INTRODUCTION TO RFID
The Purpose of my research job is creation of the monitoring system and restriction of access to a premise on the basis of contactless reading and identification of radio-frequency labels (RFID).
RFID is the technology, that allow to pass and receive the information from identified objects on a radio channel, without direct visibility or physical contact between the input reader and the identifier.
Owing to presence of these two conclusive advantages before others, RFID gradually supersedes such "dying off" technologies of identification, as a stroke-coding and magnetic maps.
RFID-identifiers not only are more convenient in application, but also can store in itself more information, allow to use various systems crypting data for copy protection and falsifications.
At given stage RFID of technology intensively develop and cover all new spheres of a life of people and public work as a whole. It, basically, also causes the growing responsibility assigned to methods of radio-frequency identification. The need for development of new methods of enciphering of data, for development and improvement of channels of asynchronous data transmission, for use of algorithm of coding with the open key grows.
the Review of existing researches
Protection of automobile trailers against stealings
In the Great Britain automobile hook-on small houses-vans of type "caravan" are widely widespread. Annually them is on sale up to 24 000 pieces at the price of from 6 up to 25 thousand pounds sterling. Their safety first of all anxious the insurance companies, therefore described below the protective scheme for automobile owners is realized free of charge. At manufacturing to each small house-van the unique identification code VIN consisting of 17 alphanumeric signs is appropriated. This code is registered at sale together with data about the owner of a small house in the special association consisting of 35 firms-manufacturers of vans, 100 dealer companies and 550 parking places.
Since 1998 the scheme of marks of small houses is introduced. Identification code VIN is put by a method of chemical etching on all glasses with simultaneous duplication of this information in memory of a radio-frequency label. The passive radio-frequency label of type WORM of development company TIRIS (Texas Instruments, Northamptron, UK) has the sizes of a credit card and possesses programmed memory in capacity of 1360 bits (about 170 alphanumeric signs).
The label is established inside of a van at assembly at a factory. Data about the owner unitary enter the name in memory WORM during the moment of sale and after that cannot be changed any more. Even if jacker a van will replace all glasses with others with own engraving, he cannot change a code of vehicle VIN and data about the owner in memory of a radio-frequency label. In turn this information is read out from a label distantly at movement of a van by a post of a traffic police. If data about stealing are available in a police computer, the disturbing signal will be automatically given out. Besides, if code VIN on glass of a van mismatches data readed from a radio-frequency label, the automobile owner will excite attention of police.
the Control of movement of public transport
The Italian company transporting passengers public transport in Turin (Italy), has commissioned the monitoring system behind movement of 900 buses belonging her and 300 trams. In her devices RFID of development Confident, TAGMASTER and Kista (Sweden) are used. Turin became the third Italian city which has got the specified system.
The small radio-frequency label is established by each bus and a tram. At returning the bus from a route the central computer (ordinary the simple PC) on a signal, readed from a label, automatically registers date and an arrival time.
At an output on a route registration repeats, thus the driver sees identification number, numbers of the bus (tram) and a route, displayed on the big screen about a gate of park. The driver does not need to stop or pass in immediate proximity from the input reader: the labels working in a frequency range of 2,45 GHz, allow to read out from them the information on distance up to 6 meters. The system allows to plan optimum loading of drivers of buses and trams and to supervise timeliness of an output on a route and returnings from a route.
Electronic marks of the goods in trade
Company Sainsbury's Supermarkets (Great Britain) possessing a network from 381 supermarkets, has made a decision on electronic marks of the goods. The technology of radio-frequency identification CHECKPOINT SYSTEMS (Harlow, UK) is used. Small size labels RFID thickness about a leaf of a paper have been pressed into pack of the goods at a stage of their manufacture. In shops detectors of protection against thefts on inputs and outputs of a trading hall are established. Detectors find out presence of a radio-frequency label and publish an alarm signal. Deactiveting labels are located at the cashier.
Standard scanners of a shaped code 2010 series Scantech (Holland) are modified by special image and allow instead of traditional two consecutive operations of reading of a code of the goods with the subsequent removal of protection to carry out one, uniting both specified functions. The system has proved the efficiency. First of all the goods from group of risk (the most subject to thefts), and also the goods in expensive section are marked. The marked and not marked goods do not differ on appearance (the code is visible only shaped, but it is not known, whether have been pressed into a label in packing and in what place). Application of the specified scheme reduces an operating time of the cashier and total of the control equipment in a trading hall. It is planned to translate all of 100 % of the goods on marks by radio-frequency labels.
