Abstract
Contents
- Introduction
- 1. Theme urgency
- 2. The purpose and objectives of the research, the expected results
- 3. Overview of Research and Development
- 4. Study of Network Attacks
- 5. Algorithm protection from DDoS-attacks.
- Findings
- References
Introduction
The development of information technology and increasing of the information space has a huge impact on all areas of human activity associated with the accumulation and processing of data. Currently, there are a huge variety of location in the Internet databases and other resources that contain information about the various branches of science, education and business. There is a need to provide easy access to the databases and to ensure their proper operation and reliable protection. At this stage, and the question of protection of servers, networks, and certain parts of the network from attacks such as DDoS.
Denial of service can be achieved under various conditions, and as a consequence of different factors, for example:
- bugs in the software that runs on the victim service
- disadvantages of network protocols
- limitations in channel capacity
- ill-conceived network infrastructure
Usually the source of DDoS-attacks is a certain amount of infected computers networked together and called "botnet." Usually, the computers that are infected, control and listen to a specific port or responses to commands in IRC-chat. However, currently a proliferation of botnets controlled via the website or on the principle of p2p-networks.
1. Theme urgency
One of the most urgent tasks in the service of providing information is to ensure the stable operation of and access to the database at any time. When operating in this mode, so it is necessary to ensure a certain degree of reliability and resistance to stress the system. One of the most serious and common ways to attack a DDoS-attack (from the English. Distributed Denial of Service, distributed attack of the "denial of service"). The purpose of this attack is to bring the system to failure, that is, the creation of an environment in which legitimate users of the system can not access the resources provided by the system, or that access is difficult.
Master's work is devoted to the study of sources of malicious traffic and its parameters, creating a model of the enterprise network in which there is a surge protector (handles requests from the outside), the creation of the algorithm to distinguish malicious traffic generated by attackers.
2. The purpose and objectives of the research, the expected results
The purpose of this study is to improve the quality of filtering traffic from malicious loads through the development of model processing external requests received by the network, and improve their filtering algorithms.
The main objectives of the research:
- Analysis of the structure and parameters of the network model of the enterprise;
- The research data obtained in the simulation process for creating an algorithm;
- Creating a filter algorithm malicious traffic;
- Assess the effectiveness of this algorithm.
The object of research : an algorithm for filtering malicious traffic.
The subject of research : filtering techniques malicious traffic.
As part of the master's work is to get the actual scientific results in the following areas:
- Development of a reliable model of the structure of the corporate network;
- Development filtering algorithm malicious traffic;
- Development of recommendations for the prevention of the problem;
- Modification of the known methods of filtering malicious traffic.
3. Overview of Research and Development
The problem of DDoS-attacks is very urgent, so there are always new techniques and ways to carry out attacks. Publications on this topic is not very much, but the information in the books quickly become obsolete and do not take into account the current trends. Most of the publications on this subject is the English-language form. Content is considerably less than the post-Soviet space.
3.1 Overview of international sources
One of the most useful books on the subject, which dealt with all aspects of the problem of the possible solutions is the typical "Internet Denial of Service Attacks and Defense Mechanisms", written by the University of Mehmud Abliz Pitsburga [5]. In order to ensure the unity of the terms and concepts in studies conducted around the world to agree on the terms and concepts, structure and organization of knowledge on the subject .. One of the first publications on the taxonomy of the sources of DDoS-attacks and defense mechanisms against them was written in 2002 in the "A Taxonomy of DDoS Attack" authored by J. Mirkovic, P. Reiher [6]. Later, the same authors reviewed one of the ways to deal with DDoS-attacks by comparing traffic patterns in normal mode with all the traffic that passes through the system [24]. More deeply the topics considered by other authors, who suggest the use of statistical indicators of traffic received on the basis of long-term network traffic analysis [7]. Among the alternative solutions are hardware solutions, where algorithms are routers and they make a decision about the undesirability of traffic [8 - 10 ]. Some researchers have proposed to shift the solution to the problem of the user. By introducing the CAPCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) or similar methods [11]. Regular analyzes and quarterly annual reports issued by large companies market to protect against DDoS-attacks - Arbor Networks and Kaspersky Lab [ 12 , 13].
