Abstract
When writing this essay master's work is not yet completed. Final Completion: June 2019. The full text of the work and materials on the topic can be obtained from the author or his manager after the specified date.
Content
- Introduction
- 1. Network Architecture Analysis
- 1.1. Client-server architecture
- 1.2. Selection of network architecture
- 2. Analysis of the necessary equipment
- 3. Protocols used by routers on the network
- 3.1 Classification
- 4. Performance analysis
- Conclusion
- References
Introduction
The process of automating industrial production is developing at an ever-accelerating pace: the number of “intelligent” terminal devices is increasing, the number of microcontroller-based computing systems involved in the process control and process management is growing. Under these conditions, the role of data collected at all levels of the process control system significantly increases. The requirements imposed by consumers of this information are becoming increasingly stringent in terms of the volume, speed and reliability of receiving data, therefore the issues of ensuring communications become a high priority. For many years, data exchange systems were built according to the traditional centralized scheme, in which there was one powerful computing device and a huge number of cables through which terminal devices (sensors and actuators) were connected. Such a structure was dictated by the high price of electronic computing equipment and the relatively low level of production automation.To date, this approach has almost no followers. Such disadvantages of centralized process control systems, such as the high costs of cable networks and auxiliary equipment, complex installation, low reliability and complex reconfiguration, made them in many cases absolutely unacceptable both economically and technologically. Under the conditions of rapidly growing production of microprocessor devices, digital industrial networks (DSP) have become an alternative solution, consisting of many nodes, the exchange between which is done digitally. Today, there are about a hundred of different types of DSPs used in automation systems on the market. The technical and cost differences of these systems are so great that the choice of a solution that is optimally suitable for the needs of a particular production is not an easy task. The purpose of this article is to help end users and designers of distributed process control systems to take a reasoned decision that can increase production efficiency and ensure reliable operation of process equipment [7].
1. Network Architecture Analysis
A network architecture is a combination of topologies, media access methods and protocols necessary to create a workable network. Computing Network - It is a complex set of interconnected and consistently functioning hardware and software components. Hardware components of the local network are computers and various communication equipment (cable systems, hubs, etc.). Software components are operating systems and network applications. Network layout is the process of building hardware components in order to achieve the desired result. The network can be built according to one of three schemes:
- A peer-based network is a peer-to-peer network;
- network based on clients and servers - a network with dedicated servers;
- The network that includes nodes of all types is a hybrid network.
Each of these schemes has its advantages and disadvantages, which determine their areas of application. [5]. Peer-to-peer LANs are the easiest and cheapest type of network to install. When connecting computers, users can share resources and information. Peer-to-peer networks have the following advantages:
- they are easy to install and configure;
- Individual PCs do not depend on a dedicated server;
- users are able to control their resources;
- low cost and easy operation;
- minimum hardware and software;
- there is no need for an administrator;
- well suited for networks with no more than ten users.
A peer-to-peer architecture problem is when computers are disconnected from the network. In these cases, the types of services that they provided disappear from the network. Network security can be applied to only one resource at a time, and the user must remember as many passwords as network resources [3]. When accessing a shared resource, there is a drop in computer performance.

Figure 1. Ethernet's productivity
СA major disadvantage of peer-to-peer networks is the lack of centralized administration. The use of a peer-to-peer architecture does not preclude the use of a terminal-host architecture or a client-server architecture on the same network [11].
1.1 Client-server architecture
Client-Server Architecture is the concept of an information network in which most of its resources are concentrated in servers serving their clients. The architecture under consideration defines two types of components: servers and clients.
A server is an object that provides services to other network objects upon their requests. Service is a customer service process. The server works according to the tasks of the clients and controls the execution of their tasks. After completing each task, the server sends the results to the client who sent the task. The service function in the client-server architecture is described by a set of application programs, according to which various application processes are performed [1].
