Author's abstract
Theme: «Development of algorithms for protection of information systems against virus attacks».
Introduction. Urgency. Purposes
1 Principles of construction of the automated systems of protection of the information in banks
1.1 General requirements to system of safety
1.2 General data about the automated systems of safety
1.3 Interaction of a subsystem of proactive protection and other computer subsystems
2 Scientific novelty
2.1 Use of expert systems in proactive protection
2.2 Use of neural networks for formation of rules of expert system
The conclusion
The list of the literature
Introduction. Urgency. Purposes
Information safety from the moment of occurrence of an opportunity of data transmission thought the instrumentality of Internet, stood on the first place. The greatest interest represents Internet as the instrument for fulfillment of crimes usually in sphere of economy and the finance. In accordance with the certificate of experts the most attractive sector of economy for criminals is the computer credit and financial system. The most widespread computer crimes are made by not authorized access to bank databases by the instrumentality of telecommunication networks. Banks because of competitive struggle are among themselves compelled for maintenance of convenience and speed of work with clients to give to them an opportunity of the removed access from networks of the general using to the bank computing systems with the purpose of audit of own accounts. And not looking at complexity of safety systems of banks on a background enough strong protection against a hostile environment still lacks an effective control to all of them.
Without introduction of innovative technologies in subsystems of information safety, can shortly lead to that breaking of computer credit and financial systems becomes habitual business. Experts in the field of information safety such as Iskander Rustamovich Koneev (the Chief of a department of computer safety systems of National bank in Uzbekistan) and Kaspersky Evgenie Valentinovich (in the field of protection of the information and a member of the Organization of researchers of computer viruses - CARO) approve One of leading world experts, that existing methods of protection of the information become outdated. Scientists have noted, that in second half of 2005 individual viruses of new generation have been fixed.
Struggle between systems of information safety and viruses is an infinite process. As a result, counteraction to threats promotes their complication, and complication of threats conducts to perfection of means of counteraction. This spiral has led to that speed of occurrence of viruses continuously grows.
Anti-virus laboratories in structure of leading firms on system engineering protection are engaged in a problem of protection of the information. To such firms it is possible to carry Kaspersky laboratory, McAfee, Panda, Symantec and Dr. Web. All these leading firms are engaged in improvement of algorithms of protection of the information and development of the anti-virus automated systems.
It is possible to approve safely, that threat to the automated bank systems grows every year. Creation of a subsystem of information safety with use of innovative technologies for such automated systems is the actual task.
Proactive protection is one of modern technologies. An essence of technology is, that not algorithms of attack are exposed, plunders and removals of data, but a set of the actions made by viruses in automated system. The main advantage of proactive protection to my opinion is ability to find out and block absolutely new virus, the signature for which else is absent in bases.
Object of research - automatic systems of designing of protection of the information.
An object of research - algorithms of proactive protection.
The purpose of research - research of work of algorithms of proactive protection. Development of a subsystem of information safety with use of algorithms of proactive protection and expert systems.
- To the top -
1 Principles of construction of the automated systems of protection of the information in banks
1.1 General requirements to system of safety
The automated system of protection of the information is considered separately from other information space of bank, however it is clear, that a number of specific mechanisms and the technologies which are present at bank, can and should influence the list of shown requirements.
The automated system of safety should work at a level of a kernel of the automated system of bank so that any significant action within the limits of system - whether it is an action of the user or process - did not occur without participation of a subsystem of safety.
The scheme of safety realized in system, should be separated from means of safety of the most operational system on which the automated system of safety will be realized, in the sense that failure or vulnerability of system safety of operational system should not influence to the work of the automated system of safety.
Mechanisms of safety of system should be issued in the form of widely known in the world, the tested and approved standards and reports.
The system of safety should provide the closed preservation and the data transmission, connected with the automated system (actually modules of system, system and applied data) so that:
- It was impossible to get logic access to the specified data beyond the framework of work of the appendix of the automated system;
- Any movements of data in the system occurred under the control of system of safety.
- To the top -
1.2 General data about the automated systems of safety
In conditions when computer systems become a basis of business, and databases - the main capital of many companies, the automated system of safety strongly rises near to with the questions of the general economic safety of the organization. Especially this problem is actual for the banks, being keepers of rather confidential information about clients, whose business is constructed on continuous processing of electronic data.
