Abstract
At the time of writing this abstract, the master's thesis has not yet been completed. Final completion: June 2024. The full text of the work and materials on the topic can be obtained from the author or his supervisor after the specified date.
Contents
- Introduction
- 1. Relevance of the topic
- 2. Purpose and objectives of the study, planned results
- 3. Research and Development Overview
- 3.1 Review of international sources
- 3.2 Review of national sources
- 3.3 Overview of local sources
- 4. Authentication Approaches
- 4.1 Password authentication
- 4.2 Authentication based on
challenge-response
- 4.3 Authentication using access keys
- 5. Analysis of the features of modern authentication protocols
- 5.1 Cryptographic algorithms used
- 5.1.1 Kerberos protocol
- 5.1.2 SAML protocol
- 5.1.3 OpenID Connect Protocol
- 5.2 SSO single sign-on
- 5.3 Mutual client and server authentication
- 6. Alternative authentication methods
- 6.1 SRP Protocol
- 6.2 OPAQUE protocol
- Conclusions
- List of sources
Introduction
One of the most important tasks for any computer system is reliable and secure authentication of its users. To solve this problem, authentication protocols use special rules for transmitting information and various cryptographic algorithms.
Every user of modern computer systems encounters authentication procedures repeatedly, working in the system every day [1]. Client-server applications are no exception. Moreover, today client-server architecture is widely applicable in various systems and is the basis of Internet services and web applications, social networks, as well as other applications that distribute information over the Internet
Today it is difficult to imagine that programmers, when developing a client-server application, do not use secure means of user authentication based on cryptographic algorithms. Any modern application uses security measures to transmit confidential information. To do this, we use secure authentication protocols or our own secure authentication proposals based on existing standards and solutions.
1. Relevance of the topic
In modern conditions, there are enough methods and approaches for authenticating subjects of various systems, including client-server applications. But despite the availability of seemingly excellent authentication means, issues of unauthorized access to software systems are still relevant.
Modern authentication protocols still have vulnerabilities that can be exploited by attackers. For example, existing standardized authentication protocols such as OAuth and SAML are well understood, but they can also be susceptible to certain threats such as Man-in-the-Middle
attacks or session hijacking [2].
Thus, the urgent task is to develop our own authentication protocol, which will correspond to the characteristics of client-server systems and satisfy specific security requirements.
In addition, developing your own authentication protocol can provide greater control over information security. And when resources are limited, an authentication protocol that consumes fewer resources than existing protocols will optimize system performance and reduce costs.
2. Purpose and objectives of the study, planned results
Object of study – authentication protocols in client-server applications.
Subject of research – methods and trends in the field of secure user authentication in client-server applications.
The purpose of the study is to study modern protocols and approaches to authentication, their advantages and disadvantages, as well as the formation of requirements for your own authentication protocol in client-server applications, taking into account the features of the client-server architecture.
Main objectives of the study:
- Overview of methods and approaches to authentication in client-server applications.
- Research of threats and vulnerabilities in authentication protocols.
- Putting forward your proposals to improve the authentication protocol.
- Formation of requirements and determination of the general scheme of operation of the author’s protocol.
- Implementation of a test client-server application with an improved authentication protocol.
As a result, it is planned to demonstrate the operation of the author's authentication protocol, designed taking into account the advantages and disadvantages of existing protocols, in a test client-server application. The improved protocol will meet the requirements of secure authentication, and can also be used when developing different client-server applications, rather than one specific application.
3. Research and Development Overview
Let's consider international, national and local sources on the topic under study.
3.1 Review of international sources
Users are typically authenticated using their passwords. The article by Taekyoung Kwon and Joo-Seok Song Efficient and secure password-based authentication protocols against guessing attacks
discusses authentication and key exchange protocols that are effective against password guessing attacks [3].
The article by Li Gong Efficient network authentication protocols: Lower bounds and optimal implementations
presents the minimum requirements for network password authentication protocols [4].
In the article Roger M. Needham and Michael D. Schroeder Using encryption for authentication in large networks of computers
, the authors discuss the use of encryption for authentication in large computer networks [5]. Both symmetric and public key encryption algorithms are explored as the basis of the protocols.
3.2 Review of national sources
The article by Shapiro L. Authentication and One-Time Passwords
describes OTP technologies that can reduce the risks that companies face when using long-term, memorable passwords [6].
In the article by Titov V.S. Identification and authentication. Methods and methods of authentication
describes the advantages and disadvantages of the main authentication methods [7].
