Anastasya Tsymbalova
Faculty: Computer Science and Technology
Theme of master's work:
Development of the model of use and distribution of resources for information security
Scientific adviser:Natalia Gubenko
Abstract
Master's Qualification Work
"Development of the model of use and distribution of resources for information security "
Contents
- Topicality and motivation
- Aims and objectives
- Scientific innovation
- Review of research and development on the topic
- General model of information security
- The model of resources distribution
- The model of resources use
- Analysis of the model of resources use
- Expected practical results
- References
Topicality and motivation
Effective Information Security Effective Information Security is one of the most important contemporary problems since the information resource became one of the major thrusts of economic development in the modern world. Application of high information technologies of the XXI century, on the one hand, gives considerable advantages in activities of enterprises and organizations, and on the other hand - potentially creates conditions for theft, loss, distortion, falsification, destruction, copying, and blocking of the information and as a consequence, application of economic, social or other kinds of damage. Therefore, the problem of information protection and finding ways to reduce damage is becoming more and more acute every year[1].
<Some of the main elements of the scientific and methodological basis for information protection are the models of information protection processes. One of the issues that arise in solving the problem of constructing the model of the protection system is resources and their optimal distribution assessment. [2].
Aims and objectives
The main aim of master's work is development the model of use and distribution of resources allocated for information protection and practical application of this model in the company to prove its efficiency and expediency.
The object of the research is a model of the use and distribution resources allocated for information protection.
In accordance with the stated aim and object of the research the following objectives are pointed out:
- overview and analysis of existing models of information security;
- analysis of the model of use and distribution of resources for information protection, systems analysis, determination of its strengths and weaknesses;
- development and improvement of the model of use and distribution of resources;
- testing of the developed model in the company to prove its efficiency and get practical results;
- overview of research and developments
Scientific novelty
Scientific novelty of the master's work is to systematize the existing approaches for constructing models of use and distribution of resources, to create an improved model based on the chosen method and to test these models in the company, to determine advantages and disadvantages of this models.
Review of research and developments on the topic
Because of the great importance of information safety and especially systems which ensure its security reserach in this area requires further development and not lose its actuality. In Ukraine we can find the work of Domareva V.V. on the development of information security systems with complete openness of modern information technology, Grezdova G.G. on the formation of cost-effective integrated system of information security, Petrenko S.A., Simonov S.V. on making economically grounded information security systems and many others [1].
Let us dwell on the consideration of the model of use and distribution of resources allocated for information protection offered by Grezdov G.G. as mathematical modeling methods used in constructing of the model are of great help in making an effective information security system [8].
The general model of information security
Scientific novelty of the master's work is to systematize the existing approaches for constructing models of use and distribution of resources, to create an improved model based on the chosen method and to test these models in the company, to deterine advantages and disadvantages of this models [4].
In general, the process model of information security in an IS can be represented as shown in Fig. 1.
Figure 1 - The general model of information security
The process of information protection should also be considered as a process of distribution of resources allocated for information protection.
Optimal choice of resources of information protection is a daunting task, that in the future will be solved by creating an improved model of the use and distribution of resources [9].
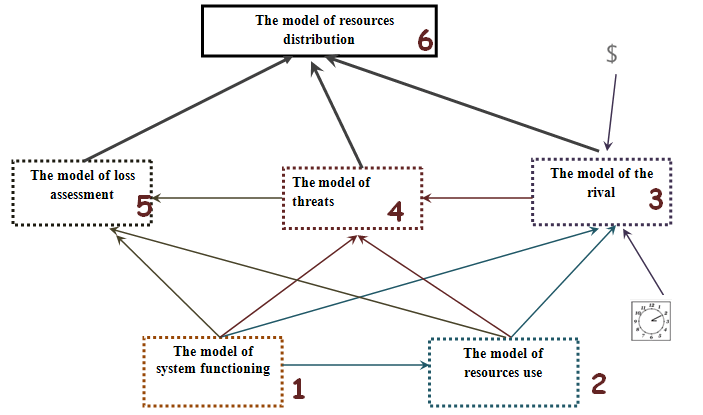
The model of resources distribution
Figure 1 shows a step by step process of making a model [9].
