The abstract of master's qualifying work
Development models and methods for establishing a system of information security corporate network, taking into account different criteria
Introduction
The modern society is characterised by high degree of information, and it does its dependent on security of an information technology. Computer systems and telecommunications provide reliability of functioning of a large quantity of information systems most of different function. The majority of such systems bear in itself the information having confidential character. Thus, the decision of a problem of automation of processes of data processing has caused a new problem — a problem of information safety. [1] thus it is necessary to consider that information loss in the personal computer as a result of virus penetration is notable for its owner, but infringement of work of systems of the government, life-support systems touches interests of a society, and creates a national problem.
Urgency
Many operations are written about importance of implantation to intelligence systems of protection frames. But till now it is impossible to select the universal method, allowing to create an optimal protection system of the information. It occurs that any intelligence system has the features in the architecture, ways of data processing, a degree of criticality of the information and in many other things. Besides, each sphere has the criteria of an optimality. Therefore development of an optimal protection system of the information for certain type of intelligence systems is an actual problem for today.
The purposes and problems
The work purpose is the сhoice an optimal system of protection of the information for corporate system of the Donetsk regional centre of estimation quality formation. The tasks solved in Master's Qualification Work:
- studying informational structure of corporate system;
- the analysis threats of informational safety ;
- building a model of an estimation of cumulative cost of possession;
- development of mathematical model of an estimation of a system effectiveness of informational safety;
- synthesis of variants of system of informational safety and a substantiation of an optimal variant.
Prospective scientific novelty
Prospective scientific novelty of operation consists in the following:
Предполагаемая научная новизна работы заключается в следующем:
- Ordering of various criteria of an optimality of a protection system of the information.
- Creation of the simulation model of a protection system of the information on the basis of various criteria.
- Development of the circuit of a choice of this or that criterion of an optimality depending on sort and intelligence system tasks
Development of mathematical model of an estimation of a system effectiveness of informational safety
In a general view the process model of protection of the information in ИС can be presented how it is shown in a figure 1.
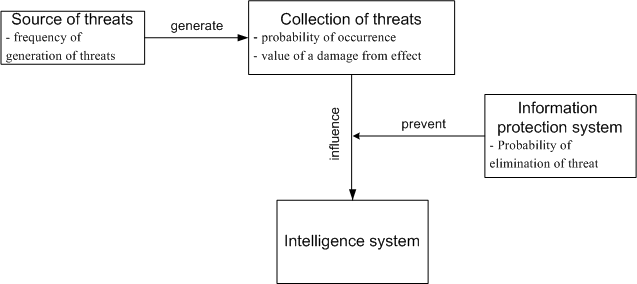
Figure 1 - The common model of a protection system of the information
ЗThe malefactor, using some source of threats, generates a collection of the threats everyone i-я threat it is characterised by probability of occurrence Pвоз i and the value of a damage ΔWвоз i from effect on an intelligence system. The information protection system is characterised by probability of elimination i-й threats Pпарвоз i.
Let's enter into system criteria of an optimality. П The prevented damage from effect of i th threat we will designateм ΔWi, and the common prevented damage W. Under condition of independence and additivity of threats:
W=∑ Pвоз i • Pпарвоз i • ΔWвоз i
Now we can formulate in a general view the task of synthesis of protection frames of the information in an intelligence system. It looks like the following: it is necessary to select a variant of implementation of a protection system of the information, providing maximum of the prevented damage from effect of threats at admissible expenses for information protection frames. Formal setting of the task looks like:
Find
T0 = arg maxW(T), T0 ∈ T+
at limitation C(T0) ≤ Cдоп
Here Т - some vector characterising a variant of technical implementation of a protection system of the information;
T+T0 - admissible and optimum value of a vector Т;
Cдоп - admissible expenses for an information protection system. [3]
The simulation model
On the basis of the considered mathematical model the simulation model. The information protection system is presented in the form of the model consisting of some kit of protection. On an input of protection frames streams of inquiries of unauthorized access arrive. Further these streams are rarefied, forming an output stream.
