Abstract
Content
- Introduction
- 1. Relevance of the Topic
- 2. Purpose and Objectives of the Research
- 3. Face Recognition Methods
- 3.1 Principal Component Method
- 3.2 Flexible Graph Matching Method
- 3.3 Viola–Jones Algorithm
- 3.4 Neural Networks
- Conclusions
- List of Sources
Introduction
Facial recognition is a form of biometric authentication. It involves detecting a face and comparing it with a known model in a database based on its features. This can be done through 2D or 3D real-time scanning or analyzing existing images. The significance of this technology is high as it is used in various fields, including ATMs, access control systems, people search, and smartphone authentication. Facial recognition is particularly relevant now due to the preference for contactless authentication methods. Our work will evaluate the methods and applications of this technology, as well as explore how organizations are already using it and how its application can be expanded.
With the development of society, there arose a need for personal identification for various reasons. As early as 1880 in France, scientist Alphonse Bertillon proposed the concept of identifying a criminal by their biometrics, allowing for precise individual identification. It was one of the first implementations of identity identification based on unique characteristics. In the modern world, facial identification is used in various fields, such as accessing a bank account through an ATM with a camera, serving as secondary authorization in access control systems, people search, or personal smartphone authentication. One cannot imagine any modern security system without a facial recognition system. Previously, biometric readers that scanned employees' fingerprints and compared them with a database were popular in security systems, including access control systems. However, due to the current global situation caused by the pandemic, modern solutions are trying to eliminate contact sensors in favor of contactless ones for hygienic reasons. Therefore, facial recognition is currently the most relevant topic when choosing biometric authentication.
There are many ways to identify a person through photos or video streams, from primitive to highly reliable, using only a camera or additional sensors (infrared emitters or LIDAR sensors). This paper will analyze key facial recognition algorithms and present a program for detecting a face in a video stream.
Existing facial recognition algorithms:
- Principal Component Method
- Flexible Graph Matching Method
- Linear Discriminant Analysis
- Viola–Jones Algorithm
- Support Vector Machine
- Neural Networks
- Template Matching Method
- Optical Flow Analysis
- Deformable 3D Face Model Construction Algorithm
1. Relevance of the Topic
In the modern information society, where technologies play a key role, the topic of facial recognition becomes an integral part of ensuring security and convenience in various fields. This essay explores the relevance and importance of applying facial recognition technology in different areas such as security, access control, medicine, and the entertainment industry.
Security and Access Control
One of the key aspects emphasizing the relevance of the topic is the use of facial recognition systems to ensure security and strict access control. These technologies are successfully applied in offices, banks, airports, and other places where it is necessary to manage staff access efficiently.
Contactless Authentication Technologies
In the context of growing interest in contactless authentication methods, facial recognition becomes a preferable and secure way to confirm identity. This trend gains particular relevance in light of modern challenges, such as the COVID-19 pandemic.
Application in the Banking Sector
Banks and financial institutions are successfully implementing facial recognition technologies to ensure secure access to bank accounts through ATMs and mobile devices. This not only enhances security but also provides convenience to customers.
Role in the Medical Field
Facial recognition technologies are playing a significant role in the medical field, ensuring secure access to patient data and enhancing overall healthcare efficiency.
Entertainment Industry and Research
Facial recognition technologies also find application in the entertainment industry, creating innovative and interactive user experiences. Continuous research and development in this field contribute to the emergence of new methods and technologies.
Thus, the topic of facial recognition remains relevant and in demand, playing a crucial role in ensuring security, efficiency, and innovation in various areas of human activity.
2. Purpose and Objectives of the Research
Research Objective: To evaluate facial recognition methods and their application areas, and to study how organizations are currently using this technology and how its application can be expanded.
Research Tasks:
-
Analysis of facial recognition methods:
- 2D facial recognition.
- 3D facial recognition.
- Infrared facial recognition.
- Deep learning for facial recognition.
-
Exploration of application areas of facial recognition technology:
- Security, including border control and law enforcement.
- Access control in various systems.
- Authentication on smartphones and other devices.
- People search and authorization.
-
Examination of real-world examples of technology application in modern companies.
-
Investigation of the potential use of technology to prevent dangerous situations.
Expected Research Outcomes:
- Evaluation of the effectiveness of various facial recognition methods.
- Identification of potential application areas for the technology.
