Abstract
Content
- Introduction
- 1. Relevance of the topic
- 2. Goals and objectives, planned practical results
- 3. The review of the research and development
- 3.1 Overview of international sources
- 3.2 Overview of national sources
- 3.3 Overview of local sources
- 4. Analysis of approaches to authentication in distributed software systems
- Conclusion
- References
Introduction
The rapid development of computer networks and especially the Internet has led to the widespread use of distributed systems for various purposes. Around the world, the process of decentralization of computations is underway, which allows you to create scalable systems capable of serving a huge number of users with high performance.
In connection with the widespread distribution of distributed systems in all spheres of human activity, there is an urgent need ensuring information security in such systems. One of the main measures to protect data is to ensure reliable user authentication. Currently, there are many approaches to authentication and even more implementations of these approaches. At the same time, not all classical solutions of the authentication task are suitable for use in distributed systems. But Different types of systems have unique requirements for authentication subsystems. In addition, active development computer technology makes it easy to crack authentication algorithms that 10-15 years ago were considered reliable. At therefore, continuous work is carried out in the field of research and development of authentication methods. Constantly appear new and improving existing algorithms aimed at providing secure user authentication.
1. Relevance of the topic
The relevance of the topic is due to the increasing value of information, the constant emergence of new threats to information security andthe importance of the authentication process when building information system security. Currently there is no universal solutions that can provide the necessary level of authentication security in any distributed system. Many wide common authentication algorithms remain vulnerable to various types of attacks. In the same time algorithms with a sufficient degree of security usually require complex infrastructure and remain incomprehensible for a wide range of users.
2. Goals and objectives, planned practical results
The purpose of this work is to study the effectiveness of existing approaches and authentication algorithms in distributed software systems, to analyze the advantages and disadvantages of modern authentication systems to develop a new authentication algorithm based on the analysis.
Object of study: methods and approaches to authentication in distributed systems.
Tasks :
- analysis of common approaches to authentication and specific algorithms that implement these approaches
- analysis of authentication standards
- identification of deficiencies and vulnerabilities of existing solutions
- designing a new algorithm based on the research
- development of a test software system and implementation of the designed authentication algorithm
- efficiency analysis of the developed algorithm
The proposed novelty of this work consists in the development of a new authentication algorithm oriented to use in distributed systems, which will eliminate some of the vulnerabilities and shortcomings of existing solutions.
Planned results: the design and implementation of the new authentication algorithm for distributed systems based on the analysis of currently used algorithms is planned as the results of this work, implementation of test system using the developed algorithm.
3. The review of the research and development
3.1 Overview of international sources
There are many sources, dedicated to the problem of authentication in distributed systems. In the article Secure Authentication Scheme for Internet of Things in Cloud [1] an authentication scheme for the Internet of Things in the cloud is proposed. And in the article Biometric Based User Authentication in Smart Phones [2] describes the method of biometric authentication for smartphones. There are many periodicals related to authentication. For example, Aerospace and Electronic Systems Magazine [3], IEEE Circuits and Systems Magazine [4]. Often there are conferences that deal with the problem of authentication. For example, one of the conference sections 20th International Conference on Advanced Communication Technology[5], held in November 2018, is dedicated to authentication and protection of personal data. There are organizations which activities is related to perfection of authentication in modern systems. For example, Biometrics Council [6], IEEE Cloud Computing[7].
3.2 Overview of national sources
Among national sources, many publications are also devoted to authentication. The article Strong authentication as part of
GDPR strategies
[8] is dedicated to multi-factor authentication and the use of hardware tokens as one of the factors
authentication.
The article Authentication in distributed information systems
[9] presents an overview of existing technologies
authentication in distributed systems, analysis of vulnerabilities and features of possible implementations of these technologies.
The publication Two-factor authentication to protect financial services: problems of use
[10] consider
the vulnerabilities of the main approaches to two-factor authentication based on one-time passwords.
In the article [11] prospects for the development of biometric authentication are presented, as well as disadvantages of existing methods biometric authentication.
In the article Modern methods of biometric authentication: review, analysis and definition of development prospects
[12]
Biometric authentication methods based on fingerprint recognition, retina, rainbow
shell of the eye, voice and handwriting, facial geometry and it is concluded that the most optimal at the moment is an algorithm
based on the analysis of facial expressions, as well as recommendations for the implementation of this algorithm.
3.3 Overview of local sources
In the work “Methods and algorithms of SCS for user authentication over LAN by voice tempo”[13] Kravchenko D.A. Described the possible implementation of a specialized computer user authentication system by voice.
