Abstract
Content
- Introduction
- 1. Theme urgency
- 2. Goal and tasks of the research
- 3. Chance of telecommunications network protection from specific threats specific remedies
- Conclusion
- References
Introduction
Development of information and telecommunication systems in the modern world is becoming more important. Information technology is used in the processes of public administration, business management, production processes meet the needs of citizens to have free access to information that promotes the development of information, telecommunications and information technology systems (ITS). Dissemination ITS infrastructure can reduce the distance between the interacting entities, reduce the time to exchange information and, as a consequence, to accelerate the process of managerial decision–making in government, local government and business.
A huge number of transactions that simplify our lives, provide modern telecommunications. It is difficult to imagine numerous service internet banking, various online shops, a huge amount of business transactions carried out with the help of local and global data networks.
Modern requirements for processing information lead to a merger of information and telecommunication systems, the use of publicly available communication channels , and as a consequence — leads to an increase in threats to the species and ITS increase of attacks on these system. Information and telecommunication systems are increasingly important in today's world.
The rapid development of the level of data transmission networks, rapid development is observed in the area of Internet fraud. More new techniques and methods developed daily "Hacker" is not authorized for entry into any system and benefit.
In recent years a very important question is a detailed analysis of threats to the security of information technology systems, the probability of their occurrence, the probability of their existing prevention means for preventing threats. A huge amount of complex information protection systems have been developed by experts in the field of information security, held many practical tests. However, the question of the theoretical calculation of network security data remains open.
1. Theme urgency
Currently known by a number of methods for determining the probability of protection of telecommunication systems from external influences. Was investigated efficiency many methods, the appropriateness of their use in specific environments and situations. Most methods have significant efficiency factor, but for the most accurate and flexible technique, an integrated approach to the development of the algorithm for determining the specific network security threats existing specific remedies.
This master thesis is devoted to the actual task of developing the algorithm for determining the probability of security information and telecommunications from existing threats modern remedies. The developed algorithm is designed to more effectively build complex information protection systems in data networks, reducing the economic costs of the creation of such systems.
For analysis will be used hardware and software and hardware products from leading manufacturers of network resources protection. As theoretical material will be used tutorials authoritative publications, scientific articles and publications specialists in the field of information security.
2. Goal and tasks of the research
The purpose of this study is to determine the probability of the development of security information and telecommunications network from specific threats specific remedies.
The main objectives of the study:
- Analysis methods for determining the likelihood of security telecommunications networks proposed by previous authors.
- Evaluation ways to optimize hardware costs to increase the quality of work, speed and overall performance to ensure network security.
- Combining the different methods of calculating the security and protection of information in data networks with different characteristics and operating conditions of these networks.
- Developing a more accurate algorithm for determining the probability of security information and telecommunications network from specific threats specific remedies, generating recommendations for the use of this technique.
Object of research: protected information and telecommunication system.
Subject of research: combining methods for calculating the probability of security telecommunications network specific remedies.
3. Chance of telecommunications network protection from specific threats specific remedies
Choice of means of protection against unauthorized access (UAA) and managing information security in information and telecommunications system (ITS) — a complex dynamic process. Given that distributed ITS complex, multilevel system of architecture, then the optimal decision for the organization of protection it is advisable to divide it into its constituent parts. For each component of the system defines the rules, processes and procedures necessary for good governance. This allows you to make the right decision, favors the choice of the most appropriate component of protecting a particular segment of the system.
From the viewpoint of information security for any organization, the most vulnerable places in the ITS are areas on the borders separating the liability of owners. An example of this point can serve as a place to connect the internal LAN institution (enterprise) to a telecommunications system (Fig. 1).
