
Tsikra RodionFaculty: Computer Informational Technologies and AutomaticsDepartment of Automation and TelecommunicationSpeciality: Telecommunication Systems and NetworksTheme of master’s work:
|
| Biography | Abstract | Library (RUS) | Links (RUS) | Search Results (RUS) | Individual (RUS) |
Summary of research and developments
Topic Review
Work Relevance
Problem Research
Scientific Significance and Value of Results
The Structure of Information Space of Industrial Enterprise
The Supervisory Control and Data Acquisition System
Estimation of Reliability of Information in Corporate Networks
Results
Literature
Introduction
The corporate network of a large industrial enterprise is geographically distributed, combining offices, branches, offices, shops, warehouses, and other structures located at a considerable distance from each other. Most sites of corporate networks are located in different cities and even countries. Such kind of network can be divided into two parts: a local (peripheral) and leased lines (trunk). Fiber-optic trunk lines provide the probability of error near 10^(-9), so this work will focus on the peripheral part, affected to interference from various different sources.
Topic Review
As the transfer of data through the communication occurs in a high level of electromagnetic interference, the packet transmitted in the formation of pre-processed data to improve the reliability of transmission. The main methods of data processing in order to increase noise immunity are:
* splitting the package into separate blocks and calculate a checksum for each block;
* unjammable coding (adding redundancy).
To increase the immunity transmitted data is divided into blocks. Then for each block checksum is calculated, which is transmitted after the block of information. The usage of a checksum to provides detecting single-packet errors.
To reduce the number of transmission repeats of information packets and, consequently, to increase bandwidth, as well as more reliable data direct error correction methods can be used by chosing noiseproof coding with forward error correction(FEC). Usually for this purpose the codes Reed-Solomon (RS) of various types or Hamming code (U.S.) are used. Note that usage of FEC reduces the "information" data transfer rate. Despite the reduction of speed, usage of FEC is justified in complex jamming environment, while it reduces the number of packet retransmissions and thus reduces the total time required for reliable data transmission.
Work Relevance
The most common networking technology at the moment is Ethernet. The protocol stack TCP/IP is already implied guarantee delivery of packages, in the event of loss or damage to the package is passed again. The new high-speed full duplex standard notion of «domain conflict» is no longer valid. However, the production usage of full-duplex is meaningless, the main task of the sensors and other sources of information is reliable delivering of status data of equipment, lines, processes in general. Here collisions are still possible and decreasing network performance.
Therefore the solution that will reduce the chance of error data in accordance with the request has to be found. The method must entertain all significant obstacles encountered in the workplace, should have easy implementation, and be advantageous for the value than the installation of the latest version of equipment standards.
Problem Research
To perform the objectives of work the following tasks must be done:
* to characterize the information space of industrial enterprises (corporations);
* to analyze the existing corporate network interference;
* to develop a model of the corporate network errors;
* to select and justify the method to ensure the reliability of information;
* developing and researching tool for the reliability of information;
* to make recommendations for the implementation of methods designed to ensure the reliability of the information on the corporate network.
Scientific Significance and Value of Results
Systematizing interferences is already done. The integrated model of error is based on it. In the final stage of work the turbo coding will be explored as a method of ensuring the reliability of information transmission. At the moment there are not many methods for assessing its anti-interference properties. This is mainly the results obtained by simulation with the detailed conditions. There is no exact theoretical description available yet.
The Structure of Information Space of Industrial Enterprise
The information space of whole concern is a collection of information spaces of the components of the enterprise: facilities management, control centers, and external objects (Fig. 1). The space object information comprises the following components:
1. space of primary messages from sources of useful signal;
2. space of secondary messages identified by the initial reports and going from sources of secondary signals;
3. space of useful impacting object signals, formed by the sources of feedback signals;
4. useful signal space formed by the sources of signals, the operator interacts with the space and space control centers through the physical environment messaging;
5. space of input signals of feedback, the operator interacts with the space and space control centers through the physical environment messaging.
The space of object interacts not only with the space control centers, but also from other areas objects. The space control centers includes a space of input signals, useful output signals, interacting with the space manager, specialists, other centers and facilities through the physical environment messaging.
The space center is working with the administration of the entire space, including space outside sources of information.

