
Olga Andrianova
Faculty: computers and Information ScienceDepartment: monitoring Computer Systems
Speciality: computer Ecological Economic Monitoring
Theme of master's diploma:
"The Latent Greate Information Files Transfer by Stegocoding WAV-files"
Scientific adviser: Ph.D. Natalya Gubenko
Abstract
of master's diploma
"The Latent Greate Information Files Transfer by Stegocoding WAV-files"
Аuthor: Olga Andrianova, master
Donetsk national technical university
Scientific adviser: Ph.D. Natalya Gubenko
Donetsk national technical university
Introduction
The problem of information’s protect is indissolubly related to existence of humanity and intercourse of people between itself. In fact enterprises, jars, private individuals want not only to pass information each other but also protect it from extraneous eyes. So there was cryptography, direction of defence information, at which a report is encoded by different algorithms which know an only transmitter and accepting information side [1].
Actuality
Actuality of problem of informative safety constantly grows and stimulates the search of new methods of priv. Development of information technologies stimulates the wide use of digital pictures, dvd films, music in the format of mp3, WAV. In this connection there was practical sense of information’s protect [2].
Aims and tasks
A purpose of work is an increase of efficiency of hidden information methods introduction of the in a voice WAV-file by development of new algorithms and programmatic modules.
Tasks, solved in master's degree work:
A very characteristic tendency presently in area of priv is introduction of cryptological methods. However on this path there are many yet unsolved problems, related to the destructive affecting cryptotools. An association of methods of computer стеганографии and cryptographies was a good way out of the created situation. In this case it was succeeded to remove the weak sides of the known methods of priv and develop more effective new untraditional methods of providing of informative safety.
Supposed scientific novelty
Usually apply stego methods for copyrights defense and digital signatures. In master's degree work planned a few other approach. A musical WAV-file is not defense object, but it is container for the secret texts transmission, thus largeness texts, in fact in a WAV initially there is much redundant information which can be replaced unnoticed for a human ear.
Approbation
Appearances on this work passed on conferences:
"Computer monitoring and information technologies 2007"
"Computer monitoring and information technologies 2008"
"Computer monitoring and information technologies 2009"
The twelfth (the seventh international) student's scientific conference on the applied mathematics and computer science SNKPMІ – 2009 L'vіv
Review of research-and-developments on the topic
In DonNTU
Within the limits of our university by the problems of steganography, and concretely an analysis and methods of defence of voice files the master's degree of Mikhaylyuk Ivan Sergeevich was engaged in (http://masters.donntu.ru/2007/fvti/mikhayluk/diss/index.htm). The program of introduction of digital thread-mark was developed them in MP3-file.
In Ukraine
In a table 1 is the list of the Ukrainian researchers is resulted in area of priv and theme of their works of[9].
Тable 1 - Scientists Works in the field of the information protection
| Name | Author |
| How to provide authenticity of electronic documents? | Lukatskiy А.V. |
| How a sectional code is arranged? | Andrey Vinokurov |
| Cryptography without secrets | Barichev P. |
| Cryptography and computer safety | Khorst Faystel', transl. Andreya Vinokurova |
| Cryptography with the opened key | A.Salomaa, transl. I.A. Vikhlyantseva |
| Kriptoanalysis of a tunnel protocol of type point-point (PPTP) from Microsoft | Bruce Schneier, Peter Mudge, transl. Vasiliy Tomilin |
| Bases of modern cryptography v 1.2 | P. Barichev, R. Serov |
| PGP: conception of safety and vulnerable places | Filipp Zimmermann |
In the world
One of the best and most widespread products in this area - it S-Tools (has freeware status). The program allows to hide any files both in the images of format of gif and bmp and in the audiofiles of format of wav. Thus S-Tools – it and стеганография, and cryptography, because a file, subject a concealment, is yet and coded by one of cryptographic algorithms with the symmetric key: DES, triple DES or IDEA - two last for today fully deserve a trust. Program: S-Tools (Steganography Tools) for the operating system: Windows 95/98: ftp://ftp.clark.net/pub/phoenix/steg/s-tools4.zip ftp://ftp.bogus.net/pub/mirrors/ftp.giga.or.at/stego/s-tools4.zip
Other widespread steganography program - Steganos for Wm95, which is easy to the use, but however by the powerful program for the encipherement of files and hiding them inwardly BMP, DIB, VOC, WAV, ASCII and HTML of files. It possesses those possibilities practically, what S-Tools, but uses other cryptographic algorithm (HWY1), and, in addition, able to hide information not only in the files of format of bmp and wav but also in ordinary text and HTML files, thus by a very original method - at the end of every line the certain number of blanks is added. With new properties and additional possibilities of Steganos for Win95 is serious competitors at the market of informative safety for hiding of files.
