| К списку статей | ||
|
"Presence" in the enterprise network Автор: Venkat Kalkunte, DiVitas Networks Источник: http://www.commsdesign.com/showArticle.jhtml?articleID=183700478&pgno=1 |
||
|
Well beyond the "Presence" all of us think of as IM, Venkat Kalkunte gives us a complete tour of Presence in the enterprise network--where it's been, where it's going, and the standards efforts underway to make sure it gets there. As the pace of business today continues to accelerate, staying connected in the enterprise is becoming increasingly important to meet the challenges of competition. Use of the standard postal service "snail-mail" has long been replaced by email, and businesses relies heavily on email for communications between associates, vendors and customers. Is email sufficient, however, for the rapid response required in today's commercial world? Instant messaging hit the scene just a few years ago and appeared to be a panacea for meeting ad hoc communication needs between company associates and key customers/vendors. The concept of sending text message strings (Instant Message) in a directed manner across the Internet was simple enough, but how to address a message to its intended target and, more importantly, how do I know that they are available to receive and respond to the message? Enter the concept of presence--the ability to identify that someone is there and ready to communicate. Instant Messaging (IM) is embraced by the private user community as a simple way of maintaining contact with friends, family, and co-workers. This revolution in communication happened only because early providers of the applications saw the need for coupling Presence with their application to allow the user community to see if the intended message receiver was on-line or not. Without Presence much of the "Instant" consideration of IM would be lost. 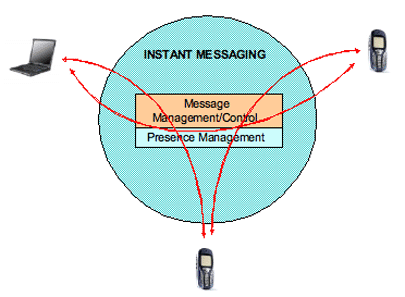 Figure 1. Basic Instant Messaging Architecture As convenient as IM is, there are problems to be addressed before businesses and enterprises can embrace this technology as a standard business tool. Several "hardened" IM applications have emerged to address enterprise security concerns, but to reach its full potential the concept of Presence must evolve to feature a higher level of application integration, tighter security, and broader network access options for the enterprise. This article discusses the state of Presence with respect to current support and future opportunities for the enterprises to capitalize on the evolution of presence and presence-based applications. Presence-centric applications Most of the existing presence architectures were designed to address specific needs of IM applications. As with most emerging technologies, the first offerings were proprietary solutions. Use within the enterprise represented a grass roots adoption without much oversight or control by network management. Application-managed "buddy" lists allowed a user to easily see which "buddies" were on-line and available for message exchanges. However, while presence/IM was used in certain contained communities within an enterprise, general use of this technology posed some corporate challenges:
Based on these problems, some enterprises have delayed adopting presence/IM applications for fear of compromising network security. Despite the inherent value of presence-based communications and applications, if a hole in their overall network security schema is a possibility, enterprises will be hard-pressed to adopt it openly. There is no denying that presence-centric applications bring great value to an enterprise, but this feature must be delivered in a format that meets the enterprise's functional requirements. Through standards created to meet expanding requirements of the enterprise, and through ISV adoption of presence capabilities on a scale beyond simple IM presence, presence-centric applications will be considered by even today's most security-conscious corporations. Presence standards that drive the market The great leveling force in any technology segment is normally delivered by the creation of an industry standard. In the case of Presence, multiple standards were developed that have a specific coupling to IM class applications. The IETF has sponsored and driven two different Presence standards for consideration:
SIMPLE is a functional extension of Session Initiation Protocol (SIP) and is a peer-to-peer architecture with its own inherent presence services defined. IETF RFC 2778 and 2779 specify the architecture and behaviors of a SIP-based IM and presence service whereby SIP User Agents (UA) can publish their presence with an appropriate Presence Server, and other entities ("Watchers") can either retrieve presence information or subscribe to updated presence information for a specific "presentity" (Presence Entity). In most implementations, the SIMPLE system provides a consistent method for establishing peer-to-peer messaging channels; this is analogous to the base SIP architecture. XMPP, as defined, supports a different architecture to provide a similar set of services. The relation with SIP is such that session signaling is accomplished through standard SIP but an XMPP service is responsible for the media management element of the application. Divorcing the session signaling and the application component allows for greater flexibility in a vendor's implementation of these standards. Typically, an XMPP implementation is a client/server architecture vs. peer-to-peer, whereby the server supports many different classes of application services. Implementations of SIMPLE and XMPP are underway and are supported by major industry players. With these standards, new applications are coming to the market providing enhanced IM products with a richer presence infrastructure. So, how is this translated into Presence services with enterprise-specific value-add? How can this be applied to other applications and communications (other than IM) to provide even greater value throughout the enterprise? To achieve maximum value, the total environment for managing Presence must evolve to a high level of feature richness and complexity. Presence in the enterprise for tomorrow For Presence to reach its full potential for value-add in the enterprise, several paradigm shifts must be made in the implementation designs of network-based applications:
