Abstract
- Introduction
- 1. Theme urgency
- 2. Goal and tasks of the research
- 3. A brief overview of algorithms WPA
- 4. Model shift register which used pseudo-random sequences (SRP)
- Conclusion
- References
Introduction
Extremely important and complex scientific and technical challenge is to increase the security of telecommunication systems and networks TCS, which refers to the ability to protect against destruction, substitution, blocking unauthorized diversion or violations of the order of its routing [ 1 ].
Particularly acute issue of security arise in wireless telecommunications systems and networks, since it involves the use of radio technologies during which the terminal equipment can be freely navigate to the conservation of the unique identification numbers within the telecommunications network [ 2 ].
1. Theme urgency
The development and improvement of TCS carried out in accordance with Concept of development of telecommunications with the latest technology that meet international standards, taking into account the technological integrity of networks and telecommunications facilities, improve efficiency stability and functioning. The main purpose of the development of telecommunications e harmonious and dynamic development TCS throughout the country to meet the needs of individuals and entities, public authorities telecommunication services [ 3 ].
Accordance with the basic concept of the development of telecommunications and the current legislation of Ukraine in TCS all forms of ownership provides for the protection of technical tools and information that is transmitted. strategically important important to ensure protection from unauthorized interference in the operation modes of equipment TCS. among the available Telecommunications security threats if not the most important are the unauthorized interception of data transmitted ; unauthorized access various telecommunication resources; violations associated with incorrect authentication and authorization devices and users.
greatest danger for authentication and authorization protocols make certain shortcomings of existing methods and algorithms key generation wireless access authorization TCR since their use is associated with radio technology, in which the terminal equipment may move freely within the telecommunications network. according to to this vital topic of master study is to improve methods and technical means to improve security TCS wireless based on the formation of pseudo-random sequences [ 4 ].
2. Goal and tasks of the research
Development and improvement of telecommunication systems and networks Ukraine is carried out in accordance with the concept of telecommunications Ukraine with the latest technology that meet international standards, taking into account the technological integrity of all networks and telecommunications, efficient and sustainable operation. The main purpose of the development of telecommunications Ukraine is harmonious and dynamic development of throughout the country to meet the needs of individuals and entities, public authorities in telecommunication services.
Accordance with the relevant provisions of the Concept of development of telecommunications Ukraine and applicable law in SCI all forms of property protection envisaged technical tools and information they conveyed. Strategically important importance to protect against unauthorized access to modes of functioning equipment. Among the available Telecommunications security threats is not the most important is the unauthorized interception of data transferred ; unauthorized access various telecommunication resources; violation associated with false authentication and authorization of users and devices.
greatest danger for authentication and authorization protocols make certain shortcomings of existing methods and algorithms forming key access authorization in wireless TSM because their use involves using radio technologies, in which the terminal equipment can move freely within the telecommunications network. by this hot topic master study is to improve the methods and technical means to improve security Wireless TSM from the formation of pseudo- Ring Road.
The purpose of the master's work is to improve the security of wireless SCI based on formation of pseudo- Ring Road . For the purpose of the work necessary to solve scientific and technical problems, which is to develop a method of improving the safety of wireless SCI based on formation of pseudo- Ring Road . To address the overall scientific and technical problem master work necessary to solve partial problems are :- Conduct research methods to increase the security of wireless SCI based on formation of pseudo- Ring Road.
- develop a mathematical model of authorization and authentication for wireless security assessment SCI.
- Improve access authentication method to increase wireless oezpeky SCI.
object of study : The process of access authorization for enhanced security of wireless SCI.
subject of investigation : Methods and means of improving the security of wireless SCI based on formation of pseudo- Ring Road .
Research Methods : When doing research techniques used in the theory of broadcast data authentication theory, mathematical modeling and simulation , probability theory and mathematical statistics, elements of the theory of finite fields and number theory. In particular , the development of mathematical models and improved method of authorization and authentication methods used wireless broadcast data * theory , theory of authentication methods and mathematical modeling. In developing an improved method of forming PVP used elements of the theory of finite fields and number theory. Experimental study of the properties of known and proposed generators PVP to form KAD performed using the methods of simulation, probability theory and mathematical statistics.
As part of the master's work is to get actual research results in the following areas:
3. A brief overview of algorithms WPA
monograph reviewing the candidate of technical sciences Prokopovych-Tkachenko Dmitry, and agreeing with him personally and with my supervisor, was to explore the network virishino WI-FI as a variety of wireless networks. Interested in the fact that reading the algorithms WEP, WPA, WPA2 ( encryption algorithms in networks WI-FI) were observed deficiencies.
