Abstract
Research of interactive methods of identification in technical protection of information
A. DyrulIntroduction
Identification cards - are tools establish the identity of human personality traits to set them through a comparative study. Depending on the object identification and its features apply a variety of methods. for example, using the method of fingerprinting based on the identification of individual unchanging features of papillary patterns of skin palmar surface of the nail phalanx of fingers, the method of verbal portrait - a description of a person's appearance and its special features of the standard terms. Verbal portrait includes a description of static characteristics (shape and other features of the face, eyes, nose, ears, etc.) and dynamic features (especially gait, gestures, facial expressions, etc.). Features of gait can be installed and footprints (lane signs while walking). An important part of verbal portrait are distinctive features. These include birthmarks, warts, scars, signs of an illness or injury, structural features of dentoalveolar apparatus, tattoos, etc. Use also measure the length of the body, feet, head circumference, chest, shoulder width, etc. [1].ID cards are widely used in information security in the form of biometric algorithms, whose work is based on comparing the facial image, iris, fingerprints, voices, ears and nose shape.
Study Objectives
The purpose of master's work is the improvement of facial recognition algorithms and images. To achieve this goal should be to:- Analysis of algorithms for recognizing facial images, auricle;
- Simulation of the algorithms of image recognition of face and ear under different conditions of work;
- Conducting pilot studies and vulnerability scanning algorithms;
- Offer ideas on the implementation of algorithms in TZI.
Relevance of the topic
For identification, we use the biometric data of the person, they are unique to each person. To date, sold a large number of different methods and algorithms based on biometrics, but they all have various drawbacks such as the dependence of the accuracy of identification of illumination of the object (face, hands etc.), age-related changes of retina, etc. , as a consequence of this is significantly reduced accuracy of the algorithms. To solve this problem using several techniques, which are also not always provide high reliability, which is a fundamental factor.Relevance of the use of biometrics to date is large and can be used everywhere, such as changing passwords to access confidential information, which is recommended to use a sufficiently complex to fit them, as a rule, it is difficult to remember and store such data on paper or other media is not safe.
Alleged scientific innovation
Joint application of algorithms for pattern recognition and voice to enhance the reliability of the system as a whole.Implementation of the studied algorithms in hardware data protection.
Algorithm for pattern recognition
Used for work are two basic filter algorithm minimum average correlation energy (MACE filter) [2] and Local Binary Patterns (LBP) [3].The principle of MACE filter is to minimize the average correlation energy on the basis of pre-prepared images. Minimize the effect is that the correlation coefficient is zero on the whole image except for areas that coincide with prepared images, it is in these areas, the degree of correlation more. Figure 1 shows the principle of the MACE filter.
It is obvious that for this algorithm requires a database of images (pre-prepared images) with which to calculate the degree of correlation. For optimum performance it is desirable that the base on a given personality is a relatively large amount of facial images in different lighting conditions and changes in facial expression. This will provide greater accuracy.
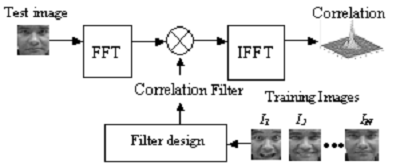
Fig.1 The principle of MACE filter.
Local Binary Patterns (LBP) are a popular technique for face recognition, as well as to recognize the image as a whole. Recently, LBP has been applied to specific problems face recognition. LBP has a nonparametric kernel which handles the spatial structure of images. In addition, it is invariant to monotonic gray-scale transformations, therefore, the implementation of LBP is less sensitive to changes in illumination. This is an interesting property in face recognition. Indeed, one of the main challenges in face recognition systems is to deal with changing light conditions.
In practice, it is very important, lighting conditions are verified
images do not meet the requirements of the gallery (database) of images, therefore, there is a need to handle such changes.
Let's consider some options for working LBP algorithm.
Net LBP method.
LBP is a description of the vicinity pixel of the image in binary form. Operator (LBP), which is applied to the image pixels, uses eight pixel neighborhood, taking the central pixel as the threshold. Pixels that have values greater than the central pixel (or equal to) take the values "1", those that are less central, take the values "0". Thus the eight-bit binary code is obtained, which describes the neighborhood of a pixel. Figure 2.
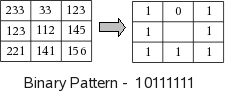
Fig.2 Description of the LBP
In decimal form resulting octal word (LBP code) can be represented as follows:
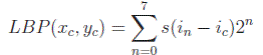
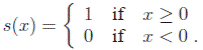
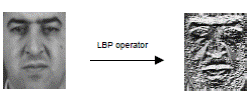
Fig.3 Original image (left) are handled by the operator LBP (right).
Because of its texture, LBP is not difficult to implement and yavlyaetsyas popular in pattern recognition. Recently, LBP has been applied in the works for face detection, face recognition, image retrieval, motion detection and visual inspection.
Scalable LBP
Ojala et al. expanded the original LBP operator to a circular neighborhood of the different size range. Their LBPp, r increases the distance p equally spaced pixels on a circle to the radius of k. For example, the operator's work LBP8, 2 are shown in Figure 4.