3.2 Overview of national sources
The number of national sources is much less of national publications are the most common review articles, such as, for example, the article authors SN Barber, D. Kisyuk, TA Govorushchenko from universities VNTU, KNU respectively [14]. More detail the problem considered A. Ignatenko from the Institute of Software Systems of NASU [15].
There are quite controversial publications that as a solution to this problem using the zoom of server capacity to cater for all conditions, including unwanted traffic [16]. This approach is not a viable solution, as the cost of implementation of this method is unreasonably high.
A similar theme is the student and faculty of Cherkasy State Technological University. Examined the sources and methods of filtering malicious traffic [17].
Theoretical developments for modeling DoS / DDoS-attacks presented by the authors Yatsikovska CU, Karpinski MP [18]; also on the subject written work authored Domareva SV Institute of Computing Technology of the National Aviation University, in which the process of DDoS-attacks is presented as a Markov model of the branched process [25].
Considered in detail by the authors Mikhaylyuta S.L., Stepanushko I.V., Babic B.A. Tkachenko V., Lavrynovych V. One of the types of DDoS-attacks, which uses the ICMP protocol [19].
3.3 Overview of local sources
In the Donetsk National Technical University was written several papers on the subject. The article "Entropy as an indicator of a network traffic anomaly", written by a student DNTU Borisov DN in 2007. This article describes how to filter based on employing modern cloud solutions in this area [20]. Indirectly, DDoS-attacks are discussed in Prikhodko NA on LAN security [21]. In the individual section of the site master Filenko MS The techniques of DDoS-attacks, recommendations for combating and preventing [22]. In the individual section of the site master uncle's IP Propose a model corporate network during the attack [23].
Partially describes the classification of DDoS-attacks in the student Breach SA Department of Computer Monitoring Systems Department of Computer Science and Technology [24].
4. The study of network attacks.
According to the report [4] published by Arbor Networks, which provides one of the best decisions to ensure stable operation of information systems and has extensive experience in fighting a DDoS-attack, in 2012, the year of growth in the number and intensity of attacks has slowed compared with previous years. In this complex attacks, and application-level attacks continue to evolve, becoming more complex.
46% of attacks treated to comprehensive DDoS-attacks that use to send junk traffic, SYN-flooding (sending a large number of connection requests via TCP) and UDP Flood (shipping large amounts of multiple UDP-packets) as well as attacks using protocols the application layer. The percentage value of attacks using application-level were the most common and accounted for about 85%. However, in comparison with previous years the proportion of declared this type of attack have not changed with respect to the majority of services, such as HTTP, DNS and SMTP. The only aspect of the application-level attacks, which apparently survived change was the HTTPS-protocol application level which rose from 24% to 37%.
According to the report, there is some concern about the compromised workstation. There is a chance that the computers belong to the corporate network can be part of a botnet (a network of infected computers that are used in the attack). such a situation is leads to increased effect of the attack, because protection may be directed only to the outer network, ignoring the corporate intranet traffic.
The increase in the number of hosts that make botnets, not surprising, given the number and complexity of the currently existing viruses, the pace of development and coming out of this inability to build a reliable system of protection based on antivirus software, and intrusion detection systems.
The most powerful DDoS-attacks for 2012 The year was the attack that struck the company's servers Cloudflare on September 15. As a result, service is temporarily unavailable Cloudflare was part of the user. It is worth noting that the company is a content delivery network and under its control are several data centers in different regions. The company can easily withstand DDoS-attacks in the tens of gigabytes, but with the attack of 65 Gbit / s could not cope.
