Abstract
- Introduction
- 1. Theme urgency
- 2. Goal and tasks of the research
- 3. The use of wireless technologies in the mine
- Conclusion
- References
Introduction
The risk of mining operations is well known. The reasons for those special hazards are work conditions which are specific for the industry, such as:
- pressure of rocks on the roof and walls of mines, constantly threatening with collapse,
- poisonous and explosive gases and dust
- accumulation of water inside the rock above the mine and its breaking into the current work sites,
- vertical or steeply inclined routs to the work sites, that must be used by the most of miners on a daily basis
- poor lighting, and in some cases, poor ventilation, high temperatures and humidity and the constant heavy rain and spray jets of water from the roof and walls of excavations.
All this creates a number of very serious, mostly natural hazards to life and health of miners, who must not only bear the risk of industrial workers in general (injuries by tools, mechanisms, machines, wiring, falling heavy objects, burns, steam, etc.), but also are exposed to many hazards specific to the mining industry.
Accident
statistics in the industry shows that the risk of death for a
miner is at least 4 times higher than for a metalworker. Another danger
of the
underground mining operations is that risk of massive, catastrophic
accidents is
much higher than in any other industry. Gas and dust explosions, fires
and
sudden release of gases are considered especially dangerous in terms of
their
consequences.
1. Theme urgency
This theme is important, since the security of miners is an issue of
a great importance for the world as well as for our region, where
miming is the core business. The industrial potential of Donetsk is the
second in the volume of industrial production (after Mariupol) and the
first in terms of growth. There are 94 mining companies registered in
Donetsk, which (combined with the city of Makeyevka) make it a major
industrial hub.
At present the coal industry is one of the strategic
for Ukraine due to the fact that the huge portion of coal supply to the
Ukrainian power generation and coke plants is domestic. Therefore, the
welfare of coal miners is an important part of Ukraine's energy
security, and export potential of metal manufacture, as up to 40%
of the total foreign exchange earnings in the country come from the
exports of steel products.
Unreasonable privatization and the lack of funding
for the modernization of mining enterprises can have a negative impact
on the economy of the entire country.
The coal industry of Ukraine is leading in terms of injuries and
fatalities in the workplace. According to official statistics it takes
the lives of two miners to produced one million tons of coal in Ukraine
(for comparison: 0.03 in the U.S., 1.1 in Russia [1]). This is due to
dangerous working conditions in the mines, as well as old and dusty,
outdated equipment. And today we need to pay particular attention to
the safety of miners.
2. Goal and tasks of the research
The aim is to develop an automated monitoring system and search for miners in the shaft, corresponding to the Safety Rules in Coal Mines. [2].
To achieve this goal it is necessary to solve the following tasks:
- to investigate and analyze existing methods and tools for miners in the mine;
- to analyze the existing systems of surveillance and searching for workers in the mine;
- to create a framework and an algorithm of automated systems of surveillance and searching for workers in the mine;
- to select a range of hardware and technical resources for the implementation of the developed system.
In this paper we carried out a review and analysis of existing systems.
Research object: process of finding and monitoring the miners in the mine.
Research
subject: automation of
search and surveillance of miners.
3. The use of wireless technologies in the mine
An analysis of modern security systems in the mine discovered the general structure of the security system in the mine similar to that shown in Figure 1.
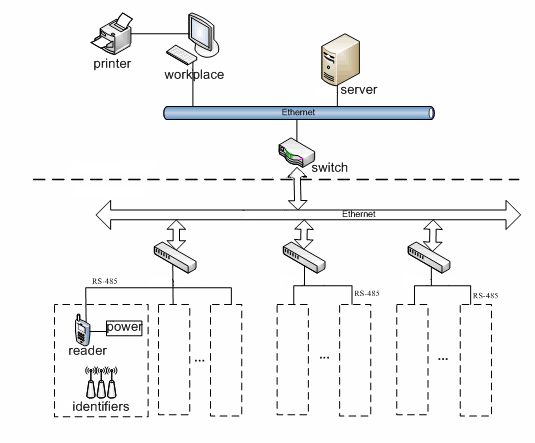
Figure 1 – The structure of the monitoring system and search for miners in the mine.
As you can see, the basic elements of modern systems are:
- Readers;
- ID Tags - unique for each miner;
- Data transmission system - switches, network;
-
Surface complex - workstations controllers, servers, storage of
information.The
system works as follows: a unique ID tag is built in the light of every
worker; readers are installed in various places throughout the mine,
depending
on the topology of these ID tags. When a miner reaches the monitored
area, the
reader catches the signal of the ID tag and sends the data to the
control room
through the network. It helps with time attendance control and the
location of
the miners. Also, in case of emergency, rescuers are provided with
current
information on the whereabouts of the miners remaining in the mine. But
the problem
of contacting and searching the miners behind the obstruction remains
unsolved.
