Yurev Nikolay
Faculty of computer science and technology
Department of automated control systems
Specialty Automated control systems
The development of the control system and access control system of security threats in the enterprise
Scientific adviser: Ph. D., associate Professor. Vasyaeva Tatyana Alexandrovna
The detection of a security threat in the access control system
Content
- 1. Goals and tasks
- 2. Analysis of access control systems
- 2.1 The structure of the ACS
- 3. Implementation of access control in a small business
- 4. Operating principle of the system
- 5. Security threat
- 6. Relevance detection in access control
- 6.1 Vulnerabilities
- 7. Method of proposed solution
- Conclusion
- References
1. Goals and tasks
The purpose of the work – to develop the access control system and enhance its reliability through the development of a subsystem for detecting security threats.
To achieve this goal it is necessary to solve the following tasks, which will be performed in the sections of the master's work:
- Investigate existing methods and algorithms used to detect threats
- Develop a mathematical model of threat detection
- To develop a modified algorithm for detecting threats
- Experimentally check the efficiency of the algorithm
The object of the study is the process of detecting threats within the access control system.
1. Analysis of access control systems
Access control system (ACS) [1], is a set of software and hardware and organizational and methodological measures by which the problem of control and management of visits to individual premises, as well as operational control of the movement of personnel and the time of its location on the site.
As you know, one of the most important tasks of the security system is the timely and reliable detection of a complex of threats to the security object [2].
The structure of the ACS
Technical means:
- stationary equipment;
- control device – controller;
- locking device;
- reader;
- access identifiers;
- power supply;
Software:
- system administration, remote access control;
- real–time monitoring;
- time tracking;
According to the degree of complexity of the system is isolated[3]:
- Autonomous
- Networking
- Integrated
3. Implementation of access control in a small business
Structural elements used in the construction of the system:
- network controller
Z–R5 net 8000 IronLogic
; - proximity card reader
Matrix II (EM–Marin 125KHz)
; - turnstile
FORMA Aldridge 5.3
; - electromagnetic door locks
YM–180
; - door open buttons;
- door opening sensors
Guardian P–408
, door closer; - power supply
ИБПС–12–1
; - interface converter USB/RS–485,
Z–397 Guard IronLogic
; - computer with software and database;
- contactless card
EM–Marin ISO 125 kHz
;
The controllers are networked using RS–485 interface and operate under computer control.
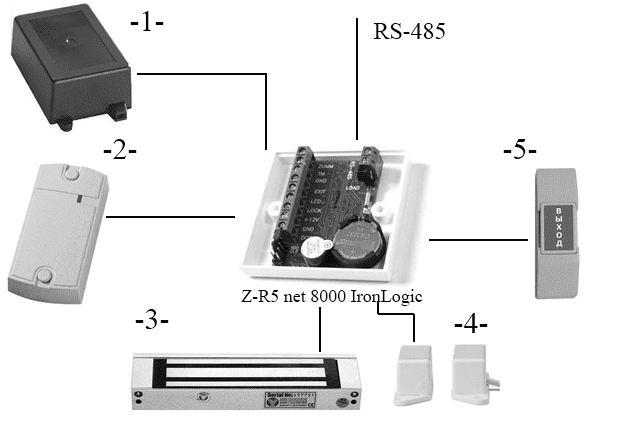
Figure 1–wiring diagram of the elements to the controller Z–5R net 8000
Let's consider the scheme of connection of the equipment to the controller,
shown in figure 2. 1 set the power source UPS–12–1
. Number 2 shows
the reader Matrix II
. Under number 3 electromagnetic lock
YM–180
. Number 4 shows the door opening sensor. Number 5 indicates
the output button to be installed indoors.
4. Operating principle of the system
When you bring the proximity card to the reader, it reads the code that comes to the controller, which decides to grant access on the basis of a database of key codes stored in its non–volatile memory. In case of permission to pass, the controller gives signals to open the door lock. The controller logs events. The actions of the system when trying to access and the positive decision of the controller are shown in figure 3.