3.3 Overview of local sources
Exactly the same problem was not found in the works of masters from previous years, but work on related topics was found. In the abstract Grishchenko O. S. Improving authentication algorithms and studying its effectiveness when used in distributed systems
approaches to authentication in distributed software systems were analyzed, where multi-factor and biometric authentication systems were highlighted as the most relevant area [8].
4. Authentication Approaches
Authentication (and other security services) can only be offered in the context of a specific security strategy. Acceptable methods and approaches to authentication depend on each specific software system and play an important role in the design of its security subsystem. Cryptographic protocols often implement an approach based on user identification using a password.
4.1 Password authentication
One of the most common methods of user authentication is password authentication. When using password information to authenticate a user, there are threats of disclosure, eavesdropping, and password guessing. To prevent them, they use means that make it difficult or slow down the possibility of brute force or guessing a password.
Within password authentication, there are options with fixed and one-time passwords. One-time password authentication is often used in conjunction with a fixed password to further confirm the subject's identity. In this case, so-called two-factor authentication is used, which significantly increases the security of the system.
4.2 Authentication based on challenge-response
In addition to password-based authentication protocols, there are also challenge-response
-based protocols. In such protocols, a subject can be authenticated by testing his knowledge of some secret information without presenting the secret itself (see Fig. 1). Some of these protocols require the server to know the secret, while for some protocols there is no such need at all. This approach is based on the user's response to server requests that change with each session.
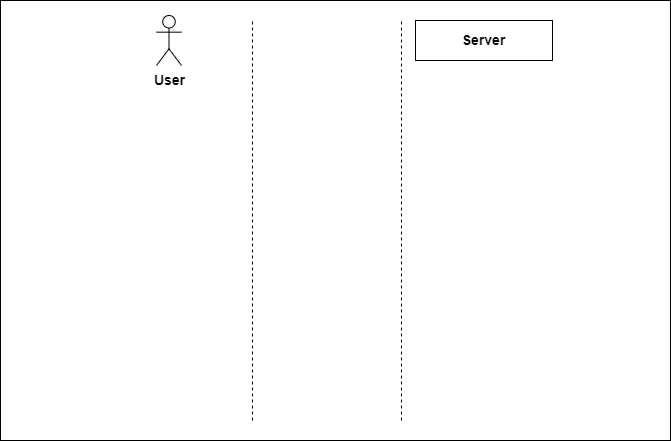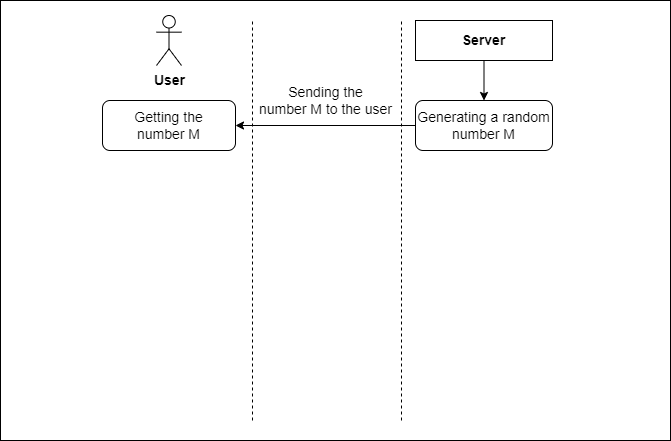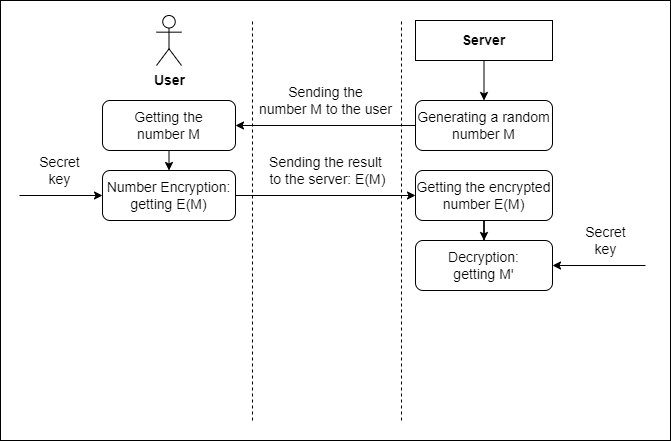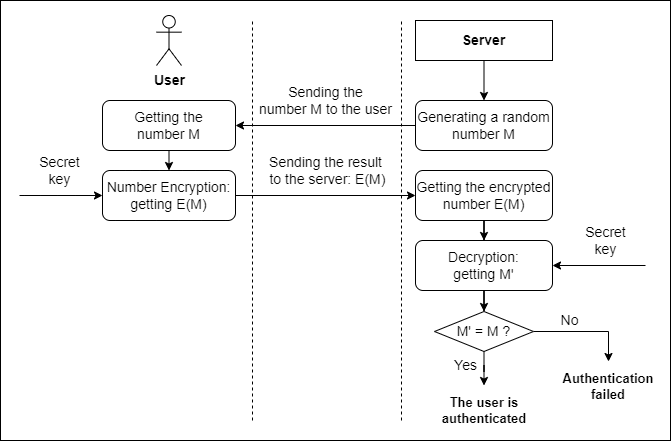
Figure 1 – Strong authentication scheme
(animation: 11 frames, 7 repetition cycles, 16 kilobytes)
4.3 Authentication using access keys
It is also possible to authenticate the user using pre-generated access keys. Access keys are generated by the server as a unique and long string of characters and stored in client applications that authenticate using the received keys. This method is very popular in various web services.
