Abstract
Содержание
- Introduction
- 1. Relevance of the topic
- 2. ЦельThe purpose and objectives of the study, the planned results
- 3. Approbation
- 4. Research and development overview
- 4.1 Overview of international sources
- 4.2 Overview of national sources
- 4.3 Overview of local sources
- 5. The problem of ensuring the protection of confidential information
- 6. Description of information concealment system by means of linguistic steganography
- Summary
- Comments
- List of sources
Introduction
To date, information is considered as one of the main resources of the development of society, and one of the strategic resources. Information systems and technologies are considered to be a means of increasing the productivity and efficiency of people. Therefore, information is a valuable and expensive resource[1].
With the development of Internet technologies, it has become easier for a person to transfer various kinds of files: video, audio, digital images and much more. The most powerful stream is text information. There are many ways to transfer text information, for example: transmission via e-mail, messages on various forums or social networks, etc. However, not every text information can be accessed by third parties. there are Often cases when the information belongs strictly to a certain circle of persons and should not be opened outside this group of people, i.e., to the public. information should be confidential. To ensure the confidentiality of information, it is possible to introduce it into a secret message and pass it to the right circle of people.
1. Relevance of the topic
The loss of information on a personal computer, or the interception of a document when sending an email, is tangible for its owner and can lead to various kinds of problems. The problem of protecting the confidentiality of information is global. The solution to this problem can be considered the direction of technology for the hidden transmission of information in text documents, which is called linguistic steganography.
After applying linguistic methods, a steganogram has the appearance of a document that can carry any distracting semantic load for the reader and non-obvious useful information for the true recipient[3].
A distinctive feature of linguistic steganography, unlike other types of steganography, a classified message can be transmitted in any form: electronic text, handwritten text or in the process of oral conversation.
2. The purpose and objectives of the study, the planned results
The aim of the work is to develop our own method of linguistic steganography based on the method of jargon to ensure the concealment of information in texts.
The following tasks were set for the implementation of the master's work:
- analyze the issue and study the literature on methods of information protection;
- it is necessary to carry out research of already existing methods of linguistic steganography;
- to determine the evaluation of research methods of linguistic steganography;
- to develop the author's method of linguistic steganography based on jargon methods.
Thus, the result of the work, it is planned to obtain the author's method of hiding information in texts, based on linguistic steganography.
Object of research:methods of hiding information in text information.
Subject of research: the effectiveness of the use of jargons in linguistic steganography.
3. Approbation
The work was presented at the following conferences:
- Software engineering: methods and technology development of informational-computational systems (PIIS-2018);
- Informatics, control systems, mathematical and computer modeling in the framework of the III forum Innovative perspectives of Donbass (IUSMKM – 2019);
- 69th international student scientific and technical conference, Astrakhan, 15-19 April 2019 [Electronic resource]: materials / Astrakhan. state tech. UN-T.-Astrakhan: publishing house of AGTU, 2019;
- Young scientists’ researches and achievements in science: collection of reports of scientific and technical conference for young scientists (Donetsk, April 18, 2019) / OTP. per vol. E. N. Kushnirenko. – Donetsk: DonNTU, 2019 – 107 c.
Research and development overview
Ensuring the confidentiality of information is one of the priorities of the XXI century. In this regard, every year a number of scientists around the world devote more of their works in the research of such areas as steganography. Figure 1 shows the structure describing the classification of steganography.
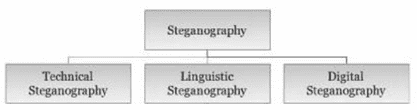
Figure 1 - Classification of steganography
4.1 Overview of international sources
The issue of protection of confidential information through the use of linguistic steganography, including the method of jargon, was considered in the works of M. K. Kaleem [4] and M. Zelkowitz [5]. Figure 2 shows the types of linguistic steganography.
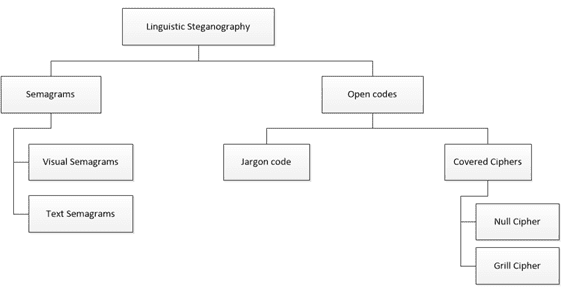
Figure 2 - Types of linguistic steganography
4.2 Overview of national sources
On the territory of the Russian Federation, the relevance of the issue was considered by O. I. Babina, who devoted several articles to linguistic steganography and their modern approaches[6,7].
