
Khamidullina Kateryna
Faculty of computer science and technology (CST)
Computer monitoring systems
Speciality «Computer-aided Monitoring Systems in Ecology and Economy»
Development of information security policies based on an assessment of losses associated with threats of information systems
Scientific adviser: Gubenko Natalia
Abstract
Abstract
on the theme of master's work
"Development of information security policy based on an assessment of losses associated with threats to information systems"
Goals and tasks
Master's thesis deals with the problem of information security (IS) of the enterprise. The basic properties of information (integrity, availability, confidentiality), as well as threats to information systems are considered.
Objective: development of an information security policy of the enterprise which takes into account the losses in the implementation of threats.
The main tasks of this work are:
- analysis of financial losses due to the implementation of information security threats;
- Prediction of the occurrence of dangerous events (associated with information security) in the enterprise
The relevance of the topic
Any business activities involve the receipt, storage and processing of information. Due to severe competition the loss from the implementation of information security threats can lead to serious problems in the sphere of business.
To observe and predict these threats without the use of special tools in the enterprise is becoming more difficult, so it seems clear that that the creation of a security policy based on an assessment of the losses, as well as the prediction of the threats has become a priority issue in the field of business.
In addition, the prediction of information threats can significantly minimize losses of the enterprise, which are based on threats to availability, integrity and confidentiality of information and properly organized information security policy reduces risk and accelerates the elimination of threats.
Expected scientific novelty
Expected scientific novelty lies in the systematization of forecasting methods and their implementation in information security policies and estimation of losses.
Planned practical results
As a result of this master's work it is expected to perform the following:
- analysis of prediction methods and the choice of the most appropriate ones;
- creation of a database for the prediction by the method of expert evaluations;
- development of information security policies based on the assessment of losses associated with the implementation of information security threats;
- analysis of the results of forecasting and their comparison with real data;
- creation of the report on the work of the proposed model of information security policy.
Analysis of the model for assessment of losses
The aim of every business is to maximize profits and minimize costs. If the former depends on the management, the latter depends on information security (IS) because the department of IS works with protecting the main features of information (availability, integrity, confidentiality).
There is the model of assessment of losses by Grezdov below[4].
The threat of accessibility is a limited access to the resource or its absence. The resource is exhausted if you have access to a resource, but it consumes a long period of time.
The losses from availability threats are calculated according to the formula:
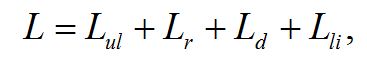
where Lul – losses from untimely services on access to information; Lr – losses associated with the restoration of working capacity; Ld – losses associated with downtime of the system unit; Lli– losses associated with the loss of income.
Data integrity is its completeness and invariability. Threat to the integrity represents the realization of changes of data intentionally or unintentionally. The formula for calculating the losses associated with threats to the integrity:
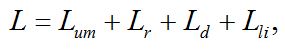
where Lum – losses from unauthorized modification of information, the amount of the losses depends on the importance of information integrity of which is compromised; Lr – losses associated with the restoration of working capacity; Ld – losses associated with downtime of the system unit;Lli – losses associated with the loss of income.
Confidential information – is information that is not publicly available and data leakage is likely to infringe the rights and interests that are protected by law. Loss on disclosure of information may be financial as well as loss of reputation and competitiveness.
Therefore, for the calculation of losses the most convenient method is the method of expert estimates. The essence of the method is that a group of experts in the field analyze losses based on the importance of the information.
From the foregoing, it is clear that the information of the enterprise must be protected in order to minimize losses. For this purpose, information risk insurance companies are used.
With the use of risk insurance of the company total losses (L *) are calculated according to the formula
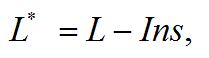
where L – the total losses due to violation of several categories of information; Ins – the total profit from risk insurance.
Grezdov’s model considers the losses of the violation of the fundamental properties of information – the availability, integrity and confidentiality. This model can be applied to calculate the losses of the violation of one, two, or all properties of the information. The formulas given above are versatile and easy to use, they can be used to carry out manual calculation, and to create a product for more accurate calculations performance.
However, this model does not account for inflation, and does not forecast threats that could result in the losses.
Forecasting of information security threats
It is advisable to apply the method of expert assessments in case of deficiency of statistical data. In this case, experts are invited to answer questions about the future behavior of nformation assets characterized by uncertain parameters, or unexplored properties.
There are 3 methods of forecasting, based on expert assessments:
- The method of collective expert assessment. In this case there is generalization of the findings of the team of experts in the field of information security. To obtain objective results it is necessary to process individual, independent estimates made by experts. Thus there is a comprehensive analysis of the problem.
