Abstract
Content
- Introduction
- 1. Theme urgency
- 2. The study of ways to separate user access to web-resources
- 2.1 ACL Access Sharing Model
- 2.2 RBAC Access Sharing Model
- 3. Implementation of separate access module based on the RBAC model
- 3.1 Algorithm of microservice authorization functioning
- 3.2 Improving the RBAC model for allocating access rights
- 4. Implementing an improved model in Go
- Conclusion
- References
Introduction
With the development of technology and the emergence of the ability to store data on separate elements and to have access to process them in the modern world, a person has the task of sharing access. At the moment, technology is quite deeply embedded in the daily life of man. The more human life is simplified, the greater the complexity of the technology.
1. Theme urgency
Web resources are the most common way to share information. These resources are used in very many areas, which has led to the development of network technologies and the emergence of corporate networks. However, the main problem appeared - the distribution of user data access. According to the different laws of privacy, each user must have access to the data that is necessary to perform his duties. This privacy policy is used by many businesses. Also, the distribution of access affects the heath data. The more accurate the rules will be described. the more flexible access can be given to the user.
2. The study of ways to separate user access to web-resources
Access research is not the most “young” topic, but it is the most interesting and useful topic based on the principles that the separation of data should clearly describe the user's rights. be flexible and not allow unauthorized access to the information that should be inaccessible and not be useful for the user in terms of the workflow. Information should always be available to the user for the productive execution of the workflow. There are different access models built on different principles and widely used. Different models are similar to each other in that they inherit certain logical principles of functioning. One of the most popular models is selected for consideration - these are ACL and RBAC.
Main tasks of the research:
- Access distribution analysis using the ACL model.
- Access distribution analysis using the RBAC model.
- Implementing a separate module access using the RBAC model.
- Implementing an improved model in Go.
Research object: RBAC access distribution model.
Research subject: research and implementation of improved RBAC model flexibility.
As part of the master's work, it is planned to receive topical scientific resultsin the following areas:
- Distribution of the user accessibility.
- Explore popular access patterns.
- Modification of one of the access distribution model.
For the experimental evaluation of the theoretical results obtained and the formation of the foundation for further research, as practical results it is planned development of microservice using the Go programming language from Google based on the proposed modifications with the following properties:
- Log in using Go.
- Implementation of modification of the distributed access model.
2.1 ACL Access Sharing Model
Access Control List or ACL is an access control list that determines who or what can access an object (program, process, or file), and which operations are allowed or forbidden for the subject (user, group of users) to perform. File systems use a process user identifier (UID in POSIX terms) to implement ACLs.
An access list is a data structure that contains records that define the rights of an individual user or group to special system objects, such as programs, processes, or files. These records are also known as ACE (Access Control Entries) in Microsoft Windows and OpenVMS. In Linux and Mac OS X, most file systems have extended attributes that act as an ACL. Each object in the system contains a pointer to its own ACL. Privileges (or privileges) define special permissions that allow a user to read from, write to, or execute an object. In some implementations, ACE (Access Control Entries) may define the right of a user or group to modify an object's ACL.
ACL concepts vary across operating systems, despite the existing POSIX “standard” [6]. (The POSIX security projects, .1e and .2c, were recalled when it became clear that they affected a very large area and the work could not be completed, but the well-defined parts that define ACLs were widely implemented and are known as "POSIX ACLs.")
In networks, ACLs represent a list of rules defining service ports or domain names available on a node or another OSI Layer 3 device, each with a list of nodes and / or networks that are allowed to access the service. Network ACLs can be configured on both a regular server and a router and can control both incoming and outgoing traffic as a firewall.
2.2 RBAC Access Sharing Model
Role-based access control - the development of selective access control policies, while the access rights of the subjects of the system to objects are grouped according to the specifics of their application, forming roles.
The formation of roles is designed to define clear and understandable for users of the computer system access control rules. Role access control allows you to implement flexible, changing dynamically in the process of functioning of a computer system, access control rules.
This access demarcation is a component of many modern computer systems. As a rule, this approach is used in DBMS protection systems, and individual elements are implemented in network operating systems. Role-based approach is often used in systems for users of which the range of their official powers and duties is clearly defined.