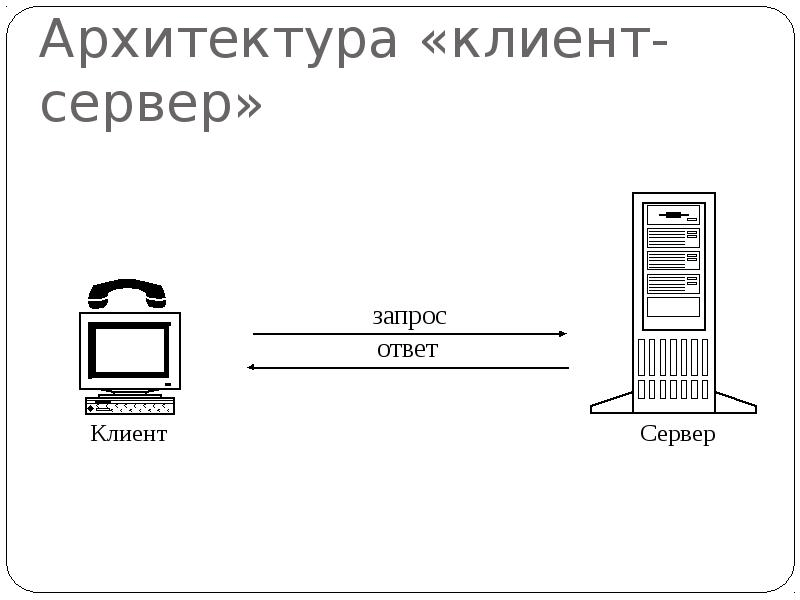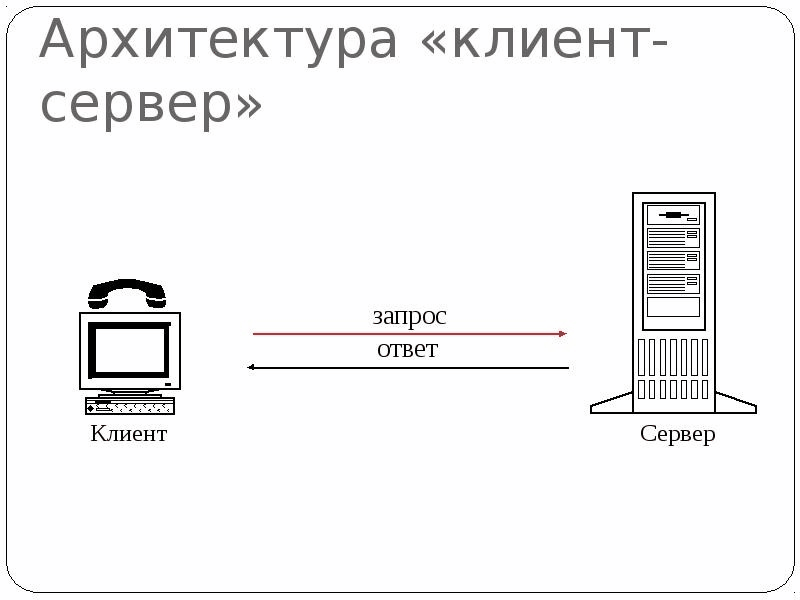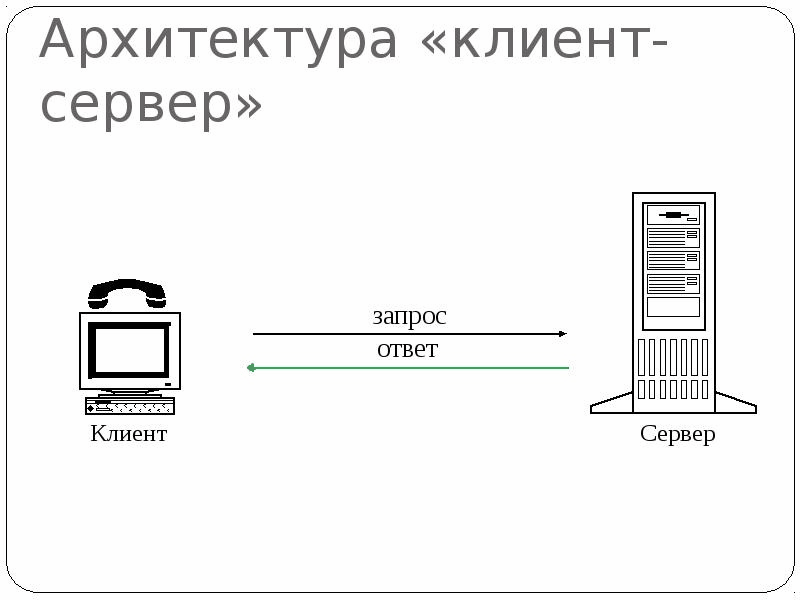
Figure 2. Client-server architecture
The process that calls a service function using certain operations is called a client. It can be a program or user. The figure shows a list of services in the client-server architecture. Clients are workstations that use server resources and provide convenient user interfaces. User interfaces are procedures for user interaction with the system or network. In networks with a dedicated file server, a server network operating system is installed on a dedicated standalone PC. This PC becomes a server. The software installed on the workstation allows it to communicate with the server. The most common network operating systems are:
- Novel NetWare;
- Microsoft Windows NT;
- UNIX from AT & T;
- Linux.