In March 2013 the company Spamhaus, which is a database of servers that are used by hackers to help postal operators spam and other unwanted content, brought it to its blacklist of servers owned by the Dutch company CyberBunker. CyberBunker company said that Spamhaus has no right to tell what to publish and what not to publish on the Internet. The Dutch company has deployed the most powerful DDoS-attack of all time. Its power reached 300Gbit / s. Friendly such capacity is not able to provide much harm as protection technology was involved, namely the distribution of traffic in different data centers and its subsequent filtering. The attack had a certain effect on the entire Internet, which was expressed in increasing ping to some European sites. Providers normally withstood the attack, but were strongly flooded.
According to the complexity of suppression, as well as the motivation for carrying out DDoS-attacks can be divided into categories such as: vandalism - this is usually not distributed attacks, and attacks that are carried out with one or two hosts, the attacker is not likely to get any benefit from it, and makes this is because the owners of the grievances of any resource, its knowledge in this area is limited by simple methods of attacks found on the Internet. These attacks are reflected fairly easy, as also do not require high skills in the area of ??computer networks against external attacks, and are often decided by blocking specific IP or a simple packet filtering seen by laws; nihilism - in fact, the reasons are virtually identical reasons for vandalism, but the action is taking place more focused, and it is distributed attack. It involved a group of people who are upset by the or other newsworthy information. Usually it is a simple bat-script, which uses the ping command with a larger screening package and listed attacked resource, no knowledge of the user is not required, just run the script. Blocked by this attack is usually easy enough, blocked the entire load obtained via ICMP; business - attackers use this type of attack, not only as a means to enrich themselves, but also to provide DDoS-attack as a service.
Consider the principles that had made ??the most powerful attack. According to the report [5] at the heart of this attack is UDP-flooding, which is accompanied by a SYN-flood. This indicates the presence of a sufficiently large number of controlled servers.
Also in the course of this attack technology was used amplification attack. Multiply the original malicious traffic carried by reflecting DNS-queries via DNS-resolvers that are installed for each ISP. Usually DNS-resolvers are configured to only handle requests from its users, but there are a large number of companies that are incorrectly configured them, so resolvers accept requests from any Internet user. There will also be interesting to note that much of the gain is due to the larger springs DNSSEC, which are included in the body of the response, and in fact DNSSEC protocol is implemented to improve the security of DNS.
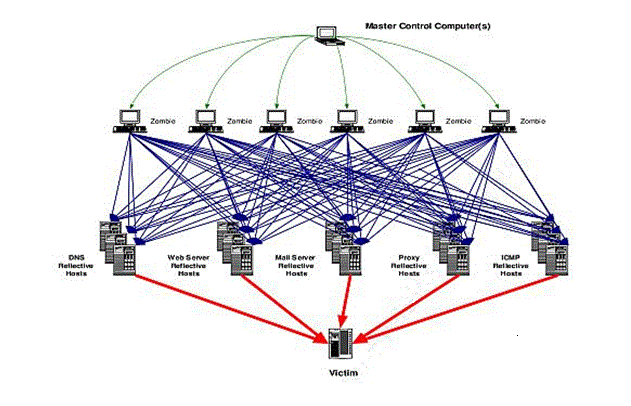
Picture 1 – Schematic representation of a network attack
5. Algorithm protection from DDoS-attacks.
There are basic solutions to protect against attacks:
- software solutions;
- hardware solutions;
- cloud solutions.
Software solutions - the most common on the market, often a set of traffic filtering rules that are made by the developer on personal experience. This solution is quite simple to install directly on the server that is running the resource, but will only attack from subtle kind of vandalism.
Hardware solutions - are creating a distributed network structure with a large stock of the traffic. Used in large-scale network structures, such as: traffic exchange points, data centers, large regional providers.
Cloud solutions represent a network structure with a large bandwidth, which are introduced into the server to filter malicious traffic. Thus, such a network will gradually filter out negative traffic and reduce the number of malicious packets. Traffic analysis is a difficult task, so some companies patent their algorithms, such as the company "Black Lotus" patented algorithm "Human Behavior Analysis", which determines who generates traffic, human or robot, and the company "Arbor" offers its product "PeakFlow" which has signature-based approach to filter out unwanted traffic.
determine the cause and the problems to be solved in the fight against this type of attack, it is possible to find ways to solve these problems.
