Abstract
Contents
- Introduction
- 1. Theme urgency
- 2. Goal and tasks of the research
- 3. Research of DDoS-attack and struggle with them
- Conclusion
- References
Introduction
One of the most urgent tasks in the service of providing information is a DDoS-attack. The essence of these attacks is to ensure that all available ways to reduce the amount of payload to the resource, or even make it inaccessible.
Denial of service can be reached in different conditions, the reasons are: the errors in the software that runs on the victim service, network protocol weaknesses and limitations in the bandwidth of communication, as well as ill-conceived network infrastructure. Typically, DDoS-attack is can be reached with help of botnets, it is quite a large number of computers and smartphones infected with malicious software.
1. Theme urgency
This problem arose with creation of the Internet and become more actual in connection with the development and expansion of the global network. On the market there are open source software solutions that can handle only simple cases of DDoS-attacks. Hardware solutions have closed algorithms.
Master's thesis is devoted to studying the sources of unwanted traffic, and their parameters, create a model of corporate network in which there is a web server (handles requests from the outside), the creation of an algorithm to distinguish unwanted traffic generated botnet.
2. Goal and tasks of the research
The aim of the research is to develop a model of corporate networks and algorithms for filtering unwanted traffic.
Main tasks of the research:
- Analysis of the structure and model parameters of the corporate network.
- Research of data that received in the simulation to create the algorithm.
- Creating algorithms filter out unwanted traffic.
- Evaluating the effectiveness of the proposed algorithms.
Research object: algorithm for filtering unwanted traffic.
Research subject: evaluation of methods for filtering unwanted traffic, and their effectiveness.
3. Research of DDoS-attack and struggle with them
According to the analytical reporting of company "Kaspersky Labs" — DDoS-attack the second half of 2011, it is clear that the leader of many sources of DDoS-attacks are Russia and Ukraine. This suggests that viral activity and the number of infected computers in these countries are at a high level, so does this mean that they are using a sufficiently large number of outdated software and attackers can use this critical vulnerability. These indicators are provided increase in amount of families who have had access to the Internet and low computer competence.
According to the company Arbor 35% of attacks were provoked by ideological or political reasons, 31% were substantiated as nihilism. Attacks are also service providers of mobile services such as email, internet access, have been noticed attacks on client devices.
As for the communication channels, the new standard in speed of nonuseful traffic is 10 Gb/s. The maximum speed that were noticed — 60 Gbit/s and 100 Gbit/s. Also in the latest report from detected first attack that using a protocol IPv6.
For the detection of DDoS-attacks, the following methods: statistical — based on the analysis of statistical parameters of traffic deviation from the mean values, static — is based on black and white lists, including those generated by user applications through the API; behavior - based on an analysis of compliance or noncompliance with the specifications applied protocols signature: based on an analysis of the behavior of individual bots [3].
Considered the the causes and issues that should be solved in the fight with this type of attack, we can define methods for solving these problems. All market solutions for protection from DDoS-attacks can be divided into three parts: software solutions - the most common in the market, often it is set of rules to filter traffic, which are made by the developer on personal experience. There are also solutions with open source software (such as DDoS Deflate), but it has very simple static method of filtering (white and black lists) over IP, based on the number of connections from one IP. This solution is quite simple to install directly on the server, but can help only with simple DDoS-attacks. The solution completely ineffective in scale of data centers, hardware solutions — used to protect large-scale network infrastructures, such as: traffic exchange points, data centers, etc. A typical scheme of such solutions is shown in Figure 1, where A — traffic which generate real client, B — unwanted traffic, C — Internet, D — telecommunication system, E — victim, F — device traffic analysis, G — device of decision-making.