The similar system under the name "Albatross" is developed for trading companies El Corte Ingles (Spain) on technology of firm PHILIPS. Jobs are begun by autumn of 1996 and is planned to reach within 5 years position at which 30 % of all goods will be supplied by labels RFID. Labels of type R/W with internal memory of 512 bits in which unique number of a label (64 bit) and a place for the information of the user (384 bit) is placed are used. Data are guarantee saved in memory within 10 years. The sizes of a label - 5х5 sm, effective range up to the input reader - 1,2 m, working frequency of 13,56 MHz, speed of job of the input reader - 20 labels in a second. Function of an anticollision is realized: labels of the same goods are selecting also do not mix up in registration system. For struggle against thefts against two parties of pass to a hall aerials of the input reader are established (only 2), thus the width of pass reaches 1,5 meters.
Control access
According to magazine "IT Reseller" from total of systems RFID of 16 % sold in the Europe make monitoring systems of access. Schemes of job are simple enough: the radio-frequency label with data of the employee is as a matter of fact the electronic miss made of a charm for keys, a firm badge, a bracelet or even a dial for a watch ("STId" FRANCE). Input readers of radio-frequency labels are established on turnstiles at an input in a building of the company, and also on doors of premises with the limited access of employees. It is enough to have only at itself the electronic miss that the code was readed, it is checked up by a computer, it is compared to the list of employees by which the admission is resolved and simultaneously with automatic opening doors it is noted in memory of a computer with the instruction of a post, a surname and the initials of the employee, and also date and time of pass. Lack of system can be pass of group under one miss which is eliminated by installation of turnstiles and the visual control over service of supervision.
The List of problems solved in job (+ novelty and so forth)
In RFID technologies there are many advantages doubtless, however it is necessary to realize that the sphere of its application can be various. Moreover, the same label can be as a key to one or several different doors, as a key of your car ignitions and even the tool of payment of the goods and services. It is natural, that such important things lead us to a question about safety, safety and protection of the property and private life as a whole.
If we are talking about use of RFID-keys for the control and access restriction to a premise, the most important and significant problems which it is necessary to solve it in job:
- To lower “scan liability” and to raise security of radio-frequency labels from copying. The choice and-or system engineering of the coding, allowing to protect a label from copying by any scanner.
- To provide simultaneous reading. Simultaneous reading of several labels without acceptance of additional measures and introductions of additional development can lead to that signals of two labels will be imposed one on another.
- To study susceptibility to handicapes in the form of electromagnetic fields
Systems RF of identification can be sensitive to handicapes in the form of electromagnetic fields. Therefore it is necessary to analyse carefully conditions in which system RFID will be maintained and develop necessary measures of counteraction.
- To consider influence of an electromagnetic field on health of people. Radio-frequency labels do not represent risk for health as 99, 9 % of time they are not active. And here input readers are a radiator of an electromagnetic field which influence, in turn, is a subject of many disputes and discussions of researchers of all world.
Developments in sphere of safety RFID
Theoretical problems of safety RFID
High technologies which are used with a society first of all should be safe for this society. It is necessary to develop decisions and to not admit, that RFID it would be possible to use in harm to the consumer. On this bill it is conducted much discussion and algorithmic decisions are searched concrete both technical, and. But theoretically all researches leave the basic theoretical ways of "breaking":
One of such experiments is described in clause Vulnerabilities in First-Generation
RFID-enabled Credit Cards (Thomas S. Heydt-Benjamin, Daniel V. Bailey,
Kevin Fu, Ari Juels, and Tom O'Hare).
A latent reading
Such type of attack assumes, that the label can respond to reading from extraneous reading.
I.e. in the elementary variant - someone can read on distance of several meters the information from all RFID-labels in your pocket. Certainly not 100 %, but very effective and obvious variant - to add the button of activation on a label (the button to disconnect the circuits of a feed). One more variant - to reduce a range of reading.
Protecting the information not only to equipment rooms, but also program methods it is offered to close access to each sector in individual pair keys.
Interception
The given type of attack consists in usual record of all proceeding data of a RFID-label, for the subsequent emulating the given label. Therefore it is necessary to use any system with changing key access. For example three-pass authentication. The algorithm of such system looks so:
1). The input reader specifies sector to which wishes to get access and chooses one of keys.
2). The label reads a confidential key and conditions of access to sector from
Trailer. Then the label sends a random number to the input reader (a stage 1).
3). The input reader calculates the answer, using a confidential key and additional
Value. The answer together with casual value from the input reader is passed a label
(A stage 2).
4). The label checks the answer of the input reader, comparing it with own
Variant. Then calculates the answer to a call and passes it (a stage 3).
5). The input reader checks the answer of a label, comparing it with expected.
After transfer of the first random number communication between the input reader and a label
It is ciphered.
The main advantage in such authorization is that a key
It is not passed on a radio channel. After authorization all operations with memory
Labels also are ciphered. Thus, "having overheard" the interface between a label and
The input reader during transaction, it is possible to receive only a set of byte.
