Systems of technical information protection and automation of ITS processing
Investigation methods of decision making, to protect information that is processed in computer networks
Application in everyday life as a single person , and the state as a whole, modern information and communication technologies can receive all the benefITS of modern science and technology. Thus all significant increasing dependence of human processes of environmental information space. This dependence gives rise to new types of threats – cyber crime. Development of effective models and methods of safety management of telecommunications systems to counter cyber crime is an urgent task.
Given the wide array of businesses and individuals who provide services, equipment and software used in the field of Telecommunications International Telecommunication Union in recommendations ITU‑T X.805 he proposed security architecture for systems providing communication between end devices (Figure 1). This architecture allows for the detailed components of ITS, in order to facilitate decision‑making for the effective management, control and use of network infrastructure, services and applications. Security architecture provides a comprehensive, top‑down cross‑cutting area of network security and can be applied to network elements, services and programs in order to identify, predict and correct the vulnerability protection [3].
Using this architecture, it is possible to obtain a quantitative assessment of the vulnerability of a specific asset from a threat by the following formula:
Weighting factor pk determines the frequency of this threat on a set of possible threats and calculated based on the analysis of statistical data or using known techniques. Factor zk determines the probability of asset protection TCS through a regular means of protection against the threat pk [2].
Determination of total asset vulnerability to possible threats Ql define as follows:
Each of the layers of protection that is presented in Figure 1, consists of a limited number of assets. Therefore, to determine the overall assessment of the level of protection of one Qp use the following formula:
Based on the obtained quantitative evaluation of security assets of a decision on risk-taking. The algorithm of this process is shown in figure 2.
The proposed algorithm estimates and risk-taking can be used for all considered levels of protection for all three planes of protection.
Determining the weighting coefficients ak, ck, ik, sk – should be conducted by a group of appointed experts.
The next step is to determine for each asset Ai threats - evaluation according to the probability and the use of existing ITS vulnerabilities and existing remedies. That group of experts assesses the threats according to three parameters:
When these factors are zero, then we assume that the asset is fully protected from this threat, and in the case when the coefficients are equal to unity - the asset must be made threat. So you can imagine graphically threat of a point in three-dimensional space, and the farther it is from the origin, the greater the importance of the asset, ie the total threat assessment will be calculated as the length of the segment line connecting the origin and the resulting point.
That is, for threat assessment will use the following formula:
Graphically, this result is shown on figure 3.
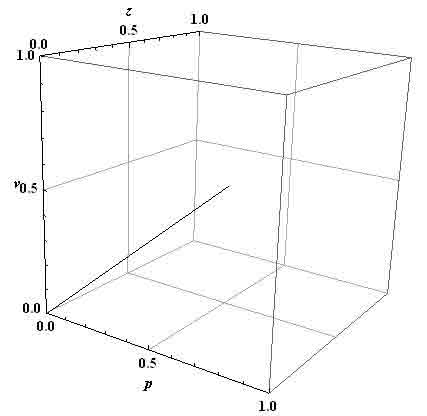
Schedule all k-'s threats to the j-th asset is shown in figure 4.
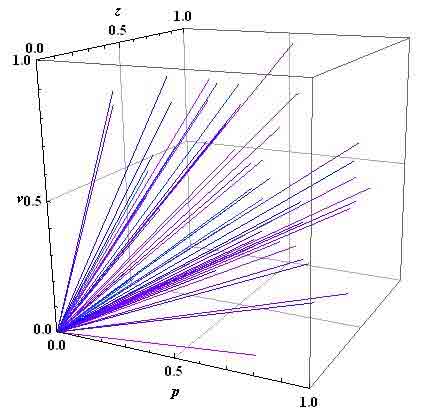
From this we can conclude that all the threats that affect the assets, in the aggregate will have some kind of surface. Type of surface threats affecting the asset is shown in figure 5.
