Maria Krakhmal
Faculty of computer science and technology
Department of computer engineering
Speciality “Software of computer equipment”
Methods of increasing the stability of documents to external influences by embedding digital watermarks
Scientific adviser:
Ph.D., Assistant professor Tatyana Zavadskaya
This abstract refers to a work that has not been completed yet. Estimated completion date: June 2020.
Contant author or his scientific adviser after that date to obtain complete text.
Abstract
Content
-
Introduction
- Theme urgency
- Goal and tasks of the research, expected results
- Overview of research and development
- Requirements for data hiding methods Conclusion
List of sources
Introduction
The creation of computer technology has prompted the formation of rules and the further development of computer steganography. As a result, the issue of information security is becoming more actual every day. A large number of new areas of use of computing methods have appeared. Digital data is included information that has an analog form, which includes images, speech, audio and video recordings. And in consequence of this, there are various methods of embedding in text files.
The main aspect of computer technology is the protection of copyright in electronic documents. By using new technologies, attackers can exploit and disseminate hidden information. The most effective ways to protect the copyright of electronic documents are the use of digital steganography and digital watermarks (DWM).
1. Theme urgency
At all times, the goal of information protection has been actual in many areas of life. This task has two main directions: steganography, aimed at saving the facts of transmission or storage of information, and cryptography, the purpose of which is to encrypt the data itself.
In this regard, currently actively used embedding in digital images and electronic documents invisible digital watermarks that carry information about the copyright holder. The introduction of digital watermarks makes it possible to reduce losses from threats of theft (use of data that is intellectual property, or illegal copying).
In connection with the above, the need to create and implement a method of implementing digital watermarks in images or documents, resistant to various external influences, to increase the effectiveness of protection against threats of theft is an actual scientific task.
2. Goal and tasks of the research, expected results
The aim of the work is to improve the efficiency of protection of digital documents as intellectual property objects from the threats of theft by introducing digital watermarks in them.
To achieve this goal, the tasks of this work are formulated:
- analyze existing methods and algorithms of digital watermarking [1];
- to develop a model of protection of marking of fixed digital files on the basis of the studied methods;
- find the optimal indicators of stealth embedding digital watermarks in the image–container;
- perform a comparative analysis of the stability of the DWM, built–in different algorithms, which will maintain acceptable levels of labeling;
- software implement the developed model with the ability to use the functions of embedding and extracting hidden data through the user interface;
- conduct experiments to confirm the performance of models and algorithms.
The object of the study is steganographic methods and algorithms for the introduction of digital watermarks in digital images.
The subject of the study is the resistance of digital watermarks to external influences on the image–container.
Thus, as a result of the work, it is planned to obtain an application program based on the methods of implementation of digital watermarks for the protection of electronic documents.
3. Overview of research and development
Currently actively many conferences are held on information security issues. The number of publications devoted to steganography and steganalysis methods is growing every year. Many Russian and foreign scientists work in this area of science.
3.1. Overview of international sources
In the world there are a large number of works, articles and publications on the development of methods for marking multimedia data with digital watermarks.
The tasks of steganographic information hiding were studied by foreign researchers: G.J. Simmons (for the first time described the model of a steganographic communication channel) [2], J. Fridrich (the new method on the basis of signs for the image taken as a standard for comparison is presented) [3], R. Anderson (the first terminology related to steganography is presented) [4], W. Bender, N. Morimoto (a contribution to development of audio steganography) [5], С. Cachin (the need to distinguish steganographic watermarks from digital fingerprints) [6], I. Pitas (specific solutions for reliable and effective protection have been proposed) [7].
It is also necessary to note works as В. Pfitzmann [8] and S. Craver [9], who created basic terminology and basic steganographic protocols.
4. Requirements for data hiding methods
Today the digital steganography has a large number of developed methods for embedding digital watermarks, each of which is divided into classes and subclasses. The overall structure is shown in picture 1 [10].
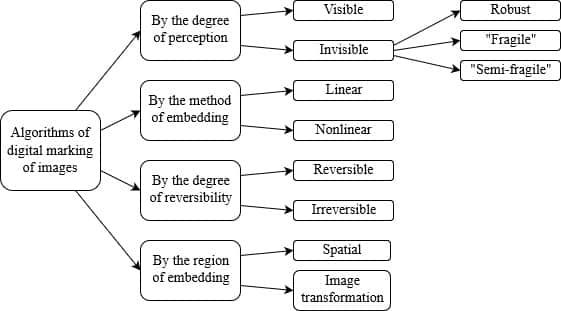
Picture 1 — Classification of algorithms
Depending on the use of data hiding algorithms, the corresponding requirements for them are determined. The most important are three requirements: the amount and secrecy of embedded information, resistance to possible attacks or distortion (the ability to extract the message after compression or modification).