Copying of the open data of a label
If as the registered and compared identifier to use factory ID number of a label the system will turn out more vulnerable as factory ID is the open information in various executions of system such information probably to use not to destination. It can be avoided using for this purpose the protected area of memory of a label or duplication ID of a label
Offered decisions
I consider, that the theory of cryptography - opened and closed can be applied by a method of pairs keys with success to enciphering data at data transmission on a liaison channel " the Input reader - the Label ".
all over again one party generates, using algorithms of enciphering with the open key, the pair keys (opened/closed) and is passed the second party with the open key;
then the second party generates (by means of methods of enciphering with the closed key) a confidential key, ciphers it by means of the open key sent by the second party (using methods of enciphering with the open key), and passes the ciphered confidential key to the first party;
the first party deciphers a confidential key by means of the closed key (still using methods of enciphering with the open key);
now both parties own a confidential key, which they use for enciphering the messages (enciphering with the closed key) during all session of communication.
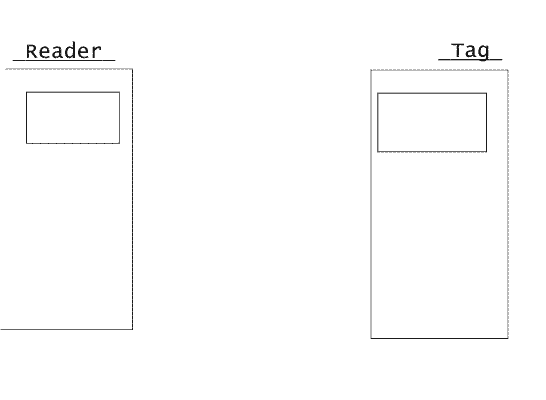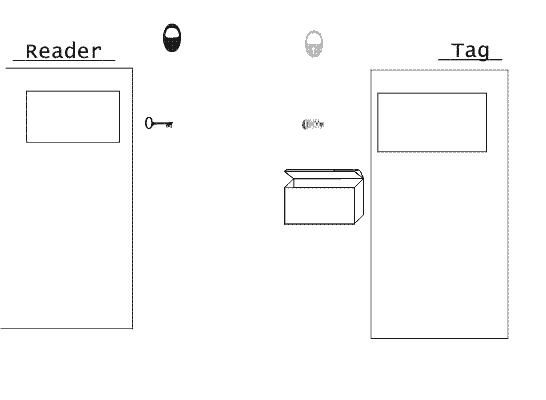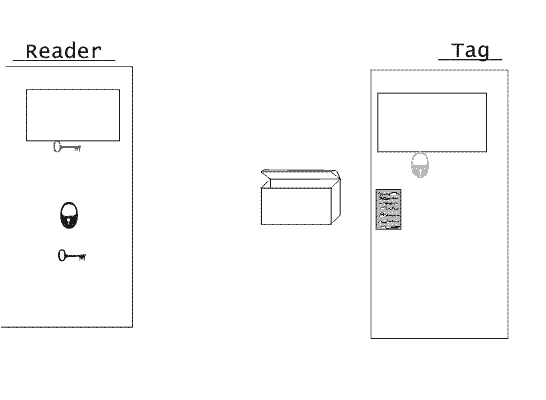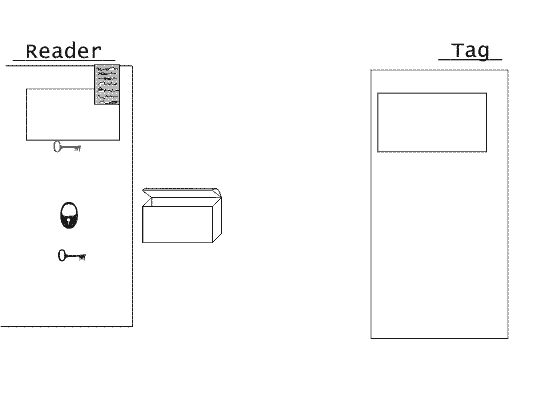
Parameters of GIF-animation:
the Size of a file - 52,5 KB
the Size of the image - 546 X 400 pixels
Quantity of colors - 4
Quantity of the staff - 23
Quantity of repetitions - 4
Duration of a cycle - 27,5 with
There is one more widely known algorithm with the open keys, allowing to generate one general confidential key for enciphering given by two parties without its transfer on a liaison channel. The algorithm is based also on use of pair keys: opened/closed.
Both parties generate the pairs keys and exchange then open keys. The essence of algorithm consists that pairs keys are generated by such rules, following which each party of a combination: the confidential key and a opened key of the partner can receive a unique key (identical at both parties!) which they can then use for enciphering messages by a method of enciphering with the closed key.
This algorithm is called as algorithm of the open distribution of keys, or - on names of authors, researchers from Stenford university – Diffy-Helmann algorithm.
