


Nataliya Selina
Faculty: Computer Sciences and Technologies (CST)
Department: Computer Monitoring Systems (CMS)
Speciality: Computer Ecological and Economic Monitoring (CEM)
Theme of Master's Work:
Research of the corporate systems protected efficiency
by visual design means and visual design methods
Scientific supervisor: Ph.D.(in Engineering), associate professor
of the CMS department Nataliya Y.Gubenko


- Autobiography
- Abstract

Abstract
Master's Qualification Work
Research of the corporate systems protected efficiency by visual design means and visual design methods
Topical issue
As we know, the first step in the process of securing corporate computer network an analysis of its security. The solution to this problem involves the collection of large amounts information about the structure, elements and assets of the corporate computer network, which is a complex technical object with a distributed structure, consisting of a legal, organizational, software and hardware levels, currently analysis protection is carried out with the constant participation by network administrators, while used their knowledge of the structure of different levels of the corporate computer network, features the methods and tools of security analysis. Automating analysis security, the relevance of which increases with the number of nodes and the complexity configuration of the corporate computer network is difficult for the following reasons: necessary to develop a model of knowledge representation on the corporate computer network, need to formalize procedures for security analysis, as well as the concept of building system security analysis. [1]
Analysis of the methods and approaches to solving the problem showed that Today, there are several areas of research. You can select work Petrenko S.A., Simonov S.V. to build economically viable systems for security, Melnikova A.Z., on security analysis information systems, Kotenko I.Z. to develop intelligent methods vulnerabilities of the corporate computer network, Vasil'eva V.L., Gorodetsky V.I/, Makarevich O.B., Medvedovsk I.D., Shelupaiova A.A. , design intelligent systems for information security [10].
Formulation of research problems
The main economic effect sought by the company, creating a IPS, is significant reduction of material damage as a result of implementation of any existing threats to information security. At the same time, guided by the statistics various analytical services, we can conclude that the damage this is real and measured in monetary units.
Information security company has a very specific economic meaning. But this goal must be economically justifiable measures. Decide on the financing of projects on information security appropriate only when have confidence that not only increases the expenditure of the budget, and produced investment in the company. In this case the return on such investments must be fully predictable.
That is why the basis of most methods of assessing the effectiveness of investments in information Safety is a comparison of costs required for the establishment of GIS, and the damage that may be caused by the company due to lack of this system [2].
The aim of this work is to improve modeling of security corporate systems.
Solution of the problem and the results of studies
To solve this problem, an analysis of all methods of assessing the appropriateness cost of information security systems. Selection was based on the following
1. The method should provide a quantitative estimate of the cost of safety, using qualitative indicators for assessing the probabilities of events and their consequences;
2. The method should be transparent to the user's perspective, and give opportunity to enter own empirical data;
3. The method should be universal, that is equally applicable to the evaluation of costs acquisition of hardware, specialized and universal software welfare costs of services, expenses for movement of personnel and training of end users, etc.;
4. The method chosen should be able to simulate a situation in which there several countermeasures to prevent certain threats to varying degrees impact on reducing the probability of occurrence.
As a tool for simulation of the processes in the system was chosen Arena firm System Modeling Corporation. Arena allows you to build simulation models, play them and analyze the results of such play.
The whole system is extremely easy to use. The system successfully connected Arena interface capabilities inherent in the Windows environment and Arena ease hierarchical construction model and its successive approximation to the real object.
Review of existing methods
Applied Information Economics (AIE)Methods AIE (company Hubbard Ross) improves the accuracy rate 'True economic value of investments in security technology at the expense of determine return on investment »(Return on Investment, ROI) before and after the investment. Application of AIE can reduce the uncertainty of costs, risks and benefits, including unobvious.
Customer Index (CI)The method proposes to assess the impact of investments in security technology to size and composition of consumers. In assessing the company or organization determines the economic performance of its customers by tracking revenues costs and profits on each customer. The disadvantage of the method is difficulties formalize the process of establishing a direct link between investment in technology safety and preserving or increasing the number of consumers. This method is used mainly to assess the efficiency of corporate information security systems within companies, the which the number of customers directly affects all aspects of business.
Economic Value Added (EVA)Methods EVA (consulting company Stern Stewart and Co.) Proposes to consider the service information security as a "state within a state", ie service professionals security sell their services within the company at rates equivalent to approximately rates in the foreign market that allows companies to track income and expenses associated with safety technologies. Thus, the security service into a profit center and it is possible to clearly identify the disposition of assets related to safety technologies, and increasing incomes of the shareholders.
Economic Value Sourced (EVS)Methods EVS (company META Group Consulting) is based on quantifying return on investment in security technology. The method requires an accurate calculation of all possible risks and benefits for businesses associated with the implementation and operation of corporate system of information protection. It expands the use of such evaluation of IT tools, as economic value added (EVA), Internal Rate of Return (IRR) and return on investment (ROI) by identifying and involvement in the evaluation process parameters of time and risk.
Portfolio Management (PM)The method of portfolio management requires that companies manage their safety technologies as well as managed to equity investment fund based on volume, size, date, profitability and risk of each investment. Asset portfolio security technology consists of "static" (/ equipment, information security, operating systems and application packages software products, networking equipment and software, data and information, provide services, human resources, etc.) and "dynamic" assets (various projects to expand and update the entire portfolio of assets, knowledge and experience, intellectual capital, etc.).
