Abstract on the master's work
Relevance of the topic
In the age of rapid development of information technology companies of all types and forms of ownership are becoming dependent on information systems. A breakthrough in the technical area encourages the development not only of the methods of information security, but also the ways of the negative impact on it. This high rate of growth of scientific knowledge and the variety of possibilities of its application makes a company vulnerable to threats of various kinds [1].
Therefore, ensuring the necessary level of information security is a serious issue. This stimulates the development of different methodologies in this area, which makes the issue relevant. There is a need to develop and improve information security policy of an enterprise, under which implies the possibility of using a distributed model of resource use and levels of security.
The goals and objectives of the study
The main purpose of this master's work is to develop a universal information security policy based on a risk analysis for used resources. The tasks of master's work are:
- the rationale for risk management;
- the analysis of methods for estimating the risk for the formation of an information security policy of small enterprises;
- the definition of the role of risk management and audit in information security;
- the analysis and improvement of the distributed model of resource use;
- the formation of the optimal information security policy of the enterprise.
Scientific novelty
Expected scientific novelty of this master's work is to improve the distributed model of the use of information resources in the enterprise due to the constant change of the current situation in the field of computer and information technologies, which will provide a more secure operation of the company, as well as in the development of a universal approach to information security, which will simplify the selection of certain methods to ensure the integrity and security of information for specific purposes and conditions.
The model of distributed resources for the protection of information
The process of information security protection is the interaction of information threats and information security, preventing their interaction. Information security is achieved stagewise and in the specific order. Each stage can be represented by its own model (Fig. 1):
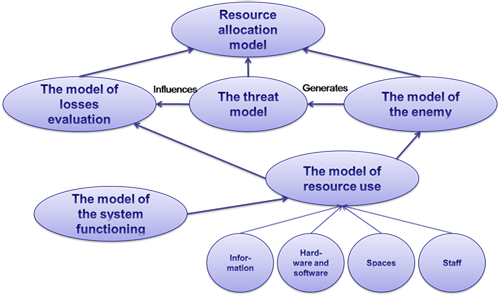
All the stages are combined into an integral model of the distribution of resources to protect the information. It is based on the capabilities of the enemy and the defending side, on the basis of the threat model and the loss estimating model. This occurs because of the fact, that the cost of protection is not to exceed the damage of the security breach [14] .
Analysis and risk assessment. Risk Management
Currently, there is international practice to ensure information security regime.
The minimum number of requirements for information security corresponds to a basic level of ensuring information security. Such requirements are usually used for standard projects.
If the basic requirements are insufficient, it is vital to apply additional and higher requirements [19]. This mode provides strategies for working with different risk classes that implement the following approaches:
- risk reduce: many risks can be reduced through the use of simple and cheap countermeasures;
- risk aversion: some classes of risk can be avoided by removing the Web server of the organization beyond the local network;
- change of risk nature: if you cannot avoid the risk or reduce it, it is better to insure the sensitive object;
- risk acceptance: the expert has to realize the residual value risk due to inability to reduce it to a small value.
As a result, after taking into account all the above-listed points, it is possible to create an effective system of risk management for the enterprise.
Statistics grounds for the use of risk management
In many small businesses risk management has the least. A survey conducted at America’s Small Business Summit in May 2010 shows that business owners distribute their priorities in the following order [16]:
- marketing and sales;
- managing cash flow;
- attracting finance;
- attracting and retaining employees;
- identifying and managing insurable risks;
- complying with federal and state regulations;
- protecting against litigation and lawsuits.
According to a report on security threats on the Internet, conducted by Symantec in 2011, the number of cyber attacks on computers has increased by 36% as compared with 2010. Every day more than 4500 new attacks occur. There have been created more than 403 million new varieties of malicious software which means an increase in new developments by 41% [17].
A study conducted by 874 certified professionals in the field of information security (CISSP) in 2004 showed that for the improvement the situation in the field of information security policies the support of the top management of the company, being insufficiently aware of the importance of the issue, is required [18].
The above listed statistical data indicate that corporate networks are currently the most vulnerable to attacks. Since they use a storage area network, communication peer–to–peer, instant messages, remote access, the definition of the boundaries of security is almost impossible.
