Abstract
Contents
- Introduction
- 1. Theme urgency
- 2. Research purpose and tasks
- 3. Research and development review
- 3.1 International sources review
- 3.2 National sources review
- 3.3 Local sources review
- 4. Increasing of copyright protection methods and means effectiveness in the field of software development for distributed systems
- Conclusion
- References
Introduction
The illegal copying and distribution of software products is one of the main problems of software developers. Successful software product creating requires a lot of time and money. If the sales of released software products don't make enough profit by the reason of illegal software product usage, it will be not profitable to continue product maintenance for a developer [1].
Thus there is a need to provide an illegal copying and usage protection system of licensed software.
1. Theme urgency
Nowadays the problem of copyright protection methods and means effectiveness in the field of software development is very urgent as one can find cracked version on special catalogs of pirated software almost for any software product that is intended for sale and protected with copyright protection tools.
This situation is the result of warez-groups activity — groups of individuals proficient at cracking the digital rights management (DRM) tools. Now the most well-known ones are 3DM, RELOADED, CPY, SKIDROW, CODEX [2]. Thus the existing methods and means applied for software copyright protection are not effective enough to prevent hacking.
2. Research purpose and tasks
The research purpose is the increasing of copyright protection methods and means effectiveness in the field of software development for distributed systems.
Research object is the software copyright protection methods and means.
The main research tasks are:
- the research of existing software copyright protection methods and means in cloud infrastructure systems;
- the analysis of existing software copyright protection subsystem scalability problem;
- the analysis of distributed systems common architecture for Big Data processing;
- the increasing of copyright protection methods and means effectiveness in the field of software development for distributed systems;
- the effectiveness evaluation of proposed software copyright protection means;
3. Research and development review
Unfortunately, in the open information sources there are no details about internal protection organazing in the existing software copyright protection solutions.
3.1 International sources review
There are several most popular license management systems used by a developer for a software product copyright protection:
- Keygen — cloud-based licensing and distribution service, provides API and supports several license types [3];
- Nalpeiron Licensing Service — cloud-based licensing service, supports software offline-activating [4];
- License4J — Java-library supporting different hardware IDs for license checking [5];
- SafeGuard LM — provides API and anti-hacking module [6];
- Reprise License Manager — provides failover distributed servers and signs licenses with digital signature [7].
The book Distributed Systems. Principles and paradigms
by Andrew S.Tanenbaum, Maarten Van Steen [8]
covers the principles, advanced concepts, and technologies of distributed systems in detail, including:
communication, integrity, fault tolerance, and security.
3.2 National sources review
The book The art of protecting and hacking information
by Dmitriy Sklyarov (Искусство защиты и
взлома информации
Дмитрия Склярова) [9] deals with errors which are often made during protection tool
developing, and the examples of existing systems hacked becase of these errors.
The book The art of disassembling
by Kris Kaspersky, Eva Rokko (Искусство дизассемблирования
Криса Касперски и Евы Рокко) [10] deals with reverse engineering. The begining covers basic hacking, popular
hacking tools review, the identifying and source language key structure reconstructing methods. Considerable
attention is paid to reconstructing of protection algorithm and anti-debug tactic overcoming methods.
3.3 Local sources review
DonNTU masters reviewed following publications.
In the work System of ensuring stability to unauthorized software modification
by Kirill Popyrko
(Попырко Кирилл Система обеспечения устойчивости программ к несанкционированной модификации
) [11]
existing software protection methods are researched, the review and comparison of existing software
protection solutions are provided.
In the work Researching methods and means of protecting sensitive data with distributed processing in the
cloud infrastructure
by Artem Yegorov (Егоров Артём Исследование методов и средств защиты
конфиденциальных данных при распределённой обработке в облачной инфраструктуре
) [12] the existing
distributed systems protection means is analyzed and distributed system Apache Hadoop is researched.
4. Increasing of copyright protection methods and means effectiveness in the field of software development for distributed systems
Warez-group hackers use different software tools which allow to research and disable copyright protection. If protection system works in offline mode and does not communicate with external network (offline checking and software using license activation), it will be ehough for a hacker to research an algorithm and to bruteforce license data a protection system would consider as valid.
If bruteforcing is unpossible, it will be enough for a hacker only to modify executable binary code of software protection module so that software product would continue to work in a normal mode despite the license checking result, or to disable activating procedure and license checking at all.
As a hacker can always apply a rude method of modifying an executable binary code of software protection module, it can be assumed that any protection based only on license data checking model can be hacked and disabled. Time required for such a hacking is the decisive factor in this case.
Addressing the vulnerability of executable binary code modifying in order to disable license checking it is required to apply executable data protection method where the important part of software product functionality remains unworkable without the available additional executable module on a client computer. Such a module can either contain a licensed functionality the access to which is possible only after successful license checking or be an additional module (a bridge) without which it is impossible to get access to licensed functionality [13]
According to the earlier implemented license checking algorithm (fig. 1), after the launch a client part of protection system sends license data to a server. In the case of successful license data checking a server sends back to a client an additional executable module encrypted with unique key. If it is required to get access to licensed functionality a client decrypts a received module and interacts with it.