Other researches and experiments
Researchers of one of leading firms on protection of the information have developed technology of blocking for those who is strongly concerned by infringement of the rights to inviolability of private life at use of labels-transponders. The laboratory of company RSA Security has promulgated plans on development of the technology named "blocking labels" (blocker tags) which at cost and the size is similar to RFID-tags, however allows to interfere transfers of the information on the scanner and stirs to data gathering.
Researchers of one of leading firms on protection of the information have developed technology of blocking for those who is strongly concerned by infringement of the rights to inviolability of private life at use of labels-transponders. The laboratory of company RSA Security has promulgated plans on development of the technology named “ blocking labels ” (blocker tags) which at cost and the size is similar to RFID-tags, however allows to interfere transfers of the information on the scanner and stirs to data gathering. While the technology operates only in the laboratory conditions, however following step becomes creation of the operating sample and definition of a degree of interest of manufacturers in creation of similar processors.
As is known, the technology of radio-frequency identification passes data about object to accepting device without participation of the person and can be applied to a mark of the goods and things with the purpose of decrease in their larceny, lost, etc. However groups of defenders of human rights have expressed concern in connection with that use of such labels will allow to interfere with a private life of citizens, tracing their movings by means of the marked things. Built in at o'clock or a bag blocking tool will extinguish a radio signal and, accordingly, movings of a subject will be unknown.
It only one of ways of preservation of confidentiality of a private life at use of radiolabels. There is also a variant of addition in radio beacon functions of self-destruction, however such way excludes an opportunity of its further use.
To sum up or a little bit about private life:
As to consider the information from tags it is possible on distance in some meters, they represent obvious and direct threat for preservation of its confidentiality. That is why defenders of the civil rights and freedom consider, that distribution RFID can lead to inadmissible intrusion into a private life.
They are afraid of not authorized use of such chips behind walls of shop: the malefactor owning reading out device, can prohonour identifiers of your things and use the received information against you (for example, having cracked a database of the necessary shop and having learned number of your credit card). To put it briefly, not to destination besides it is a lot of variants of use RFID. Prospects of such initiative are obvious: the state can learn all about the citizens. Moreover, by means of radiolabels it is possible to organize total shadowing.
On 22-nd congress of known community of German hackers Chaos Computer Club taken place Berlin one of reports has been devoted to a popular method of deactivation of chips. However manufacturers RFID up to now and did not have enough convincing stimulus (like the state laws) for inclusion in the chip of means of its deactivation ("murder") after sale. For this reason two German skilled craftsmans have laid down to themselves the aim to develop the simple means of constant deactivation RFID-Zapper operating by a principle "has died, so has died".
Created by Germans tiny RFID-Zapper operates by a principle of microwave owen, generating electromagnetic radiation which capacity allows to burn out some electronic components, but leaves an external environment of the chip practically intact. To make « Zapper » extremely cheap, it has been decided to make it on the basis of a disposable film camera with flash as such "soap trays" sell practically everywhere under the below cost price. For generation of an impulse the coil from a copper wire serves. It place inside of the device on a place of a film then the case of the chamber is closed – and "murderer RFID" is ready to job from a usual battery. Designers have repeatedly tested the child, "having destroyed" all available them available RFID, and now prepare for the detailed documentation of the device which promise to lay out in an easy approach.
From all above-stated it is obvious, that RFID systems can essentially relieve us of superfluous vanity and expenditure of time. However it is necessary to concern very closely to a question of maintenance of safety and safety data on a label. And if you do not wish "to share" details of your life with other people - it is not necessary to trust without corresponding protection them and RFID.
Directions and prospects of the further researches:
The Most promising direction in safety RFID - development firewall. It is supposed, that such firewall will automatically block all radiochips for reading and opens necessary of them only when it actually is necessary. It is offered to build in the module of safety devices like a handheld computer or cellular telephones that the person had not to hammer even more in the pockets electronics. Such approach is more convenient also that for administration of firewall it is possible to use the display of the mobile device.
As the majority of RFID-input readers is not calculated on firewall use or other similar devices. Therefore the firewall constantly scans an ether for connections and not only protects your data, but also conducts broad gullies – who, when also what exactly wished to consider. At presence of inquiries breaking safety, such firewall intercepts packages of data from the chip and sends instead of them own, not containing the confidential information.
Sources:
S. Cherepkov // "Стандарты и тенденции развития RFID-технологий", "Компоненты и технологии" № 1, 2006
М. Fedorov // "Технология RFID. Опыт использования и перспективные направления., "Компоненты и технологии" №9, 2005
M.Gudin, V.Zaycev // "Устройства радиочастотной идентификации компании Tagsys", "Компоненты и технологии" №6, 2003
M.Gudin, V.Zaycev // "Технология RFID: реалии и перспективы", "Компоненты и технологии" №4, 2003
| 
