 |
Vladimir O. Kuz'menko
 |
Faculty: Computing engineering and science |
1. Introduction. Ground of actuality of theme
Concordantly to information of PricewaterhouseCoopers (PWC), only 22% modern organizations did not feel any incident on informative safety for the last year. In comparsion with 2002 (36%) this number diminished practically in one and a half times. Does it mean, that the number of security incidents has been increased? Probably, does it no. Just now, the company is able to record those cases that had been hidden from their attention previously.
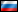
Answering a question, how it is possible to protect information from these misfortunes, from all of modern technologies the most obvious variant – data encryption (picture 1). Really, if encrypt data on a transmitter with one of the modern encryption algorithms with 128-bit key and higher, it is possible to be untroubled for safety of information on this transmitter in case if a transmitter gets in a malefactor hands.
Picture 1. Measures to protect information in the modern organizations, according to the PwC(Animation, 80 shots, 9,12 Kbyte)
Today, as encryption devices most widely use three types of encoder: software, hardware and software and hardware. Their fundamental difference is not only in the method of encryption realization and degree of reliability of data protection but also in a price, that often becomes a determinative for users. As a rule, the most inexpensive solution - software, followed by software and hardware and, finally, the most expensive - hardware. But while the cost of hardware encoder significantly higher software, it almost always pays through a higher quality of information protection, incomparable to the difference in price.
Actuality of dissertation work theme is caused by need modern information protection markets in hardware complexes with low cost.
2. The purposes and tasks of job
A purpose of work is implementation of block encryption algorithms in a base of VLSI FPGA type.
Tasks of work:
3. Prospective scientific novelty and practical value
The peculiarity of the Master's work is in the using of principles of the parallel and conveyer data processing during optimization of the encipherement algorithms.
The practical value of work is in that algorithms realization can be successful use in the different telecommunication systems and in storage and data transmission devices. The results can also be used in the educational process in the study subjects of digital systems and protect information.
4. A review of existing research and development on the topic
4.1 Local review
The problem of information security DonNTU involved in the department: computers , radio engineering and Information protection. Be familiar with the work of the department of computer graduates, on the topic, can be in the directory of links. The questions of information protection are engaged byIvanov A. U and Krasichkov A.A.
4.2 National review
Development of information protection domain in CIS countries regulated by the legislation, , this special service Communication at the Federal Security Service Russian Federation, State Department special communications and information protection of Ukraine and relevant services of other countries. But despite the fact that the initiative crypto - studies of the state, CIS market represents firms providing
5. Conclusions
Now the following jobs has been carried out:
In future it is planned to conduct algorithms optimization on speed of enciphering. It is planned to conduct an analysis and comparison parameters of received FPGA - implementations.
6. Literature
ДонНТУ 2008 © Кузьменко Владимир