WPA, WiFi Protected Access - a new, more modern, at the moment, the mechanism of protection wireless networks from unauthorized access. WPA, and its further development - WPA2 replaced the mechanism of WEP, which began to be old until then. WPA - encryption protocol designed to protect Wireless O network standard IEEE 802.11, developed by Wi-Fi Alliance in 2003 as a replacement for the obsolete and dangerous protocol WEP [ 6 ].
Technical cancellation of WPA WPA2 encryption technology is, in particular, in the protocols used. WPA includes protocol TKIP, a WPA2 - protkol AES. In practice this means that the more modern WPA2 provides greater protection to the network. For example, you can create, TKIP authentication key size of 128 bits, AES - up to 256 bits.
Foruvannya key WPA2
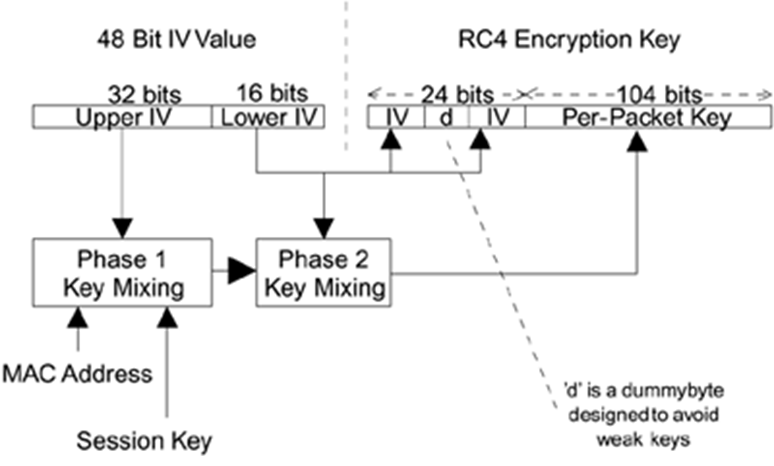
Picture 1 - Scheme of formation of the keys in the WPA2 [ 7 ].
4. Model shift register, which used pseudo-random sequences
In this paper investigates algorithm properties formation of authorization keys that was changed by the addition thereto of the shift register generator. This is necessary because the original algorithm open and search for the key to the attacker is only a matter of time. In our case, we get a new algorithm that an attacker does not look that gives you an advantage. This approach allows us to strengthen the protective properties of the algorithm, and does not require overnight change protocols.

Picture 2 - Example of using a shift register generator
( animation: 8 sequences , 135 kilobytes )
Conclusion
Nowadays extremely important and urgent task is the development and improvement (TCS) consists in increasing the security under which refers to protection from destruction, substitution, or the blocking of information against unauthorized information leakage. Especially acute issue in wireless
Master's thesis is devoted to the actual scientific problem to improve the properties of wireless security. At the moment are the following results:
- Analyzed threats wireless
- The analysis suggests possible ways to improve.
- Conducted a series of experiments on the use of shift register generator (PVP).
- Possibilities vikoristannya proposed methods for other networks.
Further research is focused on the following aspects:
-
Calculation
- quality methods used.
- Comparison of the performance.
In writing this essay master's work is not yet complete. Final completion: December 2014 . Full text of and materials on the topic can be obtained from the author or his manager after that date.
References
- Моделі і методи авторизації доступу в безпроводових телекомунікаційних системах / Л. С. Сорока, О. О. Кузнецов, Д. І. Прокопович–Ткаченко. – Дніпропетровськ : Пороги – 2013. – 196 с.
- Дослідження протоколів автентифікації та авторизації доступу в безпроводових телекомунікаційних системах та мережах / Д. І. Прокопович–Ткаченко // Системи озброєння і військова техніка. – 2013. –№ 1(33).–С. 119–122.
- Математична модель авторизації та автентифікації безпроводового доступу в телекомунікаційних системах та мережах / Д. І. Прокопович–Ткаченко // Системи обробки інформації. – X.: ХУПС, 2013. –Вип.5(112).–С.97–104.
- Метод формування псевдовипадкових послідовностей максимального періоду із використанням перетворень на еліптичних кривих / Д. І. Прокопович–Ткаченко // Вісник Апоследовательностейемії митної служби України. Серія «Технічні науки». – Дніпропетровськ : АМСУ, 2013 – № 1.– С. 47–53.
- Прискорене формування псевдовипадкових послідовностей максимального періоду із перетвореннями на еліптичних кривих / Д. І. Прокопович–Ткаченко // Системи обробки інформації. – X.: ХУПС, 2013. –Вип. 2 (109). –С. 197–203.
- Удосконалення методу авторизації та автентифікації безпроводового доступу для підвищення безпеки телекомунікаційних систем та мереж / Д. І. Прокопович–Ткаченко // Системи озброєння і військова техніка. – 2013. – № 2(34). – С. 124–132.