Figure 2 - general model of choice of resources of information protection
The Model of resources distribution is based on the capabilities of the rival and the defender, on the basis of model of threats and also on the model of loss assessment [9,10].
The Model of resources distribution can be described formally. It includes:
- a set of information threats;
- a set of quantitative estimates of losses in case of successful realization of information threats;
- a set of quantitative estimates of system losses in case of application of information protection;
- a set of resources for the implementation of the destructive actions;
- a set of offenders;
- a set of resources of information protection;
- available time to the attacking side for implementation of threats;
- financial funds that available to the rival.
Let us dwell on the consideration of the model of resources use, because this model is part of a general model of choice of resources for information protection (see Figure 2). The results of making this model are important for constructing the model of adversary, the model of threats, the model of loss assessment and the model of resources distribution [4,9].
The model of resources use
Information, hardware and software, staff and premises with the nodes of functioning system are the resources of the system [4,9].
Information is the main resource. Information which is placed on the nodes of functioning system can be described as coming for processing, adopted for the processing and is sent for output. To construct the model of information use you need to know what information and in what form is located in the system [1,11].
The Model of information use can be represented as follows:
- MI - the model of information system use;
- k - the number of nodes of the functioning system;
- MIj - the model of using of system information for the j-th node of the functioning system [9].
The following resource is hardware which includes:
- server and users workstations,
- data transmission system,
- data transmission system [1,11].
The Model of the use of hardware system can be represented as follows::
- AO - the model of hardware use;
- N - the amount of hardware in the system;
- AOi - the model of using the i-th system hardware [9].
The following resource is premises which includes the power supply system, water supply, telephone lines, etc [1,11].
The model of the premises use can be represented as follows
- P - the model of using premises
- M - the number of premises in the system
- Pi - the model of using of the i-th system premises [9].
The following resource is users or staff , people who support the functioning:
- System programmers
- Service provider stuff
- Administrators databases
- managers and operators AU
- Administration
- users
- information security Service [4]
The model of describing users of the system can be represented as follows:
- U - the model of describing users ;
- L - the number of users in the system;
- Ui - the model of describing the i-th system users [9].
Figure 2 shows schematically the interaction of the models described above.
Figure 2 - The interaction of the models described above
(a picture is animated; volume = 25,7 Кb; size - 620х505; number of shots - 9; delay between shots - 80 ms; delay between the last and first - 100 ms; number of repetition cycles - infinitely)Analysis of the model of resources use
As the analysis shows from the perspective of a systems approach, the model of using resources is effective for the formation of an integrated, planned, purposeful, active and reliable information security system. In this model we can see a clear interaction between each of the considered system resources, but the main thing in coordination of information security is the completion and distribution of these resources [13].
the strengths of the Model
- the model of the hardware use includes information such as its placement, the use of software and information, user access to this hardware.
- the model of the premises use includes information as the overlap of the premises, their systems of functioning, hardware and information, as well as and users who have access to these premises.
- the model of describing users includes information such as a set of premises and hardware, that users can access depending on their role [1].
the weaknesses of the model
- to construct the model of information use we must take into account the degree of information importance (very high, high, medium, low), volume of information (very large, large, medium, small), intensity of processing (very high, high, medium, low) [4].
- to construct models of describing users it is also necessary to take into account the degree of importance of information and access to it depending on user roles.
Since users are the main source of threat in the enterprise, it is expected to create an improved model, that is, to a set of users and roles we should add a lot of authorities to access objects and users connections with the system.
- as for the hardware, one should clearly develop a policy of tracking outdated hardware and the introduction of new, as well as the reflection of these innovations in the model [1].
