| Ê ñïèñêó ñòàòåé | ||
|
Management and Security Considerations for Instant Messaging in the Workplace Àâòîð: Microsoft Corporation |
||
|
Abstract This paper identifies potential threats to corporate computer security that can result from the use of instant messaging in the workplace. It discusses specific risks and defines steps that organizations can take to ensure the security of their collaborative work environment. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. December 2005 Microsoft Corporation. All rights reserved. Introduction Over the past several years, instant messaging (IM) has evolved from a tool used almost exclusively by computer experts and systems administrators into an everyday communication mechanism for business users. Technology research firm the Radicati Group estimates that in 2004, 13.9 billion IM messages were sent per day, with an increasing number of these used for business collaboration.1 Clearly, increasing numbers of businesses are realizing that real-time communications such as IM can help streamline communications and save considerable time and money. As instant messaging technology is embraced by information workers and their organizations, it is important that system administrators and information technology (IT) professionals within these organizations recognize both the value and the potential risks posed by this new technology. Businesses must ensure that, like every other technology they have in place, IM is included both in IT plans and in corporate security and usage policies. In particular, two attributes of instant messaging technology merit attention from IT professionals:
The following paper discusses the benefits and risk factors to consider when adopting IM in the workplace, as well as recommendations for implementing and managing IM to obtain these benefits without compromising the security of the computing environment. Business Benefits of Instant Messaging IM is a highly effective, expedient means of communication. Real-time text discussions harness information workers’ ability to multi-task and break through typical organizational barriers to increase productivity. For example, a user can be on the phone with a customer while using IM to gather necessary information from others in the organization to help solve a problem or close a sale. Additional benefits include:
Risk Factors to Consider For some organizations, the use of public IM clients is an acceptable, low-cost alternative to traditional forms of communication. However, reliance on public or consumer-class IM applications creates some unique obstacles:
Industry-Specific Challenges In addition to these common challenges, business may face additional issues specific to their industry or line of business. Two examples of these industry-specific considerations are presented below. Ultimately, each organization must assess its unique needs to ensure that the instant messaging solution fits well with its unique security, communications, and compliance strategy.
In each of these scenarios, the risk and exposure posed by the non-secure, unmonitored communication provided by public IM clients could outweigh the benefits of real-time communication. To implement instant messaging effectively, and without compromising security, compliance, or communications policies, these organizations require solutions that provide centralized management and tracking of IM communications. Why IM Security is Critical Organizations invest a great deal of money in security and considerable time implementing corporate policies to prevent users from becoming carriers or transmission points for malicious code; inappropriately sharing confidential company information; or sending or receiving language or materials that exposes the corporation to legal liabilities. The conversation and file transfer capabilities of consumer-class or publicly available IM applications can make it easy for users to bypass traditional security measures and e-mail policies. This leaves systems susceptible to attacks such as worms and Trojan horses that export data and create “back doors” into the system. As IM increases in popularity, its utilization as a vector for potential malicious attacks or as a means for sending unsolicited information is expected to increase as well. For this reason, it is essential that enterprises put plans in place for this new collaboration application, protecting themselves from these threats. Worms Potentially devastating e-mail worms are a common reality for any computer security professional. These e-mail threats can be dealt with effectively by using antivirus products that monitor e-mail traffic. IM-specific worms are a newer threat, and their numbers are steadily rising. Backdoor Trojans Some malicious Trojan horse programs target IM by modifying configuration settings to enable file sharing for an individual’s entire hard drive, thus allowing hackers full file access to a machine. Meanwhile, classic backdoor Trojans utilize IM to send messages to the author of the Trojan horse, giving the hacker information about the infected computer. Hijacking and Impersonation 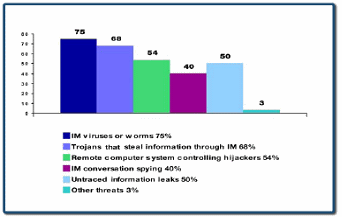 There are several ways that hackers can impersonate unsuspecting users to access their account information. As noted, a hacker can obtain the account information of a user, including passwords, via a Trojan horse. He or she can then impersonate the victim and convince the victim’s “buddies” to run files on their computers or divulge additional confidential information. A