Let us consider the abovementioned identifiers and its use in the system, so-called RFID tag (Radio-Frequency Identifier). Its advantages are non-contact work; work in out of side areas, sufficiently large data storage capacity, ability to read multiple tags, and durability. All these benefits are certainly there, but the following disadvantages of RFID tags make their application in mining conditions impossible: - Low performance in the presence of radiopaque and radio-absorbent materials, which often depends in the frequency. The technology in its present state does not work with such materials, and in some cases fails completely;
- Exposure to environmental factors. Environmental conditions can have a negative impact on the RFID-solutions. If the operating environment contains a large amount of metal, liquids, etc. this may affect the accuracy of reading labels, depending on frequency;
- The impact of noise from the equipment. Improper installation of equipment may adversely affect the RFID-solution (e.g. the location and orientation of the antenna);
- Limited penetration of energy waves. Although RFID does not require line of sight, there is a limit of penetration of the energy of radio waves, even in the radioparent objects [3-4].
To date, ZigBee (operating frequency 2.4 GHz) is a promising replacement of RFID technology. It surpasses RFID in the following criteria: low power consumption and noise immunity. ZigBee technology also has the following advantages:
- Spatial scalability - the number of nodes in the network can be increased to thousands, and more;
- Functional scalability - a network can be used in many control systems at the same time and the number and variety can be easily changed without changing the software and reconfiguring the router and the network coordinator;
- Ease of installation and setting up - end network devices notify about their services and capability and find a coordinating device with which they must work to fulfill the targets of the management;
- Ease of monitoring the network and optimizing its structure by means of special methods of administration;
- Network survivability solves the problems of the loss of communication with the network nodes and rebuilds by re-structuring and re-routing. A parallel coordination can be easily set up in case of the loss of connection with the main coordinator;
- Addressing the quality of communication - additional routers can be installed in order to improve the quality of communication;
- High information security - cryptographic protection at three levels of the stack and authentication of network nodes;
- Implementing of individual protocols and integration of technology-based services are also supported by ZigBee [5].
ZigBee technology is not designed to transfer large amounts of information. However, transmission of sensor readings, the volume of which rarely exceeds tens of bytes, does not require high speed, in this case low energy consumption, cost and high reliability are required[6].
Another feature that makes ZigBee different from other technologies in the modern positioning systems is that it does not distinguish devices as readers, identifiers, and the search device. All of these devices will be replaced with ZigBee modules with different specification:
- Portable - unique identifiers worn by miners;
- Fixed - readers of information;
-
Special – used by rescue services.
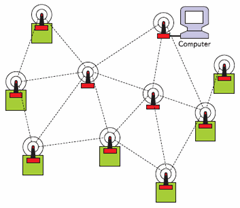
Figure 2 – Topology Mesh Network
All of these devices will make up a single network of devices that are capable of exchanging information among themselves. Due to the fact that ZigBee technology supports not only simple wireless topology ("Point to Point", "star"), but also a complex mesh topology Mesh (see Figure 2).
Data are transferred from node to node until they reach the final
destination. There are various ways of passing data, which increases
network availability in case of failure of one of the links.
Conclusion
Analysis of existing systems surveying miners under the debris showed that the modern systems theoretically solve the problems of Safety Rules in Coal Mines, but in reality they have several disadvantages.
In this regard, it is proposed to develop an automated system of monitoring and searching for miners in the mine on the basis of existing principles and structure of the system, but using the technology of ZigBee.
Thus, the new system would have several advantages over previous analogues:
- Accuracy of positioning due to the fact that these devices are not affected by the environment, as opposed to RFID;
- There is a feature of bilateral relationship between the warning and miners;
- The possibility of finding a miner in the case of an emergency.
References
1. Аварии на шахтах Украины в 2007-2010 годах. Справка [Электронный ресурс]/ РИА Новости – Режим доступа: http://www.rian.ru/spravka/20100613/245849728.html
2. Про затвердження Правил безпеки у вугільних шахтах: Закон Украіни від 07.09.2011 N 960 // Офіційний вісник України. – 2011. – № 62 – Режим доступу: http://zakon2.rada.gov.ua/laws/show/z0327-05
3. Финкенцеллер, Клаус. RFID-технологии. Справочное пособие / К. Финкенцеллер; пер. с нем. Сойунханова Н.М. — М. : Додэка-XXI, 2010. — 496 с.: ил. — Доп. тит. л. нем. — ISBN 978-5-94120-232
4. Преимущества и ограничения RFID технологии [Электронный ресурс]. Режим доступа:http://www.itproject.ru
5. Краткий теоретический курс по технологии беспроводных сетей ZigBee [Электронный ресурс]. Режим доступа: http://indemsys.ru
6. Панфилов Дмитрий. Введение в беспроводную технологию ZigBee стандарта 802.15.4/ Панфилов Дмитрий, Соколов Михаил//Электронные компоненты – 2004 – 12. С. 75.
This
master's work is not completed yet. Final completion: December 2012.
The full text of the work and materials on the topic can be obtained
from the
author or his head after this date.