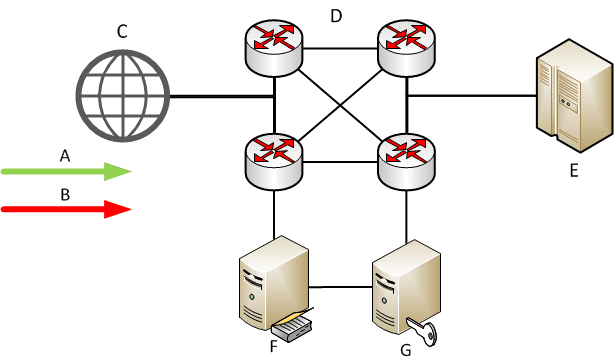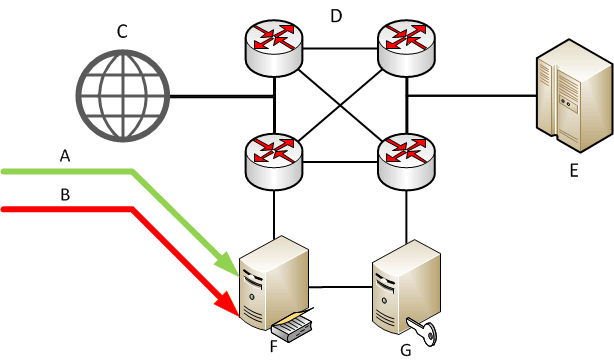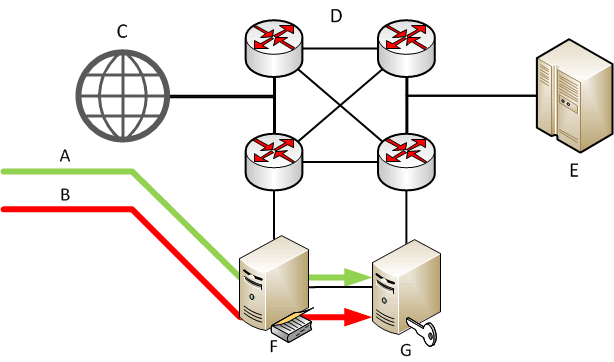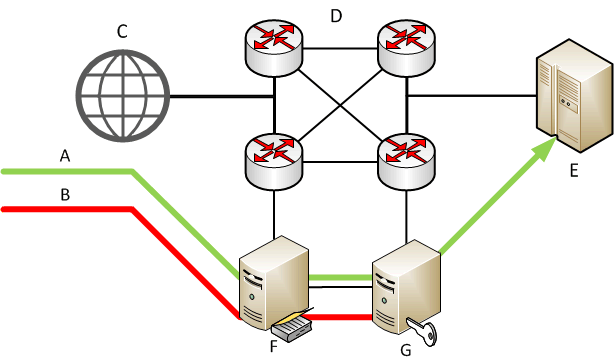
Figure 1 – Standard diagram of a hardware security solutions from DDoS-attacks (animation: 4 frames, 15 loops, 92.6 Kb)
Usually, the scheme consists of two devices: a device traffic analysis, which is duplicated on all the traffic that comes in a data center, and device of decision-making, which blocks unwanted traffic, based on analysis of data obtained by data collection device. Sometimes these solutions are combined in a single device such as solutions from Cisco, which in the absence of active attacks, works in a mode the accumulation of information about the payload, and in case of malicious activity changes and begins routing traffic filtering.
Conclusion
The abstract reviewed the causes of DDoS-attacks, their motivation and how to create them, it is shown that the problem is more important today, although there are already market leaders in the field, they provide closed solutions, which are protected by a patent or not disclosed informaton about it at all. In contrast, solutions with closed-source, open recommendations can result in methods and algorithms to the unified standard that will allow equipment manufacturers and software solutions share knowledges more effectively for solving that problem.
Master's work is devoted to actual scientific problem of combining the basic methods of minimizing the instrumental Moore automata. In the trials carried out:
- Obtain a classification of methods of DDoS-attacks.
- The existing solutions as software and hardware are reviewed.
- Created simple model of DDoS-attacks on the intranet intranet.
Further studies focused on the following aspects:
- Finalization the model corporate network to be able to simulate most of the possible methods of DDoS-attacks.
- Creating algorithms for filtering unwanted traffic.
- Evaluating the effectiveness of the algorithms and their optimization.
This master's work is not completed yet. Final completion: January 2013. The full text of the work and materials on the topic can be obtained from the author or his head after this date.
References
- Stopping & Preventing DDoS Attacks // Arbor Networks [Электронный ресурс]. — Режим доступа: http://www.arbornetworks.com/
- Behavior analysis techniques in DDoS mitigation // Black Lotus [Электронный ресурс]. — Режим доступа: http://www.blacklotus.net/
- DDoS-атаки второго полугодия 2011 года // Лаборатория Касперского [Электронный ресурс]. — Режим доступа: http://www.kaspersky.ru
- Worldwide Infrastructure Security Report 2011 Volume VII // Arbor Networks, 2011. — 72 c.