Figure 1. Composition and structure of the interactions of information spaces of enterprise
Blocks appointment:
1 – input signals space;
2 – sources of output signals;
3 – interference;
4 - useful output U signals space;
5 – manager's area;
6 – specialist's area;
7 – interfere signals sources;
8 – other controlling center's space;
9 – administration center's space.
Interfere signals cources create space of interfering signals distorting useful signals (creating information error noise) .
The Supervisory Control and Data Acquisition System
The concept of SCADA (Supervisory Control And Data Acquisition) is predetermined for all the evolution of management systems and the results of scientific and technological progress. Application of SCADA-technology allows a high level of automation in the tasks of developing management systems, data collection, processing, transmission, storage and display of information. Friendliness of man-machine interface (HMI / MMI), provided by SCADA-systems, completeness and visualize of information, accessibility «leverage» manage, user-friendly prompts and help system, etc. - increases the efficiency of interaction with the system controller and brings critical errors in controlling to zero.
It should be noted that the concept of SCADA, based on the development of automated management systems, allows to solve several problems, long considered intractable: reducing the time of project design automation and direct financial costs of their development. Currently SCADA is the main and most promising method for automated control of complex dynamical systems (processes).
Following tasks are the most important in the implementation of modern systems of dispatching management:
* chosing of SCADA-system (based on the requirements and specificities of the technological process);
* personnel tracking.
Many automated systems for monitoring and management for a large range of applications make it possible to provide the following generalized scheme for their implementation. Typically, this two-tier system, as these levels are implemented direct control of technological processes. The specifics of each control system is defined at each level of the software-hardware platform.
Lower level - the level of the object (controller) - includes a variety of sensors to gather information about the process, electric drives and actuators for the implementation of regulatory and control actions. The sensors supply information to the local programmable logical controllers (PLC), which can perform the following functions:
* collecting and processing information about the parameters of technological process;
* management of electric and other executive mechanisms;
* task of automatic logic control, etc.
As the information in the controller pre-processed and partially used at the local place, significantly reduces bandwidth requirements for communications.
For hardware-software controller level management are applied requirements on reliability, response time for the executive devices, sensors, etc. Programmable logic controllers should be guaranteed to respond to external events coming from the object, for the time specified for each event. For critical from this point of view, objects are encouraged to use the controller with real-time operating systems (RTOS). Controllers that are running RTOS operate in hard real-time. Information from the local controllers can be sent to the network tower directly and through top-level controllers.
Depending on the task upper level controllers (concentrators, intellectual or communication controllers) implement various functions. Some of them are listed below:
* collecting data from local controllers;
* data processing, including scaling;
* maintenance of a single time in the whole system;
* timing of the subsystems;
* organization of the archives according to chosen parameters;
* information exchange between the local controllers and the top level;
* work offline with violations related to top level;
* reservation of data channels, etc.
Upper level - the control point (CP) - includes, first of all, one or more management stations, which represent automated workplaces (AWP) of manager/operator. Here it may be located database server, workstations (computers) for professionals, etc. Often used as a workstation computer type IBM PC of different configurations. Control stations are designed to display the progress of technology and operational management. SCADA has to solve these tasks.

Figure 2. Using of control systems (SCADA) in the corporate network structure
Estimation of Reliability of Information in Corporate Networks
The quality of telecommunications networks in large corporations depend on the installed equipment and using of leased access networks. If the major centers installed digital equipment, the small facilities in remote areas usually analog equipment is installed.
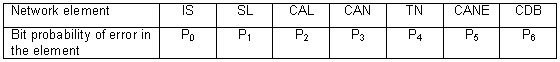
Generalized structure of the telecommunications network of the corporation, taking into account the allocation of channels for communication, is presented in Figure 1, where the CAL - dedicated channels on the lines of access, CAN - selected channels on access networks, IS - an information source (person, computer) with a subscriber line SL, IE - the source of interference in dedicated channels, CDB - central database associated with the control system CS.
One of the basic requirement in enterprise networks is to ensure reliability of information. Features of large corporate networks running in different regions are:
* using different channels and access networks;
* presence of different sources with different parameters;
* using different protocols of information exchange with various methods to combat bugs.
All this leads necessity to estimate the reliability of information in the final point - the central database.
Sources of information (operator), channels of communication lines and network access, as well as the transport network are network elements contributing errors in transmitted signals. The elements separated in space, so the errors made by them, can be considered independent.
All information sources can be divided into three groups on a territorial basis:
* distant sources located in other regions and comunicating with the CDB via the transport network (TN);
* distant sources, comunicating with the CDB via the local access network (CAN);
* sources located directly in the head office (business department) and comunicating with the CDB via the channels of communication access lines (CAL) inside production networks.
The number of radial branches of the network and sub-sources in each branch is determined by the size and structural composition of the corporation.