In the article “Development of a computerized access control system using voice authentication”[14] Kulibaba O.V. analyzes the attributes that can be used to authenticate by voice, suggests an optimal set of attributes and the possible structure of an access control system based on voice authentication.
In the article Features of the authentication model based on CEH for the development of graphical password systems
[15] Efremchenko I.A.
analysis shorthand methods that can be used to increase the resilience of systems using password
authentication. A user authentication method based on a digital watermark is considered.
4. Analysis of approaches to authentication in distributed software systems
Currently, there are several basic approaches to the implementation of authentication in distributed systems:
- user verification of some secret, such as password authentication[16];
- checking that the object or resource belongs to the user, for example, authentication using certificates [17], smart cards[18], usb tokens[19];
- verification of certain user properties such as biometric authentication[20];
- verification of user related information such as location authentication[21].
Authentication can be one-way[22]and two-way[23]. With one-way authentication, one of the parties authentication takes place. With two-way authentication, both parties involved in pass mutual authentication.
Depending on the number of different methods used for authentication, there are single-factor and multifactor authentication.
At the moment, for the organization of authentication on Internet resources most often use different implementations of password authentication. In case of password authentication, the user is pre-registered on the resource, setting his login and passwords. The authentication process verifies that the saved login and password match the values entered by the user.
This algorithm is simple to implement, but it has a number of vulnerabilities. A user-defined password is often simple or predictable. Such a password is quickly cracked by brute force or with a dictionary attack. To increase the strength of the password, password generators are used, policies on mandatory password change are used to check password complexity [24]. But these measures are not always effective and complicate the work with the system for the end user. In addition, there is the problem of unsafe password storage by the user.
Authentication data for password authentication can be intercepted during transmission over an unsecured network or stolen from a database. To avoid this, data is encrypted and avoids storing passwords in clear text.[25]. Fishing attacks are an effective way to get user credentials.[26]. Figure 1 shows an example of the implementation of such an attack.
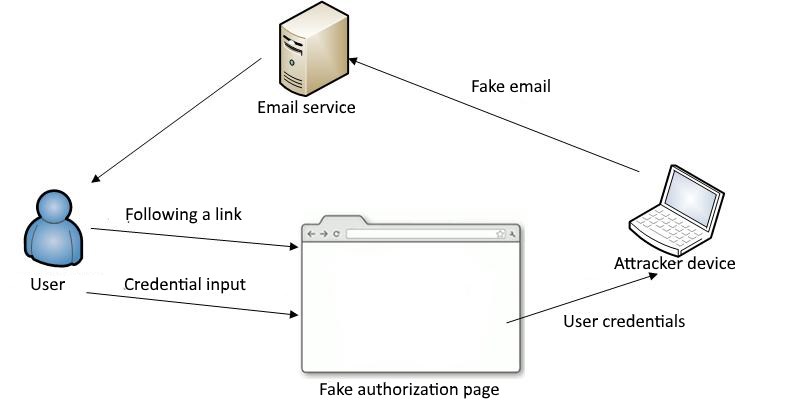
Figure 1 — Fishing attack implementation scheme
The compromise of user credentials is also possible with the use of virus software that somehow got onto the user's computer.
Another approach to implementing authentication is using public key infrastructure. (PKI)[27]. In a PKI-based authentication system, each user has a certificate issued by a certificate authority.[28]. This certificate uniquely identifies the user and contains its public key. Authentication in this case is performed by verifying the authenticity of the certificate and the ownership of the certificate to the user. Figure 2 shows an example of using the PKI infrastructure to authenticate a user.
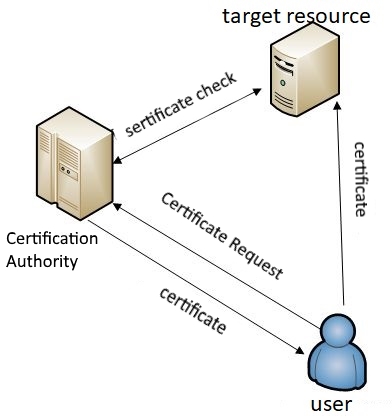
Figure 2 — PKI infrastructure usage example
This approach implements a more reliable authentication, but also has several disadvantages. Virus software can add an attacker's certificate to the list of trusted certificates. It is not possible to authenticate with a system using PKI if there is no connection with certification authorities. When the certification center is compromised, all the certificates issued by it become compromised. The security of the system depends on the method of storing the private key used in the specific implementation of the public key infrastructure.
Biometric authentication, which is based on the recognition of unique characteristics for each person, is very promising at the moment. Biometric authentication is user-friendly and provides a fairly high level of authentication.