Improvement of the model of distributed resources
Studies have shown that the model of distributed resources in the field of information security requires improvement. It is necessary to determine the resistance of the protection system to distributed attacks. For example it is possible to conduct the preliminary construction of a model of distributed attacks before the formation of the threat model.
It is also important to find the vulnerability of the defense, because the risk of information security of each resource is calculated not only by the analysis of threats, but also on the basis of vulnerability (Figure 4). For this reason it is necessary to apply audit and risk management.
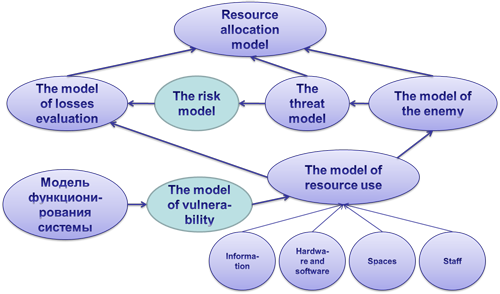
To ensure maximum data protection regime, the allocation of resources should be carried out by groups and levels of secrecy. This model is offered by Nikolay Stoyanov and Veselin Tselkov [11]. Based on this model the sequence diagram of the user access to resources was constructed (Fig. 5).
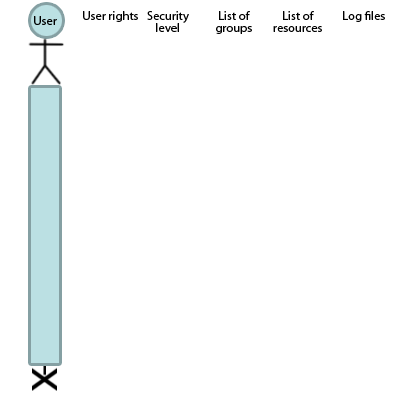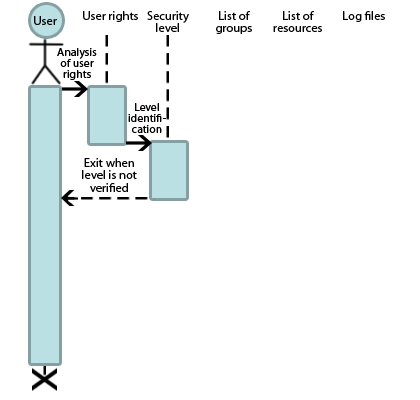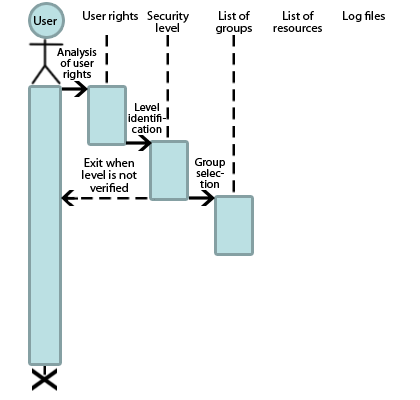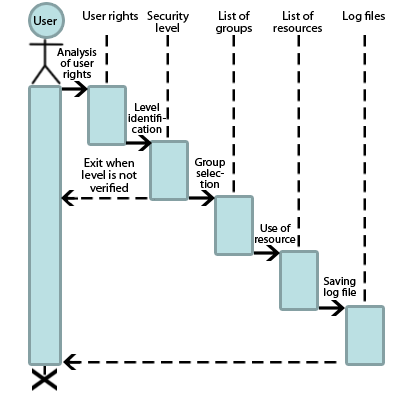
Due to this model it is possible to reduce the risk of unauthorized access to system resources, which greatly enhances the security of the organization.
Conclusions
According to the study, information security is an important factor for the correct functioning of a small business. For its maintenance it is necessary to systematically perform risk assessments, analysis of risk situations, or a full audit of the company.
In the software that is being developed as a part of an information security policy based on a risk analysis for the used resources, an improved model of distributed resources is applied. The sequence of the access to the resources of a company is determined by levels of privacy and security groups.
References
- Мельников В.П., – Информационная безопасность и защита информации./В.П. мельников, С.А. Клейменов, А.М. Петраков. – 3–е изд., стер. – М.: Издательский центр «Академия», 2008. – 336 с.