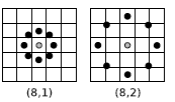
Fig.4 An example of a scalable operator LBP
Uniform LBP
In his works, Ojala et al note that most of the information contained in a small group of LBP models. These models, called the uniform model and contain at most two bitwise 0 to 1 or 1 to 0 transitions (circular binary code). 11111111, 00000110 or 10000111prednaznachenyh for uniform models. They are basically primitive micro-features such as lines, edges, corners. LBPu2p, r denotes the extended LBP operator only for uniform models.
Improved LBP
In recent years, new expansion of LBP. For example, Jin et al. noticed that the lost features of the local structure of LBP in certain specific circumstances, so they have introduced improvements to the Local Binary Templates (ILBP). The main difference between ILBP and LBP is a comparison of all pixels (including the central pixel) with a mean value of all pixels in the nucleus (Fig. 5). As a result, 9-bit word (ILBP code) decimal form can be expressed as follows:
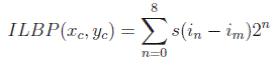
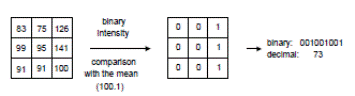
Fig.5 Calculation code ILBP
Huang et al. indicate that LBP represents only basic information about the derivation of the image, but may not reflect the rate of local variations. To solve this problem, they proposed an extended version of local binary patterns (ELBP), which encodes the image gradient magnitude, in addition to the original image. For this purpose, apply the kernel LBPu28, 1, LBPu28, 2 and LBPu2 8,3 as the original image and the gradient. As a consequence, this method can not be seen as extension of LBP.
Census transformations (Census Transform).
This method was proposed simultaneously with the LBP, which was introduced by Ojala et al His feature, called the census transform is different from the LBP only in order of bit lines. Later census transform has been extended, but it is worth noting the similarity with the extensions for LBP [3].
Algorithms to recognize individuals by ear
Enough new algorithms that perform well. It is known that the pinna (SD) final sformirovyvaetsya before birth, and in the process of life continues to grow while maintaining its shape. The form of the ear, each person individually. For the algorithm method is used SIFT, which is used for comparison of images and reduces to finding critical points.Detection of specific points made by the construction of the pyramids Gaussians (Gaussian) and the differences of Gaussians (Difference of Gaussian, DoG).
This method has shortcomings, which manifest themselves in low-light ear on the analyzed images.
Implementation of the system identification
To ensure system stability, accessibility, interactivity Next structure implementation Fig.6.
Fig.6 - Structure of the recognition of images (animation: Volume - 40,5 KB, the number of frames - 9, the delay before repeat 0 with., The number of cycles of repetition-7, correct size - 595x170)
For decision-making mobile devices are equipped with software implementations of the above mentioned algorithms. A feature of this structure is scalability, which depends on the computational capabilities of the server. It is worth noting that the implementation of the algorithm LBP and MACE filter does not require large computing power.
The research results
As a result, studies have found that using the MACE filter and Local Binary Templates, is not sufficient, but the best. In the case of MACE filter error Face Detection (> 2%), which is essential, and it is worth noting the heavy reliance of the work on the lighting. To increase the accuracy of identification is added to the use of LBP method. As a result, 90% of the identification was successful. Identification technique for ear provides a high percentage match. In the case of joint use of the three algorithms, the probability of correct recognition is stabilized vzaimoisklyuchaya inaccuracies of the algorithms used.Possible compromise of the algorithms by using a 3D model of the head created by a 3D printer. The probability of false alarm algorithms is close to 100%, as well as during the testing of software products, it was noted that the primary indication of the identity is stored in clear text, so can be a substitution data.
Conclusion
Face recognition requires a reliable mechanism to work, which may be provided by the proposed algorithm. It is worth noting that it is not always advisable to use a large number of algorithms, so as to increase the probability of detection is not significant. This system realizes the significance for the practice functions: the recognition is performed in real time.Perhaps autonomous decision-making, as well as with a trusted person who manages the GSM channel.
References
[1] [Network Encyclopedia] http://dic.academic.ru/dic.nsf/enc_medicine/12320/Идентификация[2] Face Verification using Correlation Filters
Marios Savvides, Electrical and Computer Eng. Dept, Carnegie Mellon University Pittsburgh, PA 15213, USA
B.V.K. Vijaya Kumar Electrical and Computer Eng. Dept, Carnegie Mellon University Pittsburgh, PA 15213, USA
Pradeep Khosla Electrical and Computer Eng. Dept, Carnegie Mellon University Pittsburgh, PA 15213, USA // http://www.ece.cmu.edu/ ~ kumar / Biometrics_AutoID.pdf
[3] On the Recent Use of Local Binary Patterns for Face Authentication
S 'bastien Marcel, Yann Rodriguez and Guillaume Heusch // http://www.idiap.ch/~marcel/professional/publications/marcel-ijivp-2007.pdf
[4] On guided model-based analysis for ear biometrics. Banafshe Arbab-Zavar, Mark S. Nixon. School of Electronics and Computer Science, University of Southampton, UK. //
http://eprints.ecs.soton.ac.uk/20973/1/arba-zavar-cviu.pdf
[5] [IT social network] http://habrahabr.ru/blogs/algorithm/106302/