Contraband is software allowing to hide any files in 24 bit graphic files of format of BMP [8].
Concept of steganography
Steganography is the method of connection organization, which hides the presence of connection actually, unlike cryptography, the fact of existence of secret report hides at steganography. It does not replace cryptography (encipherement of information), but complements it another strength security.
Progress in area of computer networks of world scale and tools of multimedia technologies resulted in development of new methods, intended for providing of safety of transmission of the telecommunications and use given on ductings them in the undeclared aims. These methods take into account the natural errors of devices of digitising and surplus of analog video or audio signal, enable to hide reports in computer files (containers). Thus, these methods hide the fact of information transfer [5].
Digital steganography is direction of classic steganography, based on a concealment or introduction of additional information in digital objects, causing some distortions of these objects here. As a rule, these objects are multimedia-objects (images, video, audio, texture of 3D-objects) and bringing of distortions which are below than average threshold sensitiveness man not given to the noticeable changes of these objects.
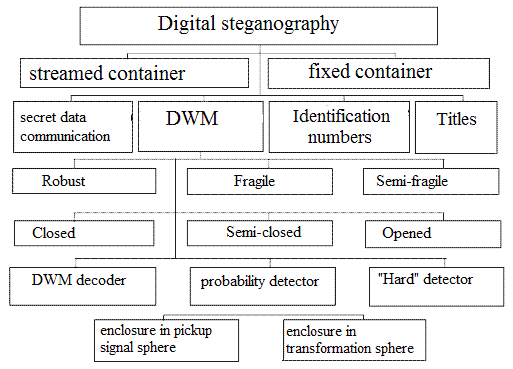
Figure 1 - Classification of the systems of digital steganography
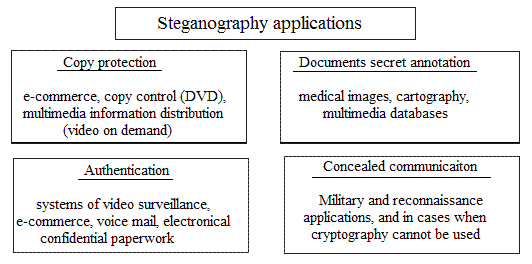
Figure 2 - The Potential application of steganography domains
Steganography system
Steganography system consists of: report which needs to be hidden; container which a report is built into; key for building and stegoalgorithm.
Stages of stegocoding process:
Steganography methods
Now all methods of computer steganography develop on two basic directions:
1. Methods which are based on the use of the special properties of computer formats;
2. Methods, based on surplus of visual information and audio.
Within the framework of the second directions at the information hiding algorithms, using, prevail in audiofiles:
Author stegocoding method
The analysis of literature shows complete absence of methods of building of steady to the compression multimedia information practically. One of transformations, allowing to carry out similar building, there is discrete wavelet-transformation. As is generally known, the set of wavelets, in their temporal or frequency presentation, can approach a difficult signal or image, thus both ideally exactly and with some error.
Wavelets have obvious advantages in presentation of function local features s and non-obvious account of psyhophisiological features perception model. Due to it they are widely used for the analysis of features, compression and reconstruction of difficult signals.
Will routine that their application at development of steganography method, oriented to achievement of maximal carrying capacity (hidden transmission and storage of information) it is possible to decide the basic steganography tasks, namely: minimization of the brought in distortions and stability to the attacks of passive malefactor.
Wavelets are the generalized name of temporal functions, having the appearance of wavepackages of one or another form, noncommunicative on the axis of independent variable (t or x) and apt at a change on it or down-scaling (to compression-tension). Wavelets are created by the special base functions - prototypes, questioner their kind and properties. On localization in temporary and frequency realms they occupy intermediate position between a sinewave function and function of Dirac.
Practice work with wavelets is usually based on the special interpretation of wavelet-преобразований to frequency area and allows fruitfully to use the well developed and a long ago known vehicle of frequency filtration and methods of rapid wavelet-transformation. They are based on the pyramidal algorithm of Mallata and thinning out of wavelets spectrum on frequency [4].