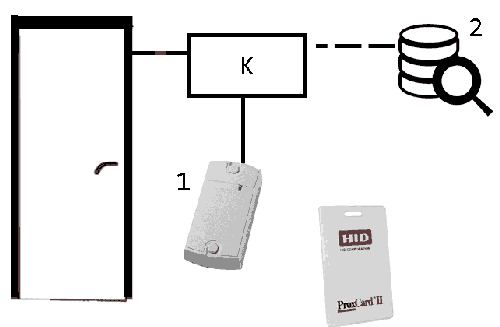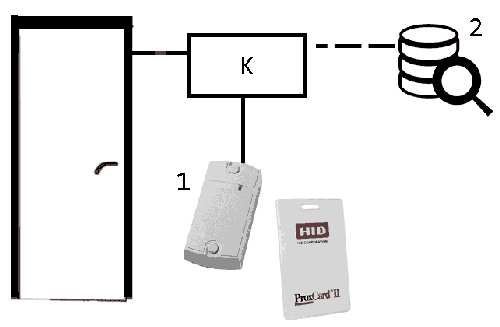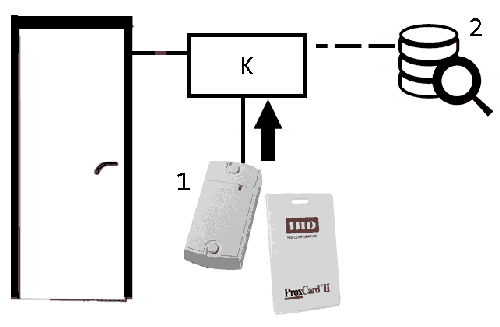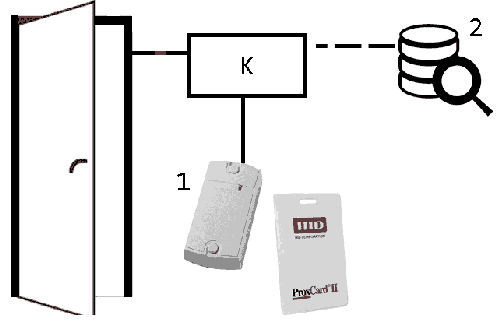
Figure 2 – operating principle of the system
(animation: frames 26, the endless cycle of repetition, 159 kbps)
( 1 – reader; 2 – data base; К – controller)
However, only the physical component of the system does not provide full protection against unauthorized access and is not able to properly respond to security violations of the protected object.
5. Security threat
Security of the protected object is a state of protection of the object from threats of damage (harm) to life or health of people; property of individuals or legal entities; state or municipal property; technical condition, infrastructure of life support [5].
A security threat is a combination of conditions and factors that endanger the vital interests of the individual, society and the state. Main threat:
- threats to life, health, personal rights and freedoms;
- threats to material and cultural values, physical media;
- threats to economic activity;
- threats of emergencies;
- threats of equipment failure.
To detect security threats, a software module is required that would monitor events in the system and inform the operator of the automated workplace of ACS about current incidents that are not noticeable in the usual analytical analysis.
6. Relevance detection in access control
Under the security breach means both unauthorized entry into the territory of the protected object, and unauthorized access to the corporate network of the object, which in turn leads to the leakage of personal information, trade secrets, theft of property, diversification in the territory of the object, as well as directly to the threat to life and health of people. Therefore, to achieve the maximum level of system protection, it is necessary to pay close attention to each potential vulnerability.
6.1 Vulnerabilities
Vulnerability (object) is the degree of non–compliance of the measures taken to protect the object with the predicted threats or specified security requirements[6].
Vulnerabilities can be divided into the following groups [4]:
- physical vulnerabilities of the equipment;
- network access control;
- behavioral vulnerabilities.
The main physical include:
- vulnerability in the energy supply system of ACS;
- physical availability of readers / controllers–readers;
- incorrect installation of turnstiles and their readers;
- equipment failure on the communication line.
Network vulnerabilities:
wiretapping
of unprotected RS 485 network;- network hacking on port 3050 / tcp.
Behavioral vulnerabilities:
7. Method of proposed solution
The task of threat detection is divided into several stages:
At the first stage, data is collected and optimized: data collection by the ACS, their filtering and aggregation.
The data collection phase of the ACS system logs all events. Then enter the filtration stage. The data obtained from ACS and passed the stages of filtering, come to the stage of aggregation and take the format of attribute (table. 1).