Generally, the automated system of safety of bank information system should be under construction by a hierarchical principle. Services of all levels are united in the uniform computer network, by means of the local computer network.
The automated system of safety should give such kinds of services:
- Updating of the software and anti-virus bases;
- Management of distribution of the anti-virus software;
- Management of updating of anti-virus bases;
- The control of the work system in whole (reception of preventions of detection of virus attack, regular reception of complex reports about work system in whole).
The automated system of safety should provide formation of the integrated computing environment satisfying to following general principles:
- Reliability - system in whole should possess, continue, function irrespective of functioning separate units of system and should possess means of restoration after refusal;
- Scalability - system of anti-virus protection should be formed in view of growth quantity of the protected objects;
- The openness - system should be formed in view of an opportunity of replenishment and updating of its functions and structure, without infringement of functioning of the computing environment in whole;
- Compatibility - support by the anti-virus software of a maximum quantity-possible of network resources. In structure and functional features a component means of interaction with other systems should be presented;
- Commonality (uniformity) - components should represent standard, industrial systems and the means which having wide sphere of application and have been checked up by repeated use.
Proactive protection (behavioural blockirator , the behavioural analyzer) - one of the modern technologies embodying a qualitative leap in the field of counteraction to virus attacks.
Essence of technology that data on data carriers are exposed to the analysis not, but behaviour of data - set of the actions, which were made in system. If to consider a certain class of data nocuous it is possible to define and prominent features of behaviour.
For today there is enough of the automated systems of protection of the information, using new technology of proactive protection.
- To the top -
1.3 Interaction of a subsystem of proactive protection and other computer subsystems
The subsystem of proactive protection is built in the automated system as the separate module. Acting streams of the information (Entering Internet traffic) for the detailed analysis act in a subsystem of proactive protection. Having passed the testing, information will act on a subsystem of anti-virus protection of bank and further to act in the module addressed (File a server, workstations, post a server and a database).
Work of a subsystem of proactive protection can be divided into stages:
- The entrance dataflow acts in a subsystem of information safety of proactive protection;
- Using analysis algorithms of the information, the subsystem of information safety of proactive protection analyzes the entrance dataflow on presence of threats;
- All the found threats act in the block of the knowledge base where by existing rules will be certain the degree of threat of entrance data;
- The Knowledge base informs a subsystem of information safety of proactive protection result of search by rules and consequence of it, a subsystem or will transform the entrance dataflow to a target stream (the Dataflow leaving of a subsystem of proactive protection) or informs the manager by creation of the report with its entering in magazine on dangerous entrance data;
Work of proactive protection can be divided into four components (blocks):
- Algorithms of processing of behaviour;
- Algorithms of processing of the information;
- Expert systems;
- Neural networks;
As the entrance information for the block of algorithms of processing of behaviour serves the entrance dataflow. This information passes careful check on presence of threat to the automated system of bank.
Algorithms of processing of the information under the acting information from expert system reports forward the entrance dataflow further or form and data menacing to the automated system of bank destroy
- To the top -
2 Scientific novelty
2.1 Use of expert systems in proactive protection
The majority of existing anti-virus systems with modules of proactive protection use knowledge of experts for struggle against entering threat. But not every user is a good expert and it’s impossible to struggle with threat by such methods if as protection of system is understood the bank automated systems. At occurrence of threat (attempt of hacker breaking or attack by a virus) to the existing automated systems demands advice of the qualified expert that speaks about not intellectuality of such methods of protection. Application of expert systems for subsystems of proactive protection will solve set of problems. The main problem is automation of process of protection of the bank automated systems.
The expert system with necessary quantity of rules can replace the qualified expert for protection against threats of the general character. But it is impossible to approve, that the subsystem of proactive protection with use of expert systems can cope with any problem as protection is psychology and to learn system to understand it, it is not obviously possible.
Sources of knowledge can be texts (instructions, documents, monographies, clauses, photos, films), supervision or experts-professionals. Process of revealing and formalization of knowledge of these sources appears difficult enough as it is necessary to be able to estimate importance and value of that or other knowledge for work of intellectual system. The knowledge engineer should describe the basic receptions or heuristics which the expert uses at the decision of badly formalizable problems, and to transform these descriptions to the strict, full and consistent system, allowing to solve complex applied problems not worse, than it would be made by the expert. The most widespread model of representation of knowledge is the system of production. The systems, which use knowledge in the form of production (rules), refer to productional. Productional system almost has no procedural components which represent a basis background of the von Neumann computing system, and practically completely cope data, that it is descriptive. Such system includes three basic components: base of rules, working memory and the mechanism of a conclusion.