The animation shows the principle of the system being modeled.
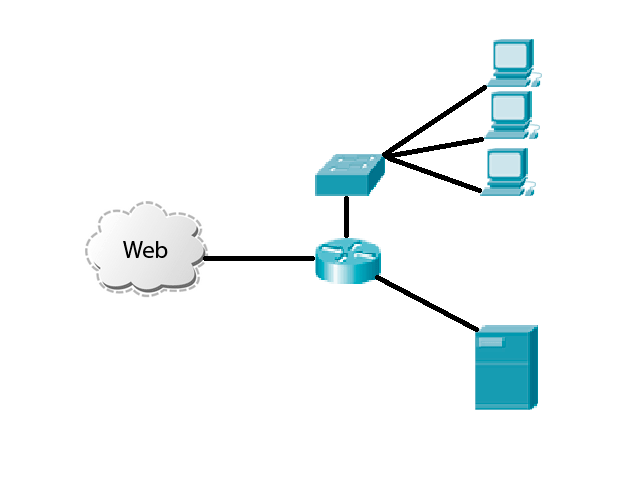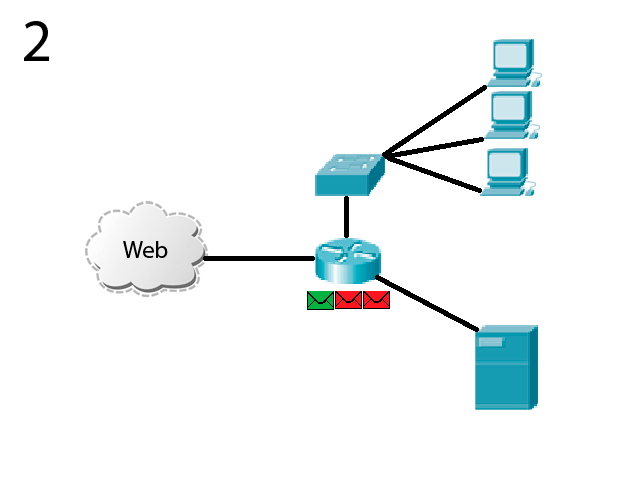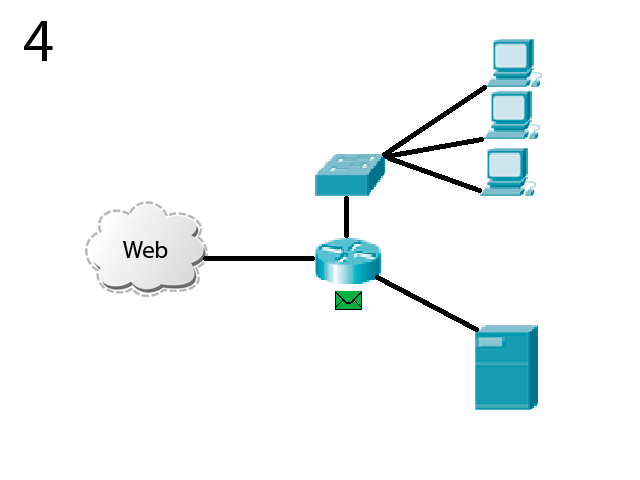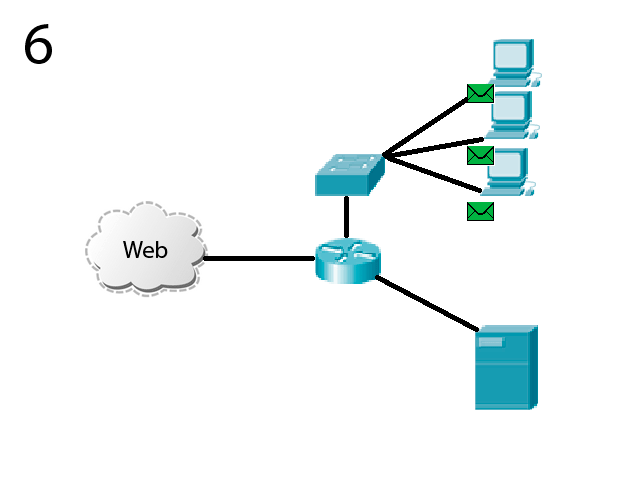
Picture 2 – The principle of operation of the simulated system
(Animation: 7 shots, 7 cycles of repetition, 24 kilobytes)
In the animation process of simulated attacks on the company's network. Malicious traffic on par with the useful into an internal network. First, the data received by the device traffic analysis. At this stage, use the most simple filtering algorithms - static tables with pomoshchbju which appears to block malicious traffic from specific sites (for example IP). Manage node (filling tables) performs server, which is the network immediately after the first device. This server performs an active verification of the data and collects statistics about the malicious traffic and its sources. After identifying the source of pest it sends information about it to the first device and thus blocking it. In order to blocked sites did not get the trusted device, and other work, the server performs a constant active analysis of all traffic. The server then performs the limiting speed and redirects certified traffic to a network. Traffic is delivered to the destination node on the corporate network without problems and congestion.
