Abstract
Ñontent
- Introduction
- 1 Relevance of a subject
- 2 Purpose and research problems, expacted results
- 3 Classification of methods and security protections of information systems
- 3.1 Cryptography
- 3.2 Digital signature
- 3.3 Authentication
- 4 Protection of networks
- 4.1 Analysis of firewalling technology
- Conclusion
- List of sources
Introduction
Growth of application of the modern information technologies makes distribution of different abuses possible to be connected to use of ADP equipment. In process of development of technologies of electronic payments, electronic document management and other systems, failure of local area networks can paralyze operation of the whole corporations and banks that leads to notable material losses. Data protection in the computer networks becomes one of the most burning issues today.
For reduction of damage it is necessary to select competent measures and means of ensuring of information security from theft, deliberate corrupting, illegal access, damage, readings and copyings. The knowledge of the basic legislative provisions in this area, economic, organizational and other measures is necessary. Technologies of computer systems and networks are developed very quickly and, respectively, new methods of information security also quickly appear.
1 Relevance of the subject
Now relevance of information protection is connected to growth of opportunities of ADP equipment. Development of the Internet global network and accompanying technologies reached such a high level that today's activities of any enterprise in general and each user separately, is already impossible to provide without e-mail, Web-advertising, communication in the online mode.
2 Purpose and research problems, expacted results
The main objectives of research:
- Analysis of potential threats in the computer networks in case of implementation of program abuses.
- Research and analysis of methods and means of information protection.
- Study of features of information security in a separate corporate network.
Subject of research: information transferred in telecommunication networks.
Object of research: information security of networks.
3 Classification of methods and security protections of information systems
Simulation of the corporate network of the enterprise happens using Cisco Packet Tracer. In the structure of the network there are server with the database, firewall, automated workplaces, USB stick serving as an access key is attached to each host. In a master's work research of technologies of setup of different firewalls, setup of the virtual private area network and remote access through it, and also technology of support of authentication of users via the flash drive is conducted.
3.1 Cryptography
Encoding or the cryptography allowing to transform data to the ciphered form which it is possible to derive the initial information is applied to support of privacy only in the presence of a key [1].
Dutch cryptographer Kerkhoff (1835–903) for the first time formulated the rule: firmness of the cipher, i.e. cryptosystem set of procedures, controlled by some classified information of small volume shall be provided in that case when to the cryptanalyst of the opponent knows all the mechanism of encoding except for the confidential key information managing of the process of cryptography conversions.
There are two main types of encoding: the symmetric encoding (it is also sometimes called traditional or encoding with the secret key) and encoding with the public key (sometimes this type of encoding is called asymmetrical) [2].
In case of the symmetric encoding the sender and the receiver own the same key (confidential) by means of which they can cipher and decrypt data. In case of the symmetric encoding keys of small length are used therefore it is possible to cipher large volumes of data quickly. The symmetric encoding is used by, for example, some banks in networks of ATMs. However the symmetric encoding possesses several shortcomings. First, it is very difficult to find the safe mechanism by means of which the sender and the receiver will be able to select the key secretly from others. There is a problem of safe distribution of the secret keys. Second, for each addressee it is necessary to store the separate secret key. Third, in the scheme of the symmetric encoding it is impossible to guarantee the identity of the sender because two users own one key.
Two different keys are used in case of the public key cryptography for message encoding. By means of one of them the message is ciphered, and with the help of the second — it is decrypted. Thus, the required safety might be obtained, having made the first key generally available (open), and to store and the second key is to be stored only at the receiver (the closed, personal key). In that case any user can cipher the message by means of the public key, but only the owner of the personal key is capable to decrypt the message. At the same time there is no need to safeguard transmission of the public key and for the users being able to exchange confidential messages, the presence of public keys of each other is sufficient.
