Introduction
The development of information technology and IT industry as a whole led to the emergence of a number of
issues related to the provision and processing of information. One of the most important in the
today is the problem of information security. Computers are used in banking
systems at airports, medicine, research, media,
so that information affects almost all areas of activity of any company, from its credibility
and depend on the veracity of the work, production safety, and even the safety of people.
Within every organization information that treated its employees can not go
beyond. Moreover, any information that has been received and processed by members of the company,
it is its property and can not be used or modified by other third parties.
To protect information during transmission between employees or departments
used steganography algorithms. Steganography – the science of secure communication
information by the secrecy of the fact of the transfer [
2]. Who is gaining popularity
the linguistic steganography – hiding a message, changing the parameters of the elements
which consists of a carrier or by creating a new medium so that it contains
transmitted message. In other words, the aim of linguistic steganography is to hide
of the transfer of the information and its encryption [
1].
In DonNTU hidden information using linguistic resources engaged K. Larionova, the theme of her master
work: “Methods of encoding arbitrary information in computer texts based on linguistic resources” [
7].
As this issue was engaged I. Sokolenko, the theme master work: “The system of hiding information based on linguistic resources” [
8].
1 The goals and objectives of the study, expected results
To implement the master's work had the following goals and objectives:
- – explore existing methods of linguistic steganography;
- – to determine the advantages and disadvantages of the investigated techniques;
- – to develop its own method of linguistic steganography based on the existing
- – develop a program that will implement the developed method.
Thus, as a result of the work planned to get his own method and linguistic
steganography software that will implement it.
2 Review of methods of linguistic steganography
2.1 Semagrams
Semagrams – concealment of information by means of signs or symbols.
For example, hand sign, head, a certain sequence of numbers
or words, all Semagrams. Such signs are not evident,
and are not visible to the casual person. Sometimes the use of visual
semagrams – the only way to communicate with friends and colleagues.
However, it is necessary to determine in advance the necessary signs for use in communication.

Figure 2.1 – Scheme Semagrams
Text Semagrams – this is a message hidden inside the text.
Capital letters, underscores, especially handwriting spaces between
letters and words – all of them can be used for transmission
any message. Association can also be used for this purpose,
If you need to pass a very small amount of information.
Say you had agreed with her friends that will share on
email seemingly harmless weather forecasts [3].
Pros:
- – unbeknownst to third parties;
- – ease of implementation.
The only drawback is easy to implement, because of which can be obtained quite easily hidden information.
2.2 Phonetics
This method can be used, if you know exactly what language is programmed
filter that “catches” the words in the language which is predominantly used
inhabitants of the country. Sometimes (in addition) and in the language that is rampant or
used on websites (english, french). Of course, it is not safe
say how exactly programmed filter. But in order to come closer to understanding,
it can be used phonetically similar words. This method is most suitable if
you are using an alphabet other than in your own language (eg, russian, instead of english)
[
3]. Example: country коунтри.
The only advantage of this method – ease of implementation.
Disadvantages:
- – easily hidden information;
- – in fact, the information is not hidden.
2.3 Jargon
In any language, there is a concept jargon. Jargon – sociolect;
it is different from the language of general specific vocabulary and phraseology,
expressive turns and the use of special means of word – formation,
but has its own phonetic and grammatical system. Slang
words or phrases called “jargon” [
4]. Using jargon in the text
can puzzle an outsider reader. Moreover slang words can be
invented members of correspondence. For the implementation of this method creates a database
words and relevant jargon, with hidden words are replaced. The recipient must
you need to know the jargon used that to understand the message. Better
choose words that will keep text – “carrier” in a clear, readable form,
even if you perceive slang “as is” [
3].

