Abstract
Содержание
- Introduction
- 1. Relevance of the topic
- 2. Purpose of research
- 3. System vulnerabilities
- Conclusion
- References
Introduction
Security of objects (enterprises) – is a complex of organizational, operational, regime, engineering and technical, fire prevention measures and actions of individuals (security personnel, administration, etc.) aimed at preventing damage to the interests of the enterprise and its personnel as a result of theft of material, technical and financial resources, destruction of property and valuables, disclosure, loss, leakage and destruction of information, disruption of technical means that ensure production activities. The main goal of any security system is to ensure the sustainable operation of the object, prevent threats to its security and protect it protection of the Customer's legitimate interests from illegal encroachments, as well as prevention of theft of financial resources, disclosure, loss, leakage, distortion, etc. destruction of service information, ensuring normal production activities of all divisions of the object, as to the conditions of daily activity, and in emergency situations.
1. Relevance of the topic
I think that the protection of particularly important objects and information that is located there will never lose its relevance. Information has been valued at all times, but today it is no less valuable. This value can be determined not only by the amount of labor spent its creation, but also the amount of profit received from its implementation, as well as all possible consequences due to its leakage. Development of technical means it does not stand still and the pace of their development, sometimes, is amazing. The development of computer networks sometimes contributes to information leakage. But, there is also a human factor, and it plays not the least role in the theft of information.
2. Purpose of research
Before we start protecting the information itself, I think we should decide on the object that we will protect. After consulting with our supervisor, we decided that we would create a security program for an object owned by an IT company with a smart home system. An intelligent building with an integrated approach provides not only centralized management, but also reduces maintenance costs systems'.
3.System vulnerabilities
Modern equipment, thanks to the flexibility and structure of automated networks, allows you to combine various automation subsystems into a single system. The room is becoming more functional, but increasing the degree of integration leads to a number of shortcomings and new vulnerabilities. To eliminate them, it is necessary to use additional devices and devices, which, in turn, does not exclude the possibility of making an error in the design or during time of the integration process. All this leads to additional weaknesses in the system.
Attackers can take advantage of vulnerabilities in modern automated life support systems of the smart home and attempt an attack in their own systems. purposes. Some of the protocols used to control devices that are open to known vulnerabilities at the same time, some vulnerabilities manifest themselves in certain situations with incorrect integration.
As a rule, management is carried out by a dedicated computer on which server software (SOFTWARE) is installed, as well as SOFTWARE for operation with a local computer network and programs responsible for processing all incoming data. Many auxiliary devices for data transmission are connected to the computer: GSM modems, Bluetooth transmitters, Wi-Fi access points, and others. These channels are the most common targets for attacks and virus introduction.
Main distribution channels of the virus:
- Bluetooth channel. Bluetooth networks are extremely unreliable and can easily accept a virus file from an attacker without requesting authorization.
- Wi-Fi channel. A Wi-Fi network can be easily hacked by an attacker, imitating an authorized user, and transmit the virus to the server.
- an HTTP channel for remote access. The HTTP Protocol uses the Internet and is unprotected.
- GSM channel. It is possible to perform unauthorized control of the system via the GSM channel, for example, when transmitting an SMS message with a fake sender number.
- Paired channels. Connecting smart home servers to the premises ' local network allows you to use it to transmit a virus program.
- Reinstalled software and logic bombs. The moment when the system is reinstalled can be used by an attacker to inject a virus. It is almost impossible to prove that the virus was installed maliciously, and it is also extremely difficult to detect such a virus.
The smart home
system allows you to combine both heterogeneous equipment and standard sensors and devices:
- Electromechanical load control devices (doors, gates, etc.) appropriate devices are used to control all kinds of Electromechanical loads. Loads can be controlled both locally and remotely from remote controls.
- Wall-mounted and portable touch control panels. Any automation system has a convenient control and monitoring tool
from one place
. Touch displays are used for this purpose. - Thermostats, temperature sensors. Designed to create the desired temperature regime in the room (in our case, in the server room). Radiator thermostats are installed on the valves of heating radiators and, receiving signals from sensors, controller, or by their own programs, regulate the supply of heat carrier, thereby ensuring the required temperature in the room.
- motion sensors. Designed for various applications. You can use motion sensors to control the light in passageways (corridors, stairs). The motion sensor can also be used in a security system, transmitting an alarm in the event of activity in the detection zone. More functional motion sensors include additional parameters (temperature, humidity, light) that allow you to use them more effectively without additional sensors.
- Sirens. Sends an alarm signal if a sensor (for example, a motion sensor, a door/window opening sensor) is triggered in a protected area. The siren can give an alarm when other devices are triggered, which increases the level of security.