Traditionally, Presence was bound to Instant Messaging applications. This must evolve to maximize the utility of Presence. A broader definition of Presence needs to include the following concepts:
The IETF standards body has taken up the challenge of expanding the functionality of Presence services and is working on defining a "Rich Presence Information Data" format (RPID) that expands the concept of presence to include:
Other potential extended RPID parameters could include application or communication modes available to this user and any application specific requirements for these modes. Many enterprise applications could take advantage of Presence information beyond the simple IM. Virtually any real-time class of application (e.g., voice, video, monitoring, etc.) could benefit from having such user-state knowledge. Any user could publish Presence with notification of support for multiple application capabilities, which would enrich the communication and collaboration options available to participating Presence users. 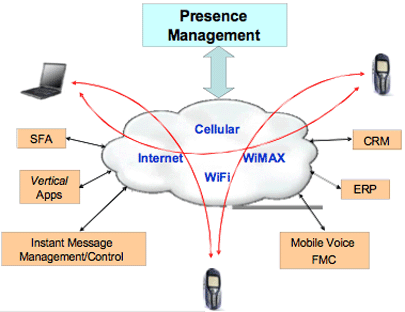 Figure 2. Full Value Presence Capabilities With the evolution of collaborative applications, the need for extended and application-independent Presence services is more important. Far too often, there is a struggle between Presence and true availability that is a result of required job mobility on the part of the presentity. Being away from the desk diminishes the value of Presence information unless those attributes follow the user as they roam through out a facility, campus, or region. The popularity of Fixed/Mobile Convergence (FMC) devices (those with WiFi and cellular service) raises the bar on what is possible through a Presence service. Coupling "mobility" with Presence significantly extends the value realized by the enterprise and the end user. Being able to know that some key contact was available, has an FMC device, and, is capable of a VoIP or cellular phone call enhances the value of a network based Presence capability. Other kinds of presence-driven options are also possible; for example, "rendezvous" calling is a concept whereby an ad hoc conference call may be scheduled and the system monitors the Presence status of all parties and initiates the call when all are available--automatically. The future of Presence in the enterprise What does the future look like for Presence capabilities within an enterprise? The IETF Instant Message and Presence Protocol (IMPP) working group has already defined the Common Profile for Instant Messaging (CPIM) format to provide a bridge to pipe Presence information between different subsystems, such as XMPP and SIMPLE. This kind of interoperability between Presence standards will simplify the deployment decisions of enterprises. To facilitate communication between customers and vendors, new Presence services will evolve where managed levels of Presence information will be published based on the "class" of the Watcher. For example, Presence information available to a company associate might show the location of the presentity, where this would not be appropriate information to expose to a customer or vendor "watcher." More importantly, Presence capabilities must evolve beyond the Internet (IP-based) and include wide-area wireless networks. The marriage of Presence and mobility brings a whole new dimension of value-add to the enterprise and has been acknowledged by the IETF, which recently published a new RFC that would support reporting GPS coordinates or mailing address information as part of the dynamic Presence information. Achieving a Presence "utopia," however, is not without its challenges. Even when all the functional elements are in place major product questions arise as who will implement the network class Presence service? Network infrastructure vendors, OS manufacturer vendors, Independent software vendors? How will such products be integrated into and managed by enterprises? Providing end-to-end Presence solutions will come about through a collaboration of multi-vendor efforts. Server and mobile client OS vendors will develop capabilities to provide key Presence attributes that will be propagated across a multi-network address spaces to a Presence service that will be managed by the enterprise. Since a full-featured Presence capability crosses multiple OSI levels and technology boundaries, such services might expose critical information about an enterprise (people, applications, and customers) and outsourcing (or hosting) such services could jeopardize enterprise network security and application integrity. Final deployment of Presence within the enterprise will be based on extended value-add for key application functions but based on enterprise-centric control capabilities. As Presence evolves to a system or network service and can be accessed across multiple network methods, it becomes a lynch pin of functionality for enabling dynamic and virtually unrestricted communication between individuals within an enterprise and their associated customers and vendors. This is a key consideration, because while person-to-computer access is important, it is that person-to-person communication that really drives business decisions. | ||
| К списку статей | ||