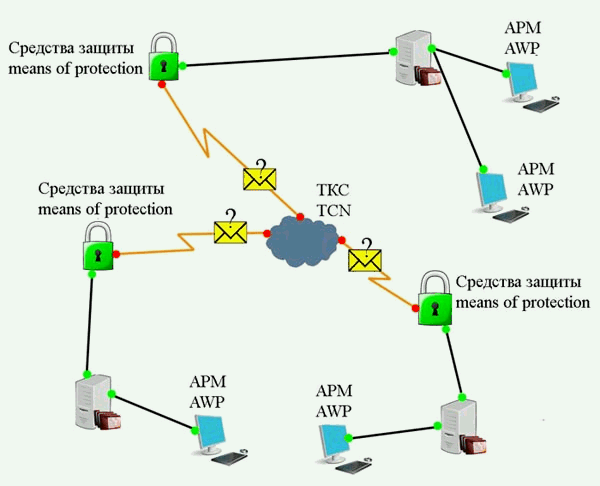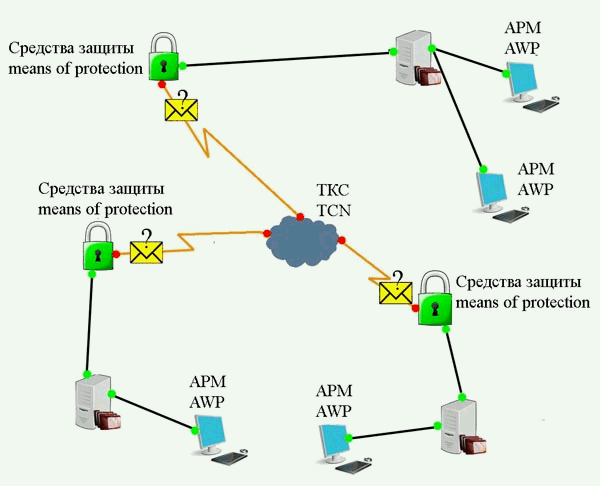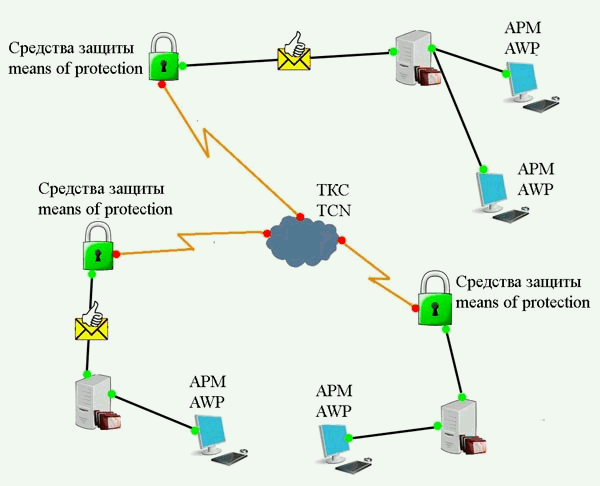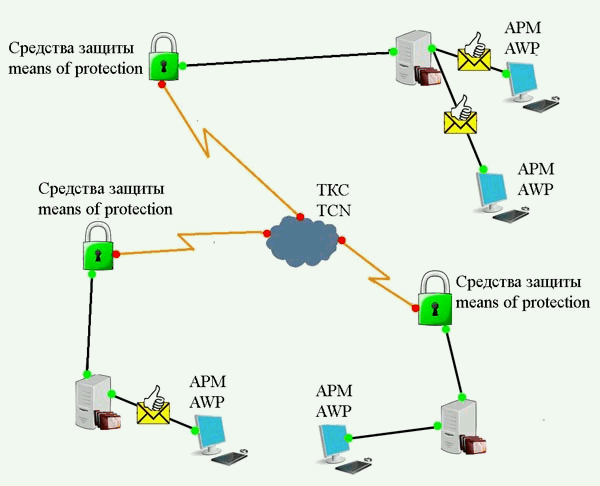
Figure 1 —
Block diagram of
the ITS
(animation: 4 frames 7 cycles of repetition, 145 kilobytes)
Involved in information processing
divisions and workstations (AWS) individual users who are
located at a
considerable distance from each other, leading to the need to use as
channels of communication and telecommunication systems (TCS)
located
outside the controlled area.
Therefore, one of the top priorities when deciding on the organization LAN security institution (enterprise) or a single user workstation, is to install adequate software or firmware remedies necessary to meet the basic requirements:
- achieve the necessary level of protection in accordance with the value of information to be protected;
- providing a predetermined level restrictions information activities of users and other [1].