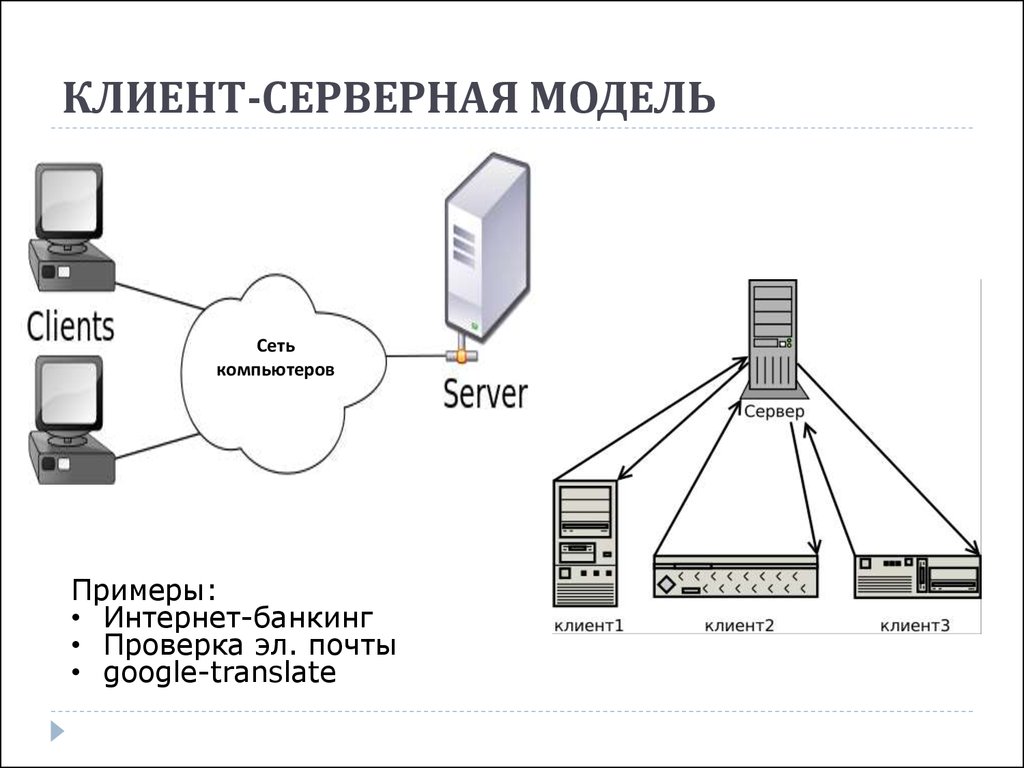
Figure 3. Client-server model
The range of tasks that servers perform in hierarchical networks is diverse and complex. To adapt to the growing needs of users, servers in the LAN became specialized. For example, in the Windows NT Server operating system there are various types of servers: The client initiates and uses email or other server services. In this process, the client requests a service type, establishes a session, gets the results he needs and reports the end of work. Server-based networks have better performance and increased reliability [2]. The server owns the main network resources accessed by other workstations. In modern client-server architecture, there are four groups of objects: clients, servers, data, and network services. Clients are located in systems at users' workstations. The data is mainly stored in servers. Network services are shared servers and data. In addition, services manage data processing procedures. Client-server architecture networks have the following advantages:
- allow you to organize networks with a large number of workstations;
- Provide centralized management of user accounts, security, and access, which simplifies network administration;
- effective access to network resources;
- a user needs one password to log on to the network and to gain access to all resources covered by user rights.
- server malfunction may make the network inoperable;
- require qualified personnel to administer;
- Have a higher cost of networking and networking equipment.
1.2 Selection of network architecture
The choice of network architecture depends on the purpose of the network, the number of workstations and the actions performed on it. Choose a peer-to-peer network if:
- the number of users does not exceed ten;
- all cars are close to each other;
- there is a small financial capacity;
- There is no need for a specialized server, such as a database server, fax server or some other;
- There is no possibility or need for centralized administration.
- the number of users exceeds ten;
- Requires centralized management, security, resource management or backup;
- a dedicated server is required;
- need access to the global network;
- is required to share resources at the user level.