Figure 2.2 – Scheme of the method jargon
Pros:
- – ease of implementation;
- – if you save the text in a readable form, will not have suspicions about the presence of hidden information.
Disadvantages:
- – list of words is limited to members of the correspondence;
- – the recipient must know the jargons;
- – for failing to use jargon, an attacker can guess and understand the hidden meaning of the message
2.4 Covert coding
A special case of linguistic steganography, most difficult to
implementation, but provides high data secrecy.
The method uses a special feature that encrypts
and decrypts the message for transmission [
6]. The simplest way is
“the first letter”. The idea is that each letter hides the message
it is the first letter of the word a new message – encryption, which is transmitted to the recipient.
An example of this method is the link [
3].
Another type of hidden code is to use a special
the formula for the allocation of the hidden message of “message – container” [3].
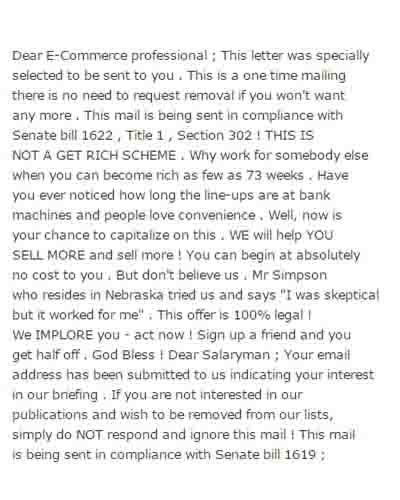
Figure 2.3 – Post – code
If you enter this message on the site, on which you can click on the link [5], we get a very interesting result.
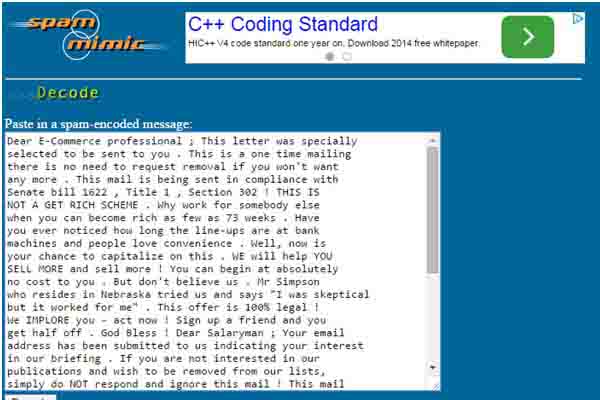
Figure 2.4 – Initial Post

Figure 2.5 – The hidden message
The general scheme of the hidden coding method is shown in figure 2.6.

Figure 2.6 – The general scheme of information hiding
(Gif animation file was created in the program Easy GIF Animator.
Animation contains 7 frames, switching interval between the two 1s,
7 cycles of repetition, the size of 85.4 KB.)
Pros:
- – if encryption decryption program, the recipient does not need to know the algorithm for hiding information;
- – strong resistance to deshiforvaniyu;
- – hard to understand that the message – code is hidden subtext.
Disadvantages:
- – implementation complexity;
- – in the generation of the text “message – container” hard to get readable form transmitted message
Table 1 – Comparison table of methods of steganography
|
Have advantages / disadvantages
|
Semagrams
|
Phonetics
|
Jargon
|
Covert coding
|
| The complexity of the implementation of |
– |
– |
– |
+ |
| Easy to detect the presence of an encrypted message |
– |
+ |
– |
– |
| Easy to decrypt the message |
+ |
+ |
+ |
– |
| Artificial restrictions (for example: the vocabulary from the sender and recipient, or other conventions between them) |
+ |
+ |
+ |
– |
Analyzing table 1, we can conclude that the most qualitative method
steganography is a hidden encoding. This method ensures complete
hide the fact of the message, which is not limited, however, it is
is the most difficult to implement.
Findings
It was considered the main methods of linguistic steganography, which are used to hide information in transit. Established the advantages and disadvantages of each method.
Thus, in preliminary studies, it was found that the most persistent linguistic steganography method is hidden encoding. This method has a complex implementation, which is associated with the generation of a word using a particular function, but this method is the fact of transmission masks the hidden message and receive the message without a specific key (function) is virtually impossible. Therefore, a proprietary method that will be developed during the execution of the master's work will be based on the method of coding hidden.
At the time of writing this essay master's work is not yet complete, but thanks to the research area chosen for further study and research goal, namely the development of their own linguistic steganography algorithm.
List of sources