Real Option Valuation (ROV)The methodology is a key concept of constructing a model of "flexibility of the company" in the future. Technique considering security technology as a set of capabilities with a high degree of detail. Correct decision taken after careful analysis of a wide spectrum of indicators and consider the set of results or options future scenarios, which in terms of technique called "dynamic plans for a" management decisions or flexibility, to help organizations better adapt or change their course in information security.
System Life Cycle Analysis (SLCA)The method of the life cycle of artificial systems System Life Cycle Analysis (SLCA), proposed in the Russian business analyst Igor Halkin, is measuring "ideal" corporate information protection system - the ratio of its useful inputs to the amount of harmful factors and factors of reckoning for performing useful functions. Assessment anticipates joint Work analyst and leading experts surveyed companies to develop a roster of useful, and cost of negative factors business systems without the use of security systems and assigning them to certain weights. Result work is to design a model that describes the state without security. After that, the model introduces described factors of the expected changes and calculates the level of development of the company with the corporate system of information protection. Thus, traditional models are being built "as is" and "How to be" taking into account the roster of useful, negative and costly factors of business systems.
Total Cost of Ownership (TCO)TCO was initially designed as a means of calculating the cost of computer skills. But recently due efforts of the company Gartner Group, this technique has become an essential tool for calculating total cost of ownership corporate information security systems. The main purpose of the calculation of CERs is to identify redundant items and score possible return on investment in security technology. Thus, the data on aggregate cost of ownership are used to identify the expenditure part of the corporate information security system. Analysis methods for assessing the effectiveness of investments in corporate information security system shows that only method of total cost of ownership (TCO) in explicit form allows us to calculate the expenditure part of the system security. Also TCO method allows to make the most appropriate economic evaluation of the project. Based on this index, the customer may choose the artist, minimizing the cost of implementation and maintenance of the system or finding "middle ground" between cost and quality Nowadays information systems audit standards Gartner Group is one of the most widely used techniques used to develop recommendations to optimize IT costs
Even a single estimate of the total cost of ownership of IT infrastructure can improve the effectiveness of cost management, thereby increasing the efficiency of the use of IT in the enterprise. If the cost accounting on IT infrastructure by the method of TCO will be held on a regular basis - this will give the opportunity not only to optimize the cost of maintenance and development information systems, but also result in a plan of development of the IT infrastructure to the main business objectives of the company.
There are two most obvious option evaluation. First - a comparison of TCO already implemented similar decisions. The second is based on comparing the TCO solutions offered by different performers or created on the basis of different products. Choice concrete way of assessing always behind the IT manager or project manager. In both cases, should the ability to compare the solutions that are deployed in enterprises in the same industry, which employs the customer project.
The first method allows us to prove the company's management that the proposed solution has the economic indicators are not worse (or better) than the industry average. This approach requires a fairly large amount of statistical material, collected is rather laborious task.
The second method of comparison does not require the amount of necessary statistical material, as in the previous case, except The data may also be obtained from open sources that you can apply this method almost always. Analysis calculation results can be used as an argument or option selection, implementation of information system [6,7,8,9].
Here is an example of calculating TCO. The client proceeded to the choice of artist and stopped while the choice to two companies,specializing in information security. Their reputation in the market about the same. Software, proposed implementing similar and certified. As sources of information used price lists or Offers performers. It is assumed that the project would operate for 10 years without additional modernization.
The initial evaluation of the project TCO to implement with the assistance of the selected artist will be evaluated using only the direct, mandatory spending.
Basically, four possible test result TCO in the context of one-time and annual costs:
1) Ед1 > Ед2, Еж1 > Еж2, customer's choice - Executive 2;
2) Ед1 < Ед2, Еж1 < Еж2, customer's choice - Executive 1;
3) Ед1> Ед2, Еж1 > Еж2, customer choice requires clarification;
4) Ед1< Ед2, Еж1 < Еж2, customer choice requires clarification.
where Eдn - one-time costs incurred by the client in bringing the perpetrators n;
Ежn – annual costs incurred by the client in bringing the perpetrators n.
Obviously, the first two options calculation TSB unambiguous and additional refinements to select the Executive does not required.
Let us consider the third and fourth options. Since options are symmetric with respect artists, consider One of them, namely the third. The results of the calculation (or submitted by the perpetrator or perpetrators) are shown in Figure 1.
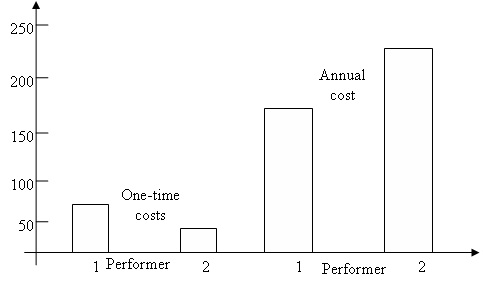
Figure 1 - The results of the calculation
Apparently, one-time cost of the project with an artist uses of products will exceed the one-time cost of the project using the products Executive 2 (primarily due to higher cost software). However, for the entire term of operation of the project TCO project involving an artist will be lower than the TCO of the project involving 2 of the Executive during the same period. This is significant excess of annual expenditures, primarily due to the high cost of software maintenance Executive 2. This situation requires an additional determination of the coefficient of comparing costs. In this example, it will be about two years, ie by the end of the second year of operation of the project the client may suffer the same cost, no matter from Artists he has chosen. But, as mentioned above, the intended duration of the operation of the project - 10 years. Consequently, during the eight years the client will bear more costs if the project will involve the Executive 2. Naturally, the customer is not profitable, and its choice should fall on the Executive 1 [6].
Also, the presented situation and the analysis result shows that if the client only compare price lists without calculating the TCO in the long term, the producer prices in February would have seemed to him much more attractive than the price of the Executive 1.
Findings
At this stage the work was to examine existing methods for evaluating the effectiveness of investments in information bezopasnsnost,select the most suitable method for the selected criteria and is working to develop a model for this method using Arena simulation system (Figure 2).

