Abstract
In this paper is proposed an algorithm to ensure information security in a computer network. The algorithm is based monitoring of information flows between workstations of employees and external devices connected to USB.
The relevance of the proposed approach – to monitor the implementation of internal and external flows of the enterprise data to maximize the confidentiality of internal information.
The scientific novelty of the work is to develop a predictive algorithm for filtering information streams that are transmitted from / to USB-devices. Filtering algorithm provides the possibility of isolating specific information on a wide range of parameters (or file name of the process, the mask data, date / time of the read / write, etc.).
The practical value of the proposed algorithm is to develop a client-server program-spy which provides control, management and collection of statistics on workstations connected to the USB-devices of employees, as well as the content of information flows coming from them.
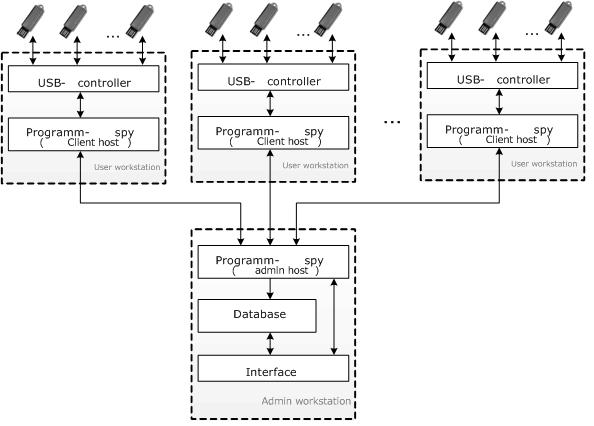
Within the analysis of user data streams from USB-devices has been implemented algorithm for identification of devices that can be used to determine the parameters and characteristics of the devices that are connected to USB bus workstation. The algorithm of the identification device is shown in figure 3.

Figure 3 – Algorithm for identification of USB-devices
Realized program detects host controllers that are set on the workstation is hubs and ports, and then scans for the presence of connected devices. If the device is found, the form requests for standard descriptors devices.The program is part of the system, so the implementation is designed as a console application. The results of the program are presented in figure 4.
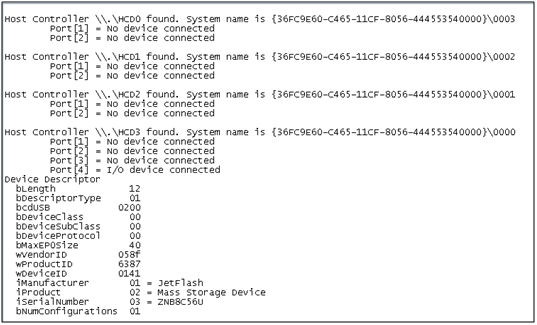
Figure4 – The results of the program for identification of USB-devices
The algorithm of information security based on the USB interface
Each user of the modern personal computer has ability to store and transfer information using USB-drives (flash memory). The cost of such devices in the computer market is about $ 10 depending on capacity. Due to the relatively low cost, and flexible enough and easy use of flash memory for most users and employees of enterprises choose exactly this way of storing and transmitting information.
In terms of corporate security and confidentiality of internal information is often necessary to control intra-flow of information. It is therefore describe the algorithm proposed monitoring workstations of employees of any organization or enterprise. The ultimate goal of the algorithm is to control the information that travels between the employee’s workstation hard drives and external USB-drive.
The proposed algorithm is implemented surveillance program, intelligence officer, who will monitor the operation of all drives that are connected to workstations staff bus USB (figure 5).
Figure 5 – The principle of interaction programs with USB-controller and the computer of administrator
- On Figure 5, the program-intelligence structure consists of two parts - client and server that communicate with each other on the LAN.
The client side runs on the local workstation and the employee performs the following functions: - 1. Autorun program at the start of the reconnaissance of the operating system.
- 2. Determining the types of USB-connected devices, as well as groups of parameters that characterize the device (manufacturer, model, serial number).
- 3. Monitoring of requests to read / write access, the possibility of isolating specific information on the process name or file mask, or content.
- 4. Determination of MAC-and IP-addresses of the workstation.
- 5. Transmission of the information collected on the server, the volume of the information package is configured.
- 6. Operating in stealth mode (as a service).
The server component runs on a reconnaissance administrator's workstation and executes the following functions. - 1. Verifying and full remote control of all programs on clients.
- 2. Save and storage of information from the client programs.
- 3. Batch configuration of all connected clients.
4. Provide user interface to existing information.
- An analysis of the architecture and component interaction USB was an algorithm to ensure security on the basis of interface USB, and also contains the general principle of the program. In the proposed system is implemented routine identification of USB-devices in accordance with its descriptor. The information obtained, which allows you to uniquely identify a specific USB-device, if necessary, can be stored on the server Realized routine is only part of the developed system.
- Implementation of the proposed algorithm can be useful in public, private or state-owned enterprises as a control to ensure privacy of data within the computer system of the enterprise, and to prevent leakage of corporate information outside the enterprise.
- At the moment the writting of this paper master's work is not completed.
1. Агуров П. В. Интерфейс USB. Практика использования и программирования. – СПб: БХВ-Петербург,2004. – 576 с.
2. Гук М. Шины PCI, USB и FireWire. – ЗАО Издательский дом "Питер", 2005.– 544с.
3. Интересное о USB [электронный ресурс]. – Режим доступа: http://hi-tech.mail.ru/articles/item/1896/.
4. Комиссарова В. Программирование драйверов для Windows. –БХВ-Петербург, 2007 – 256 с.
5. Лапин А. Интерфейсы. Выбор и реализация. – Техносфераг, 2005 – 168 с.
6. Магда Ю. Ассемблер. Разработка и оптимизация Windows-приложений. – БХВ-Петербург, 2003 –540 с.
7. Мюллер C. Модернизация и ремонт ПК (глава 15 – Последовательный, параллельный и другие интерфейсы ввода/вывода – USB) = Upgrading and Repairing PCs. – 17 изд. – М.: "Вильямс", 2007. – С. 1016-1026.
8. Уолтер О. Использование microsoft windows driver model. – Питер, 2007 – 768 с.
9. Хульцебош Ю. USB в электронике. – BHV-СПб, 2011. – 224 с.
10. Anderson D. Universal Serial Bus System Architecture [электронный ресурс]. – Режим доступа: http://interface.centraltreasure.com/files/pdf/Hardware_USB_ System_Architecture_pdf.pdf.