- Борисов Н.Е., – Разработка компьютеризированной подсистемы оценки рисков операций с пластиковыми картами в условиях Путиловского отделения ПИБ. [Электронный ресурс] – Режим доступа: http://www.masters.donntu.ru/2007/kita/borisov/diss/index.htm
- Цикра Р.С., – Исследование и разработка методов повышения достоверности передачи информации в корпоративной сети промышленного предприятия. [Электронный ресурс] – Режим доступа: http://masters.donntu.ru/2009/kita/tsikra/diss/index.htm
- Носко Ю.В., – Распределенная информационная сеть предприятия ОАО «АЗОЦМ» с повышенными требованиями к надежности и безопасности информации. [Электронный ресурс] – Режим доступа:http://www.masters.donntu.ru/2006/kita/nosko/diss/index.htm
- Химка С.С., – Разработка моделей и методов для создания системы информационной безопасности корпоративной сети предприятия с учетом различных критериев. [Электронный ресурс] – Режим доступа: http://masters.donntu.ru/2009/fvti/khimka/diss/index.htm
- Селина Н.В., – Исследование эффективности защищенности корпоративных систем средствами и методами визуального моделирования. [Электронный ресурс] – Режим доступа: http://masters.donntu.ru/2010/fknt/selina/diss/index.htm
- Никуленко Е.Д., – Разработка модели для оценки потерь, связанных с реализацией угроз и уязвимостей для информационных систем. [Электронный ресурс] – Режим доступа: http://masters.donntu.ru/2011/fknt/nikulenko/diss/index.htm
- Цымбалова А.А., – Разработка модели использования и распределение ресурсов, выделяемых на защиту информации. [Электронный ресурс] – Режим доступа: http://www.masters.donntu.ru/2011/fknt/tsymbalova/diss/index.htm
- Домарев В.В., – Безопасность информационных технологий. Персональный сайт к.т.н. Домарева В.В. [Электронный ресурс] – Режим доступа: http://www.security.ukrnet.net/modules/news/
- Державна служба спеціального зв'язку та захисту інформації України. [Электронный ресурс] – Режим доступа: http://www.dstszi.gov.ua/dstszi/control/uk/index
- Nikolai Todorov Stoianov, Veselin Tsenov Tselkov; E–net models for distribution, access and use of resources in security information systems [Электронный ресурс] – Режим доступа: http://arxiv.org/abs/1011.3148 – Загл. с экрана.
- Ernst and Young. Official site. [Электронный ресурс] – Режим доступа: http://www.ey.com/
- ISACA. Official site. [Электронный ресурс] – Режим доступа: https://www.isaca.org/
- Грездов Г.Г. Модифицированный способ решения задачи нормирования эффективной комплексной системы защиты информации автоматизированной системы / Г.Г. Грездов; монография. – К.: ДУІКТ, 2009. – 32 с.
- Петренко С.А. Управление информационными рисками. Экономически оправданная безопасность. / Петренко С.А., Симонов С.В. – М.: Компания АйТи ; ДМК Пресс, 2004. – 384 с.: ил.
- Townsend Stephen. Managing Risk: It’s Not Just for Big Business, IS 8930 Information Security Administration, Summer 2010,7/14/2010. [Электронный ресурс] – Режим доступа: http://stephendtownsend.com/wordpress/wp-content/uploads/2010/12/ – Загл. с экрана.
- Официальный сайт Symantec. Отчет об угрозах безопасности в интернете. Том 17. [Электронный ресурс] – Режим доступа: http://www.symantec.com/ru/ru/threatreport/ – Загл. с экрана.
- K.J. Knapp, ProQuest Dissertations & Theses A&I, A model of managerial effectiveness in information security. From grounded theory to empirical test. [Электронный ресурс] – Режим доступа: http://search.proquest.com/pqdt/docview/305027061/13CC629C6525389888F/5?accountid=93221 – Загл. с экрана.
- JetInfo, информационный бюллетень, вып. 1(68)/1999; [Текст]/М.:Джет Инфо Паблишер
- Software Engineering Institute Carnegie Mellon [Электронный ресурс] – Режим доступа: http://www.cert.org/octave/octaves.html
- IT Expert [Электронный ресурс] – Режим доступа: http://www.itexpert.ru/rus/ITEMS/77-33/index.php