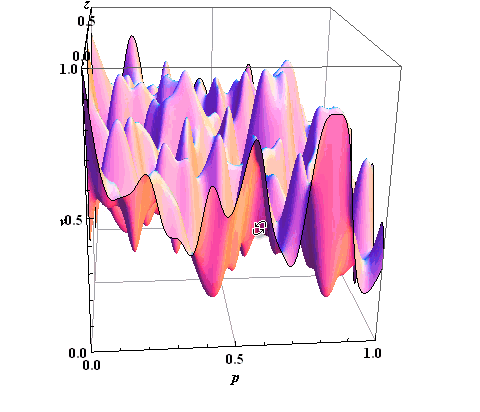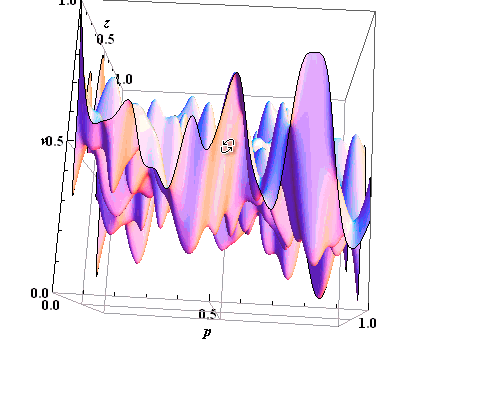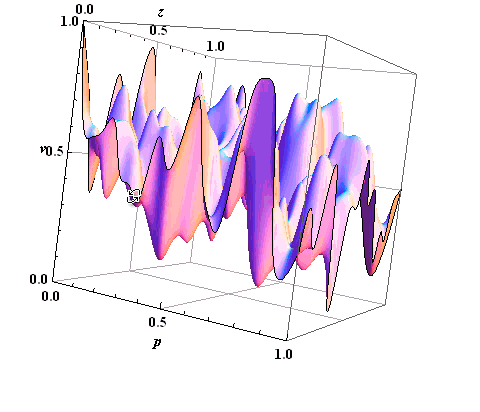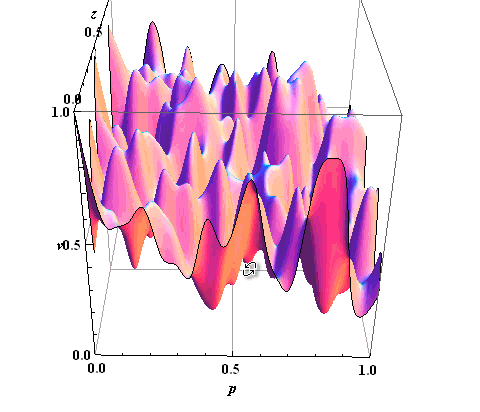
Experts (E) on the basis of knowledge obtained and graphs put down points to possible threats on 100 point scale, with a dash assessment on different characteristics of data - table 1.
| Threats | Experts (Е) | Assessing the impact of threats to property assets | ||||
| c | i | a | s | Number of points | ||
| Analysis of protocols | E1 | 20 | 10 | 30 | 20 | 80 |
| E2 | 35 | 10 | 25 | 20 | 90 | |
| E3 | 20 | 10 | 25 | 15 | 70 | |
| E4 | 25 | 5 | 20 | 20 | 70 | |
For further analysis conduct standardization (normalization) expert assessments.
| Threats | Experts (Е) | Assessing the impact of threats to property assets | ||||
| c | i | a | s | Number of points | ||
| Analysis of protocols | E1 | 0.25 | 0.125 | 0.375 | 0.25 | 1 |
| E2 | 0.39 | 0.1 | 0.282 | 0.228 | 1 | |
| E3 | 0.286 | 0.143 | 0.357 | 0.214 | 1 | |
| E4 | 0.286 | 0.071 | 0.357 | 0.286 | 1 | |
To construct the generalized use of expert evaluation method of pairwise comparisons.
To do this ranking assessments of each expert:
Then draw up a matrix of pairwise comparisons of each expert by the following formulas:
where:
Then:
| Expert 1 | c | i | a | s | Expert 2 | c | i | a | s | Expert 3 | c | i | a | s | Expert 4 | c | i | a | s |
| c | 1 | 1 | 0 | 1 | c | 1 | 1 | 1 | 1 | c | 1 | 1 | 0 | 1 | c | 1 | 1 | 0 | 1 |
| i | 0 | 1 | 0 | 0 | i | 0 | 1 | 0 | 0 | i | 0 | 1 | 0 | 0 | i | 0 | 1 | 0 | 0 |
| a | 1 | 1 | 1 | 1 | a | 0 | 1 | 1 | 1 | a | 1 | 1 | 1 | 1 | a | 0 | 1 | 1 | 1 |
| s | 1 | 1 | 0 | 1 | s | 0 | 1 | 0 | 1 | s | 0 | 1 | 0 | 1 | s | 1 | 1 | 0 | 1 |
The next step is necessary to sum up all the elements in the matrix, that formula has the form:
where:
Sij – matrix elements are summarized;
k – number of expert.
The result has the form:
| Sum | c | i | a | s |
| с | 4 | 4 | 1 | 4 |
| i | 0 | 4 | 0 | 0 |
| a | 3 | 4 | 4 | 4 |
| s | 2 | 4 | 0 | 4 |
The resulting matrix is given by the rule:
where d – number of experts.
| Result | c | i | a | s |
| с | 1 | 1 | 0 | 1 |
| i | 0 | 1 | 0 | 0 |
| a | 1 | 1 | 1 | 1 |
| s | 0 | 1 | 0 | 1 |
For each characteristic asset TCS obtain the result in points - table 3.
| Characteristic | Points |
| c | 3 |
| i | 1 |
| a | 4 |
| s | 2 |
Further use of these marks, do their normalization – table 4.
| Characteristic | Points |
| c | 0.75 |
| i | 0.25 |
| a | 1 |
| s | 0,5 |
This master's work is not completed yet. Final completion: December 2014. The full text of the work and materials on the topic can be obtained from the author after this date.
plan-do-check-act// Наукові праці Донецького національного технічного університету. Серія: Обчислювальна техніка та автоматизація. Випуск 25. - Донецьк, ДонНТУ, 2013. - c. 104-110. (Режим доступа)