The base of rules contains a set of the productional rules, witch have the form IF-THEN. Each rule develops of two parts. First of them - antecedent, or sending rules consists of the elementary offers connected bundles And and OR. The second part named consequent , or the conclusion, consists of one or several offers which form the decision given out by a rule.
Antecedent is the sample of the rule, which intends for recognition of a situation when it should work. The rule works, if the facts from working memory by comparison have coincided with the sample then the rule is considered fulfilled.
The base of rules is represented in the form of a file of structures. Each structure is a class to which will be threat concerns. Each field of such structure is an attribute for recognition.
Generally such structure can be presented:
- A kind of threat;
- Fields are attributes of threat;
- To the top -
2.2 Use of neural networks for formation of rules of expert system
There are many models neural networks with the purpose of co-ordination and the subsequent processing of the symbolical information. We shall consider architecture of a neural network of recursive autoassociative memory (RAAM - Recursive Autoassociative Memory). Main advantage of RAAM is that it can be described without use of mathematics. Purpose of RAAM is a representation of the symbolical information or structures in the form of neural networks. Symbolical structures represent trees of the fixed valency.
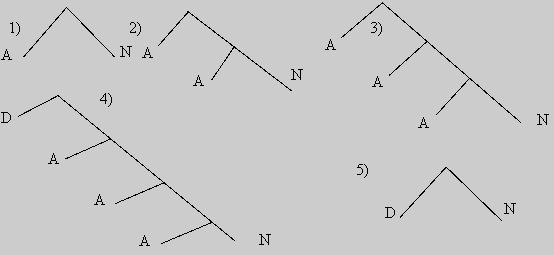
Figure 2.1. Binary trees
On fig. 2.1 binary trees which are shown some show structure of expressions of which offers consist.
Trees on fig. .2.1 can be described following rules:
- (A N);
- (A(A N));
- (A(A(A N)));
- (D(A(A(A N))));
- (P(D N)).
Network RAAM is an autoassociative network with return distribution of mistakes. In entrance and target layers RAAM elements are organized in fields where each field contains identical number of elements. Number of the fields is defined by valency of coded and decoded trees, and the number of elements in the latent layer corresponds to number of elements of one layer.
To terminal symbols correspond the vectors, in entrance set they are fixed, but as weight factors during training are constantly corrected, representations of all other vectors should vary. For example latent representation for (D N) during training changes, as weight values constantly vary. Such change in set of educational samples is named as an effect of the moving purpose. When the network comes nearer to a point of convergence, changes of the moving purposes become very small.
Realization of network RAAM, unique additional complexity in comparison with usual autoassociative networks with return distribution of mistakes is necessity of return before the samples generated in a hidden layer again in entrance layers. This question easily is solved if to use structure of a stack of data for storage of the information about the internal units. Representation of sequences by means of RAAM is easier. As an example, the sequence corresponding word BRAIN, can be presented in the form of a tree (see fig. 2.2). Terminal symbol "NIL" is used as a blank. Coding begins, as is usual, from below upwards, and "In" moves on consideration to the left entrance field, a "NIL" - to the right entrance field. Whereas the compressed representations move on a feedback only to the right entrance field, the left and right entrance fields (and, thus, corresponding target fields) can contain different number of elements: restriction consists only that the latent layer both right entrance and target weeding should be the same sizes. For sequence there is no necessity to store representation in a stack as earlier the compressed elements move back in an entrance layer.
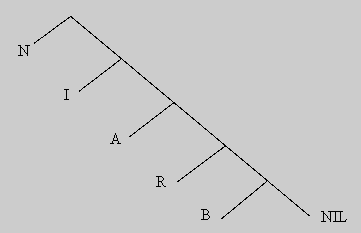
Figure 2.2. Representation of word BRAIN in the form of a tree
The word brain can be packed as concatenation of separate letters, which enter into it. Vector representation of a word brain can turn out by means of concatenation terminal codes. For example using five bit codes for letters, the word brain can be presented as "10000 01000 00100 00010 00001". Can occur, that words will have different length hence so their vector will be the different size in that case the word with smaller quantity of letters will supplement with the necessary zeroes.
