Abstract on the topic of the thesis
Content
- Introduction
- 1. Problem statement
- 2. Technical support
- 2.1 Languages working with the server
- 2.2 Database management system
- 2.3 Mobile application development software
- 2.4 MVC architecture
- 3. Research and development overview
- 3.1 Security overview in framework
- 3.2 CMS security overview
- 3.3 Standard solutions for the protection of the site
- 4. Using previously researched methods to develop
- Summary
- Source list
Introduction
Now it is very popular and useful to have your own website, whether it is just a blog or a business site. The need for them is growing as., nowadays most of the time and work relies on the Internet. There are always people in demand who can not only create the right site, but also protect it. During the development of the site there are always various problems: its protection and performance, the load with which the server will work.
1. Problem statement
Vulnerabilities are present on any site or application, for example, in a form in a PHP handler. If it is developed without protection, then it can send a request to the server, a script, a dangerous or infected file, and SQL injection can be performed. In such cases, it is impossible to lose important data or lose your site. During the development process, most of the time may be required to create a safe use of the site.
The aim of the work is to research security and develop a site, as well as a mobile application for it. During the work, an analysis of the popular framework and CMS (content management system) and analysis of user solutions will be carried out. The end result will be a website and a mobile application that can be used to create: a blog, an online store and similar resources.
This development will be able to perform the following functions:
- Registration\ user authentication;:
- data management via admin panel;
- creating your own routers;
- using MVC (Model-View-Controller) capability);
- possibility of processing the admin panel;
- order processing;
- sending data to applications via your own routers;
At the moment — this is not a complete list of possibilities.
2. TECHNICAL SUPPORT
Software plays an important role in the development, because depending on the selected software will depend on the work on the server side. The following will be used for development: Expo\ React Native, PHP, PDO, JS/JQ, HTML, CSS, Redux, Bootstrap, Apache, MVC architecture, git version control system.
2.1 Languages working with the server
PHP is a programming language used to write web applications. This language is constantly improving, most developers use it to work. The improvement made it possible to use object-oriented programming (OOP). Table 1 lists the languages that work with the server.
| Title | Web-server |
| ASP | Specialized |
| ASP.NET | Specialized |
| C/C++ | Almost anyone |
| Perl | Almost anyone |
| PHP | Almost anyone |
| Python | Almost anyone |
| Ruby | Almost anyone |
| Node.js | Own |
2.2 Database management system
PDO (PHP Data Objects) is a general database level with MySQL support among many other databases (DBs). This provides prepared statements and considerable flexibility regarding how the data is returned. Very suitable if you need to modify the database. You can work with the database, this allows you to not do database analysis, a special driver will do this. Of the methods for dealing with sql injections, prepared appeared. A prepared statement is a precompiled SQL expression that can be repeatedly executed using various data types. [7].
2.3 Mobile Application Development Software
React Native is designed to create native iOS and Android applications. It is based on the React JS library developed on Facebook for creating user interfaces. This framework is focused not on the browser, but on mobile platforms. When developing your application, you can use React Native to write clean, fast mobile applications using the familiar React JS library and a single JavaScript code base. React is a JS library for creating user interfaces for web applications. React is widespread, and unlike larger MVC environments, it solves a relatively narrow task: rendering the interface. React can be used to develop single-page and mobile applications. Its goal is to provide high speed, simplicity and scalability. As a library for developing user interfaces, React is often used with other libraries such as Redux. [4,5].
2.4 MVC Architecture
MVC architecture allows you to divide the application code into 3 parts: model, view or view and controller. It was first described in 1978 and was intended for GUI applications (windows and buttons), but was later adapted for web applications [3].
Partitioning simplifies large code. If you write code in one long script, it becomes difficult to understand, and it is difficult to make changes without errors.
Partitioning does not mean that the code should have exactly 3 files (or 3 folders with files, or 3 classes) with the names model, view and controller. MVC does not set limits on how to organize code files. In practice, the model often takes up the bulk of the application, and is presented in the form of a large number of different types of classes - entities, services, classes for working with the database, and separate folders are created for each type of class. Figure 1 shows the data transfer in this architecture.