In his works, O. I. Babina examines in detail the question of the place of linguistic steganography in the system of methods of hiding information as a way of introducing a secret message into a text container. Also, the author identifies the most popular substitution method in linguistic steganography - the method of synonymous substitutions, where synonymous series act as equivalence classes. Words-synonyms are characterized by full or partial coincidence of meanings and interchangeability in some contexts, which is due to the possibility of synonymous replacements, as a result of which a stegotext is created, claiming to preserve the properties of the" natural " text at the level of lexical semantics[7].
Also, this issue was dealt with By A. T. Aliyev with the article "Linguistic steganography based on the replacement of synonyms for texts in Russian", in which he considers the methods of transmission of hidden information, which are based on the use of synonyms[10].
4.3 Overview of local sources
In DonNTU the question of hiding information in the text by using linguistic steganography was dealt with by K. E. Larionova, the theme of her master's work was: "Methods of encoding arbitrary information in computer texts based on linguistic resources"[8].
Also, the question of linguistic steganography was analyzed by Sokolenko I. V., the theme of the master's work was: "The system of hiding information on the basis of linguistic resources"[11].
5. The problem of ensuring the protection of confidential information
The loss of information on a personal computer, or the interception of a document when sending an email, is tangible for its owner and can lead to various kinds of problems. The problem of protecting the confidentiality of information is global. Methods of implementation of threats to information security are constantly improving, high technology of these threats requires adequate countermeasures (figure 3).
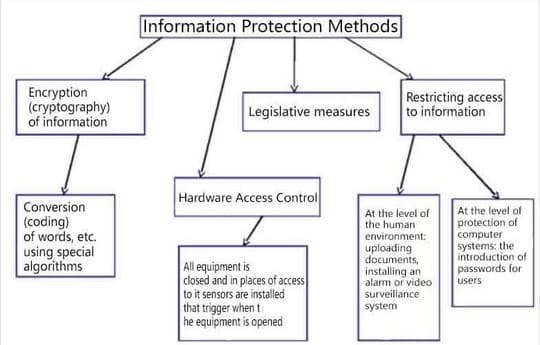
Figure 3 – information security Methods
One of the best and effective methods to ensure the protection of information is considered to be information encryption. The essence of ensuring the security of information by using encryption is that to prevent unauthorized access to any message, it is encrypted. When an authorized user receives an encrypted message, he decrypts it or reveals it by using a reverse-conversion program. These encryption methods are based on the use of a special algorithm that is triggered by the encryption key, which is a unique number or set of numbers.
6. Description of information concealment system by means of linguistic steganography
Modern methods of linguistic steganography emphasize the automated approach of creating stegotext. Basically, when creating a stegotext, use the secret message M (usually in binary representation) as input and, sometimes, the text container C (the text is usually provided in the public domain). Using the capabilities of the linguistic base, the message M is embedded in the text-container C. there are situations When the text-container is not specified. In such cases, the algorithm for creating stegotext changes. Pseudotext is created by converting secret information M on the basis of developed procedures and linguistic knowledge base. As a rule, such text meets the requirements for "normal" text at the syntactic and statistical levels, but semantics suffers in such texts, since it is the most complex object in computer modeling of natural text. When presenting such a text to a person, he will easily determine its "irregularity", indicating the presence of properties unusual for a natural text. In this regard, the main task of modern linguistic steganography is to solve the question of what should be the process of machine generation of stegotext, which, assessing at each level, would be similar to a human-created text.