Figure 2 - Example simulation in Arena (a picture is animated; the amount of cycles of reiteration = 2; volume = 42,7 Кb; size - 651x245; number of shots - 4; delay between shots - 150ms; delay between the last and first - no; number of repetition cycles - infinitely)
References
- Петренко С. Оценка затрат компании на информационную безопасность. // Институт информационной безопасности. – 2003. [Electronic resource]. URL:www.bre.ru/security/18881.html
- Чикалёв И. Во что обходится информационная безопасность. // БДМ. Банки и деловой мир. – 2006. [Electronic resource]. URL: www.bdm.ru/arhiv/2006/07/60.htm
- Ремизова О. Управление непрерывностью вашего бизнеса. // БДМ. Банки и деловой мир. – 2004. [Electronic resource]. URL: http:www.outsourcing.ru/content/rus/147/1474-article.asp
- Давлетханов М. Оценка затрат компании на ИБ. // Компьютерная библиотека GetInfo.Ru. – 2004. [Electronic resource]. URL: http://www.getinfo.ru/article682.html
- Дворчук О. Показатели экономической эффективности ИТ- проектов [Electronic resource]. URL:http://www.security.ase.md/publ/ru/pubru107/Dvorciuk_O.pdf
- Филиппова И. Выбор по расчету. Расчет совокупной стоимости владения проектов по обеспечению информационной безопасности. [Electronic resource]. URL: http://www.elvis.msk.su/files/TCO.pdf
- Соколова А.А., Филиппова И. ТСО - цена вопроса [Electronic resource]. URL: http://www.elvis/msk.su/files/TCO_common.pdf
- Соколова А.А./Филлипова И. Информационная безопасность+ТСО=? [Electronic resource]. URL: http://www.elvis.msk.su/files/TCO_new.pdf.
- СоколоваА.А./ Филлипова И. ТСО: метод один, а использовать можно по-разному [Electronic resource]. URL:http://www.elvis.msk.su/files/TCO_supplier
- Бакиров Т.Г. Автоматизированная система анализа защищенности корпоративной вычислительной сети на основе многоантенного подхода [Electronic resource]. URL:http://www.lib.ua-ru.net/diss/cont/169843.html
Remark of material significance
The abstract of the Master's work is not complete yet . The final completion in 1st December 2010. Full text of the work and materials on the topic can be obtained from the author or his head after that date.


- Autobiography
- Abstract