- Analysis of practical experience of companies implementing facial recognition technology.
- Development of recommendations for optimal use of the technology in combination with access control systems.
- Identification of perspectives for using the technology to prevent dangerous situations in various fields.
3. Facial Recognition Methods
Facial recognition algorithms fall into two categories, depending on the applied recognition technology – 2D, where recognition is based on facial geometry, and 3D, where recognition is based on skull structure. The methods are also divided into three types:
- Exhaustive Method: This method involves comparing incoming information with information in a database, where various modifications of representation are stored for each type.
- Deep Analysis of Image Characteristics: In this method, recognition involves determining various geometric characteristics.
- Use of Artificial Neural Networks: This method involves "training" a neural network or creating a structural neural network that takes into account the specificity of facial recognition. This method is highly effective and fast but requires a large information database for training.
3.1 Principal Component Method
Principal Component Method represents facial images as a set of principal components, known as "eigenfaces." It applies linear transformation to the original array, creating a new coordinate direction that reflects the greatest data variance. The first components contain the primary information about the image.

Figure 1 – Example of eigenface vectors
PCA transforms the original image variables into a new set with fewer variables, preserving almost all the information. The calculation of principal components involves computing eigenvalues and eigenvectors of the covariance matrix. Image reconstruction is performed by the sum of principal components multiplied by their corresponding eigenvectors.
For facial recognition, typically, 5 to 200 principal components are computed. Recognition involves comparing the components of an unknown image with known ones. Drawbacks include the requirement for ideal conditions and constraints on parameters such as lighting and accessories. The method's complexity is associated with processing a large volume of data.
The method's strengths include high accuracy (over 90%).
3.2 Flexible Graph Matching Method
The Flexible Graph Matching method, introduced in 1993 in the "IEEE Transactions on Computers, Vol. 42, No. 3," is an exhaustive method. Its essence lies in the elastic matching of graphs representing facial images. Graphs with weighted vertices and edges are used, describing faces using Gabor filters to extract features.
The main task of the method is to fit a deformable graph to a reference during recognition. Feature values are computed at the graph's vertices after applying the Gabor filter to the facial image. Distances between graph vertices determine the weights of edges.
Graph comparison uses a deformation cost function, considering differences in feature values and the degree of edge deformation. Graph deformation occurs by displacing vertices until achieving minimal difference with the reference graph.
The method's advantages include resistance to emotional expressions and changes in the face's pose (up to 15 degrees) with a recognition accuracy of 90-95%. However, the method has high computational complexity, leading to extended recognition times, especially with an increased database size. Additionally, the difficulty of adding new references makes it less effective in the long term compared to other methods.
3.3 Viola–Jones Algorithm
Haar-like features are a successful method for extracting features from images, based on comparing brightness in two rectangular areas, and are characterized by computational speed. These features describe object characteristics, such as brightness changes. An example of their use is the Viola–Jones method for face detection, initially introduced for recognizing faces.
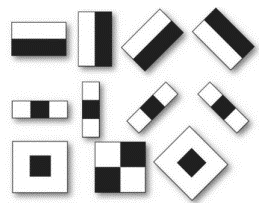
Figure 2 – Example of Haar-like features
Haar-like features can describe brightness changes, such as differences between the eye and nose areas on the face. The advantage lies in high computational speed, especially when using integral image representation, providing constant time calculations for each feature.
The Viola–Jones method uses Haar-like features for real-time object detection, initially focusing on face detection. Viola and Jones features are more complex than basic Haar-like features, including multiple rectangular regions to describe objects.
To compute features, the integral image representation is used, ensuring high efficiency and minimizing false positives. The AdaBoost algorithm is applied to build a complex classifier from simple ones, adaptively considering errors of previous classifiers. Ultimately, the Viola–Jones method demonstrates high accuracy and speed in detecting objects, especially faces in 24 × 24 pixel images.
3.4 Neural Networks
Systems based on neural networks, also known as autoassociative memory, operate by reproducing the information stored closest to the input data. In the case of facial recognition, the input data represents a facial image. Neurons, serving as basic memory elements, are connected to each other, and the system is adjusted by changing the weights of connections during the learning process.

Animation 3 - Generalized stages of the face recognition process (4 frames, 1 cycle, 81kB)
The operation of neural networks involves digitizing and encoding the image, placing each vector coordinate in a separate cell connected to other cells, and filtering images through the neural network. The output is the closest memorized image.