For modern approaches, a common property is the use of variability of language means to embed secret information in the text container
Процесс передачи секретного сообщения представлен на рисунке 4:
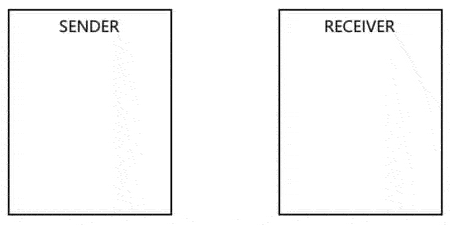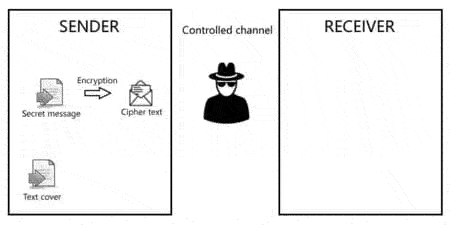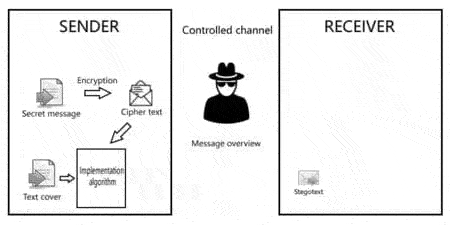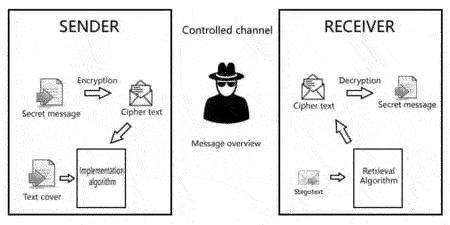
Figure 4 – The process of transmitting a secret message is presented
(animation: 13 frames, 6 cycles of repetition, 54 kilobytes)
Summary
As a result of the research work, materials on issues related to the topic of the master's work were collected and studied.
The conducted work allows us to conclude that the issue of information confidentiality is relevant not only at the local or national level, but also at the world level. In the course of research, various authors have noted the fact that using linguistic steganography as a method of hiding information, a person thus protects it. The peculiarity of linguistic steganography is that, unlike other types of steganography, a classified message can be transmitted in any form: electronic text, handwritten text or in the process of oral conversation.
Comments
At the time of writing this essay master's work has not yet been completed. Expected completion date: may 2020. the Full text of the work, as well as materials on the topic can be obtained from the author or his supervisor after this date.
List of sources
- Замкова Т.В. Проблемы защиты информации в современных информационных системах // Современные наукоемкие технологии. – 2005. – № 3. – С. 58-59; Режим доступа: http://www.top-technologies.ru/ru/article/view?id=22431
- Большаков И.А. Использование синонимов, ограниченных контекстными словосочетаниями, для целей лингвистической стеганографии / И.А. Большаков, - 2004, - с. 23-29
- Лекции.Орг - публикация материалов для обучения. Режим доступа:https://lektsii.org/2-89057.html
- M.K. Kaleem (May 2012), An overview of various forms of linguistic steganography and their applications in protecting data, Journal of Global Research in Computer Science (Volume 3, No. 5)
- Zelkowitz M (2011), Security on the Web, Academic Press, UK, p 54.
- Бабина, О.И. Лингвистическая стеганография: современные подходы. Часть 1 / О.И. Бабина // Вестник ЮУрГУ. Серия
Лингвистика
. – 2015. – Т. 12, № 3. – С. 27–33. - Бабина, О.И. Лингвистическая стеганография:современные подходы. Часть 2 / О.И. Бабина // Вестник ЮУрГУ. Серия
Лингвистика
. – 2015. – Т. 12, № 4. – С. 49–55. DOI: 10.14529/ling150410 - Ларионова К.Е. Методы кодирования произвольной информации в компьютерных текстах на основе лингвистических ресурсов [Электронный ресурс] — Режим доступа:http://masters.donntu.ru/2009/fvti/larionova/diss/index.htma
- Программная инженерия: методы и технологии разработки информационно-вычислительных систем (ПИИВС-2018): сборник научных трудов II научно-практической конференции (студенческая секция), Том 2, 14-15 ноября 2018 г. – Донецк, ГОУВПО
Донецкий национальный технический университет
, 2018. – с. 114–117. // Режим доступа:http://pi.conf.donntu.ru/collection/... - Алиев А.Т. Лингвистическая стеганография на основе замены синонимов для текстов на русском языке / А.Т. Алиев // Известия ЮФУ.Технические науки № 11, — 2010, — C. 163-170.
- Соколенко И.В. Система сокрытия информации на основе лингвистических ресурсов [Электронный ресурс] — Режим доступа:http://masters.donntu.ru/2014/fknt/sokolenko/diss/index.htm#ref3