The modified building has the followings advantages:
1. Decline of distortions at building. There is possibility of adaptive selection of паттерна taking into account the model of signal.
2. Increase of secrecy of channel. For extraction of information a malefactor must not only locate waveletом, used on the stage of hiding, but also signal-pattern, at least for one of bit characters.
3. Increase of firmness to stegoanalysis, because from a signal the unmodified areas are eliminated on the basis of which possibly leadthroughs of statistical stegoanalysis.
Confluence is carried out in accordance with expression, where wi is a coefficient of the selected window after the operation of confluence, wi— coefficient of the selected window to the operation of confluence, seq— counting out of signal-pattern, proper the bit of information of b built in a current window, а— coefficient of weakening of initial substripe.
Most interest for comparison of building methods is presented by dependence of container distortions and amount of bit errors depending on the building coefficient. At the increase of coefficient and the amount of bit errors diminishes, but distortions of signal increase at the same time. The increase of decouplig depth in this case does not have influence on probability bit errors. The important criterion of applicability of one or another stego method for the information hiding is a size of the distortions brought in a method. At building of the modulated signal at fixed level of decomposition standard deviation of signal from initial depends on the chosen coefficient.
On the resulted charts coefficient and changed with a step 0.05. The size of standard deviation droningly increases with the increase of coefficient and at the value of а= 0.61 a rejection becomes equal to the rejection at direct modulation a bit sequence [7].
![Change of standard deviation at building of the modulated signal with changing Coefficient and [0.01,0.2] And direct zeros of coefficients (horizontal lines) of the first 3 substripes](../library/stegano3/images/2.gif)
Figure 3 - Change of standard deviation at building of the modulated signal with changing Coefficient and [0.01,0.2] And direct zeros of coefficients (horizontal lines) of the first 3 substripes
![Maximal (continuous line) and minimum (dotted line) probability of bit error at a variable coefficient and [0.01,0.2]](../library/stegano3/images/3.gif)
Figure 4 - Maximal (continuous line) and minimum (dotted line) probability of bit error at a variable coefficient and [0.01,0.2]
Will consider the method of encoding with expansion of spectrum more detailed. TSVZ (digital thread-mark) is embedded in audiosignals (sequence of 8- or 16-bit counting out) by the insignificant change of every counting amplitude out. For finding out TSVZ an initial audiosignal is not required. Let an audiosignal consist of N of counting out xi, m=1,2,…,N , where value N not меньше 88200 (accordingly 1 second for stereo audiosignal, digitized on frequency 44,1 кГц). In order that to build TSVZ, the function of f(x(I), w(I)) is used, where w(I) is counting out of TSVZ, changing scope [-a; and], and is some constant. The function of f must take into account the features of the system of man ear in order to avoid perceptible distortions of initial signal. Counting out of resulting signal turns out as follows: y(i) = x(i) + f(x(i),w(i)).
Relation signal-noise in this case is calculated as 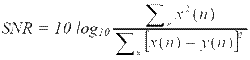
Finding out TSVZ takes place as follows: Will designate
Will designate  through S next sum: take the First sums in (4) equal to the zero, if numbers on the return of GSCH are up-diffused evenly and the expected value of value of signal is equal to the zero. There is some difference in most cases, designated w, which must be also taken into account. Consequently, assumes an air
through S next sum: take the First sums in (4) equal to the zero, if numbers on the return of GSCH are up-diffused evenly and the expected value of value of signal is equal to the zero. There is some difference in most cases, designated w, which must be also taken into account. Consequently, assumes an air
Sum ,as it is rotined higher, approximately equal to the zero. If in an audiosignal was not embedded TSVZ, then S will be approximately equal
,as it is rotined higher, approximately equal to the zero. If in an audiosignal was not embedded TSVZ, then S will be approximately equal  De autre part, if in an audiosignal was embedded TSVZ, then S will be approximately equal
De autre part, if in an audiosignal was embedded TSVZ, then S will be approximately equal  . However, it is an initial signal which on a condition can not be used in the process of finding out TSVZ. The signal of х(і) can be replaced on at(і), it will result in replacement
. However, it is an initial signal which on a condition can not be used in the process of finding out TSVZ. The signal of х(і) can be replaced on at(і), it will result in replacement  Consequently, subtracting a size
Consequently, subtracting a size  from S, and dividing a result on
from S, and dividing a result on  , will get the result of r, rationed by 1. The detector of TSVZ, in-use in this method, calculates the size of r, set a formula
, will get the result of r, rationed by 1. The detector of TSVZ, in-use in this method, calculates the size of r, set a formula 
The threshold size of discovery in theory lies between 0 and 1, taking into account approximation this interval is taken to [0 - and; 1 + and]. Experimental a path it is set that in order that to define how indeed certain TSVZ is in a signal, a threshold value TSVZ must be higher 0,7. If large authenticity is required in determination of presence of TSVZ in a signal, a threshold value must be increased. Work of coder and decoder presented on pic.6.