Convolutional Neural Networks (CNN) are a specialized architecture for efficient image recognition. They use features of the visual cortex, such as simple and complex cells, to process images by alternating convolutional and subsampling layers. Training occurs using methods such as backpropagation, with the choice of activation functions for neurons.
CNN advantages include high recognition accuracy (over 90%) and resilience to noise in input data. However, drawbacks include implementation complexity and the potential for overfitting when adding new data to the database.
Such systems are successfully applied in facial image analysis, including gender classification, recognition, and emotion detection.
Conclusions
Through the analysis of various facial recognition methods, it can be concluded that each method has its own characteristics and is applied depending on specific tasks and requirements. Principal Component Analysis (PCA), provides high accuracy in facial recognition based on the geometric features of the face. The Flexible Graph Matching method, although resistant to emotional expressions and changes in the face's perspective, requires significant computational resources. The Viola-Jones algorithm, thanks to Haar-like features, ensures high speed in detecting objects, especially faces, and is effective in real-time.
Neural networks, particularly Convolutional Neural Networks (CNNs), offer the potential for high-precision facial image recognition and demonstrate resilience to data noise. However, their complexity in implementation and the potential vulnerability to overfitting when adding new data require special attention.
Facial recognition is a relevant and in-demand topic in modern society, covering various areas:
- Security: Applied for access control, video surveillance, and authentication, ensuring security in public places and critical areas.
- Technological Progress: The development of deep learning and artificial intelligence has increased the accuracy and efficiency of facial recognition methods.
- Business and Commerce: Used for access management, time tracking, personalized advertising, and optimizing business processes.
- Medicine: Utilized for patient identification and ensuring secure access to medical information.
- Smart Devices: Integrated into smartphones and smart devices, facilitating everyday life and enhancing security levels.
List of Sources
- Mishchenkova E.S. Comparative analysis of facial recognition algorithms // Bulletin of Volgograd State University. Series 9, Research of Young Scientists. – 2013. – No. 11. – P. 74–76.
- Goncharov A.V., Karkishchenko A.N. Influence of illumination on the quality of frontal face recognition // Proceedings of SFU. Technical Sciences. – 2008. – No. 4 (81). – P. 88–92.
- Fan N.Kh., Bui T.T.Ch., Spitsyn V.G. Real-time gesture recognition on video sequences based on Viola–Jones method, CAMShift algorithm, wavelet transformation, and principal component method // Bulletin of Tomsk State University. – 2013. – Vol. 23, No. 2. – P. 102–111.
- Arsentyev D.A., Biryukova T.S. Flexible graph matching method as a pattern recognition algorithm // Bulletin of Ivan Fedorov MGUP. – 2015. – No. 6. – P. 74–75.
- Rogozin O.V., Kladov S.A. Comparative analysis of facial recognition algorithms in the problem of visual identification // Engineering Journal: Science and Innovation. – 2013. – No. 6 (18). – DOI: 10.18698/2308-6033-2013-6-818.
- Bui T.T.Ch., Fan N.Kh., Spitsyn V.G. Face recognition based on Viola–Jones method, wavelet transformation, and principal component method // Proceedings of Tomsk Polytechnic University. – 2012. – Vol. 320, No. 5. – P. 54–59.
- Usilin S.A. Algorithmic development of Viola–Jones detectors for solving applied problems of image recognition: PhD thesis. – Moscow, 2017. – 149 p.
- Samal D.I., Frolov I.I. Algorithm for preparing a training sample using 3D modeling of faces // Systems Analysis and Applied Informatics. – 2016. – No. 4. – P. 17–23.
- Tropchenko A.A., Tropchenko A.Yu. Neural network methods for human identification by facial image // News of Higher Educational Institutions. Instrument Engineering. – 2012. – Vol. 55, No. 10. – P. 31–36.
- Skopchenko A.A., Dorofeev V.A. Analysis of facial recognition methods // Microsoft Technologies in Theory and Practice of Programming: Collection of Works of the XIII All-Russian Scientific and Practical Conference of Students, Postgraduates and Young Scientists, March 22–23, 2016. – Tomsk, 2016. – P. 176–178.
- Baglikov V.G. Relevance of developing a computer subsystem for biometric identification of a person by photo portrait: Abstract of PhD thesis. – Moscow, 2008. – 5 p.
