Аннотация
S. Kukhta, O. Sokolova. The five-level data protection model. The five-level data protection model is described in the article. The basic idea of this approach is a message breaking-up into small pieces and their distribution over few different communication channels. This technique can provide the impossibility of reading the message by the interceptor, when he has just one part of the data. The author touches upon the advantages and disadvantages of this model of information transmission.
Nowadays the protection of transmitting and storing information is based upon the principles created in cryptography and steganography. Using cryptographic methods a protected message is converted into unreadable one without key character set. Steganographic techniques allow us to create a private link, which is hard to be detected even with the use of special information processing methods. The placement of hidden information in the containers occurs with the help of the key set too.
Specialists have made a lot of effective cryptographic attacks on famous cyphers and steganographic methods of protection. The presence of successful attacks indicates the vulnerability of the existing principles of information protection.
The development of information security tools and tools for cyphers attacks, methods of hiding messages have competitive (iterations) character. Usually a widespread cypher is effectively attacked a few years later after its creation and its application gradually fades away. The method of brainstorm concerning the creation of new protection algorithms is stimulated by the international competitions.
A fundamentally new approach of information security may become the method of forming several levels of message protection (Fig. 1). Figure 1 shows five possible information protection barriers. In this case a message is any transmitting (storing) information or data [1].
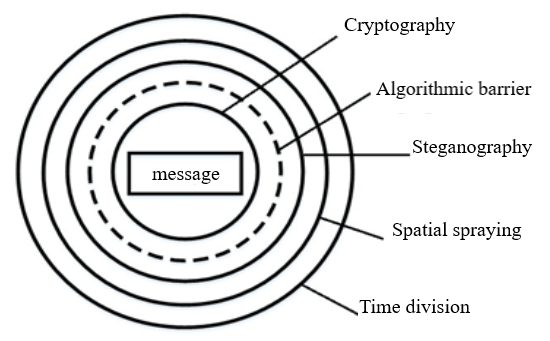
Figure 1 – Possible information protection barriers
Spatial spraying of information may become one of additional information protection barriers (besides cryptographic and steganographic). The basic idea of spatial spraying of information is in a message breaking up into some much smaller components (sentences, words, symbols, blocks of characters, groups of bytes, bytes, groups of bits, bits) and their delivering in pieces and distributing over several communicational channels (K1…Kn). The interception of all message components by breaker C (Fig. 2) is complicated by the fact that correspondents A and B have the opportunity to use several telecommunication channels available for them (radio, satellite, wire, cable, radio relay).
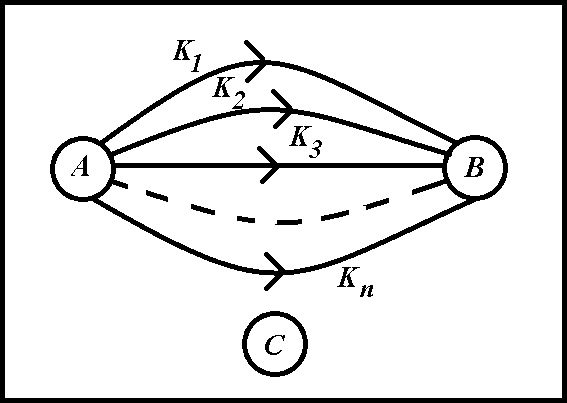
Figure 2 - Interception of a message by breaker C
Information transmission in global networks is possible due to many existing services (e-mail, messengers, chats, forums, blogs, distributed databases WWW, etc.). The use of cellular communication allows us to spray a message over several MMS or SMS and transmit them using a large number of telephone channels.
Besides three levels of protection of transmitted information mentioned above another level can be created (the fourth one), which is technically and algorithmically harmoniously combined with the considered barriers. This is a temporary message breaking-up (data transmission according to a pre-agreed schedule).
The spatial and temporal message breaking-up fits together perfectly and complements one another. These two barriers can be represented as a single one and can be called as a spatio-temporal spraying of a message. The idea of spatio-temporal spraying of a message is illustrated in Figure 1.3.
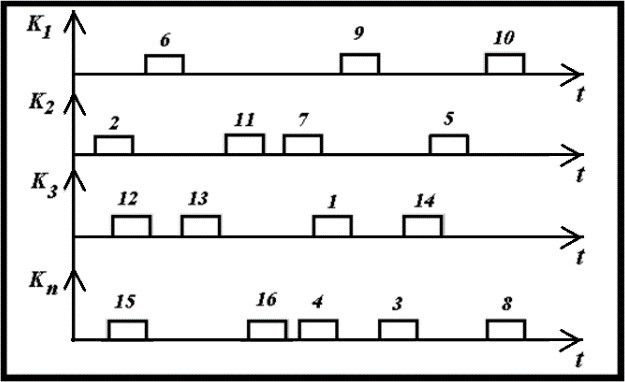
Figure 3 – Spatio-temporal spraying
Information blocks No.1…9 that contain sending message, are transmitted in pseudo-random order by communication channels (K1…Kn). Moments of transmission of message blocks are pseudo-random too. Information blocks transmission is mixed with sending masked (misinforming) blocks No.10…16. Blocks translation order, channel numbers and temporary windows are set with the help of a secret key.
It is worth to admit that if only one telecommunication channel is used for a link a spatio-temporal barrier changes into temporal one.
The fifth (algorithmic) barrier is based on special way of processing of transmitting blocks, when absence of even one of intercepted blocks causes cryptanalyst insurmountable difficulties. The closest ideology (in design and use) to this barrier are encryption modes, which are described in the domestic standard GOST 28147-89, the American standard DES and many publications [2]. The fifth barrier is like a continuation of the cryptographic one, but methodologically it is advisable to divide it into a separate level of protection.
Thus, the principle of complex, multi-level information protection can be implemented by creating various barriers. In each case the participants reasonably choose a sufficient degree of message security (the number of barriers used, the type of cypher, the key length, the types of steganographic containers, the methods for steganographically embedding information in containers, the type and number of communication channels or storage media used, the number of time windows for transmitting information).
It is clear that the implementation of proposed measures of high cryptographic stability is accompanied by an increase of the time transmission, the number of errors in a message transmission. All these complicate the transmission of a message and reduce the convenience of information storage. It is possible to regulate the degree of message protection (that means the variety of time of message transmission and changing service properties) by a selective use of some of barriers (not all of them) but only a sufficient part of them. On-line transmission of information (when the value of information is calculated in hours and even minutes) can occur with a minimum numbers of used barriers.
References
1. Алексеев, А.П. Сокрытие информации в звуковых WAV-файлах [Электронный ресурс] : методические указания по проведению лаб. работ по дисциплине "Информатика" / А.А. Аленин, А.П. Алексеев .— Самара : ИУНЛ ПГУТИ, 2010 .— 11 с. — Режим доступа: https://rucont.ru/efd/278728
2. Алексеев, А.П. Стеганографические и криптографические методы защиты информации [Электронный ресурс] : учеб. пособие по дисциплине "Информатика" / В.В. Орлов, А.П. Алексеев .— Самара : ИУНЛ ПГУТИ, 2010 .— 289 с. : ил. — ISBN 978-5-904029-12-8 .— Режим доступа: https://rucont.ru/efd/278727