3.2 Digital signature
If the message which safety we want to ensure is properly ciphered, athere is still a possibility of modification of the initial message or substitution of this message by another one. One of solutions of this problem is transmission of short submission of the transferred message made by the user to the receiver. Similar short representation is called checksum, or digest of the message. Checksums are used during creation of the abstract of the fixed length for submission of long messages. Algorithms of calculation of checksums are developed so that they are whenever possible unique for each message. Thus, the possibility of substitution of one message with saving the same value of checksum is eliminated with another one. However when using checksums there is a problem of transmission them to their receiver. One of possible ways of its solving is switching on of checksum in a so-called a digital signature.
By means of the digital signature the receiver can be convinced that the message received by him is sent not by the third party, and the sender has certain rights. Digital signatures are created by encoding of checksum and additional information by means of a personal key of the sender. Thus, anyone can decrypt the signature, using the public key, but only the owner of the personal key can create the signature correctly. For protection against interception and reuse the signature includes the unique number — sequence number.
3.3 Authentication
One of authentication schemes is use of standard passwords [3]. Password is a set of the characters known to the subscriber connected to the network which is entered by him at the beginning of the session of interaction with the network, and sometimes and at the end of the session (in especially responsible cases the password of a normal log off can differ from input). This scheme is the most vulnerable from the point of view of safety as the password can be intercepted and used by other person. Schemes using one-time passwords are most often used. Even being intercepted, this password will be useless in case of the following registration, and to receive the following password from the previous is an extremely difficult task. For generation of the one-time passwords both the program, and hardware generators representing the devices inserted into the computer slot are used. The knowledge of the confidential word is necessary for the user for coercions of this device in action.
One of the simplest systems which do not require the additional costs of the equipment but at the same time providi good protection level is S/Key, on an example which the order of submission of one-time passwords can be shown.
Two sides participate in authentication process with use of S/Key-client and server [4]. In case of registration in the system using the authentication scheme S/Key, the server sends on the client computer the invitation containing the grain transferred in networks in the open form, the current value of the counter of iterations and request for input of the one-time password which shall correspond to the current value of the counter of the iteration. Having received the response, the server checks it and transfers control to the server of the service required to the user.
4 Protection of networks
4.1. Analysis of firewalling technology
In case of connection of the corporate network to open networks, for example, to the Internet network, threats of unauthorized invasion into the closed (internal) network from open appear (external), and also threats of illegal access from the closed network to resources of open. The similar type of threats is also characteristic of the case when the separate networks oriented on integrate processing of confidential information of different level of privacy are united.
Network firewalls are capable to solve a set of tasks on reflection of threats for internal networks.
As well as for any security feature, certain compromises between convenience of operation and safety are necessary [5]. Transparency is visibility of a firerwall as to internal users, and external, realizing interaction through the firewall which is transparent for users if it doesn't hinder them to get a network access. Usually the firewalls are configured so that to be the transparent for the internal net surfers (sending packets outside), and, on the other hand the firewall is configured so that to be opaque to the external users trying to get access to the internal network from the outside. It usually provides the high level of safety and doesn't hinder internal users.