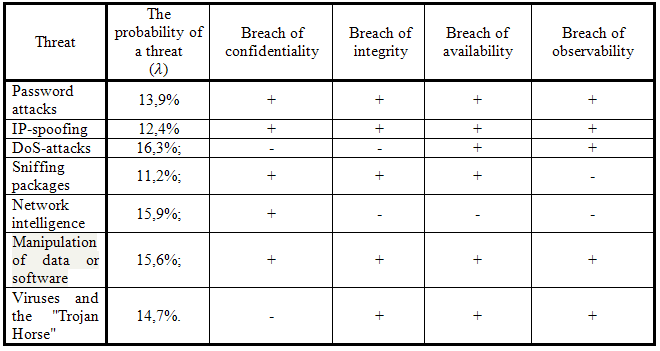
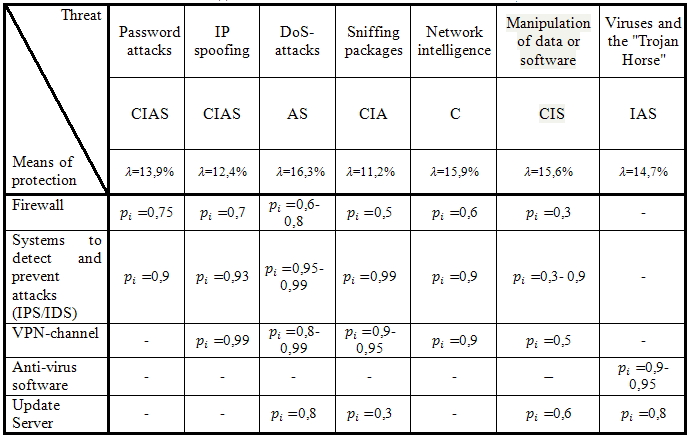
Table 1 presents the three most common classes of risks that can be implemented using an interworking protocols [2], and assess their impact on the basic properties of information.
Must take into account the fact that not all threats ITS can be fully realized or realized at all in the network, the same type of threat may cause significant or minor damage. Therefore, a decision on the information security management when selecting protective measures should define the degree of risk posed by a particular threat to network and information circulating in it [3].
Table 1
Classes of threats to information security in ITS
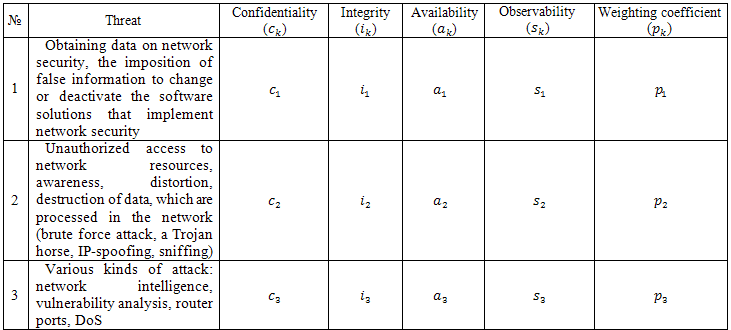
Based on the table, possible threats to the same properties of information as confidential (ck), integrity (ik), availability (ak) and observability (sk) information. Moreover, the level of threat information for these properties is determined by expert evaluation of the five-point scale:
- 0 – actually realized the threat does not bear losses;
- 0,25 – realized the threat carries no significant losses;
- 0,5 – realized the threat of losses to the average degree;
- 0,75 – implemented threat incurs significant losses;
- 1,0 – implemented threat brings irreparable losses.
Weight coefficient (pk) threats is proposed to determine the basis of the frequency of occurrence of the threat, relying on statistical information based on estimates or projections.
For this coefficient must meet the following conditions:
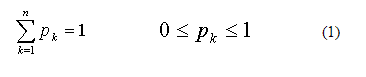
Proceeding from the known data for the properties of the level of threat information provided by experts and available weight, get a numerical value for the level of security threat information from consideration:
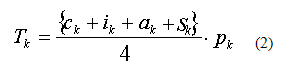
Based on the functions performed by software and firmware protection, as well as the level of danger of the threat to information processed on a dedicated workstation or in a closed network, you need to calculate the expected security of the system from a plurality of possible threats using specific remedies [3]:
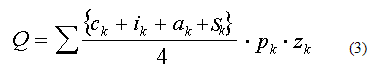
To this end, for each software or hardware and software remedies introduced numerical coefficient zk, allows to determine the probability of successful performance of functions to protect information on the specific threats considered.
One way of calculating the security is based on the calculation of the intensity of the violations and the intensity recovery of confidentiality, integrity, availability of resources and observability.
According to an article "Algorithm special security assessment information and telecommunication systems" (Author: Buryachok V.), recently the most widely used threats such as: selection of key / password (The password attack) — 13,9 % of the total; Replacement IP–address (IP spoofing) — 12,4 %; denial of service (DoS–attack) — 16,3 %; traffic analysis (packet sniffing) — 11,2 %; scan (network intelligence) — 15,9 %; substitution of data transmitted over the network (data manipulation and software) — 15,6 %; other methods (such as viruses and programs "Trojan horse") — 14,7 % [4].