- Power saving devices. The main application of this device is to save electricity and energy resources spent on heating. Tracking is performed both locally on displays and remotely via the Internet.
- Door locks. Door locks, in addition to their direct purpose, allow you to implement additional functions, such as notification of an attempt to select a code on the code panel, notification of the return of relatives home via SMS or e-mail, as well as control of other devices (light, heating).
- Auxiliary sensors. Auxiliary sensors allow you to increase the degree of integration of the intelligent home system. These include: door/window opening sensors, water leak sensors, temperature sensors, humidity sensors, smoke sensors, gas sensors, air quality sensors, etc.
- gateways – Internet. Designed to manage and control the entire home remotely from anywhere in the world. The only condition is the availability of Internet at home and in the place of observation. Access can be carried out either through a regular browser, or using specialized software that is installed on smartphones and tablets.
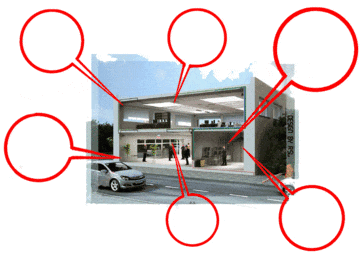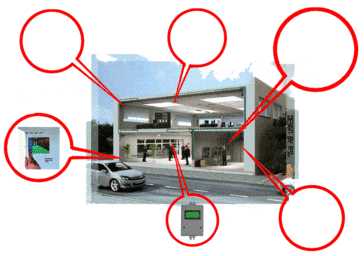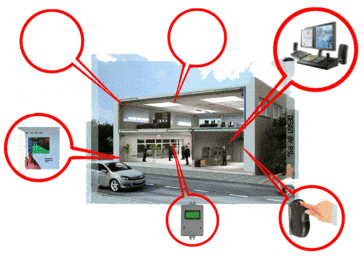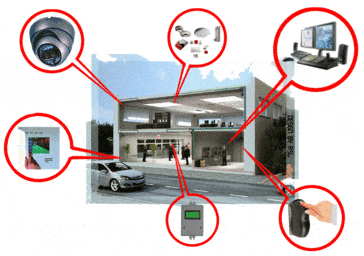
Рисунок 1 – Devices for protecting a highly informative object
(animation: 7 frames, 134 kilobytes, 6 cyclessp)
Conclusion
Every year, a number of new or modified perimeter security systems are released on the market, produced by recognized world leaders in this field.
The General trend in the development of these devices is the increasing use of digital technologies that allow you to implement many useful functions, simplified procedures for setting up, diagnosing, and managing security systems
Almost all newly developed perimeter security sensors provide for their integration into communication networks for the organization of extended systems security with centralized or distributed management functions.
References
- Аристов, М.С. Антивирусный программно-аппаратный комплекс для систем автоматизированного здания / М.С. Аристов // Международная телекоммуникационная конференция молодых ученых и студентов «МОЛОДЕЖЬ И НАУКА». Тезисы докладов. В 3-х частях. Ч. 3. – М.: НИЯУ МИФИ, 2011. – С. 151-152.
- Smart House // Разумный дом MimiSmart зданий [Электронный ресурс]. – Режим доступа: http://www.smarthouse.ua/ua.
- Игнатьев, В. А. Информационная безопасность современного предприятия [Текст] / В. А. Игнатьев. - Старый Оскол: ТНТ, 2005. - 448 с.
- Кусакин, И.И. Программно-аппаратный комплекс автоматизированного контроля целостности инфраструктуры жилых помещений для социального обеспечения / И.И. Кусакин // Международная телекоммуникационная конференция молодых ученых и студентов «МОЛОДЕЖЬ И НАУКА». Тезисы докладов. В 3-х частях. Ч. 3. – М.: НИЯУ МИФИ, 2012. – С. 156-157.
- Широков, Ф.К. Bluetooth: на пути к миру без проводов. / Ф.К. Широков // Открытие системы, – 2001. – № 2 [Электронный ресурс]. – Режим доступа: http://www.radioscanner.ru/info/article95.
- Касперски, К. Записки исследователя компьютерных вирусов / К. Касперски. – С-Пб.: Питер, 2006. – 216 с.
- ГОСТ 12.0.003-74 ССБТ. Опасные и вредные производственные факторы. Классификация. – М.: ИПК Издательство стандартов, 1974. – 4 с.
- Уэйкерли Д. Проектирование цифровых устройств / Д. Уэйкерли. – М.: Постмаркет, 2002. – Том 2. – 528 с.uide for Virtex-4, Virtex-5, Spartan-3, and Newer CPLD Devices [Электронный ресурс]. – Режим доступа: http://www.xilinx.com/support....
