Abstract
Content
Introduction
Security alarm systems, together with video surveillance systems, are used to organise security at facilities in various areas. The use of these systems often reveals their shortcomings, which can cause both direct material losses and losses resulting from increased mental strain on personnel [1]. Separately, disadvantages such as the high probability of false alarms for alarm systems, the need for a constant presence of an observer and the limited number of cameras viewed by one observer for video surveillance systems can be highlighted.
Recently, technologies for intelligent video signal processing have become widespread. The introduction of these technologies in the sphere of object protection can significantly improve the efficiency of security systems and to some extent simplify them in terms of the used technical means[2].
The objective is to create a concept of a centralized automated system for the protection of objects on the basis of video surveillance systems, define the basic structure of such a system and systematize the approach to its construction.
State of the matter
Video surveillance currently has a huge impact on people's lives and safety, so its significance simply cannot be underestimated. This industry is constantly absorbing all the latest scientific and technological developments, due to the use of video surveillance in industry, agriculture, and the fact that the various media is generated a huge amount of video data, requiring a certain amount of data storage with high capacity. The resolution of video images is increasing all the time, and the amount of stored content is increasing manifold. That's why implementing new technologies in video surveillance is one of the most important challenges in today's world.
Video surveillance systems with intelligent features can do this more effectively. In multiple studies, the effects of fatigue and loss of concentration on efficiency of such systems have already been documented.
Of course, most modern standard video surveillance systems have rudimentary video analytics capabilities, such as motion detection. But that's not good enough for a lot of today's needs. It was to solve them that video analytics was developed [3].
Video analytics – computerized processing and automated analysis of video content that comes to the video server from video cameras, wearable devices and Internet devices equipped with webcams.
Video analytics has grown in popularity in recent years for a variety of reasons. For example, it allows you to flexibly manage video streams when analyzing video content, automating analytics functions. This allows employees to focus on certain incidents from video footage and not to waste time watching long video streams, thereby reducing costs and headcount. Intelligent security systems with video analytics have the function to start recording only when there is some movement in the camera view area. This reduces the load on the network and saves storage space. Video analytics systems can provide valuable insight into the performance of staff, enabling a more accurate assessment of staff performance.
Video analytics fundamentally automates the surveillance process, making it easier to use and significantly reducing costs for businesses with video surveillance. In addition, factors such as the growth of industrial automation are driving the demand for video analytics in various industries, such as finance, retail, transportation, mining, manufacturing and others. In addition, the growing requirements on security systems and their infrastructure, and the increasing importance of security in daily life are also driving the near-term growth of the video analytics market.
Video analytics requires no cumbersome infrastructure, and even small businesses or retail stores can easily afford to use it. The frequency of use of video analytics features can be adjusted as needed, so businesses can choose the features they want based on their unique requirements. This allows solutions to be tailored to the individual requirements of the entrepreneur [4–6].
Main part
The best option is to build such systems on the basis of integrated security systems, excluding the use of video recorders where possible, as the organisation of centralised surveillance requires flexibility and functionality that cannot be provided by devices of this type [7]. However, given that video surveillance systems can be deployed at facilities that are built using both analogue and IP systems, it is necessary to use a software platform that allows them to be combined without reducing their functionality and offering new tools for video content analytics.
The following requirements can therefore be made to the proposed system:
- the system must be able to use both analogue and IP video cameras;
- the system should, where possible, exclude the use of DVR, NVR, etc.;
- the system should ensure the possibility of effective centralised video surveillance.
Axxon Next, SecurOS and the XEOMA software are proposed as platforms for building the system. Approximate figures for outgoing and incoming network flows, as well as the disk space occupied, are shown in Table 1 (data in the calculation table are presented for comparison and are based on system calculators provided on the official websites of software manufacturers for 10 cameras).
Table 1 – Proposed software
| XEOMA | Axxon Next | SecurOS | |
|---|---|---|---|
| Outgoing network connection | 2 Mbps | 20 Mbps | 23 Mbps |
| Incoming network connection | .19 Mbps | 20 Mbps | 23 Mbps |
| Necessary disk space | 22 Gb | 80 Gb | 80 Gb |
It should be noted that the XEOMA software platform in the list of integrated devices states that it allows tthe connection of virtually any video capture device and is therefore more preferable when building a centralised video surveillance console.
In order to organise the system, several construction options are offered as shown in Figure 1. The choice of a particular structure is based on the available hardware capacity and the bandwidth of the communication channel. The optimal option is to have equipment connected to the site using a dedicated Ethernet line, but other types of communication channels (GPRS, LTE, Wi-Fi, etc.) can also be used.
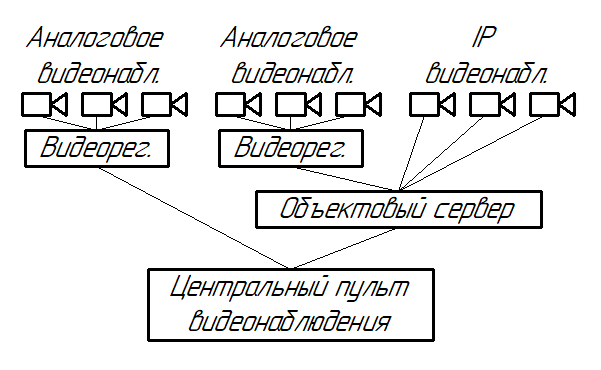
Figure 1 – A variant of the proposed system structure
The figure shows two connection options. The first (left) involves the direct connection of an analogue video recorder or IP video cameras to the central video surveillance desk. This structure is the simplest, but it limits the number of video cameras and increases the load on the control desk equipment, as it is responsible for all video processing.