Table 1 – threat detection system Input
| Attribute | Description |
|---|---|
| X1={0|1|X} | Sign of working time |
| X2={0|1|X} | First visit to the facility |
| X3={0:n|X} | The access level of the card |
| X4={0:n|X} | The access level of the object |
| X5={0|1|X} | Attempt to access forbidden object |
| X6={0:n|X;Obj;L} | The number of access attempts; an object; the access level of the object |
| X7={0|1|X;Obj;L} | A sign of hardware failure; the object; the access level of the object |
| X8={0:n|X} | Multiple entry to different objects without exit |
| X9={0|1|X;Obj;L} | Power is off; the object; the access level of the object |
| X10={0|1|X;Obj;L} | The opening of the door, without the events of the passage; the object; the access level of the object |
| X11={0|1|X;Obj;L} | Not a locked door; the object; the access level of the object |
| X12={0|1|X} | Access inside the protected object, without access to the territory of the enterprise |
Notes: 0 – the criterion is not installed; 1 – criteria set; X – the criterion is not determined; 0:n – integer value; Obj – object, L – the access level of the object.
At the second stage, we choose methods to solve the problem.
At the output of the threat detection subsystem, it is expected to determine the threat class, as well as optional parameters, the source of the threat and the sector in which the threat is identified[7].
Thus, there is a problem of threat detection, which will be solved by machine learning methods [8]. Implement a mechanism to detect threats using the method of random forests. The mathematical model is an ensemble of binary decision trees built on a training bootstrap sample using a truncated set of parameters.
The method of constructing a bootstrap sample is as follows. Suppose that there is a sample of x of the size of the sample is taken Uniformly from M objects with the return.
This means that M times an arbitrary sample object is selected (assuming that each object
gets
with the same probability 1 / N), and each time it is selected from
all the original n objects. However, as a result of the return, there
will be repetitions among them. The new sample is denoted by X1.
Repeating the procedure H times, h subsamples X1,..., XH will be generated.
The truncated set of parameters is obtained as follows: P criteria are selected from the set of K initial criteria of dimension N. Repeating the procedure H times, H subsets K1,..., KH are generated.
Based on the obtained samples and subsets of criteria, an ensemble of H binary non–truncated decision trees is constructed.
By analyzing all the decision trees built, the potential threat is determined using the voting method, which is that the final decision is the value most often found in the ensemble of trees.
At the third stage, testing of the model obtained at the second stage (checking the suitability of the model).
Conclusion
The paper analyzes the components of the access control system, as well as the types of ACS construction. A physical model of the system implementation is proposed. The definition of security threats is given. The problem of detecting threats in the system is considered. The main methods used to solve the problem are considered. The method of random forests, which is planned to be applied to solve the problem, is described. In the future, it is planned to implement the considered mathematical apparatus and conduct experiments.
References
- Ворона В. А. Система контроля и управления доступов / В. А. Ворона, В. А. Тихонов. – М.: Горячая линия – Телеком, 2010. – 272c.
- Рыжова В. А. Проектирование и исследование комплексных систем безопасности //СПб: НИУ ИТМО. – 2012.
- Юрьев Н. Н. Система контроля и управления доступом / Н. Н. Юрьев, Т. А. Васяева, С. Д. Бельков, Н. С. Суббота // Информатика, управляющие системы, математическое и компьютерное моделирование. – 2017. – № 7. – С. 601–604.
- Соболев Е. Безопасность средств безопасности: СКУД [Электронный ресурс] / – Электрон. текстовые дан. – Режим доступа: https://habr.com/post/277279/, свободный
- ГОСТ Р 53704–2009 Системы безопасности комплексные и интегрированные. Общие технические требования. – Москва: Стандартинформ, 2010.
- Волхонский В.В. Основные положения концепции обеспечения безопасности объектов // Научнотехнический вестник СПбГУ ИТМО. – 2011. – № 3(73). – С. 116–121.
- Носков А.Н., Чечулин А.А., Тарасова Д.А. Исследование эвристических подходов к обнаружению атак на телекоммуникационные сети на базе методов интеллектуального анализа данных // Труды СПИИРАН. 2014. Вып. 37. C. 208–224.
- Информатика, управляющие системы, математическое и компьютерное моделирование (ИУСМКМ – 2018) / Материалы IX международной научно–технической конференции – Донецк: ДонНТУ, 2018г. – с. 126–129.
- Волхонский В.В. Подход к оценке вероятности пресечения несанкционированных действий в объединенной системе безопасности // Правове, нормативне та метрологiчне забеспечення системи захисту iнформацii в Украiнi. – Киiв, 2000. – С. 77–81.
- Волхонский В.В., Крупнов А.Г. Особенности разработки структуры средств обнаружения угроз охраняемому объекту // Научно–технический вестник Санкт–Петербургского государственного университета информационных технологий, механики и оптики. 2011. №4 (74). С. 131–136.