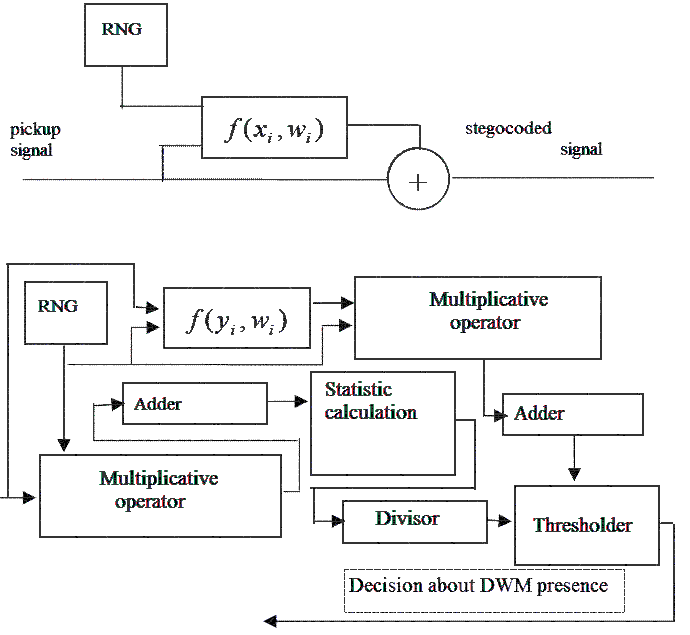
Figure 5 - Flow-chart of stegocoder and stegodecoder
Conclusion
A conclusion the Conducted experiments rotined, that the offered method allowed to save built-in information at converting in the format of file WAV. At the estimation of developed firmness methods of steganography there is an estimation of hidden report renewal probability to the attacks of passive malefactor of one of important descriptions. It was set as a result of the conducted experiments, that extraction of information in absence information about used waveletе is impossible.
It allows to provide the high level of secrecy on the basis of wavelets constructing, dependency upon the key. At further researches of method there are of interest techniques modulations of coefficients, providing a high carrying capacity at the maintainance of firmness to distortions, brought in the formats of compression with losses, in particular, the offered method is steady to transformation of format of presentation of multimedia information (quantum, compression with the loss of quality). A method also allows to build information in digital representations.
Literature
- 1. Щеглов А. Ю. Защита компьютерной информации от несанкционированного доступа. –СПб.: Наука и техника, 2004. –384 с.
- 2. Варламов О. О. Системный подход к созданию модели компьютерных угроз информационной безопасности.// Материалы VI Международной научно-практической конференции «Информационная безопасность»- Таганрог: Издательство ТРТУ, 2004 С. 61-65 .
- 3. Домарев В. В. Безопасность информационных технологий. Системный подход: - К.: ООО ТИД ДС, 2004.-992с.
- 4. И. В. Машкина, Е. А. Рахимов. Модель объекта информатизации // Материалы VI Международной научно-практической конференции «Информационная безопасность»- Таганрог: Издательство ТРТУ, 2004. С.
- 5. Абалмазов Э.И. Методы и инженерно-технические средства противодействия информационным угрозам//Гротек, 1997, 248 с.
- 6. Карасев Андрей. Компьютерная тайнопись – графика и звук приобретают подтекст. – Мир ПК. - № 1/97. – С.132-134.
- 7. В. Г. Грибунин, И. Н. Оков, И. В. Туринцев. Цифровая стеганография. – M.: СОЛОН-Пресс, 2002. – 261 с.
- 8. Portal safety: Cryptography and steganography [Electronic resource]
http://bezpeka.com/ru/lib/sec/crypt.html - 9. Information counteraction to threats of terrorism [Electronic resource]
http://www.contrterror.tsure.ru/ - 10. Konfident - systems of safety[Electronic resource]
http://www.confident.ru/magazine