The probability of support of protection is considered as probability of absence of inquiries to protected resources and defined as follows:
Z(t) = 1 - F(t)
Where is function of distribution of a random variable τнсд ((time between two next admissions streams of inquiries of unauthorized access). As stream streams of inquiries of unauthorized access is distributed under the law of Puassona, the security estimation can be received under the following formula:
Z(t)= e - ∑λiqit
Intensity of a stream of the skipped inquiries:
H(t)=∑λi⋅qi⋅t
To have possibility to estimate security of an intelligence system, it is necessary to know following metrics: probability of protection, average time, between the skipped inquiries, intensity of a stream of the skipped inquiries. [4]
During operation the simulation model has been created, allowing to obtain the given metrics of system. The model circuit is presented in a figure 1.
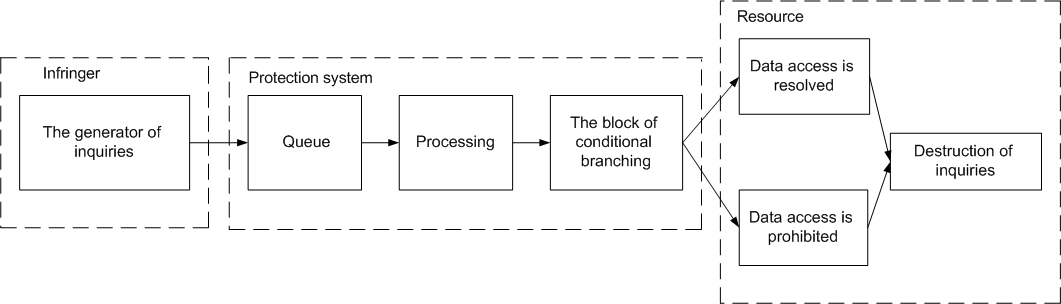
Figure 2 - The simulation model of a protection system of the information
The model consists of three blocks: "Infringer", "Protection system", "Resources". The first block describes operations of the infringer, namely generation of inquiries НСД. Generation is characterised by intensity λ. Block "Protection system" imitates queue of inquiries НСД on protection logon, processing of each inquiry, and also with specified probability eliminates inquiries НСД. Block "Resources" is used for the statistical information on quantity of skipped inquiries НСД and for their leadingout from model. This statistics also allows to define protection system key parametres.
For model construction programming language GPSS was used. Possibility of manifestation of threat is considered as casual events. Let time between inquiries НСД is arranged on an exponential low, and average intensity of a stream - 60 with. Then, having accepted an assumption that demand processing time makes 1 with, and with probability 0,9 inquiry will be neutralised, we can промоделировать system throughout 100000 with. As a result following results are received: intensity of a stream of skipped inquiries Н=0,01, average time between skips of inquiries: τнсд=593 seconds, the standard form has the schedule of a probability distribution of protection.
Conclusion
Further it is planned to construct on the basis of criterion of security some various variants of system of protection of the information and to estimate the risks arising during their operation, by means of the matrix approach described in article "Informatio security risk analysis - a matrix-based approach". [5]
At creation of mathematical model of definition of security and safety of corporate system, and also at an estimation of risks the real corporate system of the enterprise "Donetsk regional centre of estimation of quality of formation" will be used. On its example aspects of technical reliability of topology of a network, and also aspects of information safety of a corporate network of the enterprise will be considered.
References
- Зегжда Д.П. Принципы и методы создания защищенных систем обработки информации / Д.П. Зегжда // Дис. д-ра техн. наук - Санкт-Петербург, 2002 380 c.
- Домарев В.В. Безопасность информационных технологий. Системный подход./ В.В. Домарев – К.: ООО ТИД Диа Софт, 2004. –992 с.
- Personal site ukrainian leading expert in the field of information tehnologies V. Domareva http://www.security.ukrnet.net/
- Карпов В.В. Вероятностная модель оценки защищенности средств вычислительной техники с аппаратно-программным комплексом защиты информации от несанкционированного доступа/ В.В. Карпов // «Программные продукты и системы» № 1, 2003 год.
- Sanjay Goel Information security risk analysis - a matrix-based approach / Sanjay Goel, Vicki Chen
At writing of this abstract of thesis master's degree work is not yet completed. Final completion: December, 2009. Complete text of work and materials on the topic can be got for an author or his leader after the indicated date.