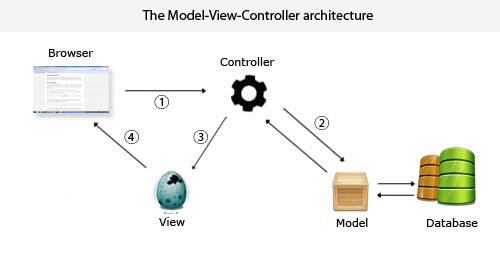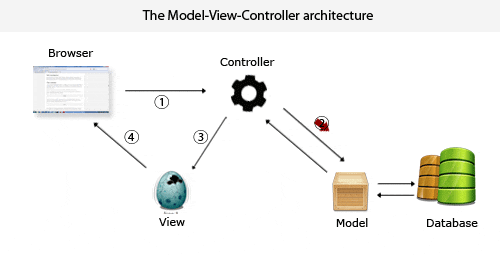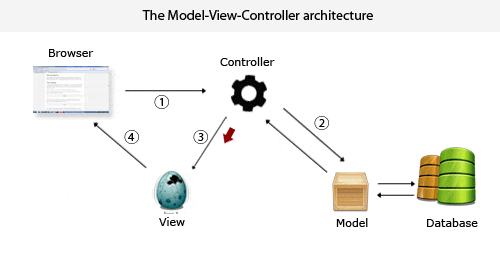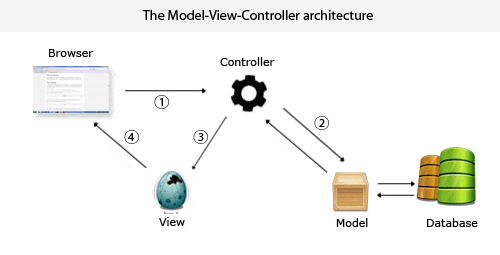
Figure 1 - data transfer to MVC Animation: 58 frames; number of repetitions: 7 repetitions; 16 kb
MVC is applicable to different types of applications - both server-side web applications and desktop (client) applications. The difference between the two is that in the web application the program receives one request from the user, processes it, displays the result, and terminates. If another request arrives, a new, independent copy of the program will be launched to process it. Unlike web applications, desktop, mobile applications (as well as JavaScript applications that run on a browser page) are long-lived. They process a lot of requests from the user and update the information on the screen, not ending [3].
3 Research and Development Overview
The security of a site, system, or something is usually not public information. During which standard methods for implementing basic protection methods that can be used for your own purposes appear.
3.1 Security overview in the framework
Laravel is a free open source framework that is popular with web developers. This framework is intended for development using the MVC architectural model.
At the beginning of the work, some methods and functions for security are available. Password storage provides a class called "Hash" that provides secure caching for Bcrypt. The make () function that belongs to this class takes a value as an argument and returns a hashed value. The hashed value can be checked using the check () function.
$password = Hash::make('secret');
Hash::check('secret', $hashedPassword)
User Authentication in Laravel - User authentication and certain actions. This framework allows you to perform this task much easier, for this you need to use the Auth :: attempt method [1].
if (Auth::attempt(array('email' => $email,
'password' => $password))) {
return Redirect::intended('home');
}
The Auth :: attempt method takes credentials as an argument and compares them with the credentials stored in the database. If the data matches, true is returned; otherwise, false. The authentication method contains the following security methods [1]:
- Protection against CSRF (cross-site request forgery) / XSS cross-site scripting - attacks using cross-site scripting are carried out when an attacker is able to place JavaScript code on the client side on a page viewed by other users. To protect against this type of attack, there should always be a check on user data and not allow the addition of dangerous signatures
- SQL injection - injection vulnerability is associated with the insertion of unfiltered arbitrary user data into a SQL query. By default, Laravel uses the PHP Data Object Class (PDO).
3.2 Security Overview in CMS
WordPress is an open source site content management system; written in PHP; database server - MySQL; released under the GNU GPL version 2. Scope - from blogs to fairly sophisticated news resources and online stores [6].
If you look at the WordPress database in a standard installation, you can see that all tables start with wp_. This gives attackers the opportunity to obtain personal user data. An easy way to enhance WordPress security is to turn the prefix into a random value.
$table_prefix = 'dad34_';
By default, if someone tries to enter a site with incorrect credentials, WordPress will report which field of the problem. This gives a lot of information, because the CMS gives half of what someone needs to get to the site. To fix this problem, you need to add the following code to the functions.php file:
function error_mesg ( ) {
return 'Login ***' ;
}
add_filter ( 'login_errors' ,
'custom_wordpress_error_message' ) ;
It is worth considering that WordPress has a large database of plugins where you can always find the right one.
3.3 Standard site security solutions
There are standard solutions that should be used:
- Using CNC - human-friendly URLs (Uniform Resource Locator - a pointer to the location of the site). You should not use a URL with passing parameters in it, through passing parameters you can perform SQL injections. In cases where you need to transfer something to the server through the URL, you should process it [2]. For example, if a number is passed, you can do the following $ post_id = (int) $ _ GET [`id`]. One of the options is to process the data with special PHP functions: $ post_id = htmlspecialchars ($ _GET [`id`]);
- Use proven libraries and plugins. There are sites and repositories that allow you to add these distributions through package managers: npm, yarn, composer and many others. On the site you can always get information about the latest version of the library or plugins, as well as find out what changes were.