Other option is to use object servers, the number of which may depend on the number of cameras on the site and its area. In this case, the primary processing of video information takes place at the facility itself, and the video signal is transmitted to the central console only when a given algorithm detects a violation of the standard mode, or at the operator's request. This option is the most effective for medium and large facilities where a large number of video cameras are used.
If the number of cameras used is small, a structure variant using single board computers as an object server can be used. This option is the most cost-effective. Single board computers are small in size but have sufficient hardware capacity to process the video signal from 2-4 video cameras (the exact number depends on the type of single board computer used and the video cameras used).
All of the above options allow for complete recording of information at the facility and recording at the central control panel.
The software products presented earlier allow for flexibility in creating algorithms for the protection of objects, creating a unique approach to the protection of each of them. The main advantage of the proposed centralized systems is the use of intelligent processing to significantly reduce the probability of false alarms due to the possibility of remote verification by the operator on the control panel. A possible algorithm of actions in case of an alarm is shown in Figure 2.

Figure 2 – Possible algorithm of actions when receiving an alarm from a security object. The animation consists of 4 frames with a 1 second delay inbetween; delay before replay is 5 seconds; the number of playback cycles is limited to 10
The system allows to eliminate the disadvantages of alarm and video surveillance systems by using a similar algorithm:
- for each camera in the protected object its own conditions for the alarm is created; .
- the object is armed; .
- signal from one of the cameras triggers the alarm for the operator of the surveillance console; .
- operator, after estimating the threat, permits further operation of the algorithm; .
- depending on the algorithm, further action is taken (calling the guards, turning on the sound alarms, the use of any automatic systems at the facility).
This way, it's not necessary to continuously monitor every camera, and if a false alarm occurs, the operator can choose to watch every camera in the facility and carefully analyze the entire location before triggering an alarm.
The system's capabilities are not limited to security, but also include access control, site monitoring and automation.
The number and variety of such algorithms is limited only by the user's imagination and the power of the equipment they use. We'd also like to highlight the financial benefits of the system. If a small number of cameras (up to four), it's possible to use just a single on-site PC, which significantly reduces costs compared to a traditional surveillance system, just by eliminating the DVR from the system, while also dramatically reducing the size of the equipment.
Video archiving options are also broad: it can be archived continuously, not archived at all, only archived at specific times, or triggered by preset algorithms. Archiving can take place either at the site itself or at an endpoint, and there is the option to dedicate a dedicated standalone server to it.
It should also be possible to integrate the proposed system with security alarm systems by synchronising them and creating mutual links, for example, through databases, followed by the automation of this process.
Conclusions
The main points of the proposed concept can thus be highlighted:
- use of a multi-level construction structure consisting of video cameras, object servers, communication channel equipment and central console equipment;
- use of intelligent video signal processing and related software products both at the security facility and at the central video surveillance desk to provide flexibility and functionality not available in traditional systems based on video recorders;
- use of existing equipment already installed at the security sites, providing ample opportunity to upgrade and expand the system with equipment from various manufacturers;
- the possibility of using single board and miniature computers as object servers at small or remote sites where it is difficult or not profitable to use standard video surveillance equipment;
- the possibility of integrating the system with security alarm systems at security sites.
References
- Сабанин П.В., Чупров Л.Ф. ЛОЖНЫЕ СРАБАТЫВАНИЯ ТЕХНИЧЕСКИХ СРЕДСТВ ОХРАНЫ И ИХ РОЛЬ В ПСИХОЛОГИЧЕСКОМ СОСТОЯНИИ СОТРУДНИКА ПОЛИЦИИ // Наука. Мысль. – 2016. – № 5–1.
- Гордин М.С., Иванов С.А. Алгоритмы обнаружения тревожных событий для систем автоматизированного видеонаблюдения // Вестник НГУ. Серия: Информационные технологии. – 2017. – Т. 15, №3. – С. 21-30.
- Могилин К.А., Селищев В.А. Интеллектуальные системы видеонаблюдения в комплексах безопасности // Известия ТулГУ. Технические науки. 2020. №3.
- Катковский Л.В., Воробьев С.Ю. Применение видеотехнологий для повышения пожарной безопасности объектов // Доклады БГУИР. 2011. №1 (55).
- Зенов А.Ю., Мясникова Н.В. Применение нейросетевых алгоритмов в системах охраны периметра // Известия ВУЗов. Поволжский регион. Технические науки. 2012. №3 (23).
- Ярышев С.Н. Цифровые методы обработки видеоинформации и видеоаналитика: учеб. пособие. СПб.: СПбГУ ИТМО, 2011. – 83 с.
- Торстен А., Келлер И., Лутц Х. Видеоаналитика: Мифы и реальность. – Москва: Security Focus, 2019. – 186 c.