Stability requirements are particularly important for steganographic algorithms that use a variety of digital data for labeling. Depending on the degree of possible distortions distinguish “fragile”, “semi–fragile” and robust digital watermarks [11].
Robust digital watermarks are resistant to most modifications of the stegano object and are used to ensure the protection of intellectual property rights.
“Fragile” digital watermarks collapse at any model container and “semi–fragile” digital watermarks are saved when you advance the known methods of distortion. These types of digital characters are used to confirm the authenticity of the marked data.
The information must be embedded in digital data in such a way that the human eye could not distinguish the original image–the container from the labeled one.
An important disadvantage is that meeting the requirements of resilience and stealth to different transformations simultaneously is challenging. Because of this, it is necessary to choose priorities for the requirements that depend on the task. Picture 2 shows the dependence of the criteria for the implementation of the digital and the embedding methods themselves.
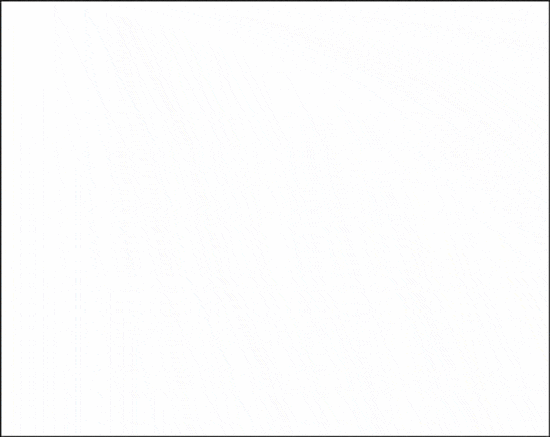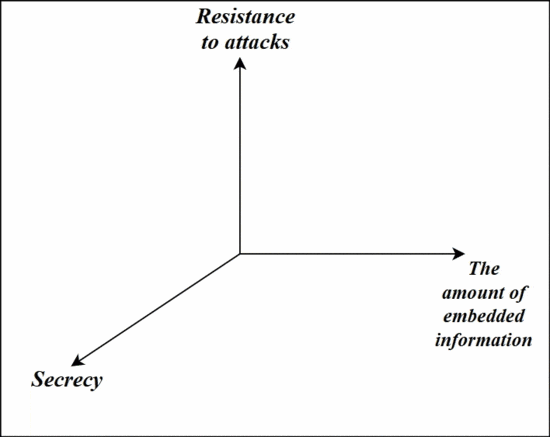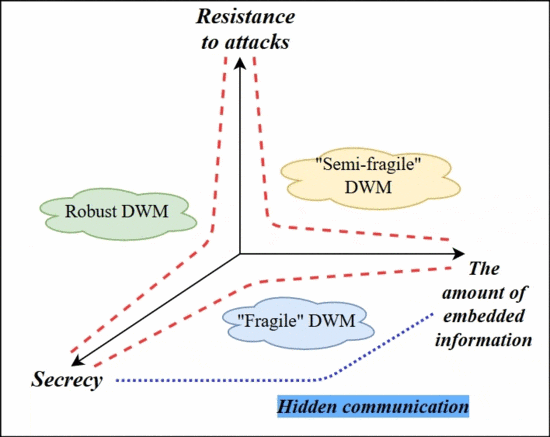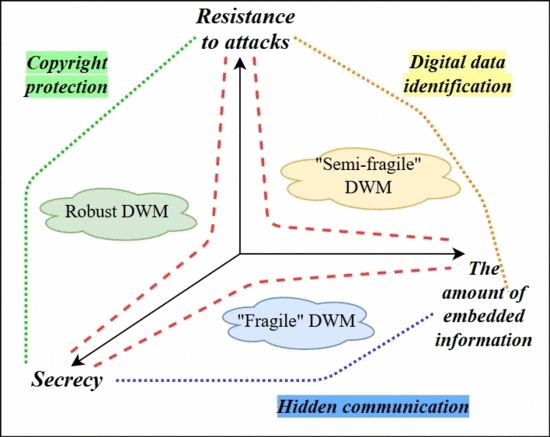
Picture 2 — Dependence of the type of DWM the main requirements of the implementation
(animation: 8 frames, 5 cycles of repetition, 120 kilobytes)
The main areas of use of steganographic algorithms are:
- hidden communication — embedded information contains a message that needs to be transmitted between two people (the main factors are the amount of information transmitted and the degree of secrecy);
- copyright protection — embedded digital watermark contains information about the author, used to prove the rights. The main task is to detect the attacker, so special attention is paid to the resistance to attacks;
- digital data identification — embedded data has its own unique number and is stored in a single whole. The difference is that there is no potential attacker.