Findings
The abstract provides information about network attacks, with the causes of their occurrence. On the example of a real attack shows the existing mechanisms to combat hackers. This issue is relevant and, although there are already market leaders in this field, their proposed product is a fully enclosed, protected by a patent. Unlike solutions with closed-source, open recommendations can result in methods and algorithms to a single standard that will make these solutions more flexible and will use them more efficiently.
As part of the research carried out:
- Studied classification methods of DDoS-attacks.
- The causes of the emergence and structure of the attacks.
- The existing solutions and the analysis of their work.
Further research is focused on the following aspects:
- Development of a model enterprise network that can resist DDoS-attacks
- Development Mechanism simulation of DDoS-attacks
- Create filtering algorithms of malicious traffic
- Evaluation of the resulting solutions
In writing this essay master's work is not yet complete. Final completion: December 2013. Full text of the and materials on the topic can be obtained from the author or his manager after that date.
References
- DDoS and Security Reports: The Arbor Networks Security Blog [Электронный ресурс]. – Режим доступа: http://www.arbornetworks.com/
- Сайт Лаборатории Касперского [Электронный ресурс]. – Режим доступа: http://www.securelist.com/ru/analysis
- Олифер В.Г., Олифер Н.А. Компьютерные сети. Принципы, технологии, протоколы. 4 издание, 2010, 943с.
- Статистика глобальной сетевой активности [Электронный ресурс]. – Режим доступа: http://atlas.arbor.net/summary/attacks
- Abliz M. Internet Denial of Service Attacks and Defense // Pittsburgh : University of Pittsburgh Technical Report [Электронный ресурс]. – Режим доступа: http://www.cs.pitt.edu/
- Mirkovic J., Reiher P. A Taxonomy of DDoS Attack [Электронный ресурс]. – Режим доступа: http://www.eecis.udel.edu/
- Feinstein L., Schnackenberg D., Balupari R., Kindred D. Statistical Approaches to DDoS Attack Detection and Response. // DARPA Information Survivability Conference and Exposition [Электронный ресурс]. – Режим доступа: http://www.cs.unc.edu/
- Ioannidis J., Bellovin S. Implementing Pushback: Router-Based Defense Against DDoS Attacks // AT&T Labs Research [Электронный ресурс]. – Режим доступа: http://www.cs.columbia.edu/
- Yaar A., Perrig A., Song D. Pi A Path Identi?cation Mechanism to Defend // Carnegie Mellon University Research Showcase [Электронный ресурс]. – Режим доступа: http://repository.cmu.edu/
- Park K., Lee H. On the Effectiveness of Route-Based Packet Filtering for Distributed DoS Attack Prevention in Power-Law Internets // West Lafayette : SIGCOMM’01 [Электронный ресурс]. – Режим доступа: ftp://mail.im.tku.edu.tw/
- Keromytis A., Misra V., Rubenstein D. SOS: Secure Overlay Services // SIGCOMM’02 [Электронный ресурс]. – Режим доступа: http://utd.edu/
- Worldwide Infrastructure Security Report // Arbor Networks [Электронный ресурс]. – Режим доступа: http://www.arbornetworks.com/report