5 Analysis of the features of modern authentication protocols
Today, password-based authentication remains one of the most popular methods of user authentication in client-server applications. However, this method is not secure enough, especially for simple user authentication.
Past research has described the need to use strong authentication to ensure security when transmitting passwords over unsecured networks [9].
Strong authentication protocols can be divided into several groups, depending on the cryptographic algorithms that underlie them. These algorithms include:
- symmetric encryption algorithms;
- asymmetric encryption algorithms;
- one-way key hash functions;
- electronic digital signature algorithms.
Earlier in the work, an overview of the most common authentication methods and protocols in client-server applications [10] was already given. Among the authentication protocols listed, the most commonly mentioned are strong authentication protocols such as Kerberos, SALM, and OpenID Connect (built on top of the OAuth 2.0 protocol).
5.1 Cryptographic algorithms used
We will consider the main cryptographic algorithms used in the Kerberos, SAML and OpenId Connect authentication protocols, and analyze the effectiveness of the technologies and methods used by the protocols to ensure security during data exchange.
5.1.1 Kerberos protocol
Kerberos version 6 (2019) is the latest version of the protocol. It also supports different encryption algorithms and key sizes, including those used in version 5, as well as new ones such as ChaCha20-Poly1305, Ed25519, Curve25519. Key sizes can vary from 128 to 512 bits.
In addition, Kerberos uses public key encryption algorithms: RSA to create and verify electronic signatures and to encrypt and decrypt session keys. In addition to RSA, various digital signature algorithms are supported, such as DSA, ECDSA and HMAC.
Kerberos also allows you to use different hash functions for different purposes. For example, using the MD4, MD5 and SHA-1 algorithms, keys can be generated from user passwords. The SHA-2 hash function can be used to sign and encrypt tickets and messages.
5.1.2 SAML protocol
The SAML protocol allows you to authenticate users and transfer information about them between different systems and applications using a single set of credentials [11]. To achieve this, SAML uses single sign-on (SSO) technology.
SAML uses an XML format to convey security assertions such as user identities, roles, attributes, and permissions. To encrypt data, SAML uses the public key encryption algorithm XML Encryption, which supports various asymmetric algorithms such as RSA, ElGamal, ECDH.
SAML also uses 3DES and AES symmetric encryption algorithms to protect two types of data: assertions and messages.
To create and verify electronic signatures, SAML uses the XML Signature public key encryption algorithm, which supports various asymmetric algorithms such as RSA, DSA, ECDSA. The SHA-1 and SHA-2 algorithms, as well as SHA-3, can be used for signing.
5.1.3 OpenID Connect Protocol
The OpenID Connect protocol can use symmetric encryption algorithms to protect the identity tokens (JSON Web Token) that are passed between the identity provider and the client. The AES algorithm with Galois/Counter Mode (GCM) is also used for these purposes.
The OpenID Connect protocol uses SHA-256 and SHA-512 hash functions to generate asymmetric keys, as well as to sign identity tokens using algorithms such as RSA or ECDSA (Elliptic Curve Digital Signature Algorithm).
The ECDH algorithm can also negotiate a content encryption key that will be used to encrypt the signed JWT.
5.2 SSO single sign-on technology
The SSO single sign-on technology of the SAML and OpenID Connect protocols allows the user to log into different systems and applications using one set of credentials (see Figure 2).