Procedure of finding in memory an element is similar to corresponding procedure of network Hopfield (i - a layer of the elements, j - an associative layer of elements):
- Set the values of elements activity of a layer i in conformity with the values by the entrance sample;
- Activity extends on a layer j. The combined input of an element of a layer j is equal
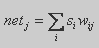 (2.1)
(2.1)
- The new condition for each element of a layer j is calculated
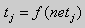 (2.2)
(2.2)
- Activity extends on a layer i. The combined input of an element of a layer i is equal
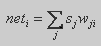 (2.3)
(2.3)
- The new condition is calculated for each element of a layer i
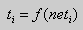 (2.4)
(2.4)
- This bilateral distribution of signals of activity repeats until the steady condition will be reached. Activity for each layer is defined concerning some threshold size
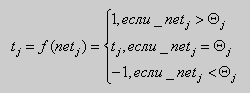 (2.5)
(2.5)
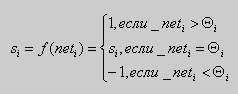 (2.6)
(2.6)
Model Dinasty is dynamic system of understanding of the text. On an input of such model move fragments of the text, and on an output turns out the intelligent completed text. Action in such model concentrates on the distributed semantic representations corresponding concepts and statements. The distributed semantic representations are generated by means of expansion of network RAAM (XRAAM - extended RAAM). Expansions of network RAAM are the dictionary, which consists a pair "symbol" and " the distributed semantic representation ". Some structure (pattern) is connected with each offer. Patterns consist of components (the AGENT, ACTION, OBJECT, the TOOL).
- To the top -
The conclusion
Using expert systems and artificial neural networks in creation of proactive protection it is possible to achieve "intellectuality" of a subsystem. The saved up experience of the expert will represent algorithms of search and the analysis of threats by the use of expert systems. Expert systems use when the analysis of the homogeneous information is required. For a problem in search and the automated removal of threats application of expert systems plays a greater role. First the entrance dataflow is not late at testing by systems under control of experts and secondly gives greater opportunities for creation of the universal automated subsystems of proactive protection.
Summing up, it is possible to draw a conclusion, that problems of information safety are not solved at the necessary level. The urgency of a problem of creation of the automated system of safety for bank systems, is very high. Firms and the organizations information engaged by automated protection allocate two directions of information safety:
- Search of threats after hit of entrance data on data carriers;
- Search of threats before hit of the entrance information on carriers (during loading).
The majority of firms is offered with decisions which are based on the first direction. It is possible to draw a conclusion, that the second direction lags behind in development as it have started to apply rather not so long ago.
Application artificial neural networks and expert systems in the automated systems of safety is a new developing direction.
- To the top -
The list of the literature
- Нейлор К. Как построить свою экспертную систему: Пер. С англ. - М.: Энергоатомиздат, 1991. - 286с.: ил.
- Левин М. Руководство для хакеров. - Москва, 2000 – 416 с.
- Хатч, Брайн, Ли. Секреты хакеров. Безопасность Linux – готовые решения, 2-е издание.: Пер. С англ. - М.: Издательский дом «Вильямс», 2004. - 704 с.:ил. - Парал. Тит. Англ.
- Анин Б.Ю. Защита компьютерной информации. - СПб.: БХВ – Санкт-Петербург, 2000. - 384 с.:ил.
- Фленов М.Е. Linux глазами хакера. - СПб.: БХВ-Петербург, 2005. - 544 с.:ил.
- Aitel D., Young S. The hacker’s handbook : the strategy behind breaking into and defending Networks. 1968 – 849 p.
- Касперски К. Записки исследователя компьютерных вирусов. - Спб.:Питер, 2005. - 316 с.: ил.
- Василенко О. Н. Теоретико-числовые алгоритмы в криптографии. - М.: МЦНМО, 2003.—328 с.
- Соколов А., Степанюк О. Защита от компьютерного терроризма. - Спб.: БХВ – Петербург, 2002. - 496 с.
- По материалам сайта «Kerberos: The Network Authentication Protocol»,
- To the top -