Despite the fact that the Role is a set of access rights to objects of a computer system, role-based access control is not a special case of selective access control, since its rules determine the procedure for granting access to computer system subjects depending on the existing (or missing) roles in its every moment of time, which is characteristic of mandatory access control systems. On the other hand, the rules of role-based access control are more flexible than with the mandatory approach to differentiation [5].
Since privileges are not assigned to users directly and are acquired by them only through their role (or roles), the management of the individual rights of the user in essence boils down to the assignment of roles to him. This simplifies operations such as adding a user or changing a unit by a user.
3. Implementation of separate access module based on the RBAC model
At the moment, the most popular model is the role-based access distribution model. Adding a role to each user contributes to a clearer and more flexible distribution of roles in the system that uses this implementation. The RBAC model is very often used in web resources, making it easy to define data access for a user based on a given role[3].
3.1 Algorithm of microservice authorization functioning
The algorithm of functioning of microservice authorization is based on URL requests and the request processing functions described inside microservice. In modern web resources, the authorization process is a rather complicated technology, since many difficulties are reduced to the main point of authorization - the security of personal data and resource data. Vazhnoy chast'yu yavlyayetsya prepyatstvovaniye vnedreniya virusnykh programm ili raznykh chastey vredonosnogo programmnogo koda, kotoryy posle vstraivaniya v sistemu privodit k utechke personal'nykh dannykh, a poskol'zu pri dal'neyshey rabote s veb-resursom vredonosnoye PO mozhet nanesti ser'yeznyy ushcherb dlya vsego resursa, kak dlya chasti kliyenta, tak i dlya servernoy chasti, v kotoroy zachatuyu vypolnyayetsya obrabotka opredelennyy dannyy kotoryye libo prishli v URL-zaprose, libo dolzhny obrabotat'sya programmno i vernut' na chast' kliyenta opredelennuyu zaproshennuyu informatsiyu, kotoraya ponimayetsya kak servernyy otvet na kliyentskiy zapros. An important part is to prevent the introduction of virus programs or different parts of malicious program code, which, after being embedded in the system, leads to leakage of personal data, and further work with a web resource, malware can cause serious damage to the entire resource, both for a part of the client and for and for the server part, in which the conception is performed, the processing of a certain data that either came in the URL request, or must be processed programmatically and return to the part of the client certain requested information a format that is understood as a server response to a client request. Microservices are created to solve this problem. They should be easily integrated into web resources and perform not only fast processing of a small part of information, but also adhere to the universality as much as possible, as well as have good protection in order to provide a high level of viral stability and personal data safety[4].
3.2 Improving the RBAC model for allocating access rights