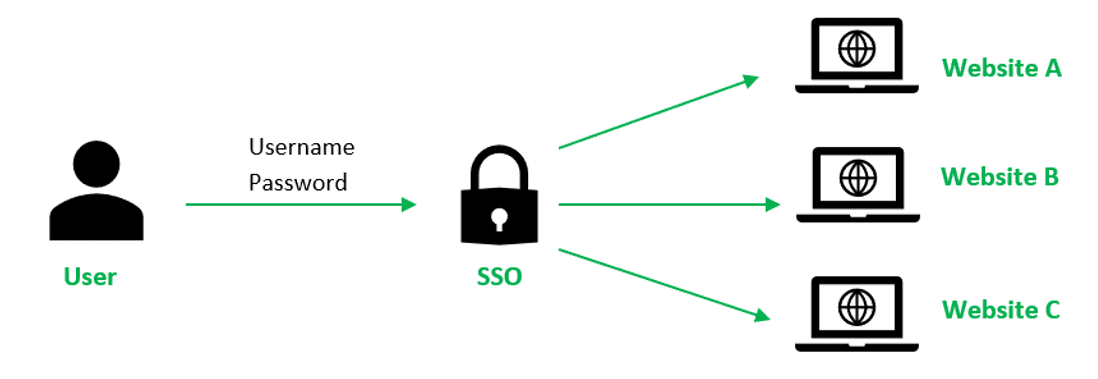
Figure 2 – SSO single sign-on technology
The Kerberos protocol uses a user's primary identity to subsequently gain access to specific network resources.
This may be convenient for the user, however, if an attacker gains access to the user's credentials or SSO token, they can log into all systems and applications that support SSO and gain access to sensitive information or resources. Additionally, if the SSO provider goes down, users cannot log in to the systems.
Thus, within the framework of the authentication protocol being developed, the use of single sign-on technology may not be appropriate. The advantages and conveniences of SSO can be beneficial in some cases, however, for most client-server applications they do not exceed the possible risks and difficulties.
5.3 Mutual authentication between client and server
The Kerberos protocol provides a mechanism for the client and server to mutually authenticate before communication is established between them. Mutual authentication in Kerberos occurs using a trusted third party.
SAML and OpenId Connect authentication protocols do not provide direct mutual authentication between client and server. However, SAML and OpenID Connect protocols can be used in combination with other protocols such as TLS for these purposes.
In this case, to implement mutual authentication of the client and server, cryptographic certificates are usually used, which are issued by trusted certification authorities (CA).
However, using this method requires a complex infrastructure and key synchronization, as well as taking into account the risks associated with loss, theft or compromise of certificates.
In general, mutual authentication of the client and server is necessary as part of the authentication protocol being developed. However, using a trust authority or certificates may not be appropriate.
6 Alternative authentication methods
If we talk about the possibility of client and server authentication without using certificates or a third trusted party, then, first of all, it is worth mentioning the PAKE key exchange protocols.
Password-Authenticated Key Exchange (PAKE) key agreement schemes allow participants to authenticate each other and obtain shared cryptographic keys using a common (weaker) password. The principle of operation is to generate a common symmetric key based on public data. A popular example of such a protocol is the Diffie-Hellman key exchange.
Figure 2 shows an idealized representation of the PAKE protocol, which does not include some random components (for example, salt) [12].
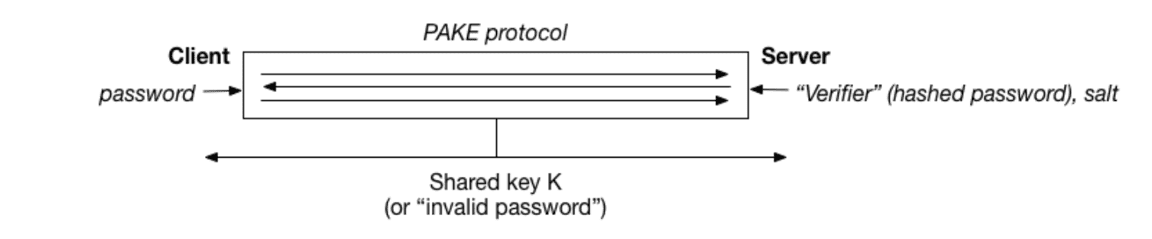
Figure 3 – Idealized representation of the PAKE protocol
In 2019, the CFRG research group recommended an additional
implementation of PAKE, OPAQUE, for use in the IETF. In addition, among the additional
implementations of PAKE, the SRP protocol is also distinguished.
6.1 SRP Protocol
The SPR protocol is an improvement on the Diffie-Hellman protocol and the most common implementation of PAKE. In this protocol, the client and server use passwords to authenticate each other and to protect against man-in-the-middle
attacks and dictionary attacks.
There are several variants of the SRP protocol, but the most popular, standardized and, moreover, not yet hacked is SRP-6 [13]. It provides secure authentication over an insecure channel. The protocol uses random number exchange and hashing to authenticate the client and server. SRP-6 avoids transmitting the password over the network, making it resistant to interception.