hacker can also use a simple denial-of-service exploit or other unrelated exploits to make a client disconnect. Since the server keeps the connection open and does not know that the client has disconnected, the hacker can then impersonate the user. Furthermore, since all data is unencrypted and unauthenticated, a hacker can use classic man-in-the-middle attacks such as address resolution protocol (ARP) spoofing. Phishing “Phishing” is a form of attack in which an attacker attempts to fraudulently acquire sensitive information, such as passwords and credit card details, by sending e-mail or instant messages that appear to originate with a trusted source. Phishing schemes are becoming increasingly common and increasingly sophisticated, making it difficult for users to recognize and ignore or delete fraudulent messages. Denial-of-Service Attacks Hackers can cause denial-of-service attacks on IM clients in various ways. Some attacks cause the IM client to crash. Other types of attacks make the client “hang,” and in some cases consume a large amount of CPU power, causing an entire computer to become unstable. One common method of attack is to flood a particular user with a large number of messages. Although some IM clients protect against flood attacks by allowing users to ignore other users, certain tools allow the hacker to use multiple accounts simultaneously or automatically create a large number of accounts to accomplish the flood attack. Furthermore, once a flood attack has started, a computer may become unresponsive by the time the victim realizes what is happening. This makes it virtually impossible to add the attacking user accounts to the “ignore” list of the IM client in a timely manner. Information Disclosure Tools that attempt to retrieve system information from IM users, such as IP address retrievers, are frequently used by hackers. For instance, if an IP address retriever is used in conjunction with a backdoor Trojan horse, a hacker could receive a message containing the IP address of an infected user each time the victim is online. In this manner, a hacker could know the IP address of the infected user, even if he or she uses dynamic IP addresses. Undesirable Content Because IM applications can often be used to exchange files or other sensitive information easily and without trace, organizations must recognize it as a potential threat to confidentiality and legal liability. Examples include the ease with which users can pass confidential company information, use prohibited language (sexual harassment, profanity, etc.) as well as to share unauthorized file types. The use of corporate networks to share media files (e.g.,.mp3 and .avi files) has been the subject of recent litigation, while other file types (e.g., .exe and .vbs) can be used to harbor malicious code. IM Management and Implementation Before implementing IM in an enterprise environment, organizations should carefully consider the issues described below. Evaluate Usage Understanding existing deployments and usage patterns is the first step to gaining control over IM usage in the workplace. Because many IM client applications are preinstalled or can be downloaded for free, employees may have started using IM applications on their own, unbeknownst to administrators or security officers. Several programs are available that can audit usage and identify users that have IM clients deployed. These programs are essential to developing an accurate picture of which applications are in use (including version), by whom, and what they are being used for. Assess Potential Risk vs. Value Determine the value of implementing company-sanctioned IM usage throughout the organization. How will employees and the organization as a whole benefit from presence awareness, real-time communication, reduced e-mail usage, or reduced telephone costs? Should IM be deployed for internal use only, or will it be used to communicate with customers and partners, as well? Organizations must weigh the benefits of instant messaging against potential risks to security, compliance, and corporate image that might result from use or misuse of the technology. Decide Whether to Deploy an Enterprise IM Solution The decision should be based on the value to the organization and the ability to manage risk, as well as factors including network use, availability, and security standards. Enterprise IM solutions such as Microsoftî Office Live Communications Server 2005 provide organizations with a powerful internal IM system. Regardless of whether or not an enterprise IM solution is deployed, companies must decide whether and under what circumstances to allow the use of consumer IM clients on the organization’s desktops. Establish Consistent Corporate Policies Corporate IT policies should be expanded to address IM usage. Companies should examine their motives for managing IM at the corporate level, for example to ensure compliance with legal regulations, management of security issues such as viruses, communication storage, prevention of sensitive data theft, or avoidance of the risk of remote hacking. File and content-filtering policies can be used as the first line of defense against viruses that propagate via IM clients. Certain filters can be static, such as those that block scripts or executable files. Educate Users Administrators should educate their users on both the benefits and the risks of IM usage, including how to recognize phishing schemes, and the potential impacts if a client is hijacked. These guidelines should be