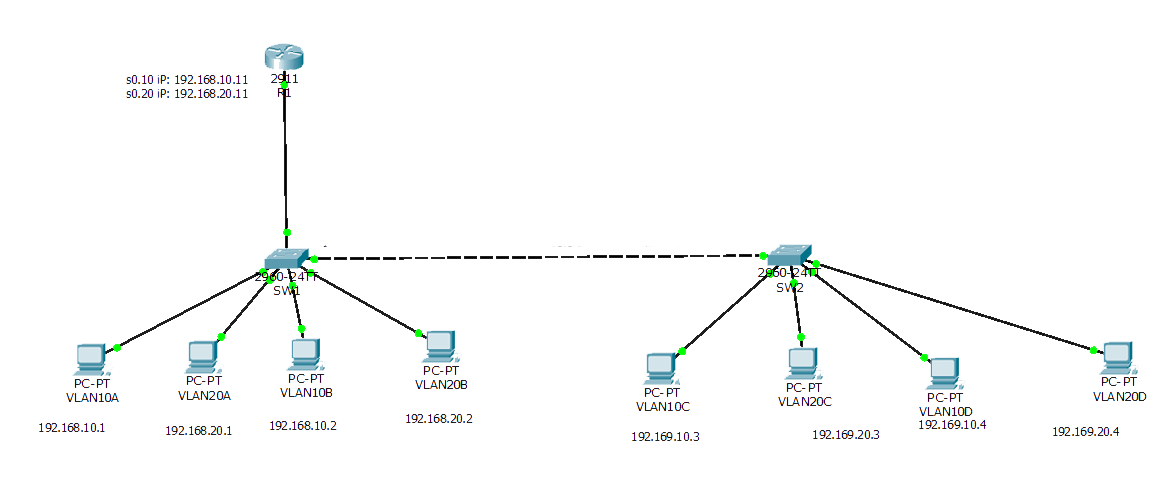
Figure 1 — Scheme of a local area network
Important concept of screening is the risk zone defined as a set of rule which becomes available to the malefactor after overcoming of the screen or any of it
components [5]. For protection of the reliability augmentation, the screen is realized as set of elements so cracking
of one of them doesn't open access to all the internal network.
Screening both from the point of view of a combination to other services of safety, and from the point of view of the internal organization uses the idea of multi-level protection at the expense of what the internal network appears
within a risk zone only in case of overcoming by the malefactor of several differently organized protective boundaries. Screening can be used as service of safety not only
in the network, but also in any other environment where there is a message exchange.
Ñonclusion
With growth of needs for support of implementation of above-mentioned points there is a need for analysis of information threats and technologies for their preventing.
The master's thesis is devoted to the extremely relevant task for today. The following tasks were carried out:
- The detailed analysis of threats of information security of the network of the enterprise and also technologies for their preventing.
- Based on the carried-out analysis, optimal solutions are selected.
- The model of an information system is developed.
- By means of implementation of this model technologies for support of information security are realized.
The master's thesis isn't finished yet. The final completion is December, 2016. The complete text of operation and materials on the subject can be received from the author or his scientific advisor after the specified date.
List of sources
- Stallings V. Cryptography and protection of networks: principles and practice. 2nd issuing — Williams publishing house, 2001 — 672 p.
- Andronchik A. N., Bogdanov V. V., Domukhovsky N. A., S's Colours., Sinadsky N. I., Polecats D. A., Scherbakov M. Yu. Information security on the computer networks. Practical course: manual / A. N. Andronchik, V. V. Bogdanov, N. A. Domukhovsky, A. S. Kollerov, N. I. Sinadsky D. A. Horkov M. Yu. Scherbakov; under the editorship of N. I. Sinadsky. — Yekaterinburg: UGTU-UPI, 2008. — 248 p.
- Biyachuyev T.A. Safety of corporate networks / Under the editorship of L. G. Osovetsky. — SPb: SPb GU ITMO, 2009. — 420 p. ISBN: 5-279-02549-6.
- Bezbogov A. A. Methods and means of computer information: manual / A. A. Bezbogov, A. V. Yakovlev, V. N. Shamkin. — Tambov: Publishing house of Tamb. State. Tekhn. Univ, 2006. —196 p. ISBN 5-8265-0504-4.
- Oglrti T. Firewalls. Practical application of internetwork screens — M.: DMK, 2003. — 401 p.
- Shangin V. F. Complex information security in enterprise systems: Manual. — M.: IDES ,
Forum
: INFRA-M, 2010. — 592 p. - Winter V., Moldovyan A., Moldovyan N. Bezopasnost of global network technologies. Master series — SPb.: BHV-St. Petersburg, 2001. — 320 p.
- Tsviki E., Cooper S., Chapmen B. Creation of protection on the Internet (the 2nd issuing). SPb.: Simvol-Plus, 2002. — 928 with.
- Yarochkin V. I. Information security — Academic Project publishing house, 2004. — 640 p.