The SRP protocol effectively implements zero-knowledge proof between the user and the server that stores his password information. It is also used for SSL/TLS authentication.
6.2 OPAQUE protocol
The OPAQUE (Oblivious PAKE) protocol is a password authentication protocol that provides secure communication between a client and a server without the server having any way of knowing the user's password.
The main advantage of OPAQUE is that the server does not store or see the user's original password [14]. Instead, it works with obfuscated versions of the password, which improves security. Also, as with the SRP protocol, even if an attacker gains access to the server database, he will not be able to recover the original passwords.
Unlike the SRP protocol, OPAQUE does not require a salt to be passed from the server to the client. The password hash is stored on the client side, but not the salt. According to OPAQUE, the server stores the original salt and the client stores another salt calculated from the original salt and the password. To calculate another salt, the so-called forgetful PRF (a family of pseudo-random functions) is used.
Conclusions
In general, the simplest and most effective way to authenticate users is through password authentication. However, in this case, it is necessary to create complex and unique passwords and set complexity requirements to increase the level of security.
When developing our own authentication protocol, we need to use cryptographic methods and encryption mechanisms. In addition, a modern authentication protocol may additionally include verification of identification data through the use of various verification technologies.
In the future, it is necessary to define the general scheme of how our authentication protocol works in client-server applications, which, in turn, can be based on a key agreement scheme with password verification.
References
- Афанасьев, А. А. Аутентификация. Теория и практика обеспечения безопасного доступа к информационным ресурсам. Учебное пособие / А. А. Афанасьев, Л. Т. Веденьев, А. А. Воронцов. – Москва: Горячая линия - Телеком, 2012. – 550 с. – Режим доступа: [Ссылка]
- Что такое атака Man-in-the-Middle [Электронный ресурс] – Режим доступа: [Ссылка]
- Taekyoung Kwon, Jooseok Song. Efficient and secure password-based authentication protocols against guessing attacks. Computer Communications, Volume 21, Issue 9, 1998, pp 853-861 – Режим доступа: [Ссылка]
- Gong, L. Efficient network authentication protocols: Lower bounds and optimal implementations. Distrib Comput 9, pp 131–145 (1995) – Режим доступа: [Ссылка]
- Roger M. Needha, Michael D. Schroeder. Using encryption for authentication in large networks of computers. Communications of the ACM, Volume 21, Issue 12, Dec. 1978, pp 993–999 – Режим доступа: [Ссылка]
- Шапиро, Л. Аутентификация и одноразовые пароли. Теоретические основы. Часть 1 / Л. Шапиро // Системный администратор. – 2012. – № 9(118). – С. 88-91 – Режим доступа: [Ссылка]
- Титов, В. С. Идентификация и аутентификация. Способы и методы аутентификации / В. С. Титов // Международная научно-техническая конференция молодых ученых БГТУ им. В.Г. Шухова, Белгород, 01–20 мая 2017 года. – Белгород: Белгородский государственный технологический университет им. В.Г. Шухова, 2017. – С. 4514-4519. – Режим доступа: [Ссылка]
- Грищенко О. С., Усовершенствование алгоритмов аутентификации и исследование его эффективности при использовании в распределенных системах, Донецкий национальный технический университет, 2018 – Режим доступа: [Ссылка]
- Чернышова А.В., Афанасьева А.А. Методы безопасной аутентификации в клиент-серверных приложениях // Программная инженерия: методы и технологии разработки информационно вычислительных систем (ПИИВС2022): Сборник материалов IV Международной научно-практической конференции, г. Донецк, 29-30 ноября 2022 г. – Донецк: Донецкий национальный технический университет, 2022 – С. 74-80. – Режим доступа: [Ссылка]
- Афанасьева А.А., Чернышова А.В. Формирование требований к протоколу аутентификации // Интеллектуальные системы и программирование (ИУСМКМ-2023): Сборник материалов XIV Международной научно-технической конференции, г. Донецк, 24-25 мая 2023 г. – Донецк: Донецкий национальный технический университет, 2022 – С. 62-66.– Режим доступа: [Ссылка]
- Security Assertion Markup Language (SAML) [Электронный ресурс] – Режим доступа: [Ссылка]
- PAKE [Электронный ресурс] – Режим доступа: [Ссылка]
- The SRP Authentication and Key Exchange System [Электронный ресурс] – Режим доступа: [Ссылка]
- OPAQUE: An Asymmetric PAKE Protocol Secure Against Pre-Computation Attacks [Электронный ресурс] – Режим доступа: [Ссылка]