2. Analysis of the necessary equipment
The Cisco 3600 series is designed to support a growing number of remote offices and offices that need access to a corporate network or the Internet. This series of access servers offers an unprecedented level of support for various remote access technologies, including voice and fax transmission over TCP / IP networks.
The most common is exactly Cisco products, according to the results for 2018, we can see the following distribution [10]:
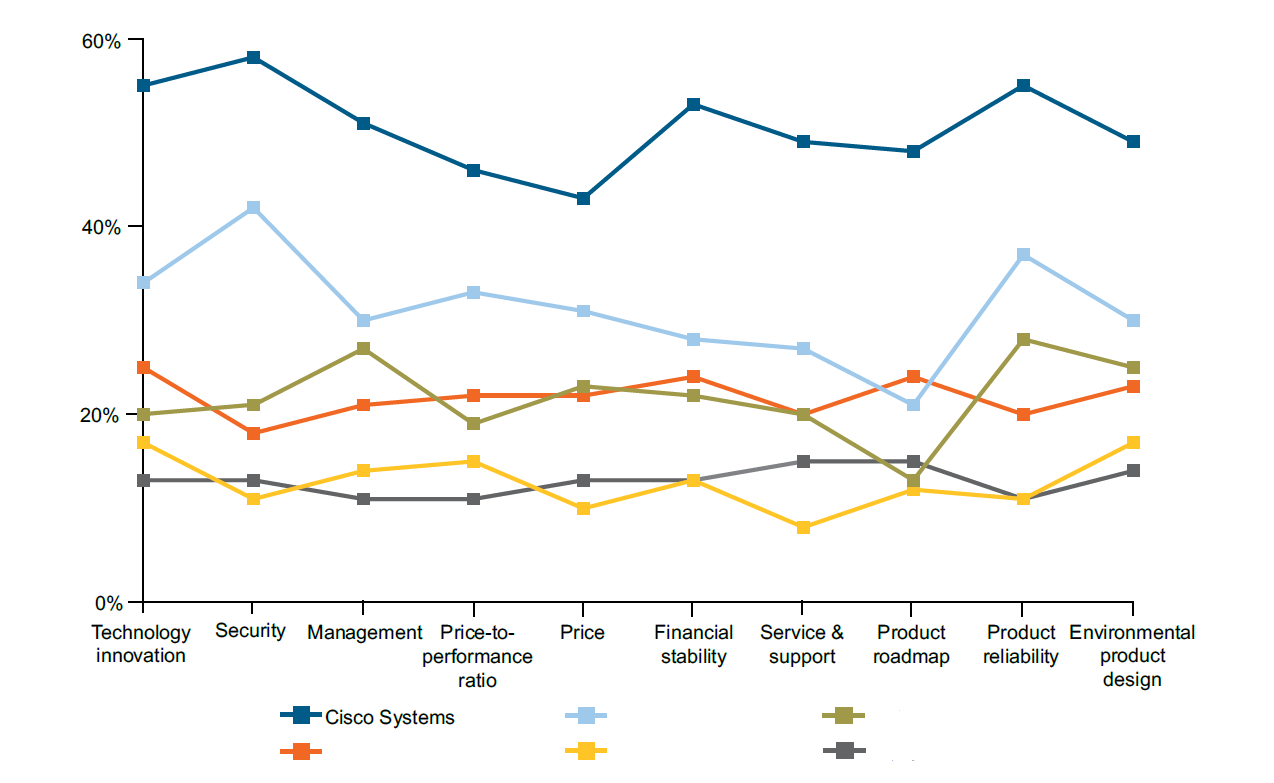
Figure 4. Distribution of equipment relative to manufacturers
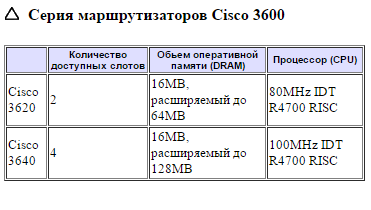
Figure 5. Cisco Router Information
- Main features
- Support for all Cisco IOSTM software features
- Modular architecture
- It supports both voice over IP and voice over Frame Relay (FRF.11 and FRF.12 standards)
- A wide range of functions within a single device
- Simple and flexible method of replacing software using flash memory
- Optional fail-safe power supply
- ConfigMaker software for Win95 and NT 4.0 for network design and simplified configuration
- LAN modules
- 1 10BaseT Ethernet port
- 1 port 100TX Fast Ethernet
- 4 10BaseT Ethernet ports
- WAN Modules
- 8 or 16 analog modems (with support for V.34 + protocol, maximum transfer rate up to 33.6 Kb / s)
- Digital modem module (up to 30 modems per expansion slot, maximum transfer rate up to 56Kb / s with V.90 protocol support)
- 16 or 32 asynchronous ports
- 4 synchronous serial ports
- 1 or 2 channels structured (channelized) T1 / E1 ISDN PRI
- 4 or 8 ISDN BRI ports
- 4 or 8 synchronous / asynchronous low-speed serial ports
- 1 ATM port 25 Mb / s
- 1 ATM port 155Mb / s (OC-3) using single-mode or multimode fiber-optic cable (CLIP, LANE, 1483 technologies are supported)
- 4/8 ports of ATM E1 IMA (inverse multiplexing over ATM network)
- 1 high speed serial interface (HSSI) port
- Hardware data compression module
- Voice and fax module with ISDN BRI, FXS, FXO and E & M interfaces (up to 4 voice ports per slot)
- Mixed network modules
- 1 10 / 100BaseTX Ethernet port, 1 T1 / E1 ISDN PRI port
- 1 10 / 100BaseTX Ethernet port, 2 T1 / E1 ISDN PRI ports
- 1 Token Ring port, 1 Ethernet port and 2 empty slots for single-port modules
- 1 Ethernet port and 2 empty slots for single port modules
- 2 Ethernet port and 2 empty slots for single port modules
- The main advantages
- Support for a wide range of protocols
The Cisco 3600 Series with Cisco IOSTM software offers support for all widely used network protocols such as IP, Novell IPX and AppleTalk, as well as a wide range of routing protocols.
- Unsurpassed bandwidth optimization