- M. Abliz Internet Denial of Service Attacks and Defense // Pittsburgh : University of Pittsburgh Technical Report [Электронный ресурс]. — Режим доступа: http://www.cs.pitt.edu/
- J. Mirkovic, P. Reiher A Taxonomy of DDoS Attack [Электронный ресурс]. — Режим доступа: http://www.eecis.udel.edu/
- L. Feinstein, D. Schnackenberg, R. Balupari, D. Kindred Statistical Approaches to DDoS Attack Detection and Response. // DARPA Information Survivability Conference and Exposition [Электронный ресурс]. — Режим доступа: http://www.cs.unc.edu/
- J. Ioannidis, S. Bellovin Implementing Pushback: Router-Based Defense Against DDoS Attacks // AT&T Labs Research [Электронный ресурс]. — Режим доступа: http://www.cs.columbia.edu/
- A. Yaar, A. Perrig, D. Song Pi A Path Identification Mechanism to Defend // Carnegie Mellon University Research Showcase [Электронный ресурс]. — Режим доступа: http://repository.cmu.edu/
- K. Park, H. Lee On the Effectiveness of Route-Based Packet Filtering for Distributed DoS Attack Prevention in Power-Law Internets // West Lafayette : SIGCOMM’01 [Электронный ресурс]. — Режим доступа: ftp://mail.im.tku.edu.tw/
- A. Keromytis, V. Misra, D. Rubenstein SOS: Secure Overlay Services // SIGCOMM’02 [Электронный ресурс]. — Режим доступа: http://utd.edu/
- Worldwide Infrastructure Security Report // Arbor Networks [Электронный ресурс]. — Режим доступа: http://www.arbornetworks.com/report
- С.М. Цирульник, Д.В. Кисюк, Т.О. Говорущенко DDoS-атаки й методи боротьби з ними [Электронный ресурс]. — Режим доступа: http://www.nbuv.gov.ua/
- О. Ігнатенко Атаки на відмову: виникнення проблеми, огляд атак, класифікація [Электронный ресурс]. — Режим доступа: http://eprints.isofts.kiev.ua/
- М. Кадыров, А. Труфанов, Р. Умеров Внедрение облачных вычислений как метод предотвращения DDoS-атак [Электронный ресурс]. — Режим доступа: http://www.uintei.kiev.ua/
- С.Л. Михайлюта, І.В. Степанушко, Б.О. Бабич Захист інтрамереж від DOS- та DDOS-атак [Электронный ресурс]. — Режим доступа: http://www.nbuv.gov.ua/
- У.О. Яциковская, Н.П. Карпинский Моделирование сетевого трафика компьютерной сети при реализации атак типа DoS/DDoS [Электронный ресурс]. — Режим доступа: http://www.nbuv.gov.ua/
- С.Л. Михайлюта, И.В. Степанушко, Б.А. Бабич, В.Ю Ткаченко, В.С. Лавринович Исследование сетевых DOS-атак, основанных на использовании протокола ICMP [Электронный ресурс]. — Режим доступа: http://www.nbuv.gov.ua/
- Д.Н. Борисов Энтропия как индикатор возникновения аномалий сетевого трафика [Электронный ресурс]. — Режим доступа: http://ea.donntu.ru/
- T.А. Приходько Исследование вопросов безопасности локальных сетей на канальном уровне модели OSI [Электронный ресурс]. — Режим доступа: http://ea.donntu.ru/
- М.С. Филенко Распределенные атаки типа «отказ в обслуживании» [Электронный ресурс]. — Режим доступа: http://masters.donntu.ru/
- С.А. Брич Интегрированная модель противодействия атакам в социотехнических системах [Электронный ресурс]. — Режим доступа: http://masters.donntu.ru/
- J. Mirkovic, P. Reiher, G. Prier Attacking DDoS at the Source [Электронный ресурс]. — Режим доступа: http://www.cs.unc.edu/
- Д.В. Домарев Математическое описание процессов атак на компьютерные сети [Электронный ресурс]. — Режим доступа: http://www.nbuv.gov.ua/