At the moment, many digital watermark embedding technologies are used on the Internet, but not many of the algorithms have good performance protection against external influences on the container.
Conclusion
As a result of the research work were collected and studied materials on issues related to the theme of master’s work.
The study analyzed the existing methods and methods of marking fixed digital files, especially the use of different types of digital watermarks.
Due to the materials studied, it can be concluded that there are a small number of applications for the hidden implementation of digital watermarks in images, most do not have the necessary functions. The task of creating a qualitatively working application that is able to secretly mark the necessary files using methods, today has not lost its relevance.
List of sources
- Крахмаль, М.В. Исследование методов цифровой стеганографии для маркировки изображений цифровыми водяными знаками / М.В. Крахмаль, Т.В. Завадская // Современные тенденции развития и перспективы внедрения инновационных технологий в машиностроении, образовании и экономике: VI Международная научно–практическая конференция, 13–14 мая 2019, г. Азов.
- Simmons, G.J. The prisoner’s problem and the subliminal channel / G.J. Simmons // Proc. Workshop on Communications Security (Crypto’83). — 1984. — pp. 51–67. URL: https://link.springer.com/chapter/10.1007/978-1-4684-4730-9_5 (дата обращения: 25.08.2019).
- Fridrich, J. Feature–Based Steganalysis for JPEG Images and its Implications for Future Design of Steganographic Schemes / J. Fridrich // Lecture Notes in Computer Science (LNCS). — vol. 3200. — 2005. — pp. 67–81. URL: https://link.springer.com/chapter/10.1007%2F978-3-540-30114-1_6 (дата обращения: 22.08.2019).
- Anderson, R. On the limits of steganography / R. Anderson, F. Petitcolas // IEEE J. on Selected Areas in Communications. — vol. 16, № 4. — 1998. — pp. 474–481. URL: https://www.cl.cam.ac.uk/~rja14/Papers/jsac98-limsteg.pdf (дата обращения: 20.08.2019).
- Bender, W. Tehniques for data Hiding / W. Bender, D. Gruhl, N. Morimoto, A. Lu // IBM Systems Journal, 35 (3&4). — 1996. — pp. 313–336. URL: https://pdfs.semanticscholar.org/8c82/c93dfc7... (дата обращения: 27.08.2019).
- Cachin, C. An information theoretic model for steganography / C. Cachin // Proceedings of 2nd Workshop on Information Hiding. D. Aucsmith (Eds.). Lecture Notes in Computer Sciences, Springer–verlag. — 1998. — pp. 306–319. URL: https://eprint.iacr.org/2000/028.pdf (дата обращения: 27.08.2019).
- Pitas, I. A Method for Signature Casting on Digital Images / I. Pitas // Proceedings of ICIP. — vol. 3. — 1996. — pp. 215–218. URL: https://www.semanticscholar.org/paper/A-method-for-signature-casting... (дата обращения: 28.08.2019).
- Pfitzmann, B. Information Hiding Terminology / B. Pfitzmann // Information Hiding, Springer Lecture Notes in Computer Science. — vol. 1174. — 1996. — pp. 347–350. URL: https://link.springer.com/chapter/10.1007%2F3-540-61996-8_52 (дата обращения: 30.08.2019).
- Craver, S. Can Invisible Watermarks Resolve Rightful Ownerships? / S. Craver, N. Memon, B. Yeo, M. Yeung // IBM Research Report. — 1996. — pp. 573–586. URL: https://pdfs.semanticscholar.org/a7f3/0abe129bdd... (дата обращения: 30.08.2019).
- Хорошко, В.О. Основы компьютерной стеганографии: Учебное пособие для студентов и аспирантов / В.О. Хорошко, О.Д. Азаров, М.Э. Шелест. — Винница: ВДТУ. — 2003. — 143 с. URL: http://ir.lib.vntu.edu.ua/bitstream/handle/123456789/12616... (дата обращения: 13.09.2019).
- Конахович, Г.Ф. Компьютерная стеганография. Теория и практика / Г.Ф. Конахович, А.Ю. Пузыренко. — К.: МК–Пресс. — 2006. — 288 с. URL: https://www.twirpx.com/file/11476/ (дата обращения: 07.09.2019).