- Властивості генераторів псевдовипадкових послідовностей на еліптичних кривих / Л. С. Сорока, О. О. Кузнецов, Д. І. Прокопович–Ткаченко // Вісник Апоследовательностейемії митної служби України. Серія «Технічні науки». –Дніпропетровськ : АМСУ, 2012–№ 1(47). –С. 5–15.
- Formation of pseudo–random sequences of maximum period of transformation of elliptic curves / A. A. Kuznetsov, D. I. Prokopovych–Tkachenko, A. A. Smirnov // International Journal of Computational Engineering Research (IJCER). –Vol. 3, Issue 5, Version 3. – India. Delhi. – 2013. – P. 26–33.
- Пат. УА 78038, МПК (2013.01) С09С 1/00. Спосіб формування послідовностей псевдовипадкових чисел / Л. С. Сорока, О. О. Кузнецов, Д. І. Прокопович–Ткаченко та ін. – №и2012 08718; заявл. 16.07. 2012; опубл. 11.03.2013,Бюл.№5.–Зс.
- Пат. УА 80375, МПК (2013.01) О09С 1/00 Пристрій формування послідовностей псевдовипадкових чисел / Л. С. Сорока, О. О. Кузнецов, Д. І. Прокопович–Ткаченко та ін. – №ІІ201213846; заявл. 16.07. 2012; опубл. 27.05.2013, Бюл. № Ю. –Зс.
- Формування псевдовипадкових послідовностей максимального періоду із перетворенням на еліптичних кривих / О. О. Кузнецов, Д. І. Прокопович–Ткаченко // Праці IV міжнародної науково–практичної конференції «Обробка сигналів і негаусовських процесів», присвяченої пам'яті професора Ю. П. Кунченка: тези доповідей / М–во освіти і науки України, Черкас, держ. технол. ун–т. – Черкаси : ЧДТУ, 2013. – С. 63–65.
- Обеспечение безопасности информационньк технологий й систем в таможенном деле / А. А. Кузнецов, Д. Й. Прокопович–Ткаченко // Таможенному делу – идеи молодьіх : сборник материалов международной научно–практической конференции. – М.: Изд–во Российской таможенной апоследовательностейемии, 2013. –С. 124–125.
- Удосконалення методу авторизації та автентифікації безпроводового доступу з метою захисту економічної інформації / Д. І. Прокопович–Ткаченко // Математическое моделирование процессов в зкономике й управлений инновационньїми процессами (ММП–2013): тезисьі докладов международной научно–практической конференции, Алушта, 9–15 сентября 2013 г. – Харьков : ХНУРЗ, 2013. – С. 178.
- A Statistical Test Suite for Random and Pseudorandom Number Generator for Cryptographic Application. A. Rukhin, J.Soto. NIST Special Publication 800–22, September 2001.
- "Mobile WiMAX security", Airspan Networks Inc.Airspan, 2007. [Online]. Available: http://www.airspan.com
- Alamouti, S. M., A Simple Transmit Diversity Tec hnique for Wireless Communications,. IEEE Journal on Select Areas in Communications, vol. 16, no. 8, pp. 1451.1458, Oct. 1998.
- Handbook of Applied Cryptography – CRC Alfred J. Menezes, Paul C. van Oorschot, Scott A. Vanstone. Press, 1997. – 794 р.
- A simple unpredictable pseudorandom number generator. Blum, L., Blum, M., Shub, M.// SIAM Journal on Computing, vol. 15, 1986, pp. 364 – 383.
- How to generate cryptographically strong sequences of pseudo–random bits. Blum, M., Micali, S.// SIAM Journal on Computing, vol. 13, 1984, pp. 850 – 864.
- How to choose the best SoC for your WiMAX design Bob Wheeler. // Wireless Net DesignLine. Oct 17, 2005.
- A pseudo–random bit generator based on elliptic logarithms,Burton S. Kaliski, Advances in Cryptology — CRYPTO ’86 (Andrew M. Odlyzko, ed.), LNCS, vol. 263, Springer, 1986, pp. 84–103.
- “Operational semantics of security protocols,” C. Cremers and S. Mauw,In S. Leue and T. Systa, editors, Scenarios: Models, Transformations and Tools Workshop 2003, Revised Selected Papers, vol. 3466 of LNCS, Springer, pp. 66–89 2005.
- “Scyther – Semantics and Verification of Security Protocols,” C. Cremers, Ph.D. dissertation, Eindhoven University of Technology, Netherlands, 2006.
- “The Scyther tool: Automatic verification of security protocols,” C. Cremers, http://people.inf.ethz.ch/cremersc/scyther/index.html, 2009.