Cisco 3600 routers offer more options for optimizing bandwidth and, accordingly, its cost, than routers of any other network equipment manufacturers. Data compression and numerous methods for prioritizing data flow guarantee the delivery of important data, while at the same time such features as protocol spoofing, “instant” routing, bandwidth allocation on demand, connection establishment on demand, etc. guarantee minimization of the cost of the compound used.
- Expanded support for multimedia and virtual networks
The ability to use 3600 series devices as medium density remote access servers with installation of 6 to 60 digital modems or 8 to 48 analog modems that support protocols such as V.34 + and V.90. Technologies such as IGMP, RSVP, PIM, WFQ, ISL (InterSwitch Link), 802.1Q allow the Cisco 3600 series to provide service for video and audio applications, as well as support for virtual networks. None of the competing companies offer similar technologies. The presence of voice modules enables voice (telephony) and fax transmissions via TCP / IP networks, while providing connection of telephones, office telephone exchanges, and transmission of faxes in real time and in the mode of their routing through a common IP network. Voice modules also support the ITU G.729, G.711 and G.723.1 standards for voice and fax quality, and the H.323 standard for multimedia applications.
- Top security
User identification, access lists, event control, encryption, private networking, tunneling, etc. A wide range of security protocols are supported, including TACACS +, Radius, Kerberos. No other network equipment provider is able to provide such a range of solutions.
- Support for a wide range of protocols
- Software options
- IP Routing (IP Feature Set)
- IP, IPX, Apple Talk (AT) and DEC routing (IP / IPX / AT / DEC Feature Set)
- Firewall (IOS Firewall Feature Set)
- Full set of network protocols (Enterprise Feature Set)
- Address Translation (NAT), Remote Monitoring (RMON), Resource Reservation Protocol (RSVP) and IBM Protocol Support (Plus Feature Set)
- Network level encryption using standard IPSec (Plus Encryption Feature Set) technology
Thus, we can build a comparative characteristic relative to other analogues:
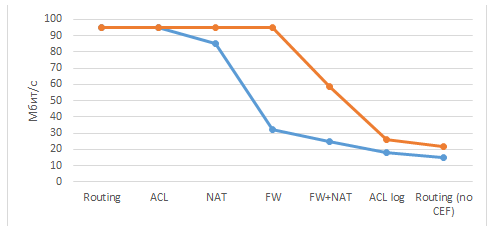
Figure 6. Comparative characteristics regarding manufacturers and equipment Cisco Catalyst
3. Protocols used by routers on the network
Routing Protocol is a network protocol used by routers to determine possible routes for data to flow into a composite computer network. The use of the routing protocol allows you to avoid manual entry of all valid routes, which, in turn, reduces the number of errors, ensures the consistency of actions of all routers in the network and facilitates the work of administrators [8]. Classification
Depending on the routing algorithm, the protocols are divided into two types:- DVA — distance vector algorithm);
- LSA — link state algorithm).