Figure 3. The structure of corporate network connections. i, j, k, l, m, n, s, t - the current values of the elements, branches of the network
Table 1. Quantitative characteristics of the network structure
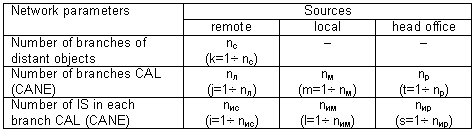
Table 2. Conditional symbols of the network and the probabilities
1. The calculation of error probability of remote sources group

Figure 4. Structure of remote sources group
The calculation is carried out through the errors of individual branches and groups.
1.1. The calculation of error probability of group IS – SL.
 j-th branch:
j-th branch:
 (1)
(1)1.2. The calculation of error probability of group IS - SL - CAL.
 j-th branch:
j-th branch:
 (2)
(2)1.3. The calculation of error probability of branch group IS – SL – CAL up to CAN.
 k-th branch:
k-th branch:
 (3)
(3)1.4. The calculation of error probability of k-th branch  (with TN)
(with TN)
 (4)
(4)1.5. The calculation of error probability of group of k branches 
 (5)
(5)1.6. The calculation of error probability of remote group with CANE (channels on access networks of enterprise)
 (6)
(6)2. The calculation of error probability of local sources group

Figure 5. The structure of local sources group
2.1. The calculation of error probability of group IS – SL  for m-th branch
for m-th branch
 (7)
(7)2.2. The calculation of error probability of group IS – SL – CAL for m-th branch
 (8)
(8)2.3. The calculation of error probability of local group of branches 
 (9)
(9)2.4. The calculation of error probability of local group with CANE
 (10)
(10)3. The calculation of error probability head office sources group

Figure 6. The structure of head office sources group
3.1. The calculation of error probability of group IS – SL  for t-th branch
for t-th branch
 (11)
(11)3.2. The calculation of error probability  for t-th branch.
for t-th branch.
 (12)
(12)3.3. The calculation of error probability  for head office sources group.
for head office sources group.
 (13)
(13)4. The calculation of error probability in CDB 
Figure 7. The calculation of errors probability in the corporate network. (number of frames - 15, the framerate - 12 fps, the delay between frames - 3c, the animation made in Macromedia Flash 8)
 (14)
(14)Results
During researching the information space of corporation (enterprise), the interference and errors in the path of communication systems, were analyzed, a general model of network errors was developed.
Using the results of a study to evaluate a system of communication to meet the requirements of noise immunity. In the case when these demands are not satisfied, using received quantitative characteristics will help to be clearly defined with the parameters means to improve the reliability of information transmission.
At the moment, the work is far from complete. In order to create the ultimate effective model it's necessary to determine the weight of the impact of different types of interference on the performance of the network. This will provide the specific values on which further selection of method for the reliability of the information will be based method. Also a model to ensure the reliability of the method (in this case, coding) will be developed, which will provide an opportunity to assess the effectiveness of solutions.
Literature
[1] Кульгин М. Технології корпоративних мереж. – Спб.: Питер, 2000. – 543 с.
[2] Олифер В.Г., Олифер Н.А., Комп'ютерні мережі. Принципи, технології, протоколи. - Спб.: Питер, 2001. - 672 с.
[3] Советов Б. Я., Яковлев С. А. Построение сетей интегрального обслуживания. Л.: Машиностроение, 1990.
[4] Бертсекас Д., Галлагер Р. Сети передачи данных. М.: Мир, 1989.
[5] Куцевич Н.А. «SCADA-системи. Погляд з боку», ЗАТ "Ртсофт", Москва, "PCWeek", N 32-33, 1998 рік.
[6] Гадасин В. А. Методы расчета структурной надежности сетей связи. М.: 1986.
[7] Филин Б. П. Методы анализа структурной надежности сетей связи. М.: Радио и связь, 1988.
[8] J. Bowles. A Model for Assesing Computer Network Reliability. IEEE Southeast CON'89: Conf. and Exhib. Energy and Inf. Technol. Southeast. Columbia, S.C. Apr. 9-12, 1989: Proc. vol.2. NewYork (NY), 1989.
[9] Кодирование информации (двоичные коды) / Н. Т. Березюк, А. Г. Андрущенко, С. С. Мощицкий [и др.]. – Харьков: Вища школа, 1978. – 252 с.: ил.
[10] Вамберский М.В., Казанцев В.И. и др. Передающие устройства СВЧ. –М.: Высшая школа. -1984.-448 с.
To the top > DonNTU > Master's Portal >
| Biography | Abstract | Library (RUS) | Links (RUS) | Search Results (RUS) | Individual (RUS) |