communicated to all employees as part of an updated corporate messaging policy that covers both e-mail and IM usage. Protect IM and File Sharing from Virus Attacks Ensure that enterprise IM solutions and consumer managed solutions are secured from the aforementioned threats. For example, security experts recognize the limitations of relying on desktop antivirus protection alone for protecting e-mail servers, messaging gateways, and collaboration applications. Today, a prudent “defense in-depth” strategy relies on multiple levels of scanning and the use of multiple antivirus engines. Antivirus protection should be enabled so that IT administrators can manage and secure enterprise and public IM communications at the server level. Even organizations that deploy enterprise IM solutions for internal use only should implement security measures to prevent the corporate messaging systems from being used to propagate malicious code or inappropriate content that is introduced through other sources. Centralize Control for Regulatory Compliance and Legal Protection When deploying IM to desktops, organizations should also deploy tools that enable administrators to log messages, scan for inappropriate content, and implement corporate messaging policies from a central server environment. Centralized protection mechanisms enable organizations to manage and control IM traffic. Tools for Secure Instant Messaging Secure, well managed instant messaging requires technology beyond the desktop messaging client. A central messaging server, such as Live Communications Server 2005, provides control and management functionality, while specialized security tools, such as Antigenî for Instant Messaging, deliver antivirus scanning, content filtering, and message content scanning. Together, these technologies create a secure, manageable, collaborative environment. Tight integration between Live Communications Server and Antigen for Instant Messaging enables organizations to apply corporate security policies consistently and to deploy IM solutions without compromising the security of the enterprise environment. Antigen for Instant Messaging Antigen for Instant Messaging is a server-based antivirus solution that provides comprehensive protection for Live Communications Server and its Office Communicator and Windowsî Messenger clients. For organizations that allow use of public IM clients, Antigen for Instant Messaging also integrates with IMlogic IM Manager on a separate server to provide threat protection for other public IM clients. By using layered defenses, corporate content policy enforcement, and optimization of messaging server resources, Antigen for Instant Messaging provides comprehensive protection to ensure that messages and file transfers are secure at all times. Layered Defenses By managing multiple antivirus scan engines to scan all IM and file transfers, Antigen for Instant Messaging minimizes the average window of exposure for emerging threats by providing and managing frequent signature updates from multiple antivirus labs around the world. Layered defenses also protect against downtime; if one engine fails or goes offline to update, other engines remain active to provide protection, ensuring that IM service is not interrupted and user security and compliance are not compromised. Content Control Through administrator-defined content filtering rules, Antigen for Instant Messaging helps enforce compliance with corporate policy for language usage and confidentiality within IM conversations and file transfers. Customizable filters help protect against inadvertent or intentional transmittal of inappropriate content, such as offensive language, legally or ethically questionable material, or confidential company information. Antigen for Instant Messaging includes a set of predefined, customizable keyword dictionaries to target profanity, discriminating language, and spim. Administrators also have the ability to configure file filtering rules that block file types that may contain malicious content (for example, .exe) or expose organizations to legal liability (for example, .mp3). Server Optimization Antigen for Instant Messaging integrates closely with Live Communications Server, optimizing server performance and ensuring that protection does not overtax server resources. With features like in-memory scanning, multi-threaded scanning processes, and performance bias settings, businesses can achieve the benefits of multiple-engine scanning without introducing additional processing time or server performance degradation. Conclusion IM is rapidly becoming a staple in corporate communications, enabling employees to share information and documents in real-time. However, as IM introduces new collaboration capabilities and productivity gains, it also has the potential to introduce new threats to corporate computer security. Because of growing IM use, organizations need to address the security concerns associated with IM-specific malicious code as well as undesirable content. By leveraging best practices and the appropriate technology solutions, today’s organizations can create an enterprise IM system that adds significant business value while enabling consistent policies and threat protection across their networks. Enterprise-class collaboration tools such as Microsoft Office Live Communications Server and Antigen for Instant Messaging provide a high degree of management and security, enabling organizations to adopt these new collaborative technologies with confidence. | ||
| Ê ñïèñêó ñòàòåé | ||