Choose language:
- RU
EN
Dissertation
- Biography
- Dissertation
- Library
- Links
- Individual task
- Report of search
Digital watermarks in IT-technologies
- Actuality
- Introduction
- Digital watermark for DVD
- Container types
- Algorithm of inculcating DWM in a static image
- Presentation
- Links and notes
Actuality
Actuality of information protection leaves for a long time.The science steganography and digital watermarks are newer, that's why many questions are not received and there are a lot things for reasearching.
Introduction
Development of information technologies has led to the wide usage of digital photos, DVD film and music in a format mp3. Therefore there was a practical sense of information protection. So steganography as a direction in IT became an important part. Steganography is a method of the content organization which actually hides presence of content. Methods of steganography allow building in confidential information (messages) in harmless messages so that it’s impossible to suspect existence of the built in secret message. The word "steganography" in translation from Greek means (steganos - a secret, secret literally; graphy - recording). The huge set of a confidential communication facility concerns to it such as invisible ink, micro pictures, a conditional arrangement of signs, secret channels and a communication facility on floating frequencies, etc. Steganography occupies the niche in a safety: it doesn’t replace but implement cryptography. Concealment of the message by methods of steganography considerably reduces probability of detection of the fact of transfer of the message. And if this message besides is ciphered, it has one more, additional, a level of protection. Now in connection with rapid development of computer facilities and new channels of transfer of the information have appeared new steganographical methods in which basis features of performance of the information in computer files lay, computer networks, etc. It enables us to speak about becoming a new direction in computer since is computer steganography. From digital steganography the most claimed legal direction is the embedding of digital watermarks being a basis for systems of protection copyrights. Methods of this direction are adjusted to embedding of the latent markers, steady against various transformations of the container (attacks). In result it is necessary to build the information not only it is not appreciable but also so that she was steady against various kinds of attacks.
 Paint.1 Typical scheme of stegosystem
Paint.1 Typical scheme of stegosystem
- precoder is the device intended for transformation of hiding message to a kind, convenient for embedding in the signal - container (the container the information sequence in which the message is hidden is called);
- stegocoder is the device intended for realization of an investment of the latent message in other data in view of their model;
- device for seeking stegomessage
- stegodetector is the device for definition of presence stegomessage;
- decoder is the device restoring the latent message.
Let's pass from the common circuits to concrete examples of embedding of digital watermarks. Digital watermarks can be built in:
- dvd;
- images;
- video;
- music;
Digital watermarks for DVD
The concept of watermarks on DVD is a presence of some regular going distortions at video and at audio files. These distortions are imperceptible for the vestibular device of the person. They can carry the various information including information license. On not licensed copied disk these watermark disappears. At the licensed copying change together with the changes number of disk’s copies. It allows consumers to consider, whether it’s a license product or only a copy. By means of watermarks it is possible to carry out the control of playing also. The example of protection can be an interdiction of reproduction of disks without watermarks and the control of recording.
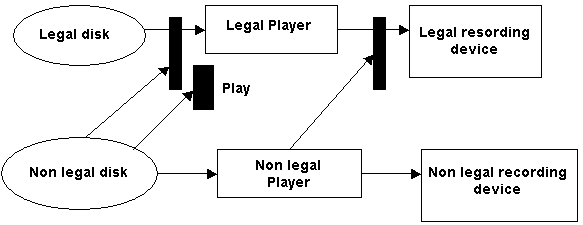 Paint.2 – Scheme of DVD protection
Paint.2 – Scheme of DVD protection
Container types
Essential influence on reliability and stability stegosystem, and also an opportunity of detection of the fact of transfer of the latent message renders a choice of the container. The most skilled designers with perception{recognition} of color scale of the greater, than at the usual user at introduction of the message in images can notice the given container. Therefore with a choice such as the container it is necessary to be cautious. Thus, containers can be subdivided into two types:
- Continuous;
- Fixed size;
 Paint.3 – Scheme of protection of multimedia files
Paint.3 – Scheme of protection of multimedia files
Steganographical methods used for embedding of the information in video, compressed according to standard MPEG demand job in real time and should possess small amount of calculations. The stream of the video data in MPEG has hierarchical structure. The sequence of the videodata is divided on some set of groups of the staff representing set of the video staff of the following one after another. The staff in turn shares on layers and macro blocks. The lowest level will consist of blocks of brightness and chromaticity. Thus, operating with blocks of brightness and chromaticity it is possible to achieve embedding Digital Water Marks. There are many methods of embedding of the information in video, namely:
- Embedding the information at a level of factors;
- Embedding the information at a level of a bit plane;
- Embedding the information at the expense of a power difference between factors;
Algorithm of introduction Digital Watermark in the static image
The 24-bit image of format JPEG or BMP has the RGB-coding. Embedding is carried out in the channel of dark blue color as the system of human sight is least sensitive to dark blue color. So has developed that the range of colors achieves approximately 16 million but a human eye in dependence from a profession can see from 1 up to 4 million colors. The common circuit of chromaticity can be described schematically so:
R (red) - human eye catches 7 bits from 8;
G (green) - human eye catches 8 bits from 8;
B (dark blue) - human eye catches 4 bits from 8;
B (dark blue) - human eye catches 4 bits from 8;
According to it it’s possible to do conclusions that to blue color the human eye are least susceptible. This advantage allows building in information in the field of dark blue color. But its property can use and optimizers the size of a picture. It is possible to cut off the unused bits to be exact invisible to an eye of the human. But we shall pass to the theory. We shall consider algorithm of transfer of one bit of the classified information.
si - built in bits
I = {R, G, B} - the container
p = (x, y) - a position in which the investment is carried out.
Confidential bits are built in the channel of dark blue color by updating brightness with the help q - a constant determining energy of the built in signal. Its size depends on applicability of the circuit.
Extraction a bit of the addressee is carried out without presence of the initial image. For this purpose the prediction of value of the initial unmodified pixel is carried out on the basis values of neighbors. For reception of a rating pixel it is possible to use values of 2 pixels located on the right and to the left of estimated in same line. At use of an initial file value built in the bit is defined is familiar to a difference of values for the coded and not coded image.
A presentation of usage digital watermarks and it's actuality (This presentation shows you that you are not allowed to use other people images because they can be protected by unseeing digital watermarks.)
| © Antony Khotov 2006 |