- Цирульник С.М., Кисюк Д.В., Говорущенко Т.О. DDoS-атаки й методи боротьби з ними [Электронный ресурс]. – Режим доступа: http://www.nbuv.gov.ua/
- Ігнатенко О. Атаки на відмову: виникнення проблеми, огляд атак, класифікація [Электронный ресурс]. – Режим доступа: http://eprints.isofts.kiev.ua/
- Кадыров М., Труфанов А., Умеров Р. Внедрение облачных вычислений как метод предотвращения DDoS-атак [Электронный ресурс]. – Режим доступа: http://www.uintei.kiev.ua/
- Михайлюта С.Л., Степанушко І.В., Бабич Б.О. Захист інтрамереж від DOS- та DDOS-атак [Электронный ресурс]. – Режим доступа: http://www.nbuv.gov.ua/
- Яциковская У.О., Карпинский Н.П. Моделирование сетевого трафика компьютерной сети при реализации атак типа DoS/DDoS [Электронный ресурс]. – Режим доступа: http://www.nbuv.gov.ua/
- Михайлюта С.Л., Степанушко И.В., Бабич Б.А., Ткаченко В.Ю, Лавринович В.С. Исследование сетевых DOS-атак, основанных на использовании протокола ICMP [Электронный ресурс]. – Режим доступа: http://www.nbuv.gov.ua/
- Борисов Д.Н. Энтропия как индикатор возникновения аномалий сетевого трафика [Электронный ресурс]. – Режим доступа: http://ea.donntu.ru/
- Приходько T.А. Исследование вопросов безопасности локальных сетей на канальном уровне модели OSI [Электронный ресурс]. – Режим доступа: http://ea.donntu.ru/
- Филенко М.С. Распределенные атаки типа «отказ в обслуживании» [Электронный ресурс]. – Режим доступа: http://masters.donntu.ru/
- Брич С.А. Интегрированная модель противодействия атакам в социотехнических системах [Электронный ресурс]. – Режим доступа: http://masters.donntu.ru/
- J. Mirkovic, P. Reiher, G. Prier Attacking DDoS at the Source [Электронный ресурс]. – Режим доступа: http://www.cs.unc.edu/
- Михайлюта С.Л. Математическое описание процессов атак на компьютерные сети [Электронный ресурс]. – Режим доступа: http://www.nbuv.gov.ua/
- Котенко И.В., Степашкин М.В., Богданов В.С. Модели и методика интеллектуальной оценки уровня защищенности компьютерной сети [Электронный ресурс]. – Режим доступа: http://stepashkin.com/pubs/2006/ais-06-paper.pdf
- Домарев Д.В. Математическое описание процессов атак на компьютерные сети [Электронный ресурс]. – Режим доступа: http://www.nbuv.gov.ua/
- Крис Касперски Техника и философия сетевых атак [Электронный ресурс]. – Режим доступа: Техника и философия сетевых атак
- Гамаюнов Д.Ю. Обнаружение компьютерных атак на основе анализа поведения сетевых объектов [Электронный ресурс]. – Режим доступа: Обнаружение компьютерных атак на основе анализа поведения сетевых объектов
- Емельянова Ю.Г., Талалаев А.А., Тищенко И.П. Нейросетевая технология обнаружения сетевых атак на информационные ресурсы [Электронный ресурс]. – Режим доступа: Нейросетевая технология обнаружения сетевых атак на информационные ресурсы
- Комар М.П. Методы искусственных иммунных систем и нейронных сетей для обнаружения компьютерных атак [Электронный ресурс]. – Режим доступа: Методы искусственных иммунных систем и нейронных сетей для обнаружения компьютерных атак