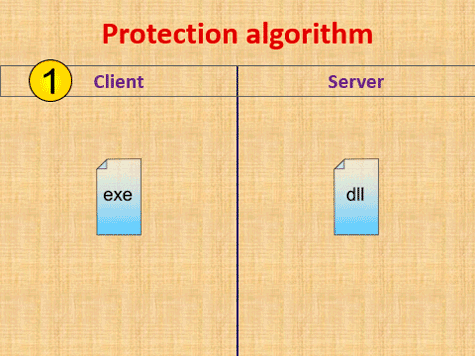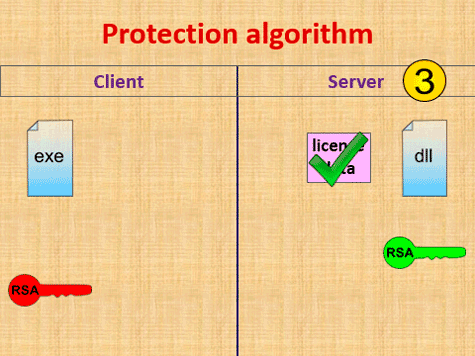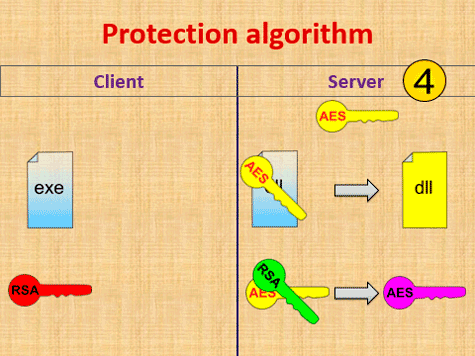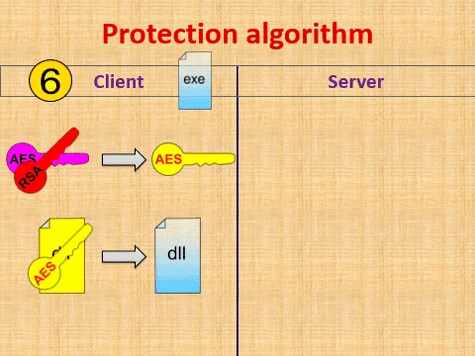
However, a required performance and failover level of a copyright protection system being developed should also be taken into account. If this system is used by several developers for their software products protecting (with several users per each software), it is required to provide appropriate performance level for license server. For solving this problem it is necessary to apply distributed computing methods and spread a load between different computing clusters and database servers [14].
For implementing a distributed system it is going to use the opensource framework for distributed programs developing and executing Apache Hadoop [15], namely, Cloudera Distribution for Hadoop (CDH) [16] included built-in tools which allow to provide cluster protecting with data encrypting, user authenticating and authorizing mechanisms.
For storing the information about the developers, licensed software products and their versions, users and licenses it is planned to use the NoSQL distributed database Apache HBase which is also included in the CDH.
Conclusion
The existing software usage copyright protection methods and means have some disadvantages. A license checking algorithm can be researched and modified, and a server part of such the systems does not always provide required performance and failover level.
To increase the effectiveness of a software usage copyright protection system it is required to combine a remote licensed functionality protection method and a distributed computing method.
References
- Чернышова, А.В. Подсистема защиты авторского права в программном обеспечении / А.В. Чернышова, Д.В. Кубашевский // Информатика и кибернетика. – 2016. – № 2(4). – С. 68-72.
- All Scene Groups and Crackers [Электронный ресурс] // CrackWatch. – Режим доступа: https://crackwatch.com/groups – Загл. с экрана.
- Keygen [Электронный ресурс] // Keygen. – Режим доступа: https://keygen.sh/ – Загл. с экрана.
- Software Licensing Cloud-Based [Электронный ресурс] // Nalpeiron. – Режим доступа: https://www.nalpeiron.com/ – Загл. с экрана.
- License4J [Электронный ресурс] // License4J. – Режим доступа: https://www.license4j.com/ – Загл. с экрана.
- Tech [Электронный ресурс] // Persistent Security. – Режим доступа: https://www.persistentsecurity.com/tech/ – Загл. с экрана.
- RLM [Электронный ресурс] // Reprise Software. – Режим доступа: http://www.reprisesoftware.com/products/software-license-management.php – Загл. с экрана.
- Таненбаум, Э. Распределённые системы. Принципы и парадигмы / Э. Таненбаум, М. ван Стеен. – СПб.: Питер, 2003. – 877 с.
- Скляров, Д.В. Искусство защиты и взлома информации / Д.В. Скляров. – СПб.: БХВ-Петербург, 2004. – 288 с.
- Касперски, К. Искусство дизассемблирования / К. Касперски, Е. Рокко. – СПб.: БХВ-Петербург, 2008. – 891 с.
- Система обеспечения устойчивости программ к несанкционированной модификации [Электронный ресурс] // Портал магистров ДонНТУ. – Режим доступа: http://masters.donntu.ru/2013/fknt/popyrko/ref.html – Загл. с экрана.
- Исследование методов и средств защиты конфиденциальных данных при распределённой обработке в облачной инфраструктуре [Электронный ресурс] // Портал магистров ДонНТУ. – Режим доступа: http://masters.donntu.ru/2017/fknt/yegorov/diss/index.htm – Загл. с экрана.
- Чернышова, А.В. Подсистема защиты авторского права в программном обеспечении [Текст] / А.В. Чернышова, Д.В. Кубашевский // Сборник материалов VIII Международной научно-технической конференции
Информатика, управляющие системы, математическое и компьютерное моделирование
(ИУСМКМ–2017). - Донецк: ДонНТУ, 2017. – С. 110-114. - Чернышова, А.В. Подсистема защиты авторского права в сфере программного обеспечения / А.В. Чернышова, Д.В. Кубашевский // Информатика и кибернетика. – 2017. – № 4(10). – С. 84-90.
- Apache Hadoop [Электронный ресурс] // Apache Hadoop. – Режим доступа: https://hadoop.apache.org/ – Загл. с экрана.
- Overview of Cloudera and the Cloudera Documentation Set [Электронный ресурс] // Cloudera Documentation. – Режим доступа: https://www.cloudera.com/documentation/enterprise/5-13-x/topics/introduction.html – Загл. с экрана.