Given the nature of the impact of these threats at the entrance to a local computer network, you can share them on the threat of a breach of confidentiality, integrity, availability and observability.
Level of information in a computer network is protected from unauthorized access is defined for each resource, designed to protect [5].
Therefore, to calculate the ratio of protection of confidentiality, integrity, availability and use of resources sposterezhenosti formula:
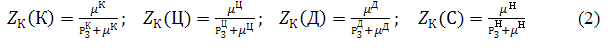
 — probability of
overcoming
all threats confidentiality, integrity and availability, and
observability, which may arise.
— probability of
overcoming
all threats confidentiality, integrity and availability, and
observability, which may arise.
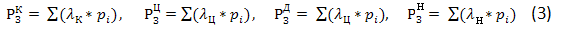
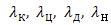 —
flux intensity threats confidentiality, integrity and
availability of resources and observability, respectively;
—
flux intensity threats confidentiality, integrity and
availability of resources and observability, respectively;pi — chance of countering the threat of k–type specific remedy.
Based on the data obtained
by the expert and the table 1,
we can make the following table showing
the relation remedies and possible threats to computer networks. From
this table, counting 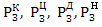
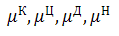 —
intensity recovery protection for confidentiality, integrity,
availability of resources and observability, respectively [5].
—
intensity recovery protection for confidentiality, integrity,
availability of resources and observability, respectively [5].
Coefficients 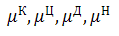 calculated
as follows:
calculated
as follows:
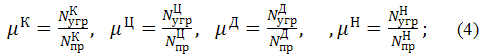
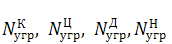 —
number of new threats that have emerged over time t.
—
number of new threats that have emerged over time t.
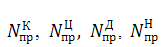 —
amount of interference threats developed during t.
—
amount of interference threats developed during t.
For brevity, we write the expression (2) as follows:
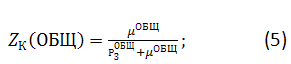
Given that a computer network protected status of all necessary resources and to protect the resources are not used for more alternative remedies need a formula for finding security proposed in Kozlenko A., Avramenko V., Saenko I., Kiy A. "A method of estimating the level of protection of information from unauthorized access to computer networks based on graph of security".
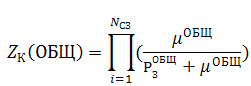
Zk (ОБЩ) — coefficient of computer network security,
Ncз — number of remedies.
Conclusion
Determination of the protection of telecommunication networks from external threats is one of the most important trends in information security sphere activities. This work contributes to building quality and flexible security systems telecommunication networks.
As part of the master's work were obtained actual scientific results in the following areas:
- Studied previously proposed approaches to determining the level of protection of the telecommunications network from external threats and attacks.
- Combined and codify the most relevant and flexible methods for assessing the security of the telecommunications network in a single algorithm.
- The results obtained when calculating the security of the proposed method.
- The estimation results, revision and improvement of the proposed method.
In writing this essay master's work is not yet complete. Final completion: December 2014. Full text of the work and materials on the topic can be obtained from the author or his manager after that date.
References
- Воропаева В. Я., Щербов И. Л. Адаптация информационно–телекоммуникационных систем к внешним воздействиям / Научные труды Донецкого национального технического университета. Серия: «Вычислительная техника и автоматизация». Выпуск 23 (201). — Донецк, ДонНТУ, 2012. — 83 c.
- The basic model of security threats personal data during their processing personal data information systems (extract) [electronic resource]. — Access mode: style="color:blue;">http://fstec.ru/component/attachments/download/289.
- Воропаєва В. Я., Щербов І. Л., Хаустова Е. Д. Управління інформаційною безпекою інформаційно–телекомунікаційних систем на основі моделі «PLAN–DO–CHECK–ACT» / Воропаєва В. Я., Щербов І. Л., Хаустова Е. Д. — Наукові праці ДонНТУ. Серія: обчислювальна техніка та автоматизація № 2 (25)’2013. — 7 с.
- Бурячок В. Алгоритм оцінювання ступеня захищеності спеціальних інформаційно–телекомунікаційних систем / Бурячок В. — Науково–технічний журнал «Захист інформації» № 3, 2011. — 9 с.
- Козленко А. В., Авраменко В. С., Саенко И. Б., Кий А. В. Метод оценки уровня защиты информации от НСД в компьютерных сетях на основе графа защищенности / Труды СПИИРАН, 2012. — 45 с.