- Configure https protocol. HTTPS (Hypertext Transport Protocol Secure) is a protocol that ensures the confidentiality of data exchange between a site and a user device [1]. Information security is ensured through the use of cryptographic protocols SSL / TLS, which have 3 levels of protection: encryption, authentication, data security.
- Validate the form not only on the server side, but also on the client side.
- Install captcha on the site. There are various captcha, but one of the well-established ones is google recaptcha v3.
4. Using previously explored development methods
The developed application and the site currently have some developments. An NC is implemented with routing that can be seen in Figure 2. This routing uses regular expressions for URLs, where the first parameter is the name of the controller and the second parameter is action (in figure 3, the controller code is shown).
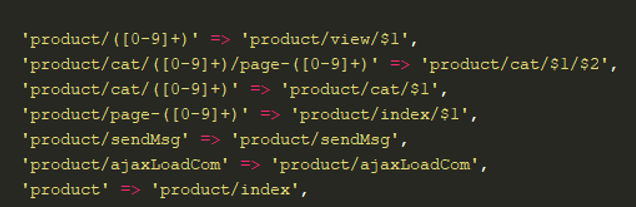
Figure 2 - An example of the implementation of routing
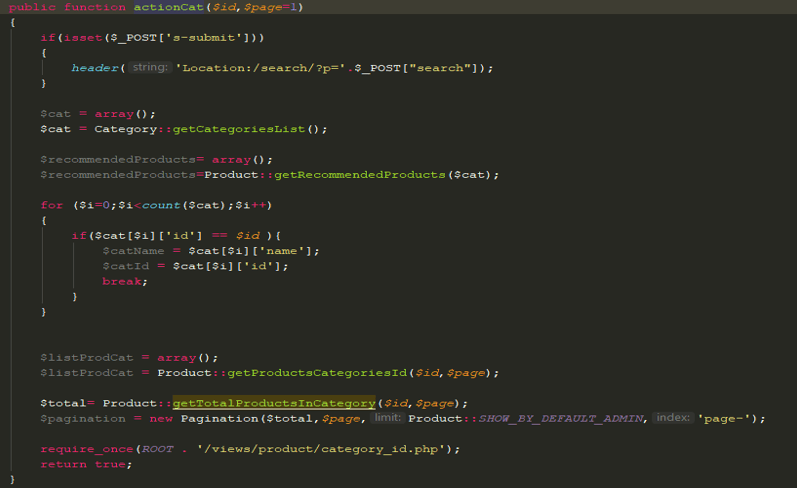
Figure 3 - Controller action code
Implementation of protection against CSRF attacks has begun. The implementation has not been completed completely since needs improvements in working with Asynchronous Javascript And Xml (AJAX) requests. AJAX is a technology for accessing the server without reloading the page. The implemented protection will not only make it possible to exclude calls from other resources, but it will also provide protection for the routings used by the mobile application.
Functions have been developed for creating tables in the database using PDO, as well as a function for working with the table prefix in the database. This function works by default with a prefix from the settings file, but it is possible to specify a different value. The function to create tables in the database will create a structure with ready-made settings and fields. You can usually import into the database or create tables manually.
There is a possibility of registration \ user authentication. The user is assigned a specific role that limits his actions on the site. He can change his contact details, password, email, restore password, track changes to his order.
It was the beginning of the implementation of an application that has the ability to work with the Application Programming Interface (API). Redux storage is connected for working with data. Validation for registration / authentication forms is being developed (an example of the graphical form of the forms in Figures 4.1 - 4.2). The following screens are available for work: home, single product, registration, login, password recovery, personal account. To navigate between them, navigation was configured using the React Navigation library.
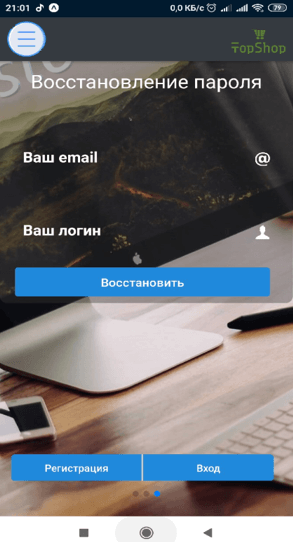
Figure 4.1 - Registration Screen

Figure 4.2 - password recovery screen
Conclusion
The development of the application and site using the analyzed methods has begun. The analysis of security methods is carried out on the example of popular framework and CMS, as well as some standard methods. When writing this essay, the master's work is not yet completed. Final completion: May 2020. The full text of the work and materials on the topic can be obtained from the author or his leader after the specified date.
