Theme of master's degree work:
«Research and development methods of cryptographic defence information»
Author: Polovenko Yan Igorovich
Abstract of thesis
In my work application of methods of cryptographic defence of
information is examined at creation of the coding file systems and their
further introduction in the kernel of the operating system. These
methods allow to accelerate creation of such systems, and also to bring
in in their development terms, allowing effectively to protect
information from an unauthorized division with the minimum loss of the
productivity.
For
realization of methods it is suggested to utillize the coding file
system (Encrypting file system, EFS), architecture of which is developed
with a help Windows CRYPTOAPI. In its basis technology of coding lies
with the opened key, in obedience to which for every file casual
appearance is generate the key, any symmetric algorithm can be used in
this connection . Presently utillized only one - DESX, being the special
modification of widely widespread standard of DES [1].
EFS codes
information utillizing a chart with the general key storage of which
takes a place in the resident pool of memory (the system is located in a
kernel Windows2K/XP/Vista), that eliminates access to it through the
file of pumping [3]. FEK - it by casual appearance the generated key of
certain length, its size in a north-american version was 128 beaten, and
in an international version got out between 40 and by 56 bats.
FEK is coded
one or a few general keys of coding, the list of FEK, which is kept in
the special attributes of EFS, DDF (data decryption field is the field
of decoding of information) and DRF, turns out as a result (data
recovery field is the field of renewal of information). Information
which coding of information is made through is hardly related to this
file. The general keys are selected from the pair of user, certificate
of X509, with additional possibility of the use of «File encryption», and also from a few written down in the policy of renewal of in cipher
information for this computer, with additional possibility of «File
recovery». The personal keys from these pair are used for decoding of
information and FEK, part is kept either on smart cards or in other
reliable place (for example, in memory safety of which is provided
through CRYPTOAPI) [2], and the agents of renewal can keep them in a
safe place out of the system.
EFS executes
four basic operations with by files which utillize ordinary Win32API: opening, reading, record and transformation. At planning of process of
transformation of files consists a main requirement in that, to
eliminate the loss of data even in case of setting off feed or other
failures.For this purpose the careful going is utillized near storage of
back-up copies of the deciphered information which are saved until
transformation will not be completed fully.
For providing
of transparent work of service EFS its components must be present on
many levels of the operating system, here utillizing intuitional-clear
man-machine interface. Components can be divided into two groups:
workings in the user mode and mode of kernel, their intercommunication
is shown on Pic.1.
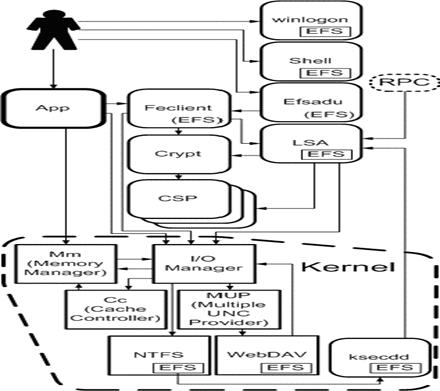
Pic.1. Intercommunication of the operating system and EFS
On the whole, EFS provides acceptable defence and confidentiality of
files, its components are successfully projected, realized and
repeatedly utillize an existent code, speaking to the system API at a
management the keys and certificates. It successfully gets along at
cleaning of resources on completion of their use and renewal after
system errors, arising up at implementation of operations. It is
important to mark that EFS not utillized for providing of integrity of
files and defence on the basis of authentification, developers
consciously went on a compromise between absolute safety and comfort.
During realization of such methods of cryptographic defence of
information there is a row of advantages: use of rapid and reliable
algorithms of coding, integration with a graphic shell, transparent
access to the protected files, low cost of development.
Conception of
the probed defence of information, is innovative, because the systems of
such type yet are only developed. Because of what it is needed to notice
that if to take into account all of lacks of these methods of defence,
such systems will be able to utillize not only professionals but also
ordinary users, and also will be much more reliable and less dear, what
other similar type. To date, this method of the coding file systems is
large scientific interest and space for development of such type of the
programs.
Banner on the theme of master's degree work
Literature
[1] The Microsoft Windows Vista Driver Development Kit (DDK) [Электронный ресурс]: Справочная система — Microsoft, 2006.
[2] MSDN Library [Электронный ресурс]: Справочная система — Microsoft, 2006.
[3] Solomon D.A., Russinovich M.E. Inside Microsoft Windows 2000[Электронныйресурс]: Справочная система – 2000.