Abstract
Content
Introduction
Develop new Web applications often focuses on the experience of the customer, and most often it comes down to providing the necessary functionality and high-quality interface for users. Often enough attention is paid to the system server application integration. Safety issues at the same time are often neglected or postpone their decision on the last stage - the stage of testing the application.
Many years of experience in various companies shows that the security of web applications should start already in the early stages of the design process and application development [1]
The purpose of addressing Web application security is:ensuring high application availability, quality server solutions, and protect confidential data, to ensure the development of safe and secure software solutions
It should be noted that the cost and the time taken for the implementation of security measures at the stage of application development is much less than the perfection of them on stage, start-up or fixes are "ready" applications.
ПWith the development of Web applications, you must perform the following tasks:
- Avoid application vulnerabilities in the early stages of development;
- Make it so that application developers to create high-quality and safe design;
- If there are applications developed within the company does not need to require the application providers expert advice in order to ensure safety.
1. Topicality
Web-based applications are among the most insecure systems to date. The more critical and sensitive data stores software, the more important it becomes an audit of its security.
2. Statement of the problem
The main objectives of this work is to study the means of web application security, as well as a more detailed discussion of this type of vulnerability as XSS vulnerability and try to find ways to determine this kind of attack. As for the classic types of vulnerabilities as this:
- SQL injection
- PHP include
- XSS
They are considered in more detail in Section 3.
As part of the master's work is to get the actual scientific results in the following areas:
- Algorithm improvements testing web-applications
- Writing your own xss scanner.
- Site testing freshmen faculty CST via xss scanner for vulnerabilities.
3. Overview of Research and Development
Among the tested resources are web applications written in different programming languages??, with each language characterized by its own set of the most significant vulnerabilities (according to the research group Positive Technologies [2]. Most developers prefer PHP: it says 63% of all tested sites. Substantial proportion ASP.NET (19%) and Java (14%). The other languages ??are much less common. Distribution Sites - test participants on their underlying programming language visually represented in Fig. 1.
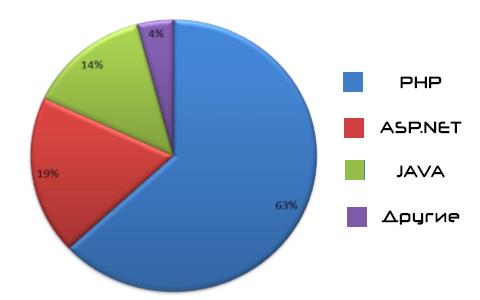
Fig. 1. The programming languages for creating dynamic Web-pages
Personally, I work with the sites began in the third year. Together with the supervisor, we have developed a portal for freshmen faculty CST. In the plans it was a kind of library methodological provisions for all specialties and faculty. At the time of writing a master of this resource is not over yet. It is scheduled to run and put on the hosting of the official website of the faculty. Since this project is quite promising and useful for students, it is expected a huge number of visits and in connection with the probability of an attack increases the probability of data loss. So before you upload it to the appropriate universal access to worry about the safety of the resource and to test it for vulnerabilities. For this task was to examine types of vulnerabilities and write your own scanner to test the site.
In the early days of the Internet, almost every application contained a large number of these vulnerabilities. But every day it became more difficult to meet this type of vulnerability. And the cracks are becoming more sophisticated, leading to the development of new types and vectors of attack - one of these types of attacks has been isolated in a separate class, and was named CSRF.
Conclusion
In this paper, we classified the most common WEB-vulnerabilities. The results showed that among the identified vulnerabilities in the largest number of sites is the leader - Cross-Site Request Forgery (CSRF).
The paper analyzed the security features of web-applications. As a method for the further development of research in the master's thesis decided to work with methods that analyze the source code of web-applications, and configuration.
In order to know how to protect their own resources should be thought of as the part of the attacker, and thus to know the basic requirements for a successful attack:
- Ability to force the victim to a page with additional code. Or the possibility of modifying the attacker frequently visited pages of the victim (as the saying goes, if the mountain will not come to Mohammed, then ...).
- No protection against CSRF on the target site.
- The user at the time of the attack must be authorized for the action that we want to execute on its behalf.
And based on these requirements, you should try to build a defense.
References
- Безопасность web-приложений http://www.fortconsult.net/ru/ваши-трудности/безопасность-веб-приложений
- Positive Technologies – безопасность,консалтинг http://www.ptsecurity.ru
- Уязвимость CSRF. Введение http://intsystem.org/768/learn-about-csrf-intro/
- Издательство БХВ-Петербург, Тактика защиты и нападения на Web-приложения – 2005. – 432с
- Уязвимости | информационный портал о безопасностиhttp://www.securitylab.ru/vulnerability
- Козлов Д. Д., Петухов А. А. "Методы обнаружения уязвимостей в web- приложениях" / Программные системы и инструменты: тематический сборник ф-та ВМиК МГУ им. Ломоносова N 7. П/р Л.Н. Королева. М: Издательский отдел ВМиК МГУ. Изд-во МАКС Пресс, 2006 г.
- Межсайтовый_скриптинг http://ru.wikipedia.org/wiki/Межсайтовый_скриптинг
- Защита от SQL injection и XSS (функция secureInnerData ) http://n3info.blogspot.com/2013/05/sql-injection-xss-secureinnerdata.html
- XSS атака сайта и способы защиты. Как сделать и проверить XSS уязвимость http://consei.ru/xss-ataka-sajta-i-sposoby-zashhity/