Expected practical results
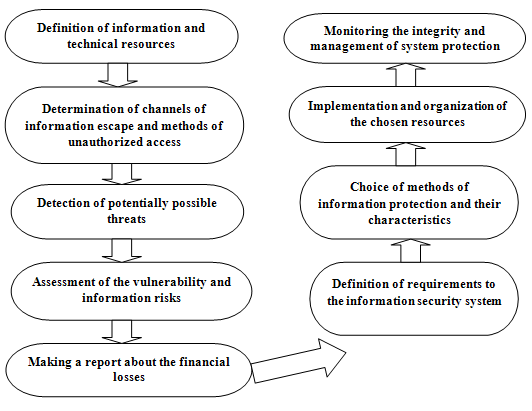
The analysis of existing methods and technique allowed to determine a step by step process of the development of the model of use and distribution of resources for businesses, where this model will be tested. It is presented in Figure 3.
Figure 3 - Step by Step process of the development of the model of use and distribution of resources
- References
- 1. Цымбалова А.А, Губенко Н.Е.Анализ модели использования ресурсов с точки зрения информационной безопасности. Информационные управляющие системы и компьютерный мониторинг — 2011 / Материали II всеукраинской научно-технической конференции студентов, аспирантов и молодых учёных. — Донецк, ДонНТУ — 2011, с. 292-295.
- 2.Корнеев Д.В. Обобщенная модель системы защиты ресурсов распределения вычислительной сети [Electronic resource]: http://admin.smolensk.ru/virtual/expo/html/tesis.htm
- 3. Химка С.С. Разработка моделей и методов для создания системы информационной безопасности корпоративной сети предприятия с учетом различных критериев /Химка С.С. Автореферат [Electronic resource]: http://masters.donntu.ru/2009/fvti/khimka/diss/index.htm
- 4.Домарев В.В. Безопасность информационных технологий. - :ТИД Диа Софт, 2002 - с. 688
- 5. Official ISACA site [Electronic resource]: http://www.isaca.org.
- 6. Official ISACA site. The Business Model for Information Security [Electronic resource]: http://www.isaca.org/Knowledge-Center/BMIS/Pages/Business-Model-for-Information-Security.aspx
- 7. Nina Dobrinkova. Information Security – Bell-La Padula Model [Electronic resource]: http://www.iit.bas.bg/PECR/62/53-59.pdf
- 8.Табаков А.Б. Разработка моделей оптимизации средств защиты информации для оценки страхования информационных рисков [Electronic resource]:http://ej.kubagro.ru/2005/04/02/
- 9. Грездов Г. Г. Способ решения задачи формирования комплексной системы защиты информации для автоматизированных систем 1 и 2 класса [Текст] / Г. Г. Грездов // ( Препринт/ НАН Украины. Отделение гибридных управляющих систем в энергетике ИПМЭ им. Г. П. Пухова НАН Украины; № 01/2005) – Киев : ЧП Нестреровой, 2005. – С. 66.
- 10 Трифаленков Илья, Макоев Владимир. Критерии выбора средств защиты информации [Electronic resource]: http://www.jetinfosoft.ru/download/public/cio_06_02_y.pdf
- 11.Малюк А.А., Пазизин С.В, Погожин С.С. Введение в защиту информации в автоматизированных системах. [Текст] – М.: Горячая линия - Телеком, 2001. – C 148 .
- 12.Гусев М.О.Открытые информационные системы и защита информации [Electronic resource]: http://jre.cplire.ru/jre/sep05/1/text.html
- 13.Малюк А.А. Информационная безопасность: концептуальные и методологические основы защиты информации. Учебное пособие для вузов. [Текст] – М.: Горячая линия - Телеком, 2004. – C 280.
Remark of material significance
By the time of writing of the abstract Graduate work is not completed yet. Final results were obtained in December 2011. You can take full text of the research from the author or supervisor after this date.
@ 2011 Anastasya Tsymbalova DonNTU


 RUS
RUS  UKR
UKR  ENG
ENG