another valuable property – low losses and insensitivity to electromagnetic fields. The core has a diameter of 9 microns (for single-mode fiber), 50 or 62.5 microns (for multimode fiber). The shell has a diameter of 125 microns and consists of a material with alloying additives that change the refractive index. The cable structure is shown in the figure [4]:
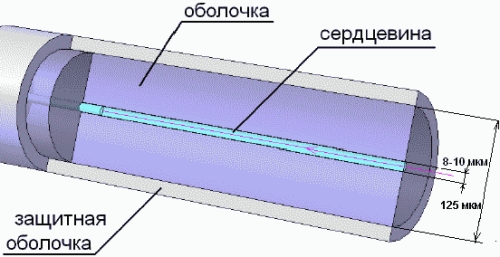
Figure 1 – The structure of fiber-optic cable
This system of information transmission is becoming more widely used in all areas – from computers and airborne space, aircraft and ship systems to information transmission systems over long distances, for example, a large-scale fiber-optic communication line Western Europe – Japan is currently being successfully used. part of which passes through the territory of Russia. Fiber-optical communication is used in the construction of work sites as external highways that combine disparate structures or buildings, as well as multi-storey buildings. It can also be used as an internal carrier of a structured cable system (SCS), however, finished SCS entirely made of fiber are less common – due to the high cost of building optical communication lines [4].
An example of fiber optic use is fiber in every house (Fiber to the premises, FTTP or Fiber to the home, FTTH) – a term used by telecommunication Internet providers to refer to broadband telecommunication systems based on a fiber channel and its completion on the territory of the end user by installing terminal optical equipment for the provision of a complex of telecommunication services, including:
- high speed internet access;
- telephone services;
- television reception services.
The cost of using fiber-optic technology is reduced, which makes this service competitive compared to traditional services.
It is believed that fiber-optical channels, due to the characteristics of the propagation of electromagnetic energy to the core, have increased secrecy. However, there is always the potential to retrieve information from a fiber optic cable. It is known that a fiber is a waveguide structure in which optical radiation propagates according to the law of total internal reflection. But, nevertheless, a small part of the scattered radiation penetrates beyond the limits of the reflecting envelope and can be a leakage channel for the transmitted information.
Advantages of fiber optics [4]:
- High bandwidth optical signals due to extremely high carrier frequency (1014 Hz). The potential of a single optical fiber is a few terabits of information per second.
- Due to the low attenuation of the light signal, optical systems can unite working areas at significant distances (more than 100 km) without using additional repeaters (amplifiers).
- High reliability and noise immunity of the system. Fiber, being a dielectric conductor, is not sensitive to electromagnetic radiation, is not afraid of oxidation and moisture.
- High FOL protection from unauthorized access – information transmitted via fiber-optic communication lines cannot practically be intercepted in a non-destructive way.
- Fire safety (fire resistance) FOCL. Due to the absence of sparking, optical fiber increases the fire safety of the network, which is especially important in chemical, oil refineries, while servicing high-risk technological processes.
- Low cost fiber-optic fiber – fiber is made of quartz, which is based on silicon dioxide, a widespread and therefore inexpensive material, unlike copper.
- Durability – the service life of fiber-optic lines is about 25 years. After 25 years of continuous use in the carrier system, the attenuation of the signals increases.
- Perspectives. The use of fiber-optic communication lines allows you to easily increase the computing capabilities of local networks through the installation of more high-speed active equipment, and without changing communications.
The disadvantages of fiber optics [4]:
- The relatively high cost of active fiber optic elements that convert electrical signals into light and light into electrical signals.
- The relatively high cost of welding optical fibers – this requires precision, and therefore expensive, process equipment. As a result, when an optical cable is broken, the cost of fiber-optic fiber restoration is higher than when working with copper cables.
The benefits from the use of fiber-optical communication lines (FOCL) are so significant that, despite the listed disadvantages of optical fiber, these communication lines are increasingly being used to transmit information [4].
Conclusion
There are various options for the construction of specific systems that differ in the degree of protection and control of unauthorized access to the information transmitted over the fiber optic link. This makes it necessary to conduct special studies in order to examine implemented scientific and technical solutions and their compliance with the requirements of information security. Therefore, an important problem in the protection of fiber optic links is the development of a regulatory and methodological framework and documents that ensure and regulate both the development of protected fiber optic links and the order of their implementation in communication networks. This problem requires its accelerated solution [8].
It should be noted here that all the above methods of protection and their combinations can ensure the security of information only within the framework of known models of threats of attack. At the same time, the effectiveness of protection systems is determined both by the discovery of new ones and by the improvement of technologies for applying already known physical phenomena. Over time, the enemy can master new methods of interception, it will be necessary to supplement protection, which is not typical of cryptographic protection methods, which are calculated for a sufficiently long period. Therefore, protection against unauthorized access to fiber-optical communication lines, namely, to the places of cable laying, is always relevant.
References
- Ионов А.Д. Волоконно-оптические линии передачи: учебное пособие / А.Д. Ионов. – Новосибирск: СибГУТИ, 2003. – 152с.
- Коваль І.Б. Защита информации в волоконно-оптических линиях связи [Электронный ресурс]. – Режим доступа: http://intkonf.org/
- Михеев В.А. Основы построения подсистемы защиты информации многофункциональной информационной системы [Электронный ресурс] – режим доступа:http://izv-tn.tti.sfedu.ru/
- Ефанов, В.И. Физика и техника оптической связи: учебное пособие / В.И. Ефанов. – Томск.: Томский государственный университет систем управления и радиоэлектроники, 2006. – 166 с.
- Хорошко В.А. Методы и средства защиты информации / В.А. Хорошко, А.А. Чекатков. – Киев: Юниор, 2003. – 502с.
- Манько А. Защита информации на волоконно-оптических линиях связи от несанкционированного доступа / А. Манько , В. Катюк, М. Задорожний – Правове, нормативне та метрологічне забезпечення системи захисту інформації в Україні, вип. 2, 2001 р., с. 249-255
- Максимов Ю.Н. Технические методы и средства защиты информации / Ю.Н. Максимов, В.Г. Сонников, В.Г. Петров. – Спб.: ООО
Издательство Полигон
, 2000. – 320 с. - Аскеров Т. М. Защита информации и информационная безопасность. Учебное пособие / Т.М. Аскеров, К.И. Курбатова. – М,: Рос. экон. акад., 2001. 387 с.