- for cross-domain routing;
- for intradomain routing.
- RIP — routing information protocol;
- IGRP — interior gateway routing protocol;
- BGP — border gateway protocol;[4]
- EIGRP — enhanced interior gateway routing protocol;
- AODV — ad hoc on-demand distance vector.
- IS-IS — intermediate system to intermediate system;
- OSPF — open shortest path first;
- NLSP — NetWare link-services protocol;
- HSRP — hot standby router/redundancy protocol;
- CARP — common address redundancy protocol;
- OLSR — optimized link-state routing;
- TBRPF — topology dissemination based on reverse-path forwarding.
- EGP — exterior gateway protocol;
- BGP — border gateway protocol;
- IDRP — inter-domain routing protocol;
- IS-IS level 3 — intermediate system to intermediate system level 3.
- RIP — routing information protocol;
- IS-IS level 1-2 — intermediate system to intermediate system level 1 2;
- OSPF — open shortest path first;
- IGRP — interior gateway routing protocol;
- EIGRP — enhanced interior gateway routing protocol.
- Static or dynamic
- Single-route or multi-route
- Single level or hierarchical
- With intelligence in the main computer or in the router
- Intra-domain and inter-domain
- Channel state or distance vector algorithms
Static or dynamic algorithms Dynamic routing algorithms adapt to changing network circumstances in real time. They do this by analyzing incoming routing update messages. If the message indicates that a network change has occurred, the routing software recalculates the routes and sends out new routing update messages. Such messages permeate the network, encouraging routers to re-run their algorithms and modify their routing tables accordingly. Dynamic routing algorithms can supplement static routes where appropriate. For example, you can develop a "last access router" (i.e., a router to which all unsent packets on a particular route are sent). Such a router acts as a repository for unsent packets, ensuring that all messages are processed at least in a certain way. Complex routing algorithms [9] when choosing a route, they can be based on a set of indicators, combining them in such a way that the result is one single (hybrid) indicator. The following indicators are used in routing algorithms:
- The length of the route
- Reliability
- Delay
- Bandwidth
- Load
- Communication cost
You should also mention one of the most important characteristics - speed. Nominal rate - the bit rate of data transmission supported on the transmission interval of one packet without distinction of service and user headers. Obviously, the smaller the package, the faster it will be transmitted.
The effective rate is the average transfer rate of user data (load) in a stream. This parameter depends on the ratio of the length of the service headers to the load. In many cases, a certain amount of information is more efficient to transfer in large batches due to lower overhead. Correctly comparing flow rates is possible only for the same amount of data that you want to transfer at a time. Thus, by checking the data, we can deduce the maximum efficiency of the transfer of useful data using some of the listed protocols: [6]
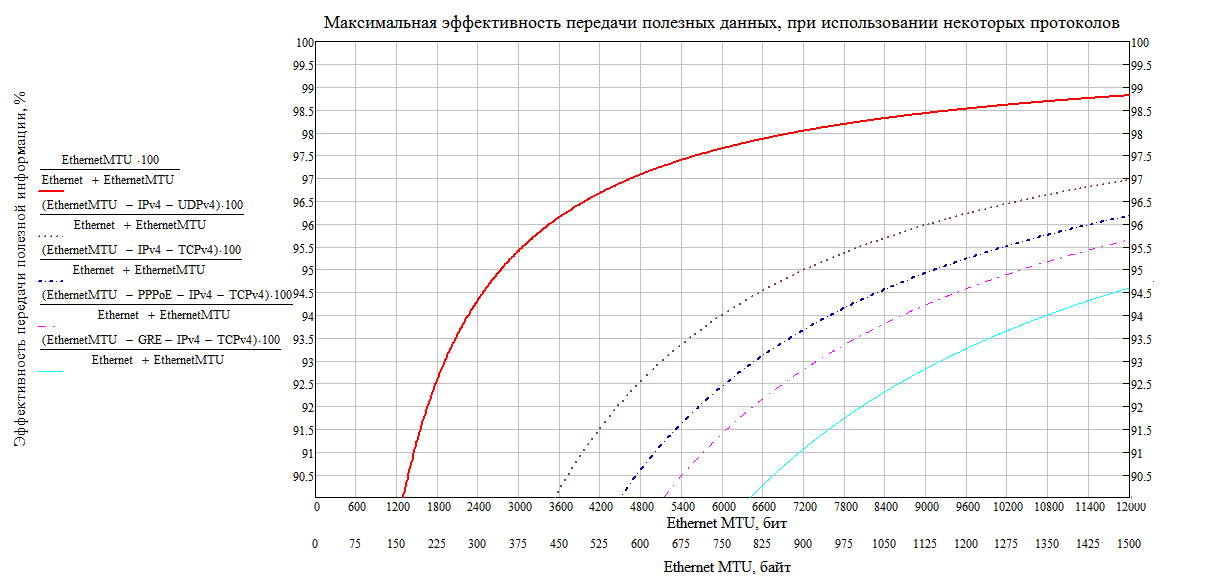
Figure 7. Dependence of effective speed on header lengths and MTU in an Ethernet network
4. Performance analysis
I decided to design the network in GNS3. I built the network on Cisco 3640 routers. The topology of the created network looks like in Figure 8.