Before improving anything, it is necessary to analyze the object of study, identify the advantages and disadvantages of the object under study, develop and implement improvements. At the time of writing the essay, namely, January 2019, various models of access separation were investigated and the RBAC model was chosen the most optimal and popular. However, with some example you can notice some of her problems[2]. The model itself implements the principle of access to data by user role and is presented in Figure 1.
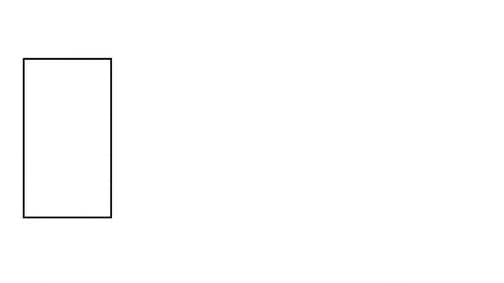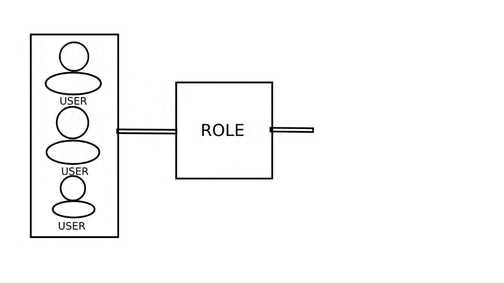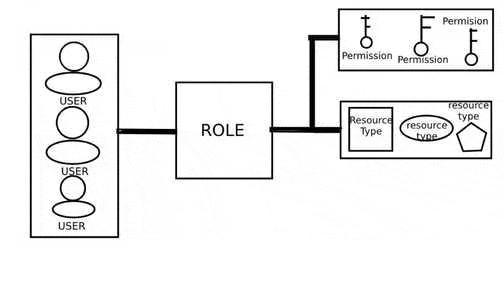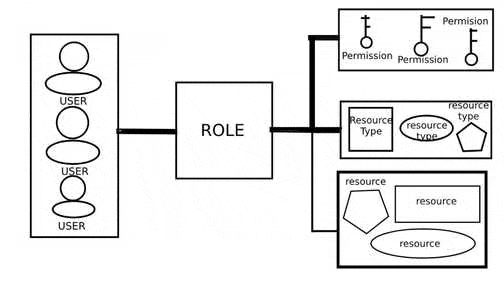
Figure 1 – RBAC model principle
(animation: 20 frames, 10 cycles, 58.1 kilobyte)
A simple example of the manifestation of the problems of this example is the following example. Imagine a simple portal-blog, with the help of which various articles, comments, discussions are published. On this resource there are users and according to the principle of the RBAC model, they have the following roles: admin- has access to all the functionality, user has access to the portal materials, moderator has to perform the moderation of the materials on the resource. With such a simple separation, the RBAC model copes well, but what if we assume that the resource administrator wants moderator users to only moderate individual groups of materials? At this point, the main problem manifests itself - the flexibility to the exact and higher level of separation of access rights. A better solution and improvement of the RBAC model will be the addition of attributes to this model. This section will be discussed in more detail directly in the work itself.
4. Implementing an improved model in Go
One of the widely popular and interesting programming languages today is the Go programming language. It was developed by Google and was first released in 2007. In its implementation, it has a similar syntax for the Java and C programming languages. The language is perfect for implementing microservices to web resources, has high performance among the languages that are directly used to write web resources, namely PHP, Ruby, Python [1]. A number of various features of the principles of the implementation of the OOP and other well-known principles of programming makes it attractive for writing microservices. Despite the relative youth of the language, it already currently has a variety of tools and a variety of packages for realizing its goals.
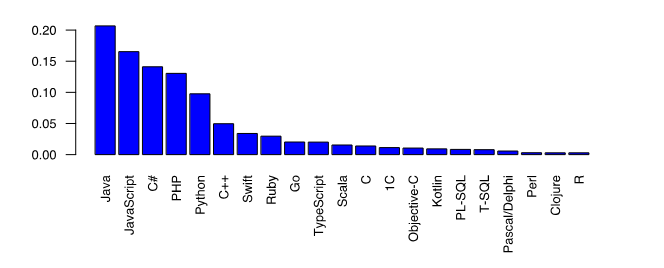
Figure 2 – Schedule selection preference PL for the project [7]
The above graph shows the increased demand for the Go Programming Language (PC), since it is one of the youngest languages compared to all other represented languages. And according to the information for 2018, it is included in the TOP10 of programming languages with a high growth of the community and a positive trend in demand in the application. Below is a graph of the choice of programming languages since May 2012.
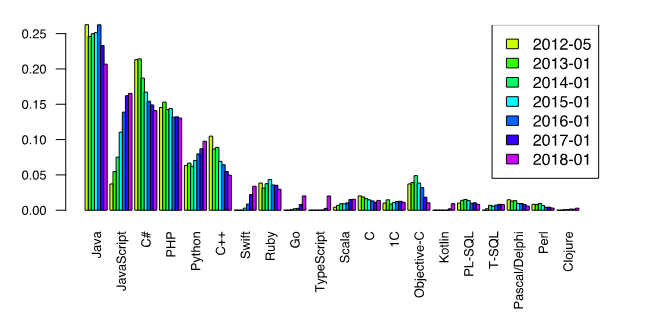
Figure 3 – Schedule of choice of preference of PL since May 2012 [7]
As far as the first eight programming languages can be seen from the graph, there is a great chance of being used in commercial and non-commercial projects since the year 2012, in turn, it is impossible not to notice the rapid growth of the Go language since 2016.
