Abstract
Content
- Introduction
- 1 Relevance of the topic
- 2 Purpose and objectives of the study, expected results
- 3 Method of work existing systems for protection against unauthorized voice access
- Conclusions
- List of sources
introduction
At present, due to the wide spread of computer technology and their use in various areas of life, particularly acute question of the limitation of user access. In this increasingly standard password protection systems are replaced or are supplemented by biometric systems identify users. The term biometrics
refers to the measurement of certain anatomical or physiological parameters of the person. If ordinary password can be stolen or to pick up something to deceive a biometric system is almost impossible. At the moment, as the measured parameters using different human traits such as voice, fingerprint, iris, signature and style keystrokes, as well as appearance. Each of these characteristics allows to select a specific person from tens, hundreds or more people. It is also possible the integrated use of multiple parameters.
1 Relevance of the topic
Actual problems for modern society of today, were the issues of non-verbal communication, this fact indicates that great importance attaches to the knowledge of the voice with the help of which you can identify [2].
2 The purpose and objectives of the study, expected results
The purpose of our research is: using a software product VoiceSec 1.0.1.149 systems of protection of personal computer from unauthorized access on the basis of spectral analysis of your voice to develop a block diagram of a subsystem of CAD, reflecting the composition of technical means, software, mathematical, information and methodological provisions that apply when implementing protection against unauthorized access on the basis of spectral analysis of your voice.
The main objectives of the study:
- Explore different voices of male and female users.
- To make the classification, organize, and encode the necessary information on project design.
- To develop software to protect against the unauthorized access based on the analysis of the user's voice and to choose the optimal method to protect your computer [1]
3 Method of work existing systems for protection against unauthorized voice access
Most biometric security systems operate in the following way: in the database of the system stores a digital fingerprint, iris or voice. People who are going to access computer networks, using a microphone, a fingerprint scanner, or other devices enter information about themselves into the system. The received data are compared with the sample stored in the database. In detecting sample is in the process, the first step of which is the initial transformation of the input information to reduce the volume processed so that it could be the subject of analysis. The next step is a spectral representation of the speech obtained by Fourier transform. Spectral performance is achieved by using wide-frequency analysis of the recording. Although spectral representation of speech is very useful, it is necessary to remember that the studied signal is quite diverse. The variety occurs for many reasons, including:
– the differences of human voices;
– the level of speech of the speaker;
– variations in the pronunciation;
– the normal variation in movements of the articulators (tongue, lips, jaw, palate).
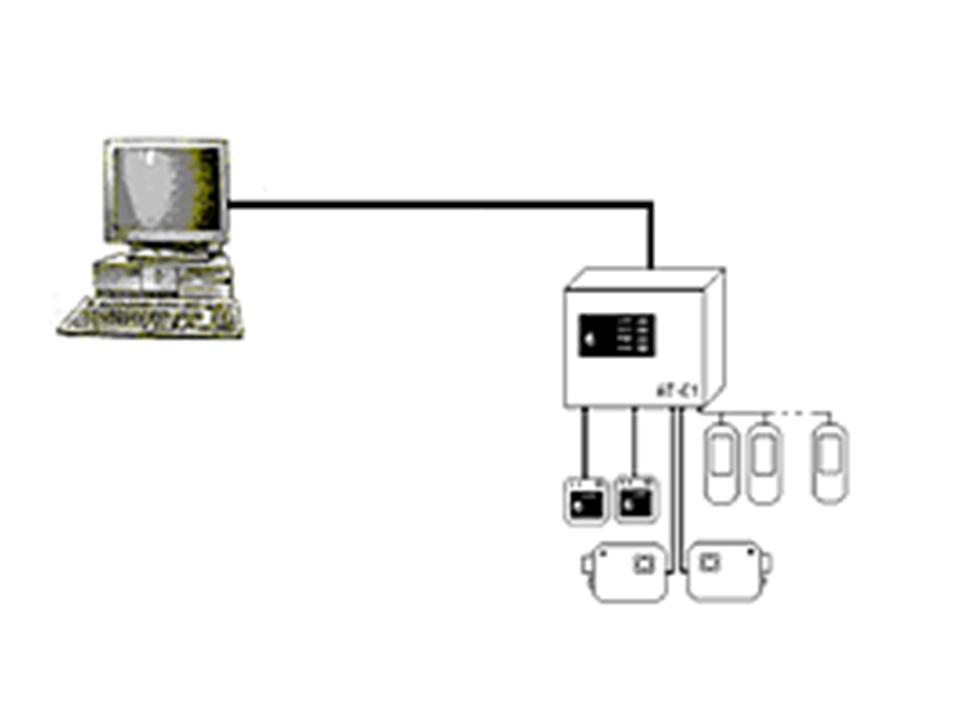
Figure 1 — Scheme simple
security system
conclusions
In this abstract we have received the result of the research, a positive economic effect, which proves the validity of subsystem development CAD personal computer protection from unauthorized access on the basis of spectral analysis of your voice.
In recent times considerable advances have been made in identification by voice and other modalities. However, there is ample reserves for increasing the reliability of biometric identification. So, promising directions of development of identification are to improve the quality of the original biometric samples; extracting a more robust identification of signs and their combinations; implementation of multi-modal mix not on grade level, and at the level of signs of different modalities. Currently at the Department of Radioengineering and information protection works on study and upgrade of existing systems identification of the human voice.
When writing this abstract the master's thesis is not finished yet. Final end: May, 2017. The full text of work and materials on a subject can be received at the author or his head after the specified date.
List of sources
- Sapogkov M. A Protection circuits radio and wire communication from interference and noise. – М.: 1959. 254 с.
- GOST 21655–87. Channels and paths backbone primary network of the Unified automated communications system. Electric parameters and methods of measurements.
- Spesivcev A. B. – Information protection in personal computers. – М.: Telecommunication, – 1992, 378 с.
- Ways of protection of information objects from information leakage through technical channels: screening [Electronic resource]. – Mode of access: bnti.ru/showart...
- A real engineer should be able to distinguish the cable from the cable [Electronic resource]. – Mode of access: rts.ua/rus...
- Electrostatic field [Electronic resource]. – Mode of access: megabook.ru/
- Nyithli Ф, Kim Philby, the KGB Superspy. – М.:The Republic Of Belarus, 1992, 127 с.