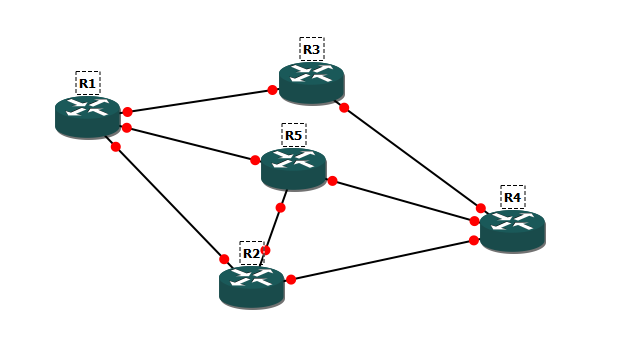
Figure 8. Network topology
Next you need to enable them and configure. To do this, we will use the topology and configuration of the gateway and IP addresses.
Figure 9. Linkage indication in topology
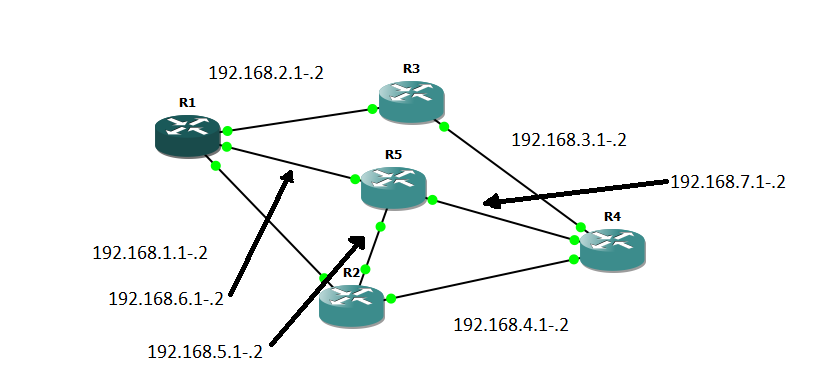
Figure 10. Connection of IP-adresses
To configure routers, we use the conf t command to enter configuration mode, to enter the required interface, enter it with the interface fa command. Next, enter the IP address and subnet mask. To enable the port, you must enter the no shutdown command.
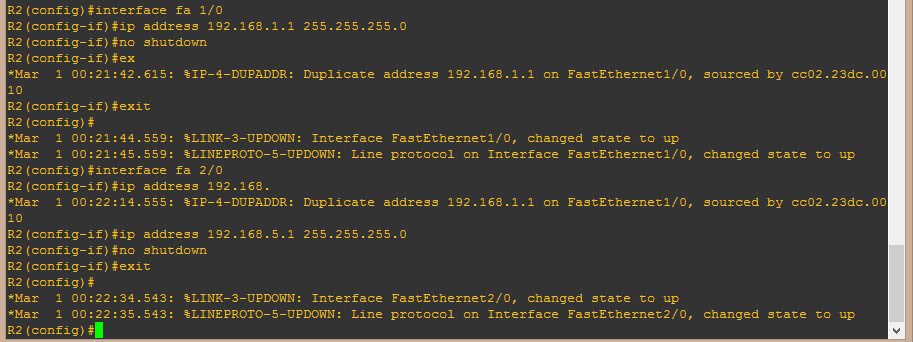
Figure 11. Butt of entering commands to configure one of the port
Next, using the ping command, check if the ports are configured correctly.