The disadvantages of biometric authentication include the fact that many of the parameters of a person can change with age or as a result of injury. Often, implementations of authentication based on face or iris recognition allow false positives when an attacker uses a photo of another person. There are ways to bypass fingerprint authentication, for example, when using a 3d finger model or a photo of a fingerprint printed using special ink. Systems using voice recognition can be circumvented using a high-quality recording of a person’s voice or systems that reproduce a person’s voice based on existing recordings. The level of security of a system using biometric authentication depends on the method of storing biometric information. This is especially true given that the compromised biometric parameters are usually impossible to replace.
A rather promising alternative to password authentication is the SQRL protocol[29], which uses QR codes and asymmetric cryptography to implement user authentication. When you first start the client application, a master key and an unlock key are generated. Based on the master key and information on the target resource, each time a unique key is generated for this resource, that is used for authentication. The master key is stored in encrypted form, the decryption key is the user password. The identity unlock key is used to replace or export the master key and is stored in encrypted form in a user-printed QR[30] code. To decrypt the identity unlock key, a randomly generated 24-digit key is used, which is shown to the user only once when the application is first launched. Authentication scheme using this protocol is shown in Figure 3.
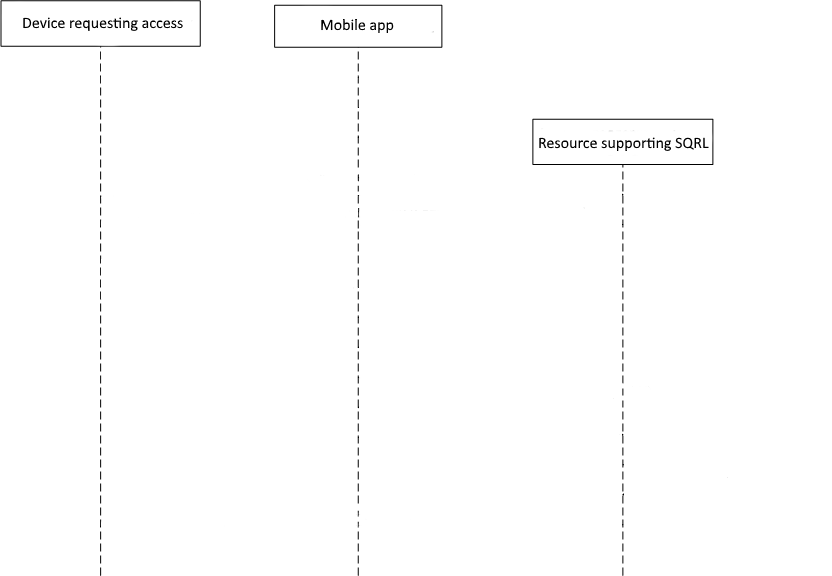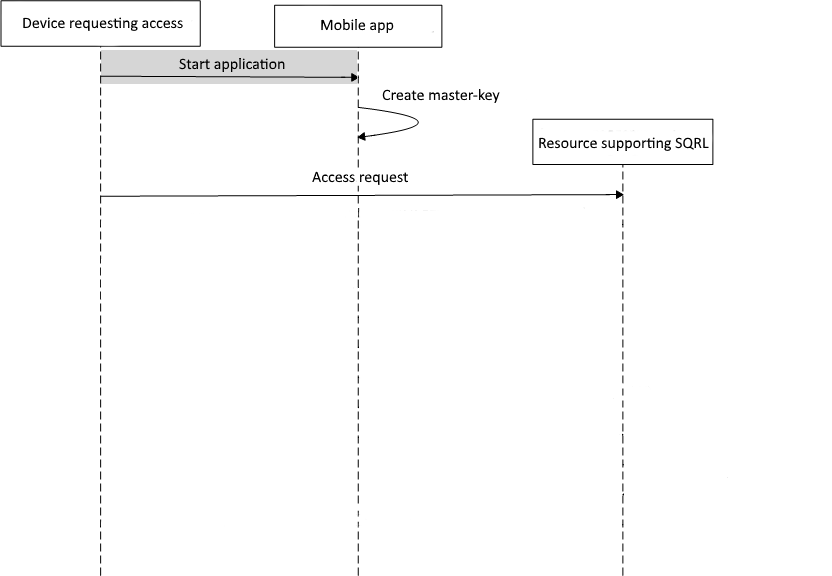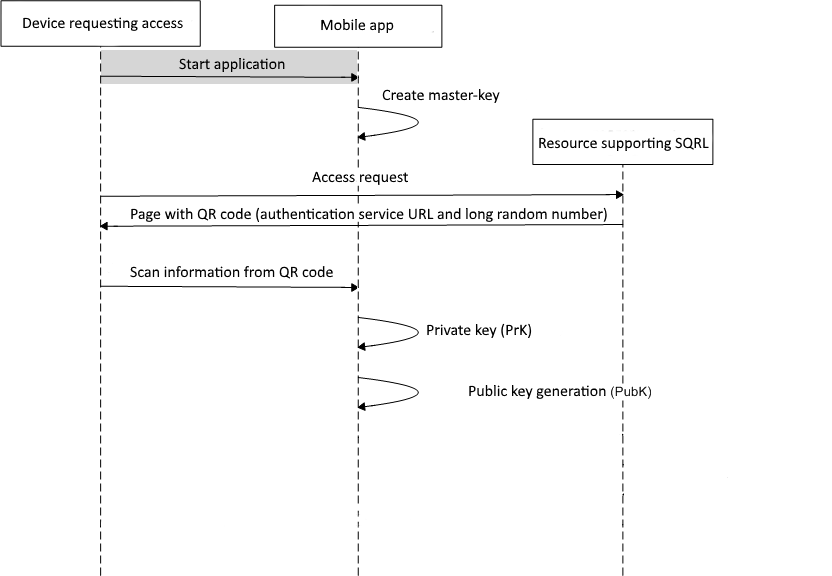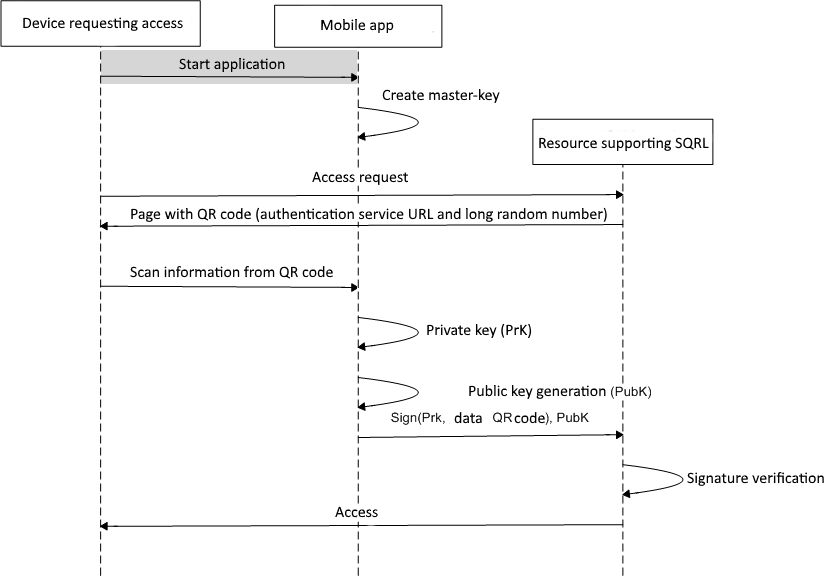
Figure 3 — Authentication scheme using SQRL protocol
(Animation: 10 frames, 100 cycles of repetition, 97 kilobytes)