- The Delphi expert estimates. This method is based on a process of "brainstorming", produced by a group of experts. This method is used when there is a need for rapid decision making. Delphi method is used for prediction by gathering and mathematical processing of expert estimates.
- The competence of the expert group. In this case there is a debate on the issue, with the aim of finding the only solution. This method differs from the previous one because the expert can also criticize other experts' opinions. The advantage of this method is the ease of implementation and reduction of the likelihood of errors.
Thus, the method of collective estimates is the most universal and is used in the master's work.
Expert knowledge is formed in the database (Fig. 1). The database helps to find similar incidents and methods of their solution, as well as minimize losses. This forecasting method has much in common with the prediction by analogy method. The main advantage of this prediction is the absence of false alarms.
The main disadvantage of this method is the inability to reflect the unidentified attacks. Thus even a small change in the already known attacks can be a serious problem [9, 11].

Figure 1. – Structure of the data base
Conclusion
To estimate the losses it is very important to recognize and take into account all the parameters that influence the cost of information security threats. They may include the cost of updating, the purchase or restoration of equipment, payment to workers who involved in restoration of the system, as well as the cost of the loss of reputation.
In addition, the information security policy should be implemented with prediction of threats to be aware in advance of a possible attack and eliminate the problem before it occurs.
In the master's work the model of assessment of losses is being upgraded through the use of predicting threats and consequent losses; the construction of the model of the enterprise security policy is held, taking into account the model of assessment of losses.
The choice of forecasting method of expert estimates is based on analysis of its advantages and disadvantages.
The advantages of this model:
- simple software implementation;
- the possibility of improvement;
- transparency of calculations;
- the possibility of use by any enterprise.
Disadvantages:
- while using the prediction by the method of expert estimates, there is a risk of inability to reflect the unidentified attacks, and the subjectivity of this method;
- lack of consideration of the inflation.
References
- Webcontrol [Electronic resourse] / Internet resource. – Access mode to article: http://web-control.ru/dlp_for_finance – Защита от утечек и потери информации о клиентах
- AVOIDANCE.RU – СТАТЬИ ОБ ИНФОРМАЦИОННОЙ БЕЗОПАСНОСТИ [Electronic resourse] / Internet resource. – Access mode to article:
http://avoidance.ru/articles/informatsionnaja-bezopasnost-na-predprijatii/57-analiz-riska-i-poter.html – Анализ риска и потерь - Arinteg [Electronic resourse] / Internet resource. – Access mode to article:
http://www.arinteg.ru/articles/analiz-ugroz-informatsionnoy-bezopasnosti-27291.html – Анализ угроз информационной безопасности - Грездов, Г. Г. Способ решения задачи формирования комплексной системы защиты информации для автоматизированных систем 1 и 2 класса [Текст] / Г. Г. Грездов // (Препринт/ НАН Украины. Отделение гибридных управляющих систем в энергетике ИПМЭ им. Г. П. Пухова НАН Украины; № 01/2005 ) – Киев : ЧП Нестреровой, 2005. – С. 66.
- Анализ модели для оценки потерь, связанных с реализацией угроз и страхованием информационных рисков: сб. текстов выступление на четвертой международной научно– технической конференции «Моделирование и компьютерная графика/ ДонНТУ 5– 8 октября – Д.: 2011. – 33с.
- Help Net Security [Electronic resourse] / Internet resource. – Access mode to article: http://www.net-security.org/secworld.php?id=8709 – Топ– 10 угроз информационной безопасности
- Telecommunication technologies - телекоммуникационные технологии [Electronic resourse] / Интернет – ресурс. – Режим доступа к статье: http://book.itep.ru/10/2011.htm#43 – 2011 г. Обзор по материалам ведущих фирм мира, работающих в сфере сетевой безопасности
- Бузинов А.С., Жигулин Г.П., Шабаев Р.И. Моделирование и прогнозирование информационных угроз как составная часть Концепции информационной безопасности РФ – СПб: Издательство «Научно– производственное объединение специальных материалов», – 2010. – С.63– 68.
- Your Private Network [Electronic resourse] / Internet resource. – Access mode to article: http://ypn.ru/448/intrusion-detection-technologies/ –Технологии обнаружения атак
- Административно– управленческий портал [Electronic resourse] / Internet resource. – Access mode to article: http://www.aup.ru/books/m6/8_4.htm – Безопасность предпринимательской деятельности
- Информационная безопасность [Electronic resourse] / Internet resource. – Access mode to article: http://inf-bez.ru/?p=424 – Анализ существующих методов экспертной оценки для систем информационной безопасности