Figure 12. Port Operation Check
An example of setting up dynamic routing by entering a sequence of commands.
Figure 13. RIP Protocol Activation on R5 Router
A confirmation of the correct work performed is the ping command to that part of the network that does not belong to the static routing of this router. For example, take the router R3 and its IP 192.168.2.2
Figure 14. Checking dynamic routing from router R5 to router R3
The next command we can enter a static route. R5(config)#ip route 192.168.0.0 255.255.255.0 fa 2/0 This is the command to enter a static route. ip route is a command telling the router that a static route will now be entered; 192.168.0.0 is a remote and unknown network; 255.255.255.0 is a remote network mask; fa 2/0 is what interface to send packets destined for that remote network.

Figure 15. Checking dynamic routing from router R5 to router R3
Thus, we have performed the creation of a network topology, static addressing without switching to neighboring networks, with static addressing and dynamic addressing using RIP v2.
Since Bandwidth is one of the most important characteristics of an industrial network, the transmission of information was derived. The maximum data rate through the TCP protocol can be calculated by the following formula:
(BS x 8) / (RTT x 1024) is a maximum speed in Mb / s, where BS is the size of the receive buffer in Kilobytes and RTT is the response time in seconds
If the response time (RTT - Round Trip Time) is 5 ms or 0.005 seconds, the maximum can be transmitted via the network:(64 * 8 ) / ( 0,005 * 1024 ) = 100 Mb / s
But RTT even before the gateway is not always below 5 ms. At best, RTT to the server will be 20-50 ms. The maximum speed will be 10-25 Mbit / s.
Below is a graph which shows the dependence of the maximum speed on TCP on the RTT response time.

Figure 16. Graph of TCP maximum speed versus RTT response time
Conclusion
The network, its structure, network operating system, cable system, cable and switching equipment, network software were studied. The necessary knowledge was gained in the area of switching and routing protocols. The study and practical application of knowledge to configure switches and routers, practical construction of the ring topology. Creating a broadcast storm and its effect on devices. The master's work is devoted to an actual scientific task - the development of an industrial network model. In the framework of the research carried out:
- Analysis of existing solutions for industrial networks.
- Network structure development.
- Industrial network implementation.
Further research focused on the following aspects:
- Search for methods to optimize the industrial network.
- Research methods for optimizing data exchange within the network.
References
- Cisco Systems. Руководство Cisco по междоменной многоадресатной маршрутизации - Издательский дом "Вильямс" - 2004г. - 320 с.
- Аллан Леинванд, Брюс Пински. Конфигурирование маршрутизаторов Cisco - Издательский дом "Вильямс" - 2001г. - 47 с.
- Сэм Хелеби, Денни Мак-Ферсон. Принципы маршрутизации в Internet, 2-е издание - Издательский дом "Вильямс" - 2001г. - 448 с.
- Уильям Р. Паркхерст. Протокол Cisco BGP-4: справочник по командам и настройке - Издательский дом "Вильямс" - 2002г - 384 с.
- Ткаченко В.А. Основы локальных сетей [Электронный ресурс]. – Режим доступа: http://www.lessons-tva.info/edu/telecom-loc/m1t4_3loc.html/
- Научная библиотека Семиуровневая модель OSI [Электронный ресурс]. – Режим доступа: http://sernam.ru/book_icn.php?id=6
- Научная библиотека Преимущества использования сетей [Электронный ресурс]. – Режим доступа: http://sernam.ru/book_icn.php?id=4
- Wiki Протокол маршрутизации [Электронный ресурс]. – Режим доступа: https://ru.wikipedia.org/wiki/%D0%9F%D1%80%D0%BE%D1%82%D0%BE%D0%BA%D0%BE%D0%BB_%D0%BC%D0%B0%D1%80%D1%88%D1%80%D1%83%D1%82%D0%B8%D0%B7%D0%B0%D1%86%D0%B8%D0%B8/
- Сергей Кузнецов Типы алгоритмов [Электронный ресурс]. – Режим доступа: http://citforum.ck.ua/nets/ito/2.shtml/
- Cisco Серия модульных маршрутизаторов Cisco 3600 [Электронный ресурс]. – Режим доступа: http://www.cisco.com/russian_win/warp/public/3/ru/products/access_cisco3600.html
- Фред Бейкер Как работают маршрутизаторы? [Электронный ресурс]. – Режим доступа: https://docstore.mik.ua/routing/18/