Despite the fact that the protocol provides a sufficiently high level of protection during authentication, the weak point is the user's password, on the basis of which the master key is encrypted. In addition, there remains the threat of unsafe storage by the user of the unlock code of the person and the 24-digit software-generated key to decrypt the unlock code of the person.
This protocol can be enhanced by introducing a second authentication factor when entering a user password into the application and entering the identity unlock key. This can be sending a one-time code to the user's e-mail address. To exclude the possibility of substitution of e-mail address, the address for unlocking a person can be stored together with the unlock code in an encrypted form. The address used to confirm the user's identity when entering a password can be set for each individual resource during registration. You can change the data of the e-mail address when the unlock code is activated.
Conclusion
Based on the information provided, it can be concluded that authentication in distributed systems is relevant challenge. Today, there are many approaches to the implementation of authentication, which have different levels of protection, potential and realizable vulnerabilities, implementation complexity, ease of use. At the same time modern algorithms can be improved to enhance their resistance to possible attacks. This improvement should be based on comprehensive analysis of their vulnerabilities. Based on the analysis of existing publications, it can be argued that currently, the most relevant areas are multifactor and biometric authentication systems. Interest in multifactor authentication can be explained by the fact that with its help it is easy to expand the widespread password authentication, which in modern conditions can no longer provide users with a sufficient level of protection. Biometric authentication is attractive because it is the most convenient and easy to use authentication for the end user, while ensuring a sufficiently high level of security.