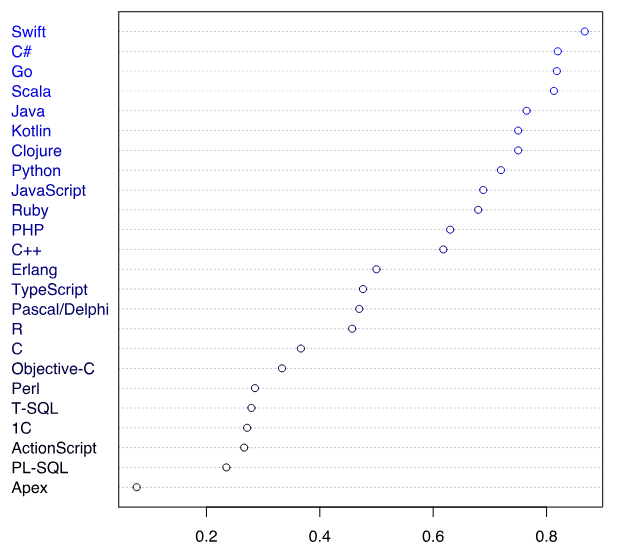
Figure 4 – Schedule selection preference PL for the next project [7]
Golang confidently closes the top three languages preferred for the implementation of the subsequent project. This is not surprising, since simplicity and high performance have all the chances to convince the developer to give preference to this language.
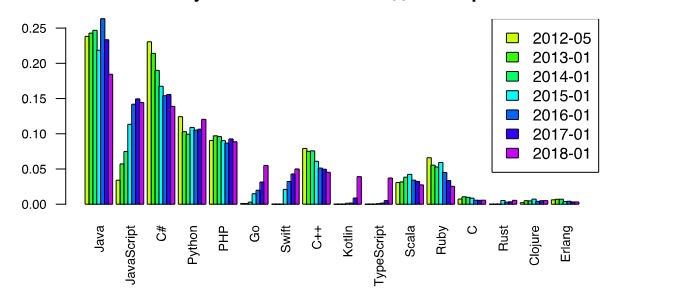
Figure 5 – Schedule selection preference PL for a personal project [7]
According to the personal selection schedule, more and more developers are leaning towards choosing the Go language for a personal project. According to the report on the cost of projects on Go and average wages, he also occupies a very promising place, thereby also attracting for study and use for personal purposes[7].
Conclusion
At the moment, work on the master's work has already explored various models of separation of access rights and work has been done on the study of the selected programming language. The conceptual implementation of the improvements made in the course of the research work has been developed. Further consideration of the RBAC model in the context of a model with attributes and an improvement in the ways of program implementation of the tasks are being conducted.
When writing this essay master's work is not yet completed. Final Completion: June 2019. Full text of the work materials can be obtained from the author or his manager after the date.
References
- 50 оттенков Go: ловушки, подводные камни и распространённые ошибки новичков [Электронный ресурс]. — Режим доступа:https://habr.com/ru/company/mailru/blog/314804/. — Заглавие с экрана. — (Дата обращения: 01.11.2018)
- Элементы RBAC [Электронный ресурс]. — Режим доступа:https://www.ibm.com/support/knowledgecenter/ru/ssw_aix_72/com.ibm.aix.security/rbac_elements_of.htm. — Заглавие с экрана. — (Дата обращения: 06.11.2018).
- Role Based Access Control (RBAC) – новая модель управления доступом к Exchange 2010 (часть 2) [Электронный ресурс]. — Режим доступа: https://www.securitylab.ru/contest/395502.php. — Заглавие с экрана. — (Дата обращения: 20.11.2018)
- Система разделения прав доступа в веб-приложении [Электронный ресурс]. — Режим доступа: https://habr.com/ru/post/51327/. — Заглавие с экрана. — (Дата обращения: 23.11.2018)
- Разграничение доступа на основе атрибутов [Электронный ресурс]. — Режим доступа: https://ru.wikipedia.org/wiki/Разграничение_доступа_на_основе_атрибутов. — Заглавие с экрана. — (Дата обращения: 01.12.2018)
- ACL [Электронный ресурс]. — Режим доступа: https://ru.wikipedia.org/wiki/ACL. — Заглавие с экрана. — (Дата обращения: 11.12.2018)
- Рейтинг языков программирования 2018: Go и TypeScript вошли в высшую лигу, Kotlin стоит воспринимать серьезно [Электронный ресурс]. — Режим доступа: https://dou.ua/lenta/articles/language-rating-jan-2018/. — Заглавие с экрана. — (Дата обращения: 27.01.2019)