References
- Secure Authentication Scheme for Internet of Things in Cloud // IEEE Xplore Digital Library. [Electronic resource]. – Access mode: https://ieeexplore.ieee.org/document/8519890
- Biometric Based User Authentication in Smart Phones // IEEE Xplore Digital Library. [Electronic resource]. – Access mode: https://ieeexplore.ieee.org/document/8520335
- IEEE Aerospace and Electronic Systems Magazine // IEEE Xplore Digital Library. [Electronic resource]. – Access mode: https://ieeexplore.ieee.org/xpl/RecentIssue.jsp?punumber=62
- IEEE Circuits and Systems Magazine // IEEE Xplore Digital Library. [Electronic resource]. – Access mode: https://ieeexplore.ieee.org/xpl/RecentIssue.jsp?punumber=7384
- IEEE ICACT. [Electronic resource]. – Access mode: http://www.icact.org/
- IEEE Biometrics Concil. [Electronic resource]. – Access mode: http://www.ieee-biometrics.org/
- IEEE Cloud Computing. [Electronic resource]. – Access mode: https://cloudcomputing.ieee.org/
- Strong authentication as part of the GDPR strategy // Habrahabr. [Electronic resource]. – Access mode: https://habr.com/post/416139/
- Authentication in distributed information systems. [Electronic resource]. – Access mode: https://aladdin-rd.ru/company/pressroom/articles/autentifikacia_v_raspredelennyh_informacionnyh_sistemah
- Two-factor authentication to protect financial services. [Electronic resource]. – Access mode: http://www.ifin.ru/publications/read/1547.stm
- Biometric authentication: origins, hacks and future // Habrahabr. [Electronic resource]. – Access mode: https://habr.com/company/asus/blog/408407/
- Modern methods of biometric authentication. Review, analysis and definition of development prospects [Electronic resource]. – Access mode: https://cyberleninka.ru/article/v/sovremennye-metody-biometricheskoy-autentifikatsii-obzor-analiz-i-opredelenie-perspektiv-razvitiya
- SCS methods and algorithms for LAN user authentication by voice tempo. [Electronic resource]. – Access mode: http://masters.donntu.ru/2008/kita/kravchenko/diss/index.htm
- Development of a computerized access control system using voice authentication. [Electronic resource]. – Access mode: http://masters.donntu.ru/2010/fknt/kulibaba/library/article2.htm
- Features of authentication model based on tsvz for the development of graphic password systems [Electronic resource]. – Access mode: http://masters.donntu.ru/2017/fknt/yefremchenko/library/article2.htm
- Password Authentication // Volpi. [Electronic resource]. – Access mode: http://www.volpi.ru/umkd/zki/index.php?man=1&page=23
- The Basics of Cryptography and Digital Certificates // Cryptography. [Electronic resource]. – Access mode: https://whatismyipaddress.com/cryptography
- Smart cards as access protection. [Electronic resource]. – Access mode: https://www.osp.ru/lan/2004/01/138525/
- Cryptographic Token Key Initialization Protocol. [Electronic resource]. – Access mode: https://tools.ietf.org/html/rfc4758#page-11
- Biometric Authentication Overview, Advantages & Disadvantages. [Electronic resource]. – Access mode: https://heimdalsecurity.com/blog/biometric-authentication
- Location based authentication. [Electronic resource]. – Access mode: https://patents.google.com/patent/US20090187492
- Authentication is one-way. [Electronic resource]. – Access mode: http://cryptography.ru/docs/àóòåíòèôèêàöèÿ_îäíîñòîðîííÿÿ/
- Two-way authentication. [Electronic resource]. – Access mode: https://studopedia.org/4-95486.html
- How to create a strong password. [Electronic resource]. – Access mode: https://support.google.com/accounts/answer/32040?hl=ru
- Hash code. [Electronic resource]. – Access mode: https://dic.academic.ru/dic.nsf/ruwiki/1185956
- Fishing. [Electronic resource]. – Access mode: https://habr.com/post/344066/
- Installation of a certification authority in the enterprise. [Electronic resource]. – Access mode: https://habr.com/company/microsoft/blog/348944/
- Public Key Infrastructure Certificate and Certificate Revocation List (CRL). [Electronic resource]. – Access mode: https://tools.ietf.org/html/rfc5280
- Simple Authentication and Security Layer. [Electronic resource]. – Access mode: https://www.isode.com/products/sasl.html
- Introduction to QR Code. [Electronic resource]. – Access mode: http://twiki.org/cgi-bin/view/Blog/BlogEntry201102x2
- Fishing. [Electronic resource]. – Access mode: https://habr.com/post/344066/

This abstract refers to a work that has not been completed yet. Estimated completion date: June 2018. Ñontact the author or his scientific adviser after that date to obtain complete text.